Full-format network-wide base station type shielding control conference system and shielding control method
A conference system, a full-scale technology, applied in the field of full-scale network-wide base station shielded management and control conference systems, can solve the problems of insufficient shielding effect, high cost, inability to achieve management and call bill analysis, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
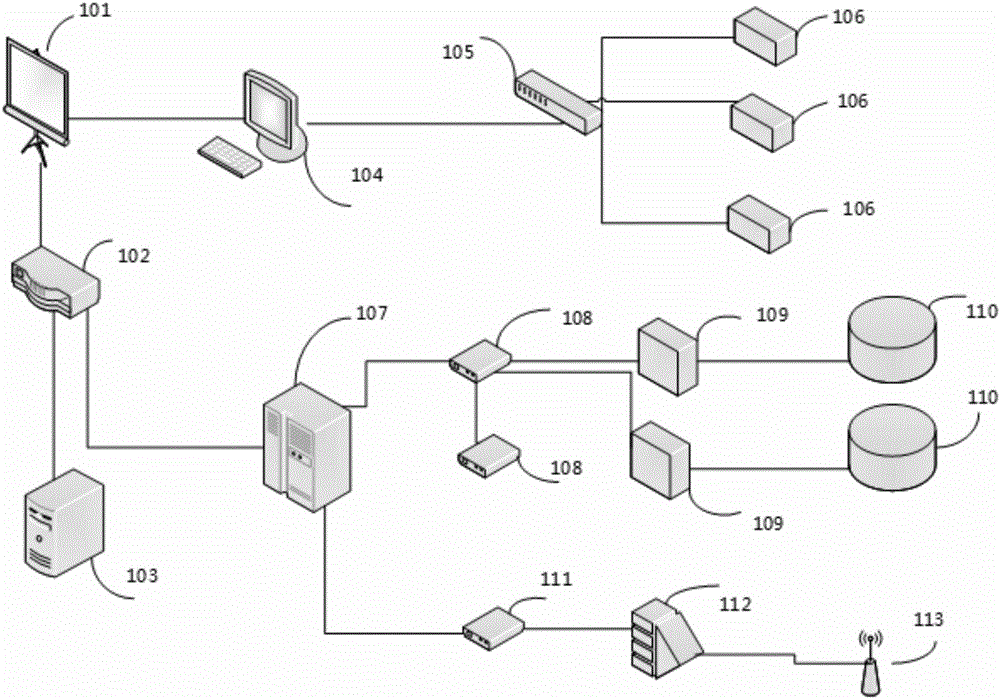
[0031] Such as figure 1 As shown, the present invention provides a full-standard full-network base station shielding management and control conference system, including a shielding subsystem, a detection and positioning subsystem, and an integrated data processing subsystem; the shielding subsystem is used for mobile communication in the entire network Signal shielding and control; the detecting and positioning subsystem is used to detect mobile terminals and obtain positioning information; the comprehensive data processing subsystem is used to collect, summarize, analyze, warn and manage equipment configuration.
[0032] The shielding subsystem is composed of a shielding master device 107 , a shielding slave device and a covering antenna. The shielding slave device is used for shielding and controlling the covering antenna, and uploads shielding and controlling information to the shielding master device 107 .
[0033] The shielding slave equipment includes an indoor shieldin...
Embodiment 2
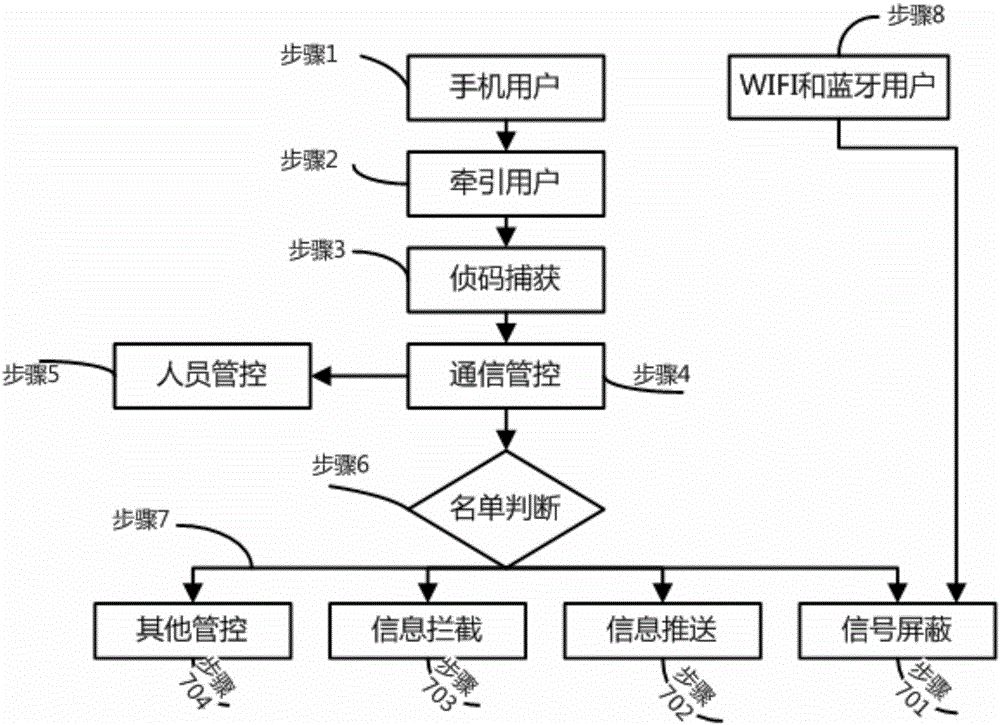
[0037] On the basis of the above embodiments, the present invention also provides a shielding control method for a full-standard, full-network, base station-type shielding control conference system, including the following steps:
[0038] Step 1: Confirm the mobile phone user;
[0039] Step 2: Attract mobile phone users;
[0040] Step 3: Conduct code detection and capture on the traction user;
[0041] Step 4: Carry out communication management and control for the users captured by the detection code, enter step 5 for mobile phone users who are not among the preset personnel; enter step 6 for mobile phone users among the preset personnel;
[0042] Step 5: Perform personnel control on the mobile phone user;
[0043] Step 6: Carry out list judgment, and proceed to step 7 according to the information after the list judgment;
[0044] Step 7: Carry out management and control processing, specifically step 701: signal shielding; step 702: information push
[0045] Send; step 703...
Embodiment 3
[0051] On the basis of the above embodiments, it is further described that the system and method of the present invention is a high-performance, scalable defined radio (SDR) platform, which can be used to design and deploy the next generation wireless communication system. Its hardware architecture combines two extended bandwidth daughterboard slots covering DC-6GHz or even up to 120MHz baseband bandwidth, multiple high-speed interface options (PCIe, dual 10 Gigabit Ethernet, dual 1 Gigabit Ethernet), and A large user-programmable Kintex-7FPGA in a convenient desktop or rack-mountable half-width 1U form factor. In addition to providing best-in-class hardware performance, the open source software architecture provides cross-platform UHD driver support making it compatible with a large number of supporting development frameworks, reference architectures and open source projects.
[0052] The signal shielding: refers to the whole network (2G / 3G / 4G) wireless communication signal s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com