Method for dispatching safety sensitive workflow based on task replication in cloud computing
A technology of task replication and scheduling method, applied in the field of cloud computing, can solve problems such as insufficient consideration of intermediate data security requirements, achieve the effect of minimizing completion time and operating cost, and improving use efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0081] 3. Model and problem description
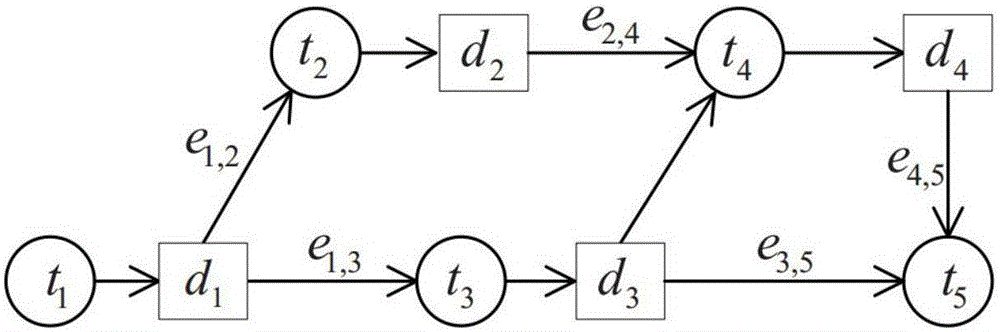
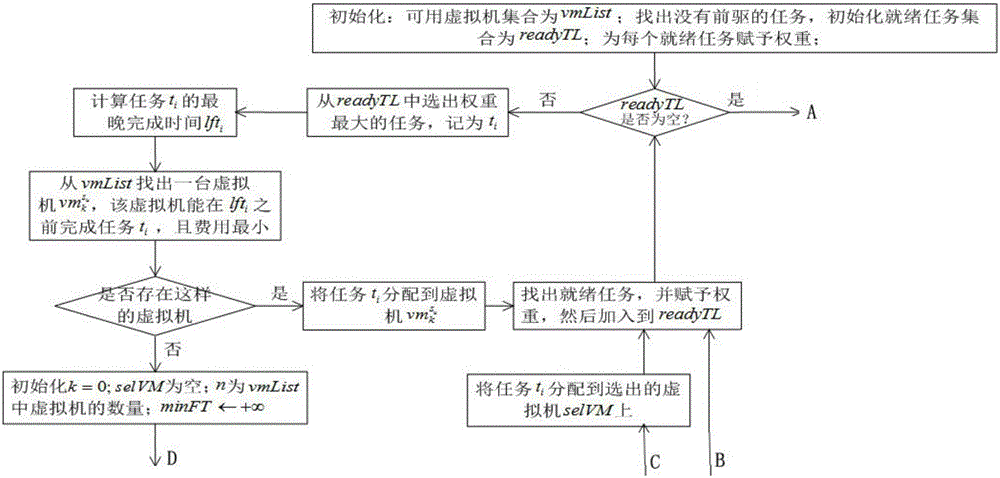
[0082]In this part, the present invention sequentially presents IaaS cloud computing, workflow, and data security models. On the basis of the above models, describe the scheduling model of the workflow, and consider the security requirements of the application.
[0083] 3.1 Model
[0084] 3.1.1 IaaS cloud computing platform
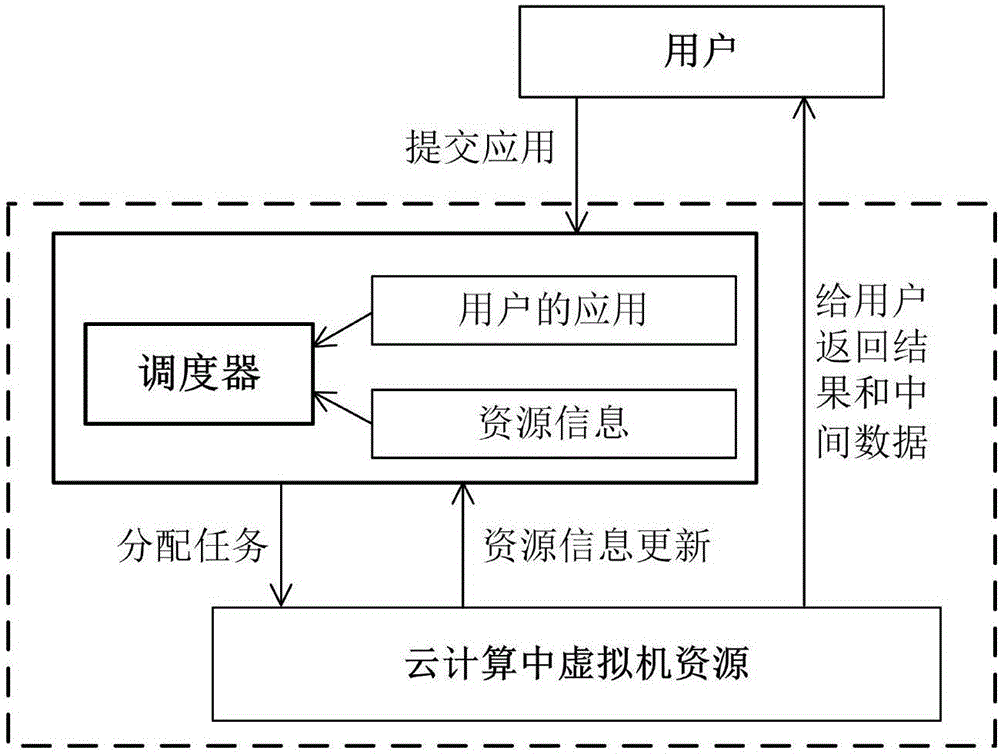
[0085] Similar to literature [16,17,22], the present invention focuses on Infrastructure as a Service (IaaS) cloud platforms, such as figure 1 shown. Throughout the architecture, the scheduler associates users with the IaaS platform. The top layer is the user, which dynamically submits the workflow to the scheduler, and the bottom layer is the IaaS platform, which provides virtual machines (VMs) for users on demand. The scheduler is a key component in the IaaS platform, responsible for scheduling workflow tasks and selecting encrypted instances for intermediate data. The invention studies the relevant rules ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com