Cloud desktop mobile device security management method
A mobile device and security management technology, applied in the transmission system, electrical components, etc., can solve problems such as restrictions on the use of mobile devices, cloud desktop data leakage, cloud desktop poisoning, etc., to prevent data leakage, reduce channels, and reduce the probability of poisoning Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
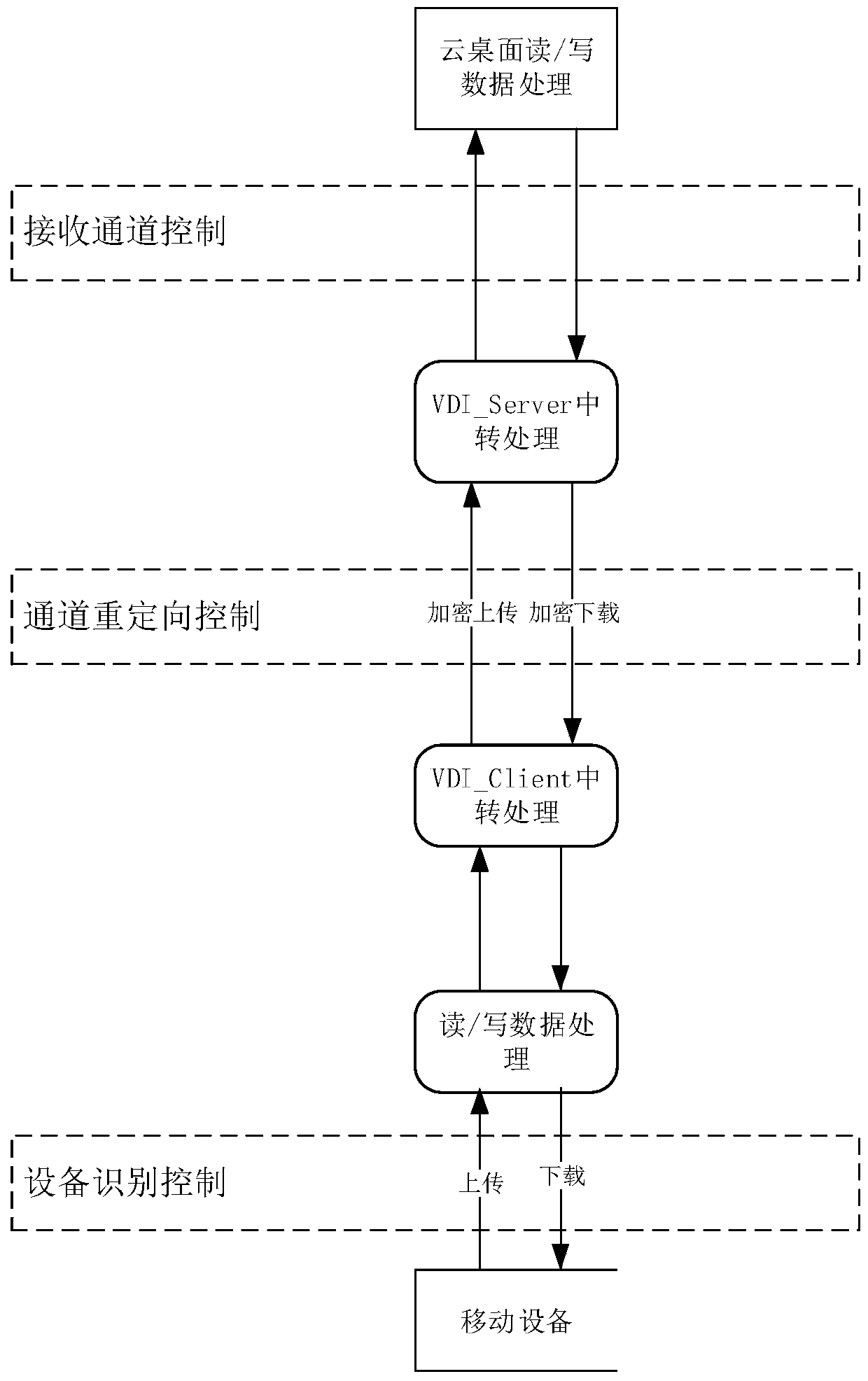
