Traffic-free fraud user recognition method and recognition system
An identification method and a traffic-free technology, applied in the field of communication, can solve the problems of inability to trace the source of traffic fraud users, inability to judge malicious traffic, etc., and achieve the effect of accurate identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
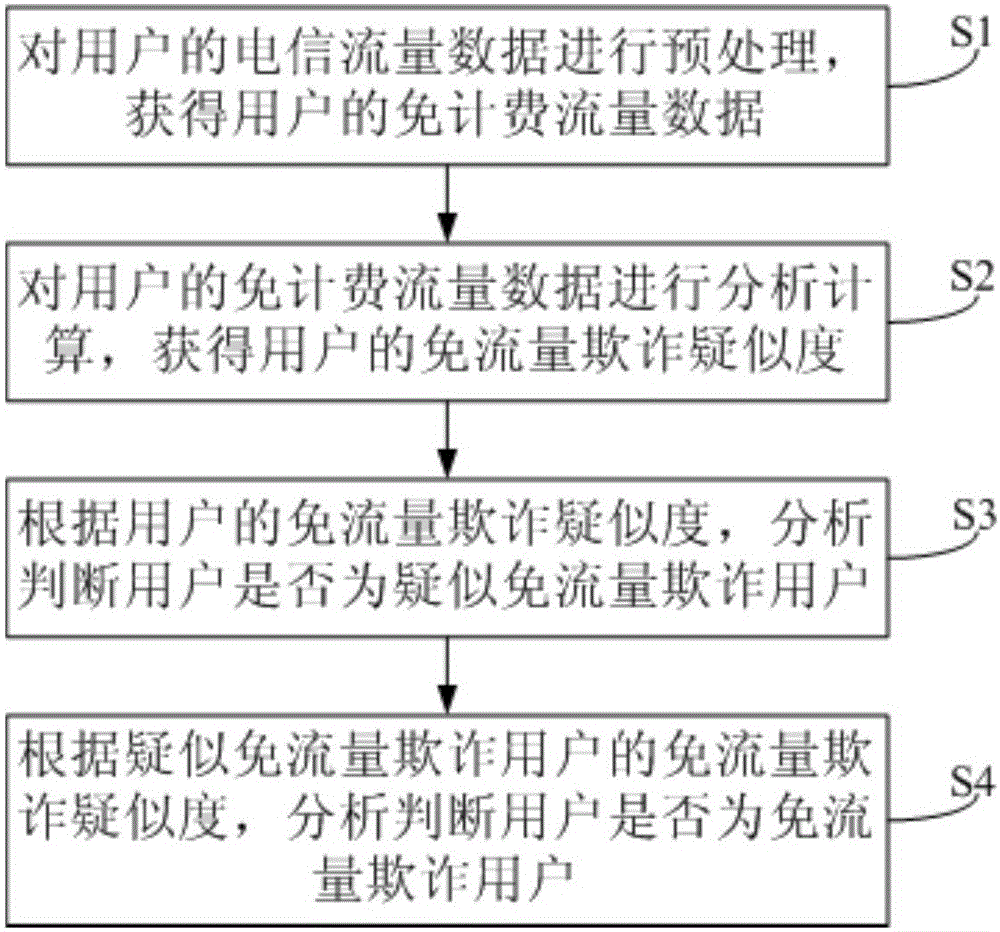
[0056] This embodiment provides a method for identifying users without traffic fraud, such as figure 1 shown, including:
[0057] Step S1: Preprocessing the user's telecommunications traffic data to obtain the user's billing-free traffic data.
[0058] Step S2: Analyzing and calculating the user's free-of-charge traffic data to obtain the user's suspicion of free-of-charge fraud.
[0059] Step S3: According to the user's suspicion of data-free fraud, analyze and determine whether the user is a suspected data-free fraud user.
[0060] Step S4: Analyze and determine whether the user is a traffic-free fraud user according to the traffic-free fraud suspicion degree of the suspected traffic-free fraud user.
[0061] Through the above identification method, by analyzing and calculating the user’s billing-free traffic data, it is possible to effectively and accurately judge the malicious free billing traffic in the form of a normal network protocol, thereby effectively and accurate...
Embodiment 2
[0063] This embodiment provides a method for identifying users without traffic fraud, including:
[0064] Step S1: Preprocessing the user's telecommunications traffic data to obtain the user's billing-free traffic data.
[0065] This step specifically includes:
[0066] Step S11: Counting the total traffic used by the user within the first set time period.
[0067] In this step, the first set time period can be set arbitrarily, for example, the first set time period can be set to 30 days.
