Brute force attack prevention method, device and system
A technology of brute force and login information, applied in the computer field, can solve the problems of inability to brute force the hosts in the cluster to crack each other's defenses, low defense efficiency, and inability to defend against malicious attackers
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
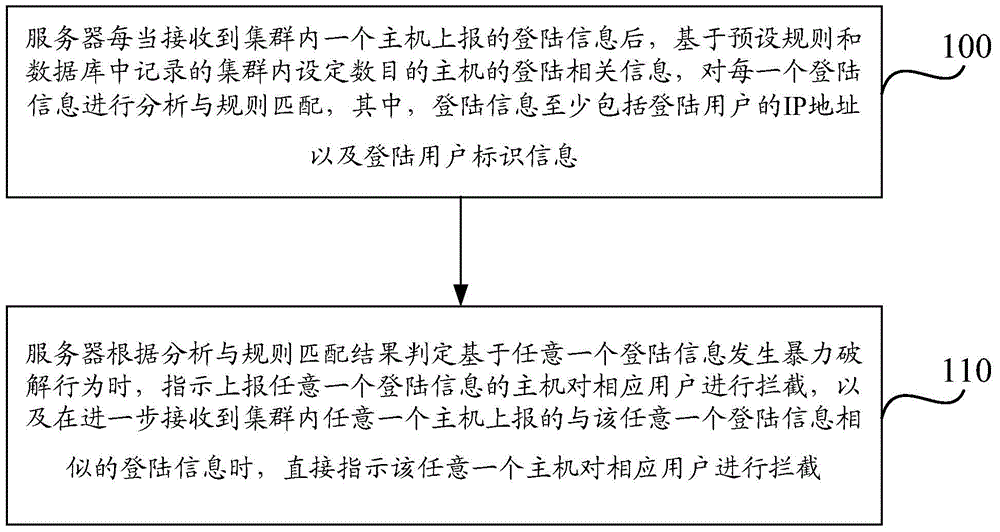
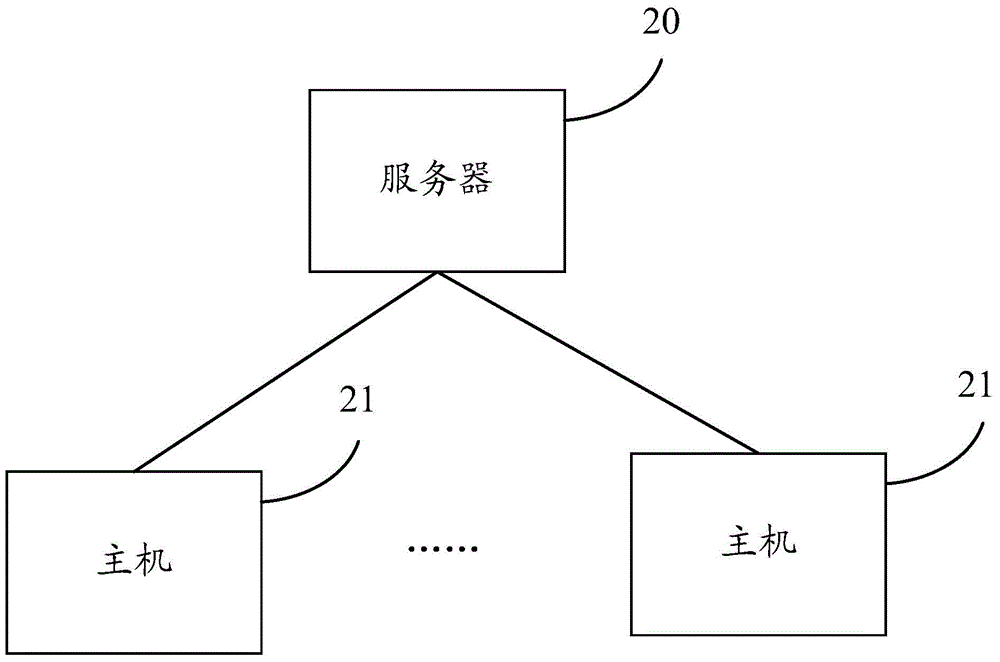
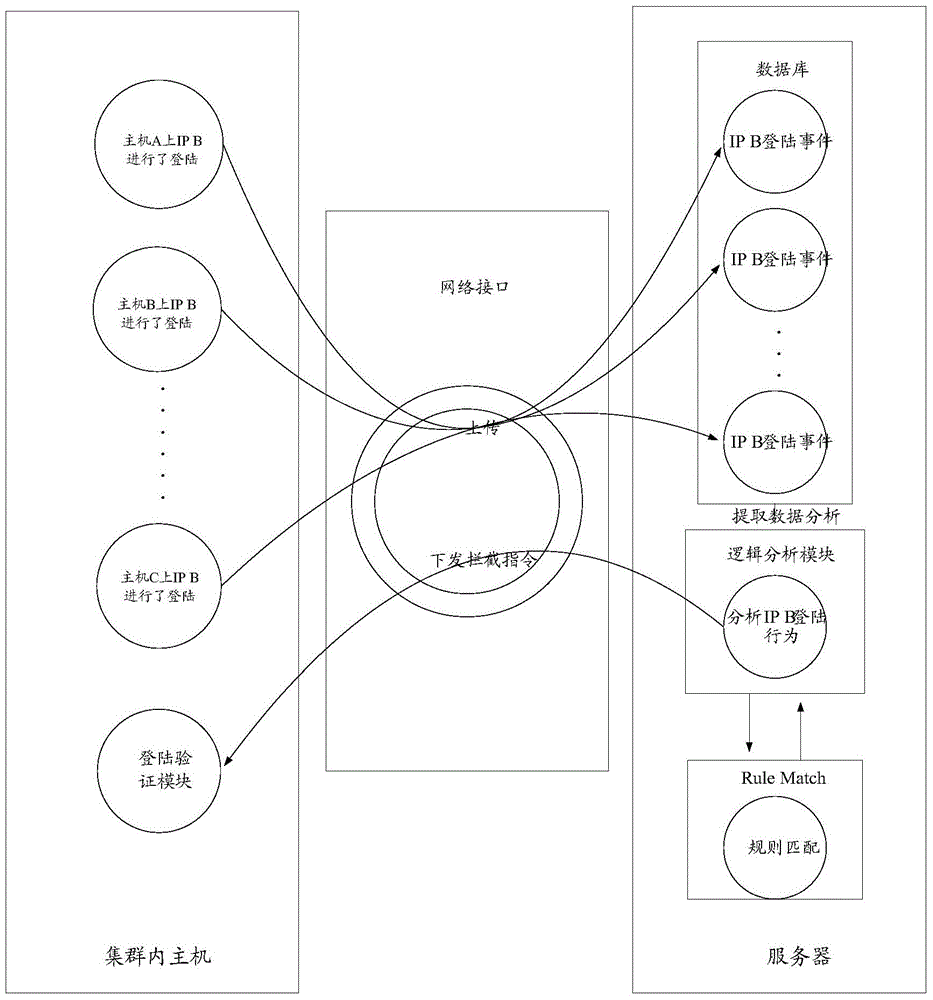
[0063] The embodiment of the present invention provides a method, device and system for preventing brute force cracking. The system is an anti-brute force cracking cloud system based on the Linux system login verification module (Pam). By connecting all hosts in the cluster to a unified server , record the login events of all hosts to the database uniformly, and make statistics and analysis of all user login events in the database. When a certain host reports a certain login information to the server, the server analyzes the login information and matches the rules , when it is determined that a brute force cracking behavior occurs based on the login information, an interception command for the corresponding login user is issued to the host, instructing the host to intercept the login of the corresponding user, and when the login user continues to attack other hosts, the server When receiving the login information of the login user reported by other hosts, there is no need to an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com