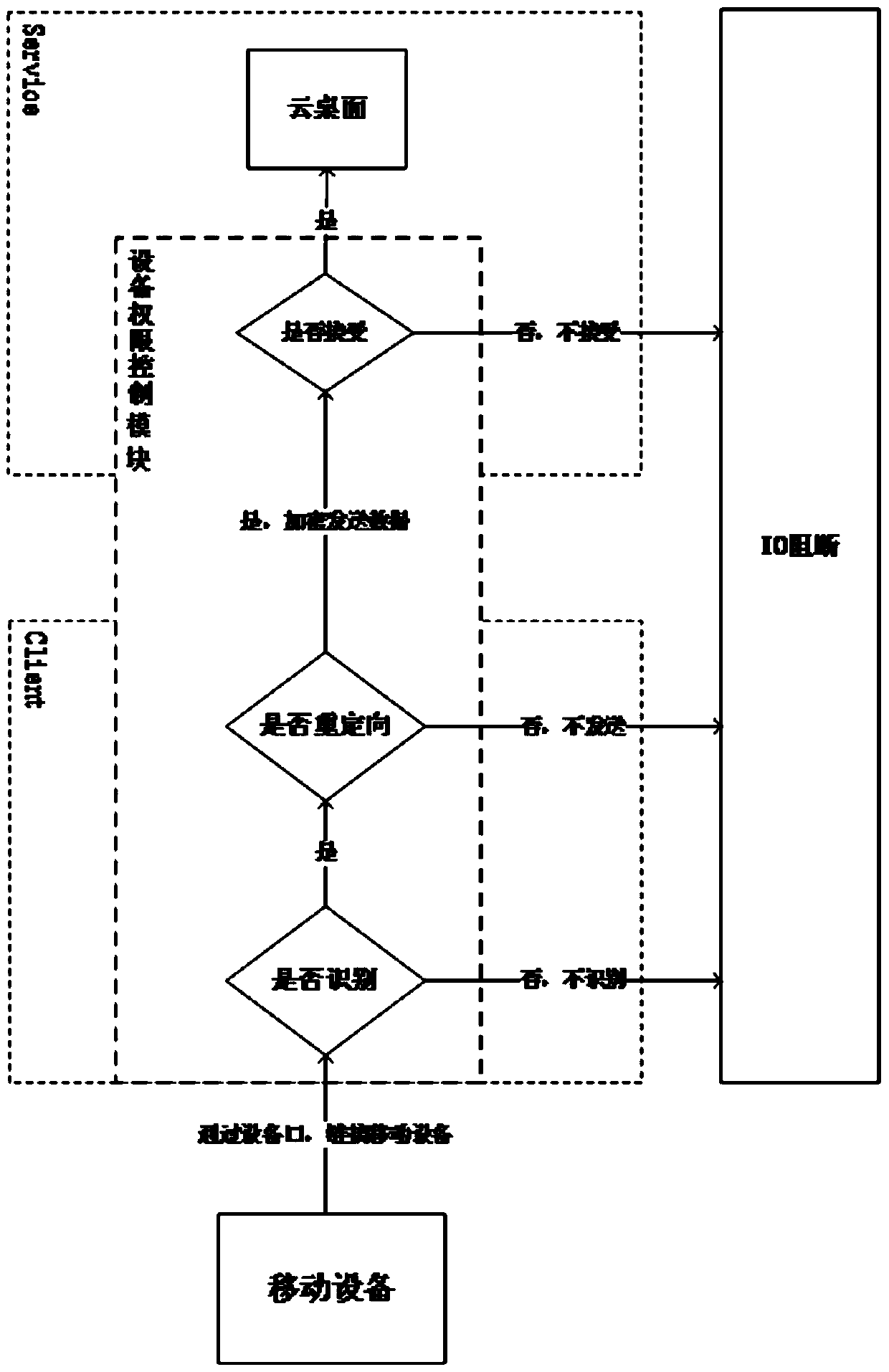
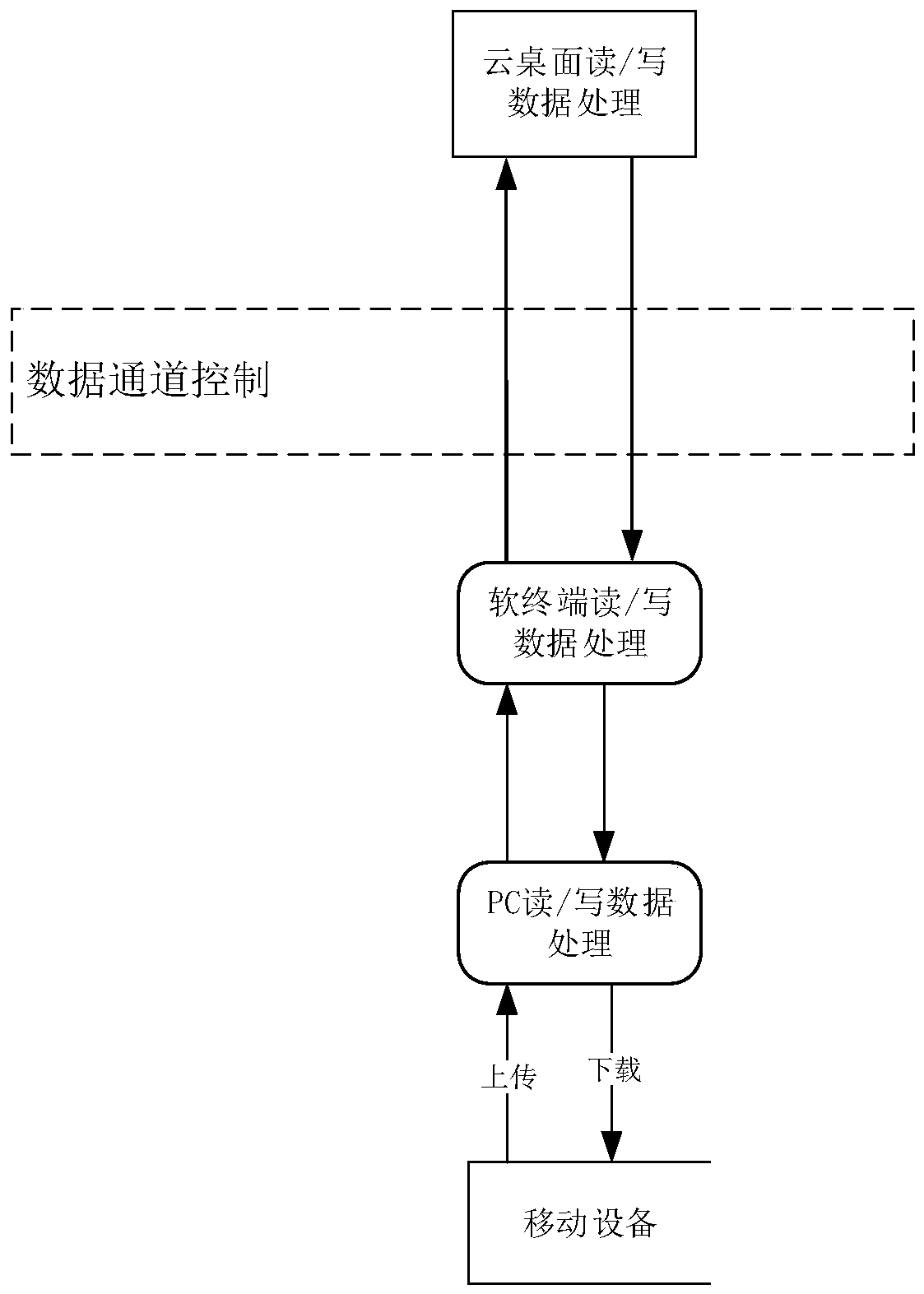
[0023] During the data transmission process between the cloud desktop and the mobile terminal, a device authority control module is set to control the data transmission between the mobile terminal and the cloud desktop.
[0024] Such as figure 1 and figure 2 As shown, the method of restricting data interaction between the thin terminal external mobile device and the cloud desktop:
[0025] Initial step: encrypt and encapsulate the thin terminal system, load the cloud desktop client when the thin terminal starts, and shield the underlying system of the thin terminal. Prevent users from operating the thin terminal system.
[0026] Step A. Device identification control
[0027] Make restrictions on the system driver layer of the thin terminal, interact with the device authority control module when the thin terminal starts, and control whether...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com