Mobile phone information protection lock
A mobile phone information and protection lock technology, which is applied in telephone communication, secure communication devices, and key distribution, can solve problems such as not being able to fully and effectively ensure user information security, not being able to effectively prevent user information from leaking, and affecting users' normal use of mobile phones. Achieve good application prospects, optimize mobile phone experience, and simple structure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
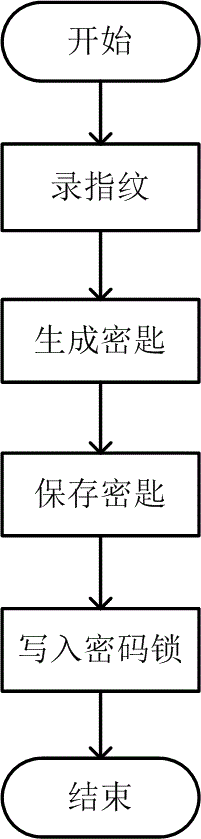
[0045] Below in conjunction with accompanying drawing, the present invention is described in further detail:
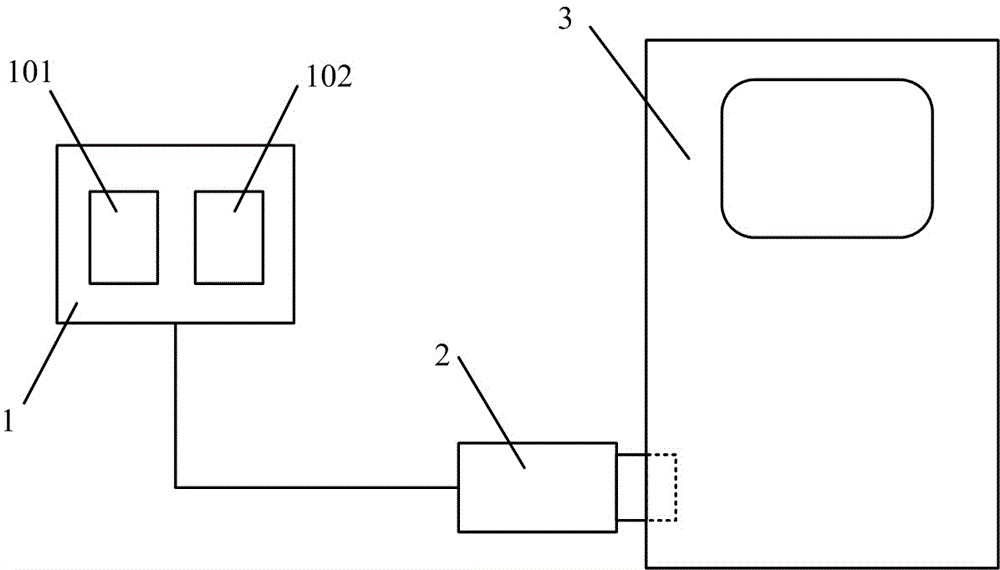
[0046] Such as figure 1 As shown, the mobile phone protection lock structure of the present invention includes a protection lock (1), a joint (2), and a mobile phone (3). The protection lock (1) includes a memory (101) and an auxiliary circuit (102), connected to the mobile phone (3) through the joint (2), the auxiliary circuit (102) is other necessary circuits to ensure the work of the protection lock (1), and the memory (101 ) is used to save the key.
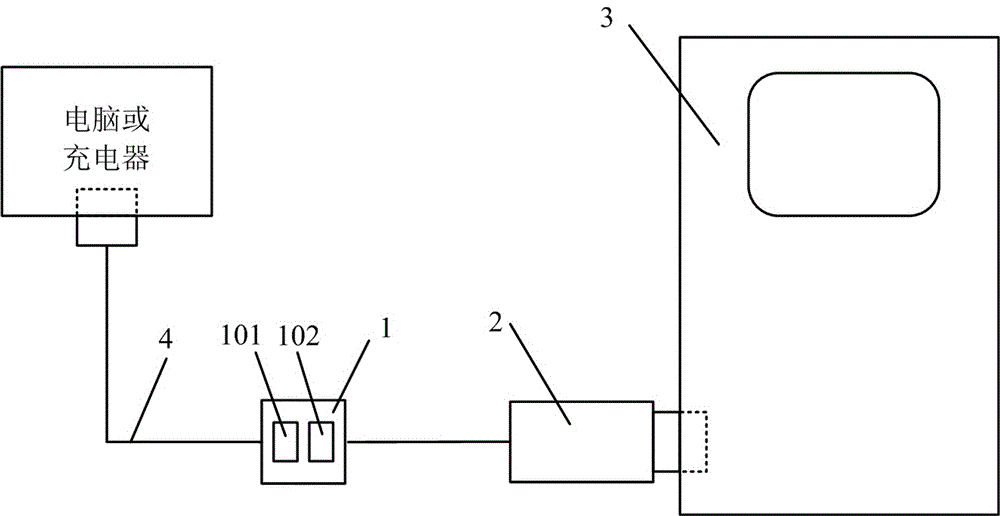
[0047] In order to make the present invention more concise and convenient, as figure 2 As shown, the protection lock (1) and connector (2) are integrated with the data cable (4) of the mobile phone (3), and the mobile phone (3) is connected to a charger or a computer and other equipment through the data cable (4). Or when the mobile phone is connected to the computer, the verification process is automatically com...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com