Method and system for user identity verification, and campus management system
A technology of user identity and verification method, which is applied in the field of user identity verification method, system and campus management system, can solve the problems of not solving multiple identities of special users, unable to verify multiple identities of the same user, and other children cannot enjoy it, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
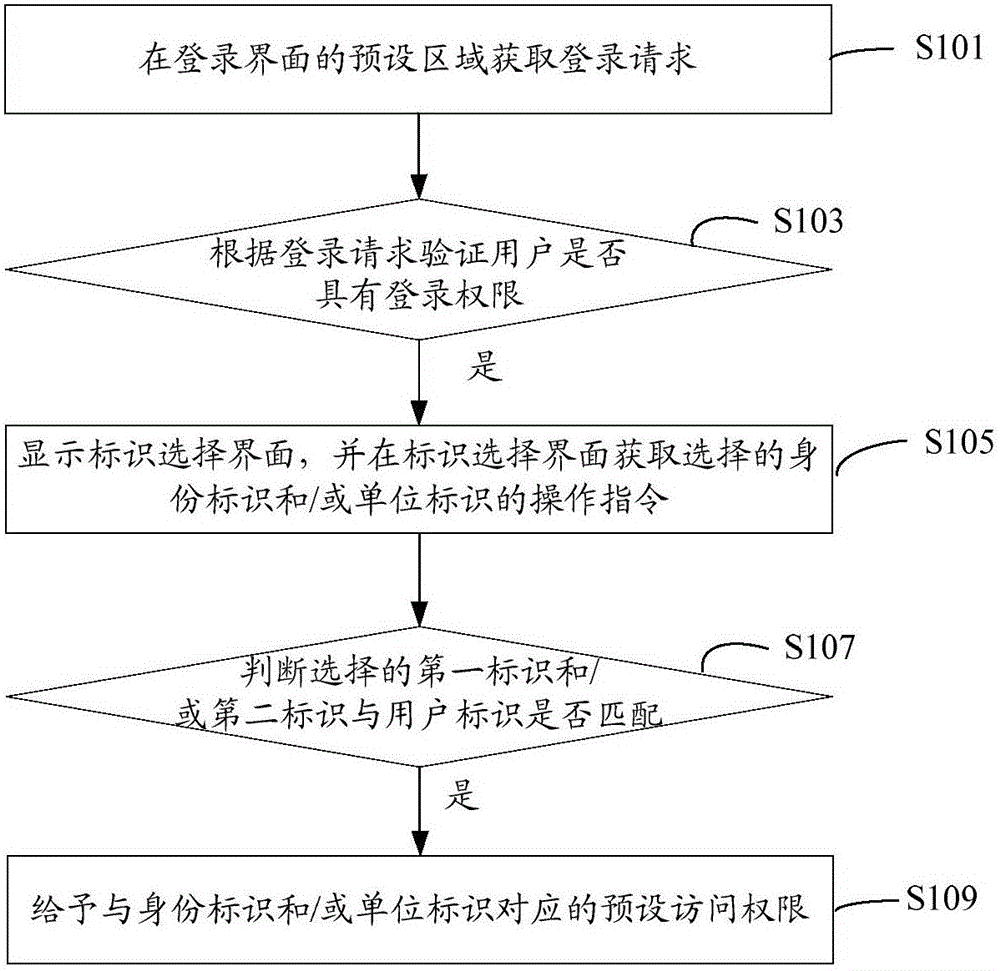
[0076] Such as figure 1 As shown, a user authentication method includes the following steps:
[0077] S101: Obtain a login request in a preset area of a login interface.
[0078] A login request includes a user ID and a user password. In this embodiment, the user identifier may be the user name, mobile phone or email address registered by the user in the corresponding system, and is used to distinguish different unique identifiers of different users.
[0079] S103: Verifying whether the user has login authority according to the login request.
[0080] In one embodiment, the user registers as a registered user in the corresponding system by using the user ID and user password in advance, or the administrator enters the user ID and initial password in the background to become a registered user. When the user logs in to the corresponding system, according to the user ID and user password to verify that the user has login permissions. In another embodiment, the user can also...
