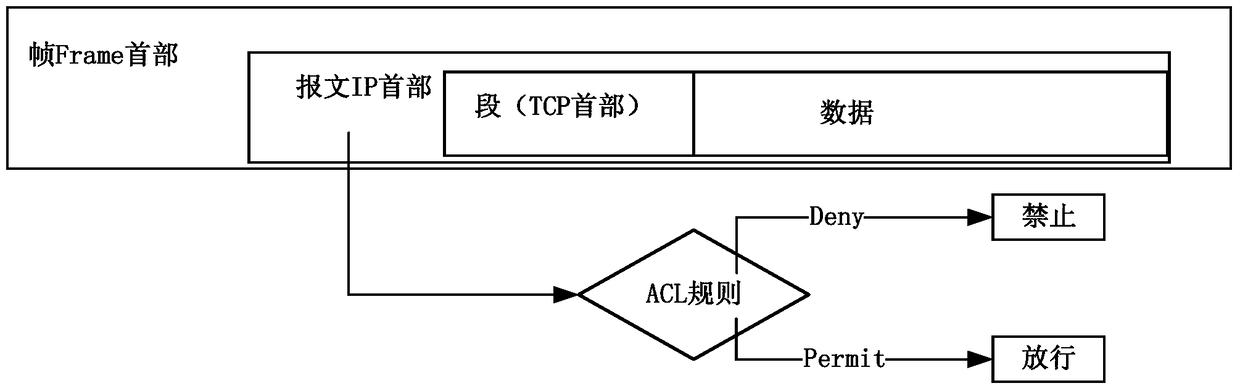
A method of operating access control policy rules
An access control policy and operation method technology, applied in the operation field of access control policy rules, can solve problems such as dragging down hardware equipment, occupying firewall system resources, failure, etc., to solve the problem of quantity limitation, improve the efficiency of research and judgment, and reduce the number of Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
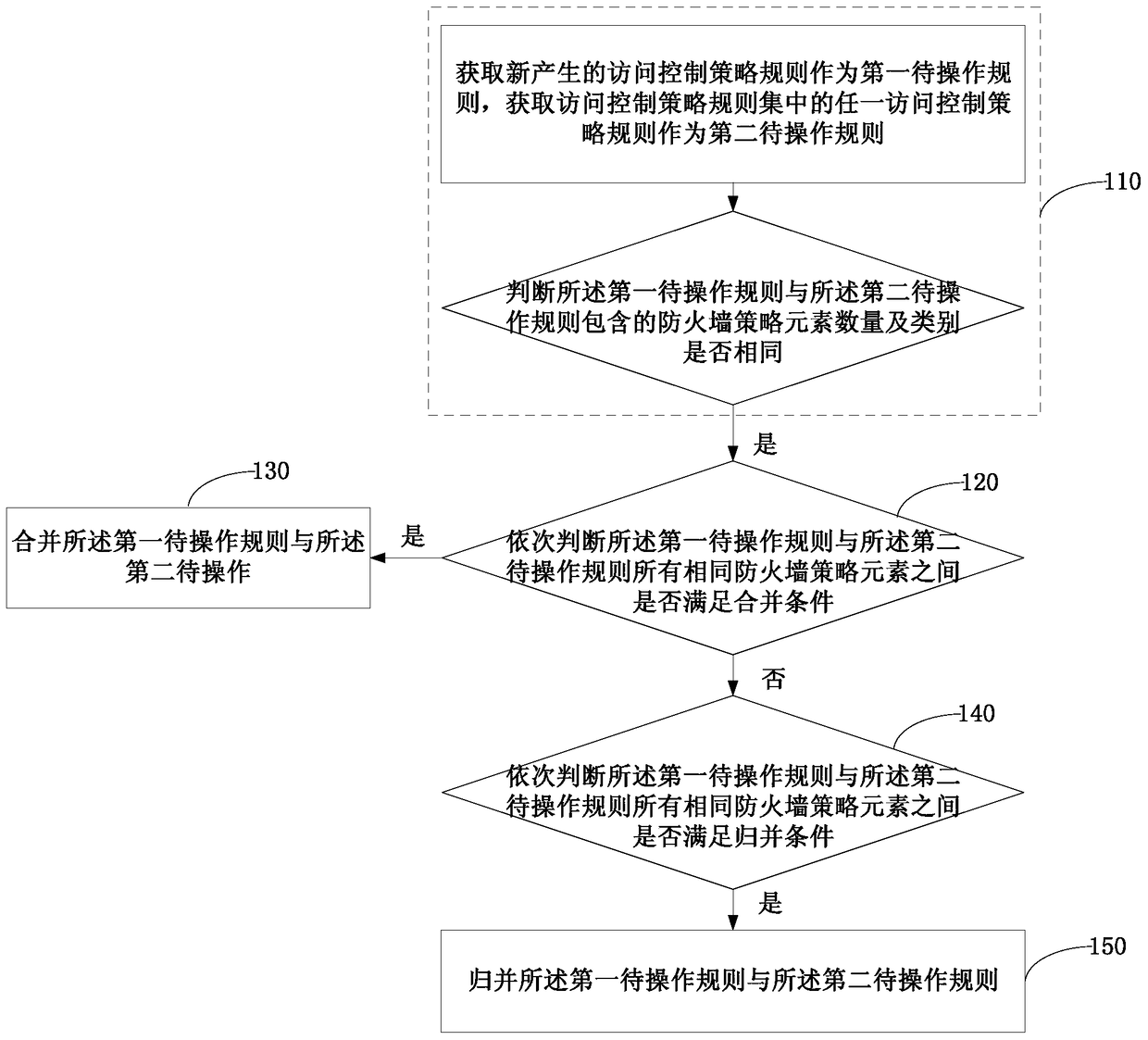
[0021] figure 2 It is a schematic flowchart of the operation method of the access control policy rule provided by Embodiment 1 of the present invention. This embodiment is applicable to the integration of access control policy rules.
[0022] see figure 2 , the operation method of the access control policy rule provided in this embodiment may specifically include the following:
[0023] Step 110: Obtain the newly generated access control policy rule as the first rule to be operated, obtain any access control policy rule in the access control policy rule set as the second rule to be operated, and determine the difference between the first rule to be operated and the first rule to be operated. Whether the number and type of firewall policy elements contained in the two pending operation rules are the same;
