Weak password verification and cracking method and device
A weak password and password technology, applied in the field of communication, can solve the problems of affecting work efficiency, inability to carry out unified management, efficient configuration, low efficiency of weak password cracking, etc., and achieve the effect of improving discovery ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
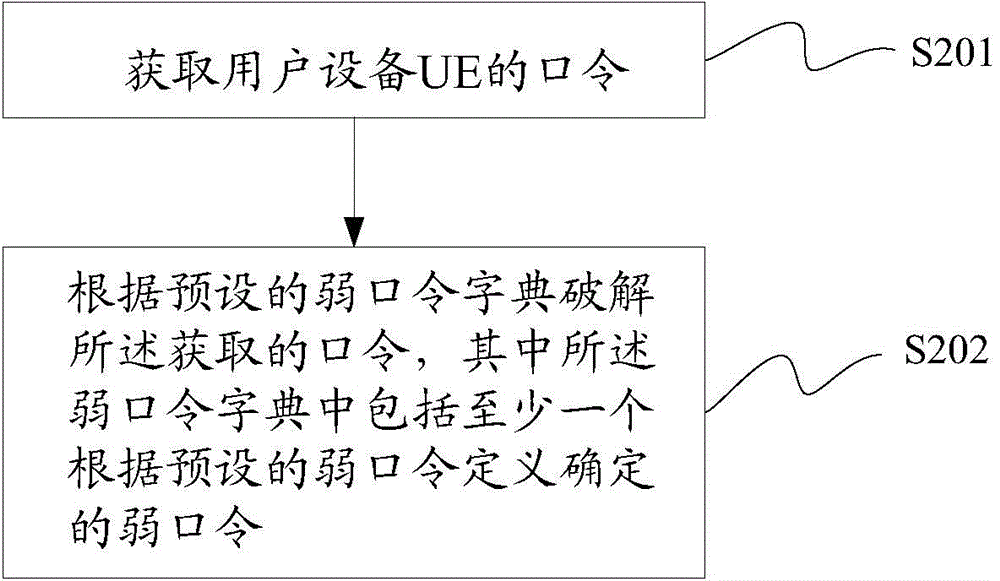
[0117] A method for checking weak passwords provided by an embodiment of the present invention includes the steps of:
[0118] Step 1: Obtain the clear text password of the UE from the security management and control platform, or the identity and access management and control system.
[0119] Among them, the security management and control platform, or the identity and access management control system is a centralized management system for account passwords, which saves the accounts and passwords of most devices.
[0120] By integrating the weak password verification module with the security management and control platform, or the identity and access management and control system, the account and password information of the UE can be obtained directly from the account and password query interface provided by the security management and control platform or the identity and access management and control system .
[0121] Step 2, according to the definition of weak passwords, it...
Embodiment 2
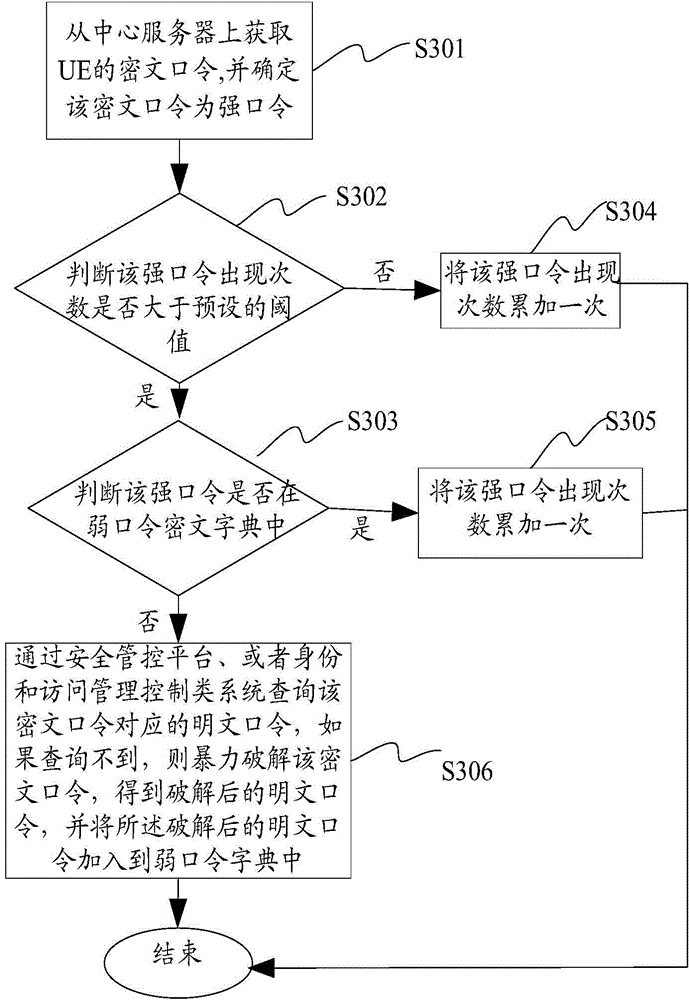
[0131] see image 3 , a method for checking weak passwords provided by the embodiments of the present invention, comprising the steps of:
[0132] S301. Obtain the ciphertext password of the UE from the central server, and determine that the ciphertext password is a strong password.
[0133] Obtain the ciphertext password of the UE from the central server. When the ciphertext password is not in the preset weak password ciphertext dictionary, it is determined that the password is not in the preset weak password dictionary, and then the ciphertext password is defined as a strong password.
[0134] S302, judging whether the number of occurrences of the strong password is greater than a preset threshold. If yes, execute S303, otherwise, execute S304.
[0135] S303, judge whether the strong password is in the weak password ciphertext dictionary, if yes, execute S305, otherwise, execute S306.
[0136] S304, accumulating the occurrence times of the strong password once.
[0137] ...
Embodiment 3
[0143] see Figure 4 , a method for checking weak passwords provided by the embodiments of the present invention, comprising the steps of:
[0144] S401. Obtain a weak password.
[0145] The weak password to be obtained is a plaintext password, which can be obtained directly from a security management and control platform, or an identity and access management control system, or obtained and cracked from a central server to obtain a plaintext password.
[0146] S402, judging whether the weak password is a newly discovered weak password, if yes, execute S403, otherwise, execute S404.
[0147] S403. Add the weak password into the weak password dictionary, and then perform S405.
[0148] S404. Accumulate the number of appearances of the weak password once, record it in the weak password dictionary, and store it in descending order of the number of appearances of the weak password.
[0149] S405, judging whether the composition rule of the weak password is in the weak password c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com