An Identity-Based Authenticable Dynamic Group Key Agreement Method
A group key negotiation and dynamic technology, which is applied in the field of network communication security, can solve the problems that cannot meet the actual application requirements, large message volume, high network load, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
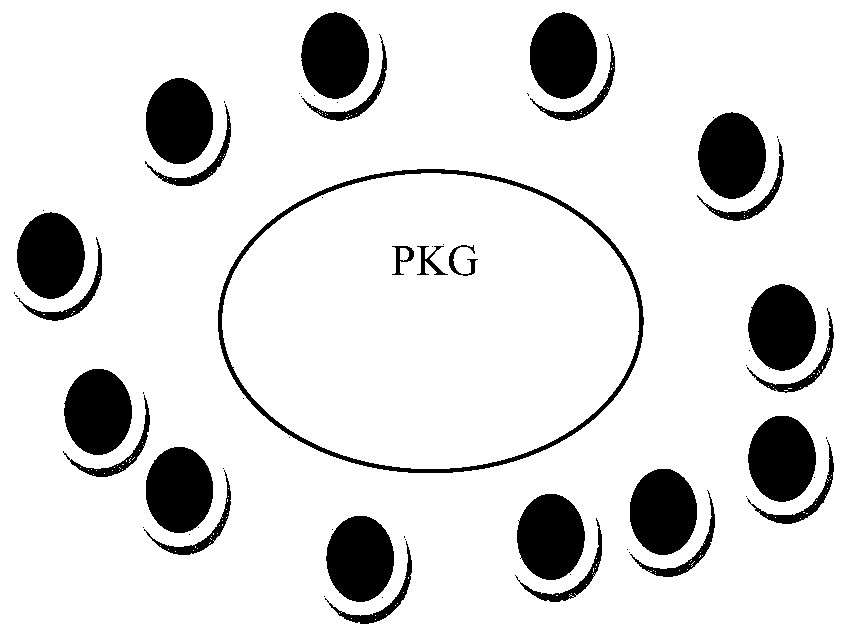
[0111] In this embodiment, the system is composed of a PKG and multiple group user nodes, such as figure 1 shown. Each user can determine the group they are in and know their left and right neighbors, and PKG is responsible for the generation and distribution of necessary parameters.
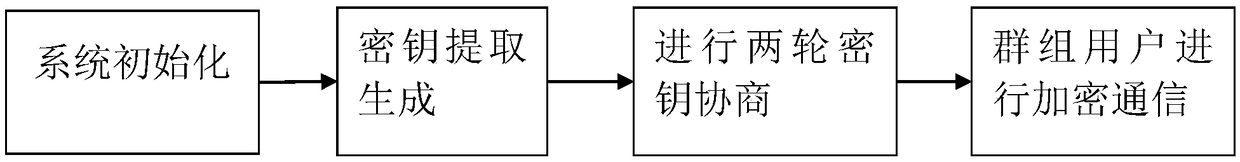
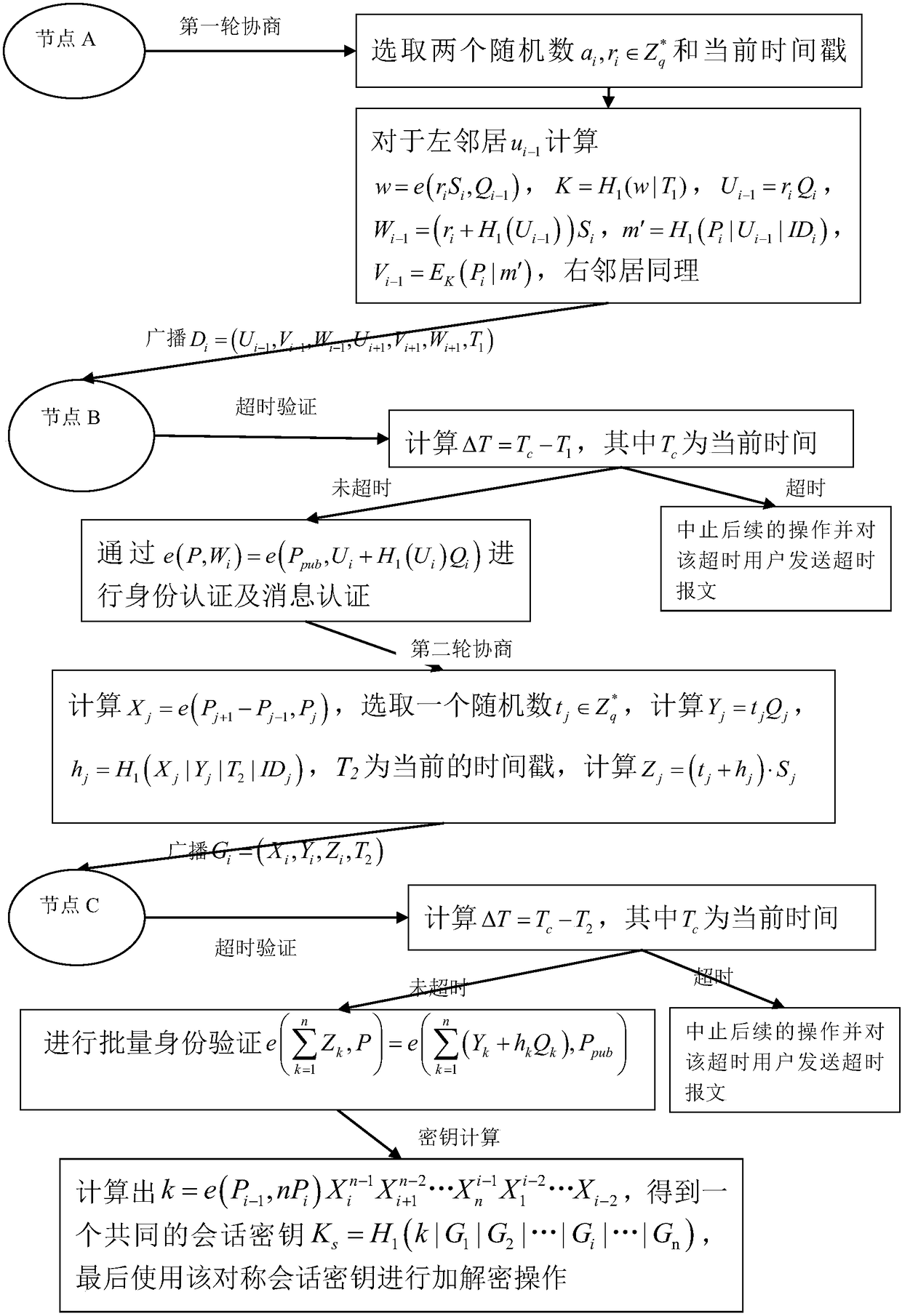
[0112] According to this embodiment figure 2 The steps shown implement key agreement, and the specific process is as follows image 3 shown.
[0113] First, you need to use a server as the private key generator PKG, and deploy the hosts in the network in a wired or wireless form so that they can communicate with each other. Deploy the software corresponding to this agreement on each user host to complete subsequent operations.
[0114] 1. Initialize the system network:
[0115] The private key generator PKG generates and discloses system parameters {q, G 1 ,G 2 ,P,e,P pub ,H 0 ,H 1 ,E k ,D k}, which is the public parameter, s is the private key of the PKG to be kept secret, P pub i...
Embodiment 2
[0162] In order to ensure the forward and backward secrecy of dynamic group key negotiation, the protocol must ensure that the session key must be updated every time a member changes. It is also impossible to calculate the content of the group communication after it leaves, that is to say, the independence of the key is the prerequisite for ensuring the dynamic nature of the protocol.
[0163] When a new user joins an existing user group, join through the following process:
[0164] When a new user u j When wishing to join the current network, it first needs to confirm its legitimacy to PKG and submit a joining request. After passing the access control, PKG assigns the corresponding private key according to step 2. Second, user u is broadcast by PKG j identity information and user u j join request. Finally, start the group key update process, as follows:
[0165] only u j The first round of negotiation needs to be performed with its left and right neighbors according to ...
Embodiment 3
[0170] When a user leaves the group, leave through the following process:
[0171] when a user u j To leave the current network, first it needs to confirm its identity to PKG and submit a leave request, and then PKG broadcasts user u j identity information and user u j leave request, when u j When being expelled by PKG for some reason, PKG will send the above message directly. Then start the group key update process, as follows:
[0172] only u j The left and right neighbor u j-1 and u j+1 The operation needs to be carried out according to step 3 described in Embodiment 1, and they do not need to re-select the random number a used to generate the temporary key to reduce the amount of calculation and improve efficiency.
[0173] then u j-1 and u j+1 Perform authentication and decryption operations according to step 4. The specific steps are the same as those in the initialization phase, that is, only uj-1 and u j+1 Perform the second round of negotiation in Step 4 in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com