[0024] This embodiment is used to merge or merge the newly generated access control policy rules with the access control policies in the access control policy set, so a...
Embodiment 2
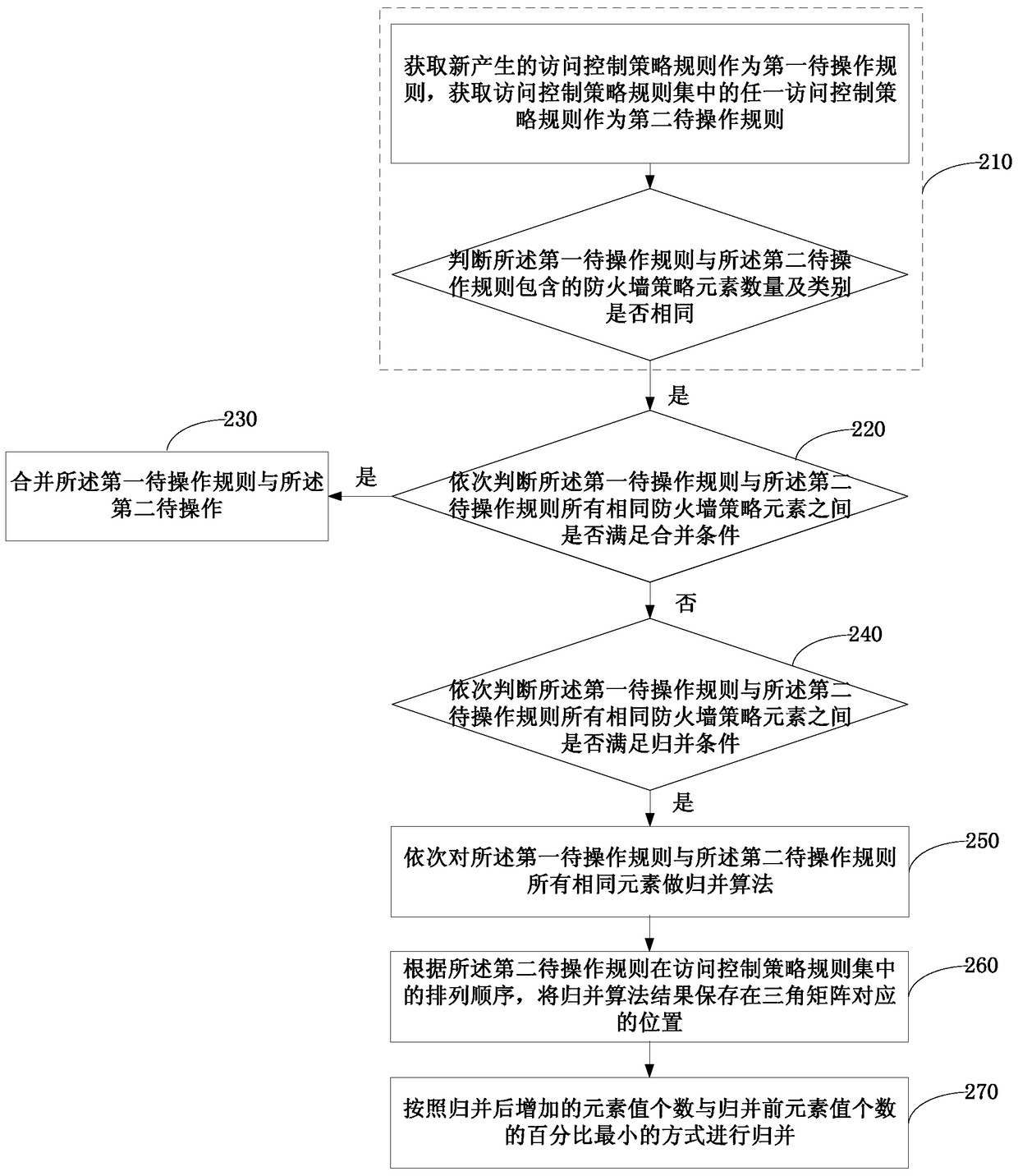
[0050] In this embodiment, on the basis of the first embodiment above, the process of merging the first to-be-operated rule and the second to-be-operated rule is further explained. image 3 It is a schematic flowchart of the operation method of the access control policy rule provided by Embodiment 2 of the present invention, as shown in image 3 As shown, the operation method of the access control policy rule provided in this embodiment may specifically include the following:
[0051] Step 210: Obtain the newly generated access control policy rule as the first rule to be operated, obtain any access control policy rule in the access control policy rule set as the second rule to be operated, and determine the difference between the first rule to be operated and the first rule to be operated. Whether the number and type of firewall policy elements contained in the two pending operation rules are the same;
[0052] Step 220, if yes, sequentially judge whether all the same firewal...
Embodiment 3
[0067] This embodiment provides an operation method of access control policy rules on the basis of the above embodiments. In the method, the integration of the first operation rule and the second operation rule is carried out in the virtual rule table. After confirmation by the user, the corresponding operation Access control policy rules stored in hardware. Figure 5 It is a schematic flowchart of the operation method of the access control policy rule provided by Embodiment 3 of the present invention, as shown in Figure 5 As shown, the operation method of the access control policy rule provided in this embodiment may specifically include the following:
[0068] Step 310: According to the access control policy rule set actually stored in the hardware, a corresponding virtual access control policy rule table is formed in the memory, which is used to realize the virtual operation before the actual operation on the access control policy rules.
[0069] Directly operating the ac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com