Hidden hyperlink detection method based on stack
A dark chain detection and dark chain technology, applied in the field of network security, can solve the problem that website administrators cannot quickly and accurately detect and locate dark chains.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
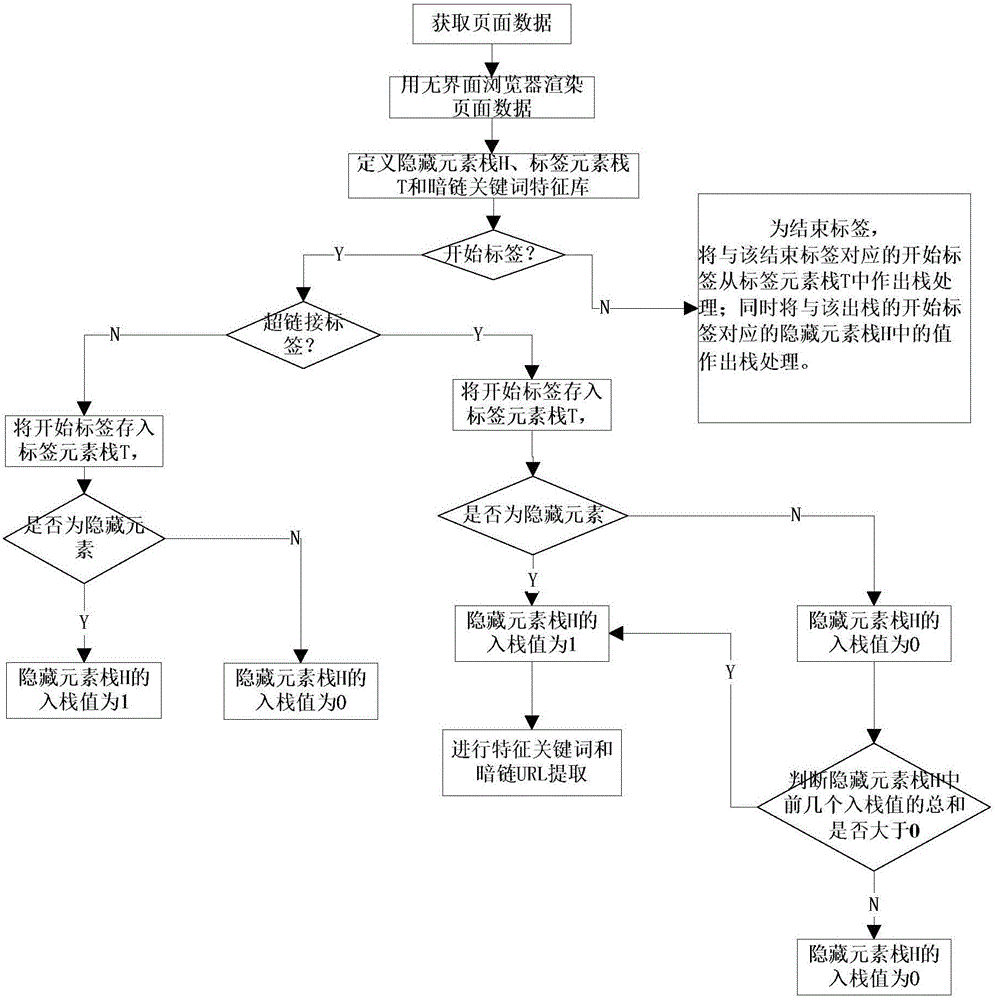
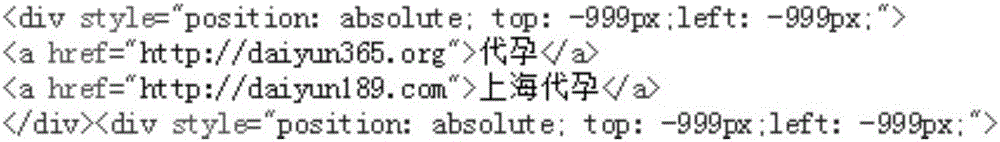
[0053] First, send an HTTP request to the web site server to be detected, such as figure 2 As shown, then utilize multi-threaded web crawler technology to grab the Web page to be detected, and the Web page to be detected returns page data; the part of the returned page data is as follows image 3 shown;
[0054] Secondly, use the interfaceless browser to render the page data, obtain the rendered web page, and complete the rendering by executing the JS and CSS codes on the page;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com