Embodiment 2
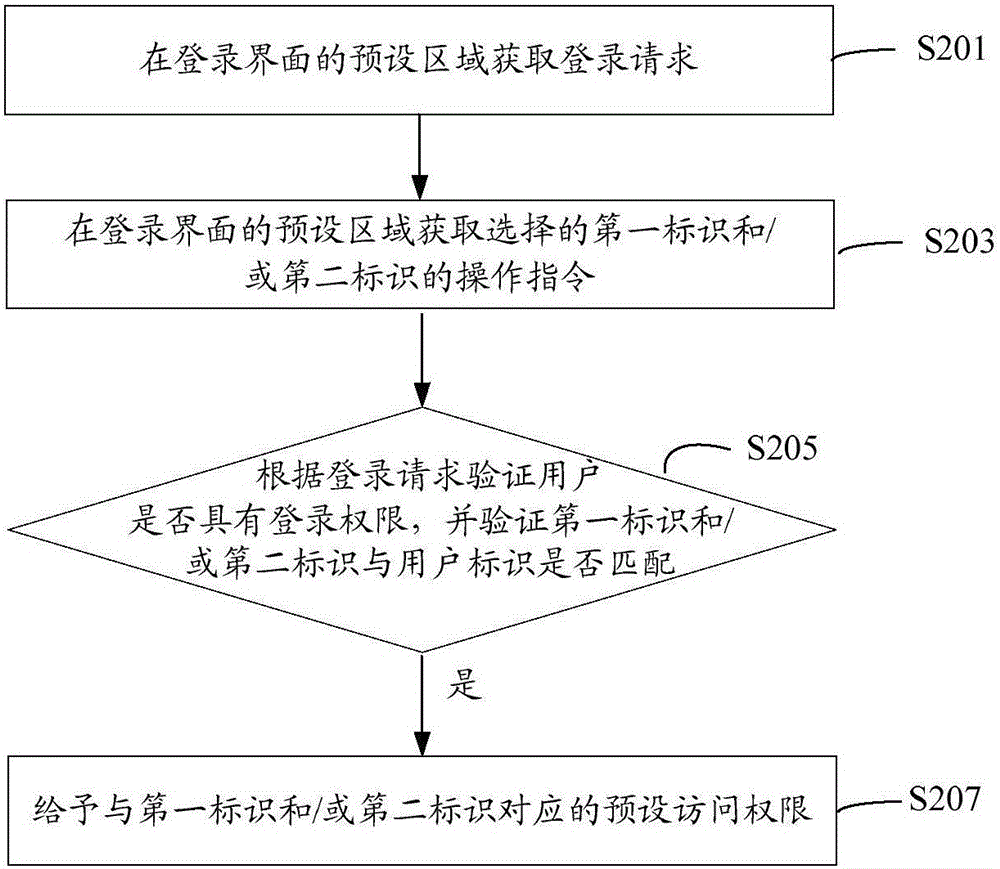
[0103] Such as image 3 As shown, a user authentication method includes the following steps:
[0104] S201: Obtain a login request in a preset area of a login interface.
[0105] A login request includes a user ID and a user password. In this embodiment, the user identifier may be the user name, mobile phone or email address registered by the user in the corresponding system, and is used to distinguish different unique identifiers of different users.
[0106] S203: Obtain an operation instruction of the selected first identifier and / or second identifier in a preset area of the login interface.
[0107] S205: Verify according to the login request whether the user has login authority, and verify whether the first identifier and / or the second identifier matches the user identifier.
[0108] If yes, perform step S207: give the preset access authority corresponding to the first identifier and / or the second identifier.
[0109]The user identity verification method of the pre...
Embodiment 3
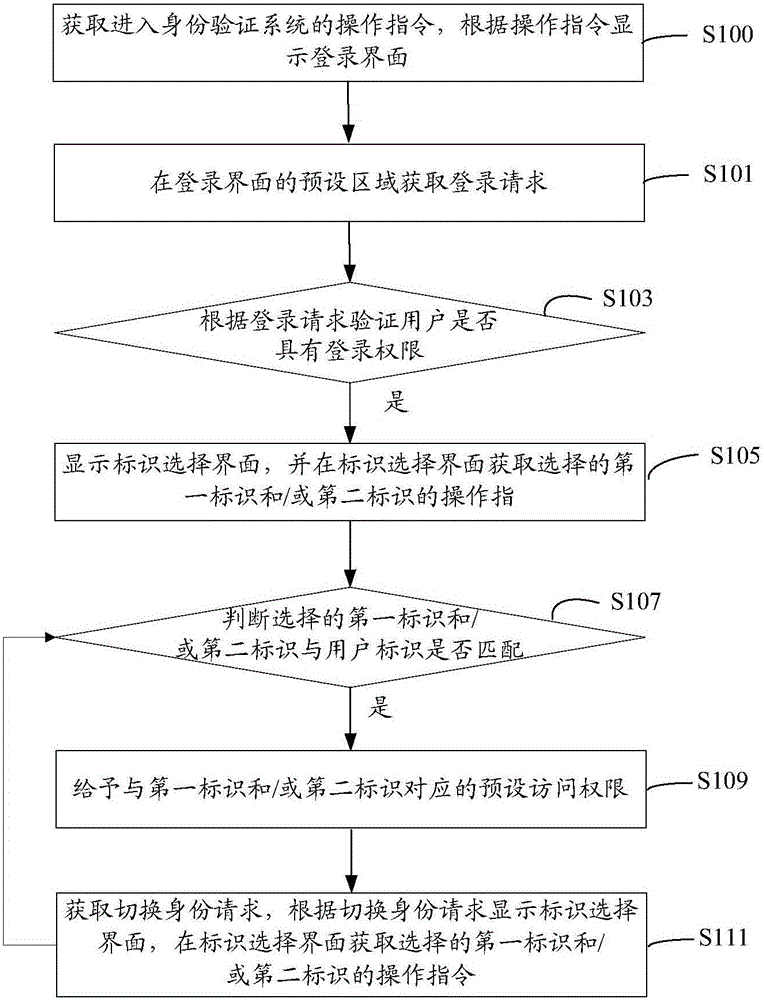
[0116] Such as Figure 5 As shown, a user authentication method includes the following steps:
[0117] S301: Obtain an operation instruction for entering the identity verification system, and display an identifier selection interface according to the operation instruction.
[0118] S303: Obtain an operation instruction of the selected first logo and / or second logo on the logo selection interface.
[0119] S305: Display a login interface according to the first identifier and / or the second identifier.
[0120] Specifically, the system corresponding to the first identifier and / or the second identifier is displayed according to the selected first identifier and / or the second identifier. For example, if the user only has the first identification as a teacher and the second identification as a school A and a class B, then it corresponds to the corresponding system of the school A.
[0121] S307: Obtain a login request in a preset area of the login interface. A login request in...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com