Method and device for finding malicious service provider of composite service in cloud system
A combined service and cloud system technology, applied in the field of computer security, can solve problems such as vulnerability to malicious attacks, unreal data processing, inability to accurately identify attackers, etc., and achieve the effect of restraining and limiting the scope of attack damage and suppressing partner attacks.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
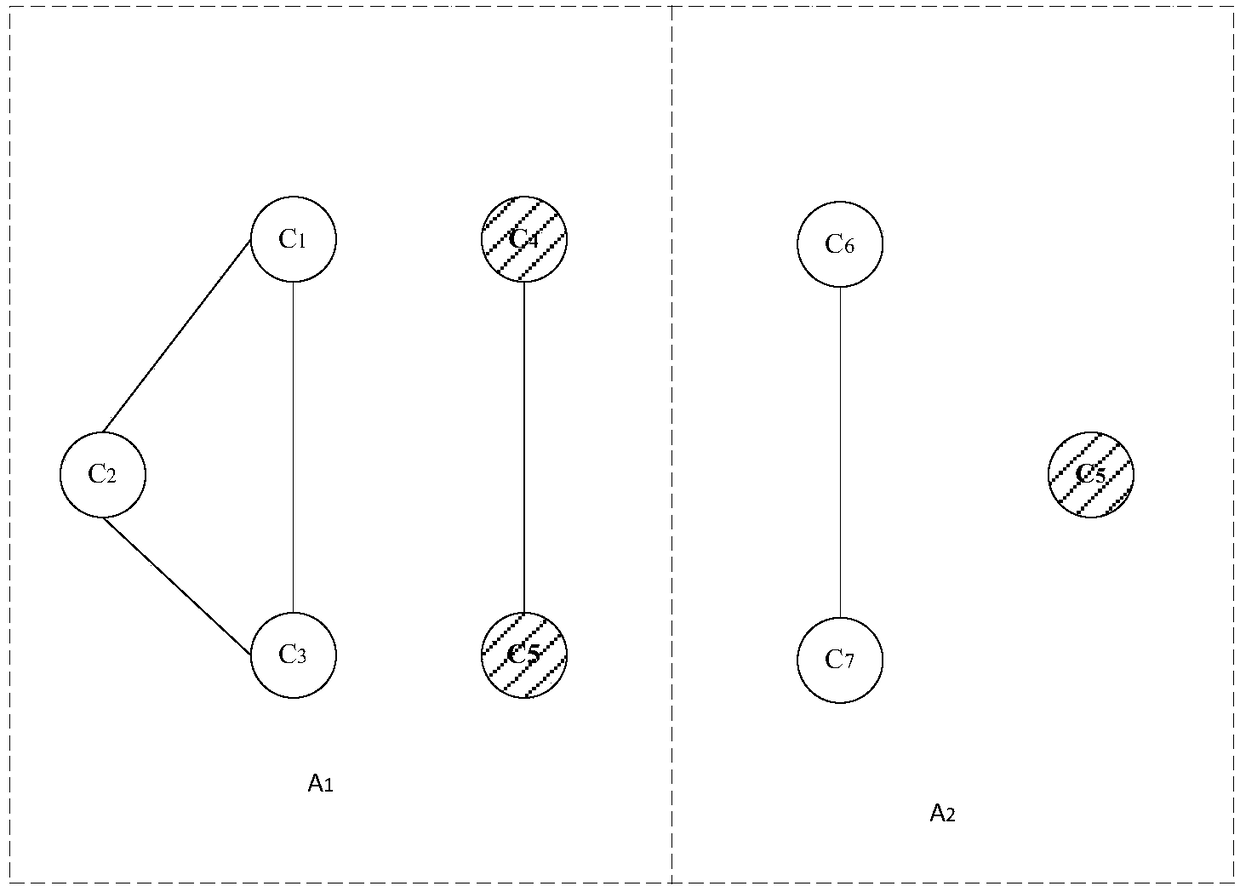
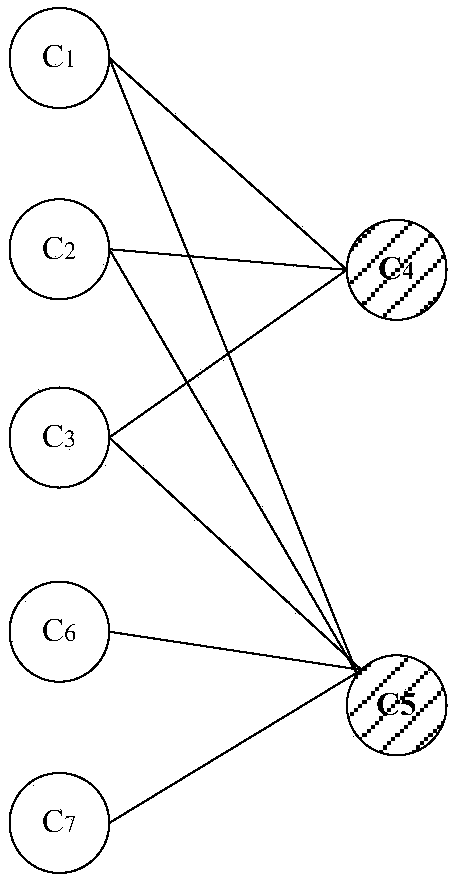
[0044] First of all, it needs to be explained that SaaS (Software-as-a-Service, short for software as a service), with the development of Internet technology and the maturity of application software, a completely innovative software application model that began to emerge in the 21st century , the concept of SaaS cloud-based software as a service and service-oriented architecture allows application service providers to provide their applications through large-scale cloud computing infrastructure. For example, Amazon Web Services and Google AppEngine both provide a set of support for enterprise Application services for high-level applications and big data processing. Each service component provides specific data processing functionality, such as sorting, filtering, correlation, or data mining. Each service component can have one or more input ports, and d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com