Data processing method of E-commerce and government affairs system
An e-commerce and data processing technology, applied in data processing applications, transmission systems, commerce, etc., can solve problems such as large computational load, complex encryption algorithm, leaking and breaking of secrets, etc., to improve the speed of encryption and decryption and improve system security Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
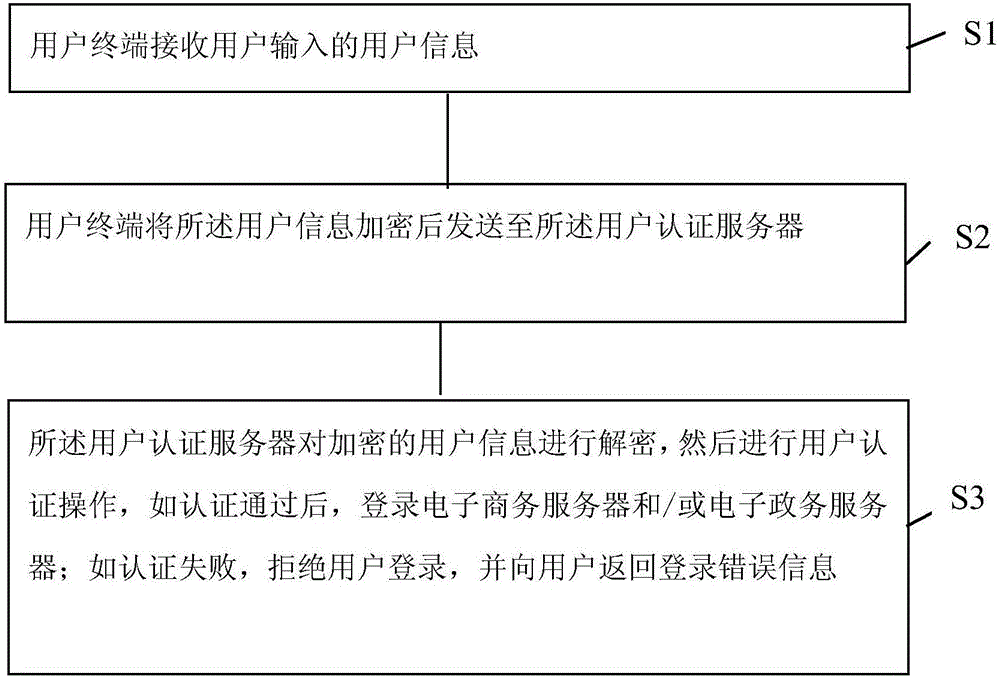
[0045] Attached below Figure 1-2 Be specific.
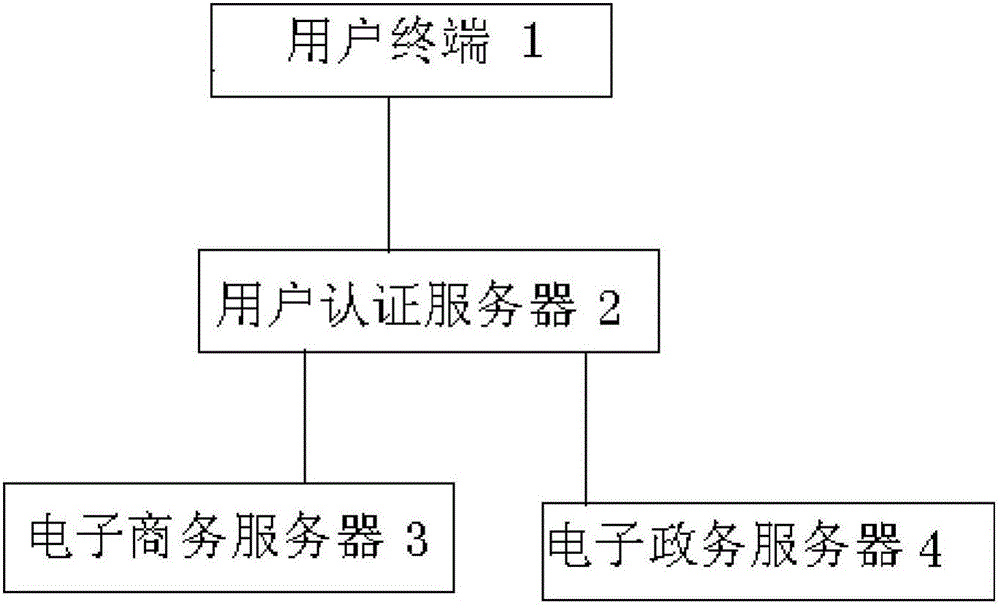
[0046] figure 1 It shows the e-commerce government affairs system of the present invention.
[0047] The e-commerce government system of the present invention includes a user terminal 1 , a user authentication server 2 , an e-commerce server 3 and an e-government server 4 .
[0048] E-commerce is a commercial activity centered on commodity exchange by means of information network technology; it can also be understood as electronic transactions on the Internet (Internet), intranet (Intranet) and value-added network (VAN, Value Added Network). The activities of conducting trading activities and related services are the electronization, networking, and informatization of all aspects of traditional business activities.
[0049] E-commerce usually refers to a wide range of commercial and trade activities around the world, under the open network environment of the Internet, based on the browser / server application mode, buyers and s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com