Reversible data hiding method and recovering method
A data hiding and recovery method technology, applied in the field of data hiding, can solve the problems of pixel redundancy, small embedding capacity, and insufficient utilization of multi-extreme value blocks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
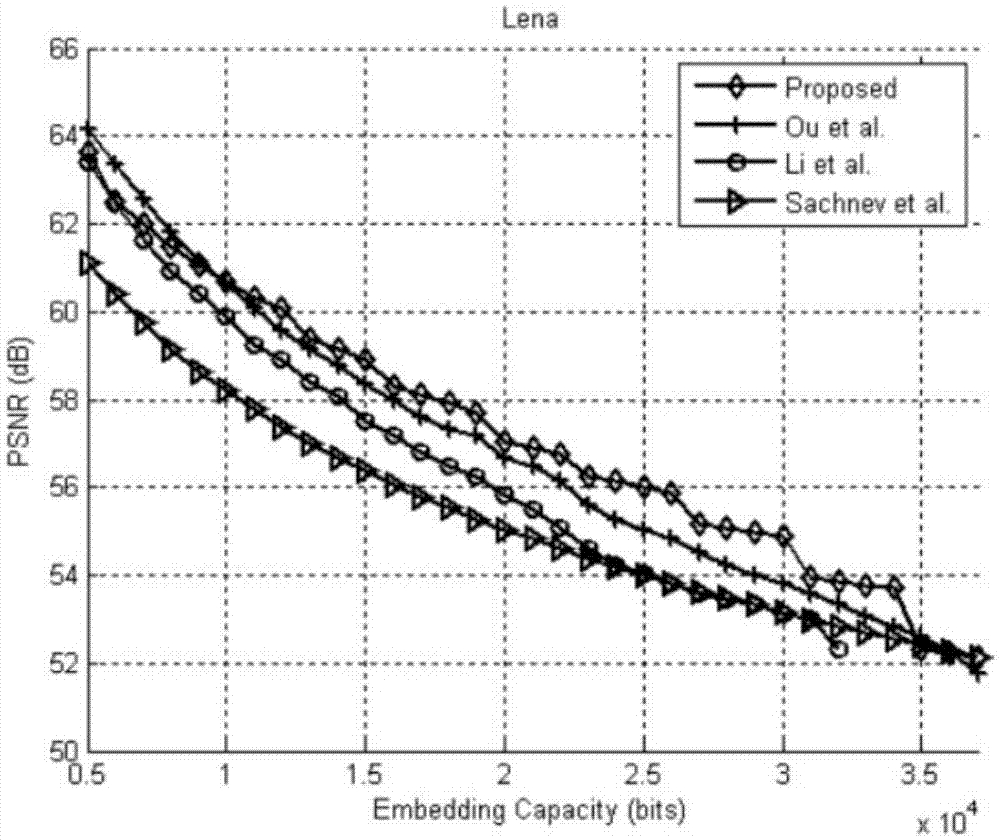
[0079] The invention relates to the technical field of data hiding, in particular to a reversible data hiding method. Reversible data hiding technology means that in the process of digital image processing, watermark information is embedded in the carrier image, and authorized users can extract the watermark information from the image after the watermark is embedded, and at the same time restore it to the original carrier image.
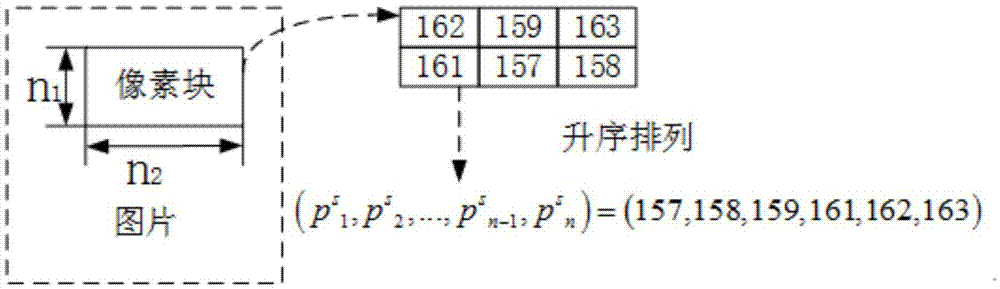
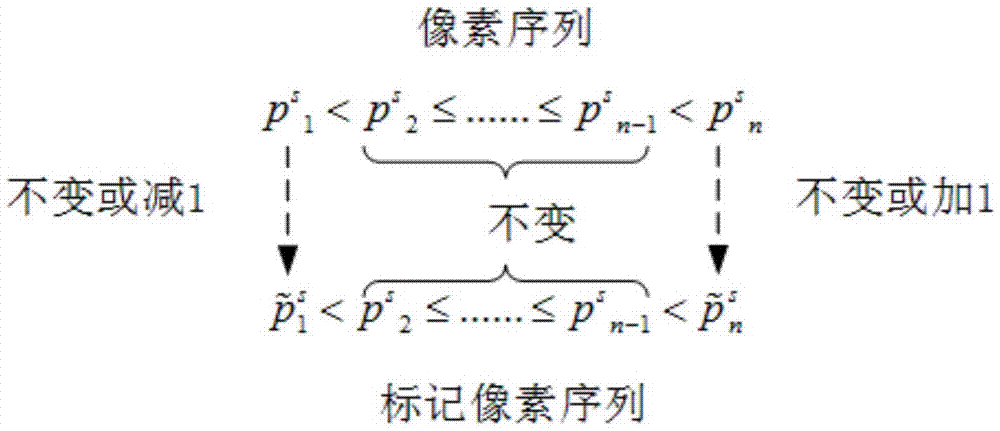
[0080] The inventive idea of the present invention is that after the image is divided into blocks, the pixel grayscale in each block has a maximum value and a minimum value, and for the entire original image, there may be many extreme values, including maximum values and minimum values. When embedding using the first embedding method, only single extreme value pixels in the block are utilized. In order to better utilize the divided pixels with equal extreme values to carry information bits, the present invention proposes a second embedding meth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com