In-event safety auditing method based on user behavior analysis
A technology of behavior analysis and security audit, applied in the field of big data security, can solve problems such as lack of processing and notification to administrators, lack of finer-grained user behavior, lack of high-risk operation executor processing and alarms, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
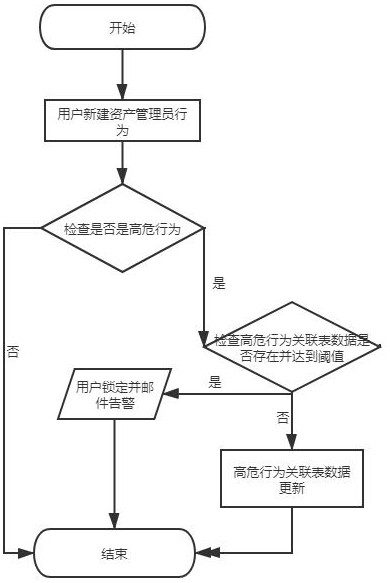
[0053] An in-process security audit method based on user behavior analysis, such as figure 1 As shown, the user operation behavior is detected. If the user operation is a high-risk behavior, the number of times the user triggers the high-risk behavior is judged. If the number of triggers is greater than or equal to the trigger threshold, the user account is locked and an email is sent for an alarm.
[0054] The present invention is real-time, and when the user performs each operation, if the behavior is in the high-risk behavior set, the user behavior is analyzed, and the user will be locked immediately when the automatic locking situation is reached, which is a risk control method in the event. The present invention assigns the definition of what is a risky user to the user for configuration, based on the configuration premise of the user, conducts risk assessment on real-time user behavior, and mainly proposes a high-risk behavior configuration definition and statistical rul...
Embodiment 2
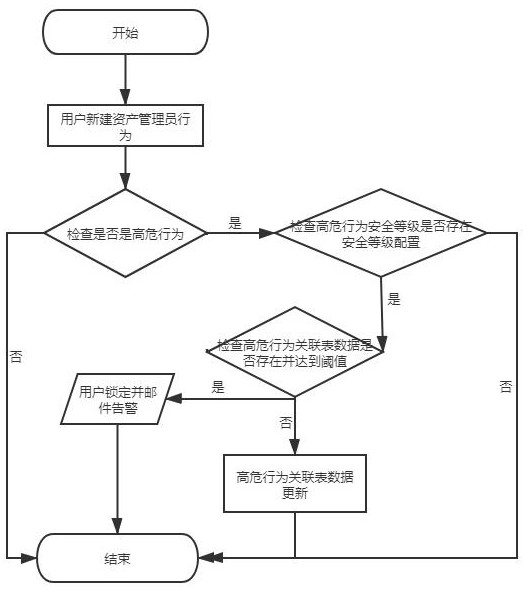
[0057] An in-process security audit method based on user behavior analysis, such as figure 2 As shown, when the user operation behavior is a high-risk behavior, the security level of the high-risk behavior of the operation is further detected, and the number of triggers of the security level is detected. If the number of triggers is greater than or equal to the number of trigger lockouts, the user is locked and an email is sent to warn .
[0058] The calculation of the number of trigger lockouts described in each high-risk level is as follows:
[0059] 1. The administrator configures the weight relationship of the trigger times of the high-risk security level;
[0060] 2. Obtain a linear relationship matrix diagram (no formula, just evolve the administrator configuration weight from the table to matrix A)
[0061]
[0062] 3. Calculate the maximum eigenvector, maximum eigenvalue and matrix consistency index of each high-risk behavior:
[0063] 1) Normalize each column o...
Embodiment 3
[0079] An in-process security audit method based on user behavior analysis. The administrator configures the security level weight relationship of high-risk behaviors including:
[0080] High-risk behavior A is medium-to-high-risk behavior, high-risk behavior B is medium-to-high-risk behavior, and the weight of trigger times is 1 / 2;
[0081] High-risk behavior A is medium-high risk behavior, high-risk behavior B is medium-low high-risk behavior, and the weight is 1 / 3;
[0082] High-risk behavior A is medium-high-risk behavior, high-risk behavior B is medium-low-high-risk behavior, and the weight is 1 / 5; the total threshold of trigger times for this configuration is 20.
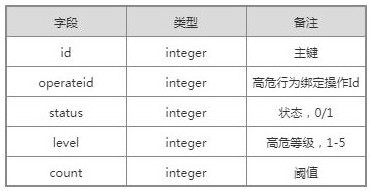
[0083] As shown in Table 1, the weight relationship table can be drawn according to the weight:
[0084] Table 1
[0085] mid Lo middle high school mid Lo 1 3 5 middle 1 / 3 1 2 high school 1 / 5 1 / 2 1
[0086] A linear relationship can be drawn from the table:
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com