Information security big-data resource management system based on trusted computing and cloud computing
A resource management system and data resource technology, applied in the field of information security big data resource management system, can solve problems such as poor scalability, inability to meet flexible, scalable and robust data resource search requirements, single point of failure, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
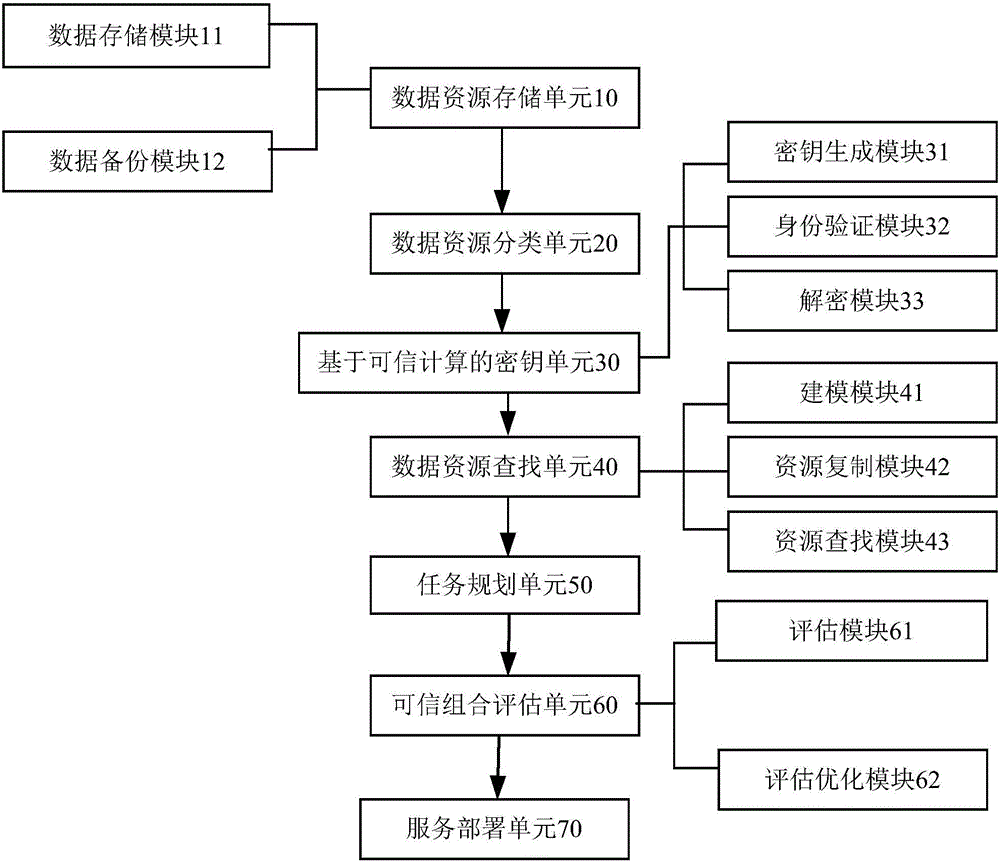
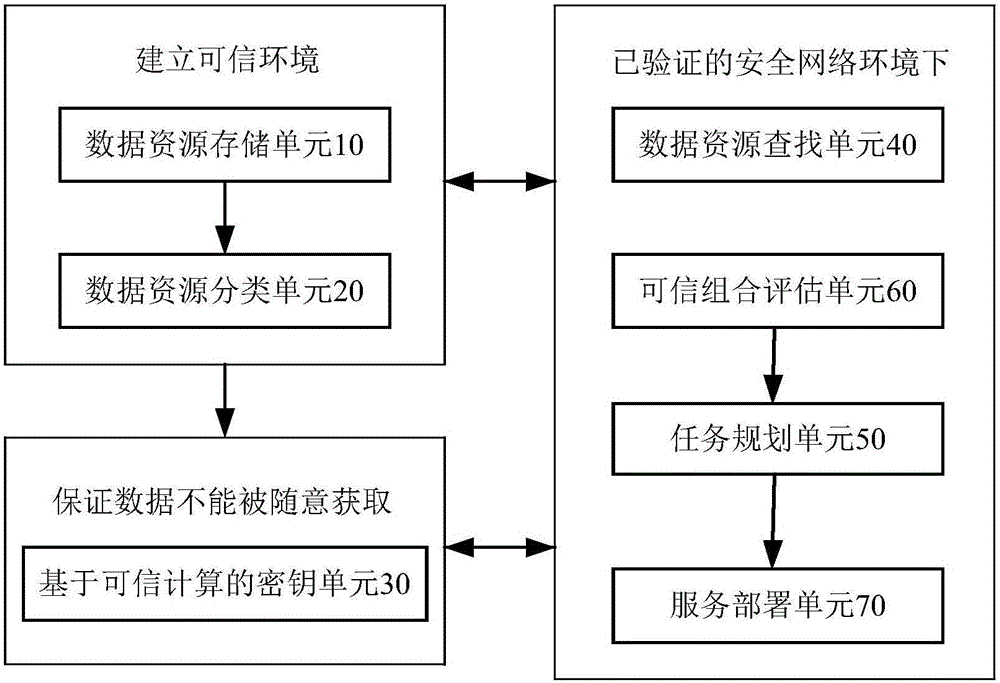
[0042] Embodiment 1: as figure 1 , figure 2 The shown information security big data resource management system based on trusted computing and cloud computing includes a data resource storage unit 10, a data resource classification unit 20, a key unit 30 based on trusted computing, a data resource search unit 40, and a task planning Unit 50, trusted combination evaluation unit 60 and trusted combination evaluation unit 70, specifically:
[0043] (1) Data resource storage unit 10: including a data storage module 11 and a data backup module 12, the data storage module 11 authenticates the hardware nodes in the network required for information storage, judges the credibility of the network hardware nodes, and establishes the stored The trust relationship of information, after the trust relationship is established, based on the data resources distributed in the cloud environment, the data resources are encapsulated and stored; the data backup module 12 is used to restore data in ...
Embodiment 2
[0072] Embodiment 2: as figure 1 , figure 2 The shown information security big data resource management system based on trusted computing and cloud computing includes a data resource storage unit 10, a data resource classification unit 20, a key unit 30 based on trusted computing, a data resource search unit 40, and a task planning Unit 50, trusted combination evaluation unit 60 and trusted combination evaluation unit 70, specifically:
[0073] (1) Data resource storage unit 10: including a data storage module 11 and a data backup module 12, the data storage module 11 authenticates the hardware nodes in the network required for information storage, judges the credibility of the network hardware nodes, and establishes the stored The trust relationship of information, after the trust relationship is established, based on the data resources distributed in the cloud environment, the data resources are encapsulated and stored; the data backup module 12 is used to restore data in ...
Embodiment 3
[0102] Embodiment 3: as figure 1 , figure 2 The shown information security big data resource management system based on trusted computing and cloud computing includes a data resource storage unit 10, a data resource classification unit 20, a key unit 30 based on trusted computing, a data resource search unit 40, and a task planning Unit 50, trusted combination evaluation unit 60 and trusted combination evaluation unit 70, specifically:
[0103] (1) Data resource storage unit 10: including a data storage module 11 and a data backup module 12, the data storage module 11 authenticates the hardware nodes in the network required for information storage, judges the credibility of the network hardware nodes, and establishes the stored The trust relationship of information, after the trust relationship is established, based on the data resources distributed in the cloud environment, the data resources are encapsulated and stored; the data backup module 12 is used to restore data in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com