[0068] Step S12: Counting the traffic of the bill-free special traffic type used by the user within the first set time period; the traffic of the bill-free special traffic type is the traffic of atypical users' mobile Internet services and functional network access free of billing flow.
[0069] In this step, the traffic of atypical users’ mobile Internet services, such as normal Internet business OTT (various application services provided to users through the Internet) traffic, TCP / IP (...
Embodiment 3
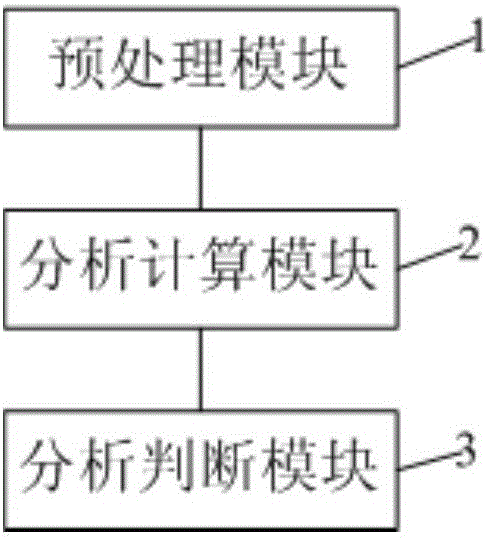
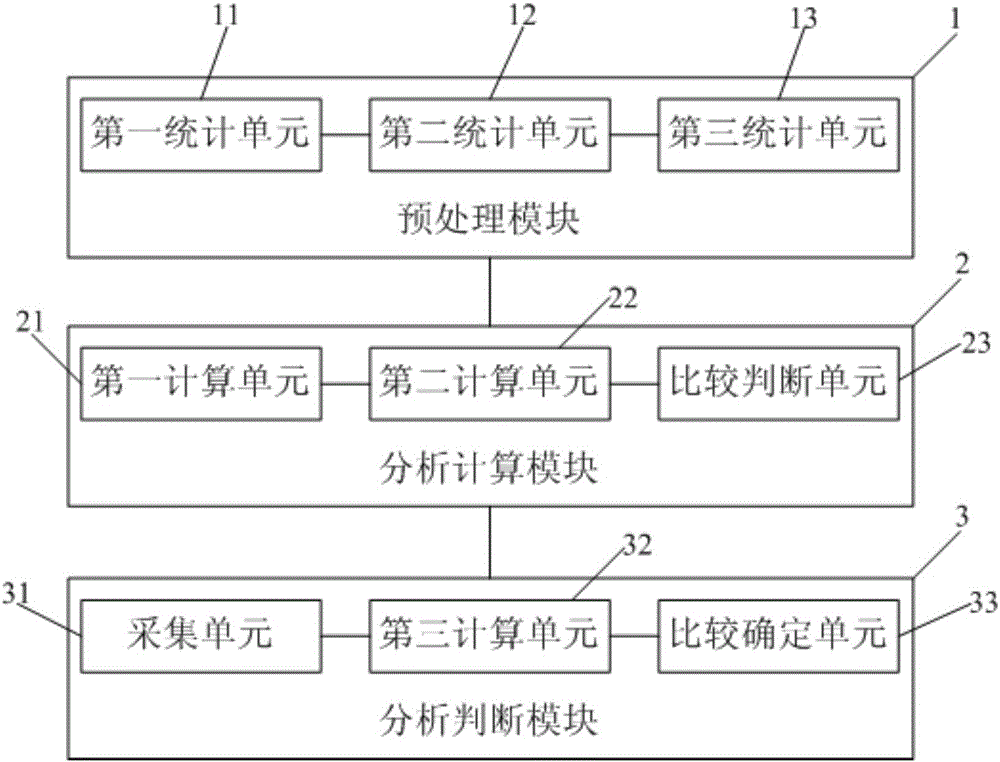
[0095] This embodiment provides an identification system for avoiding traffic fraud users, such as figure 2As shown, a preprocessing module 1 is included, which is used to preprocess the user's telecommunications traffic data to obtain the user's billing-free traffic data. The analysis and calculation module 2 is used to analyze and calculate the user's free billing traffic data to obtain the user's suspicion of free traffic fraud; and according to the user's suspicion of free traffic fraud, analyze and judge whether the user is a suspected free traffic fraud user. The analysis and judgment module 3 is used for analyzing and judging whether the user is a traffic-free fraud user according to the traffic-free fraud suspicion degree of the suspected traffic-free fraud user.
[0096] The identification system in this embodiment analyzes and calculates the user’s toll-free flow data through the analysis and calculation module, and can effectively and accurately judge the malicious...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com