Information secure spreading method and device
A technology for information security and encrypted information, applied in the field of information security dissemination methods and devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
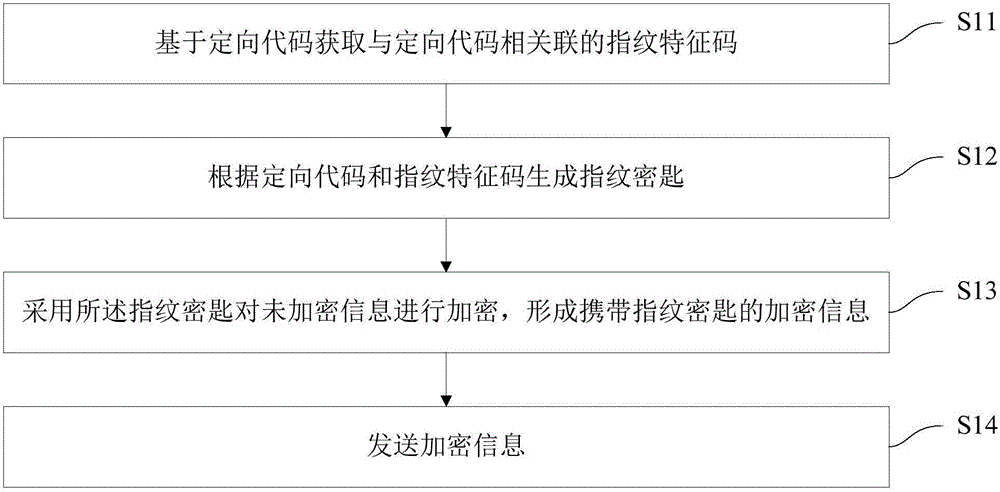
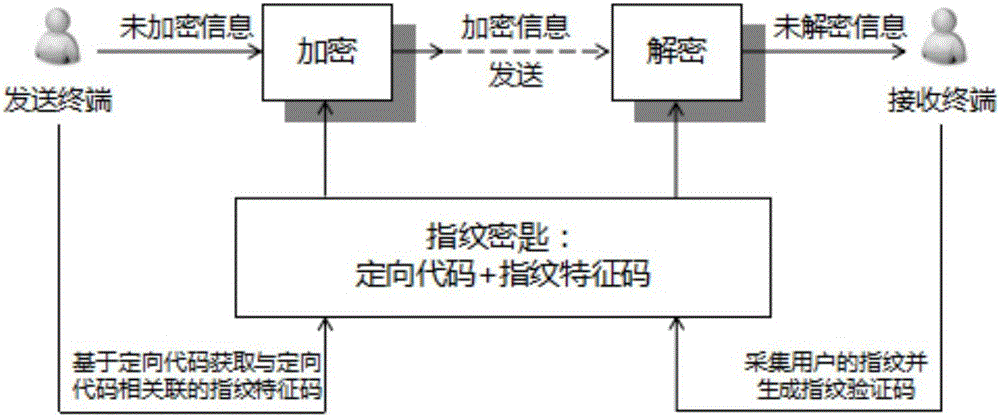
[0063] figure 1A flow chart of the information security dissemination method in this embodiment is shown. The method for safe dissemination of information is executed on a sending terminal that sends information, and is used to implement encryption protection during the information sending process, so as to avoid leakage of information content during the information dissemination or sharing process. In this embodiment, the sending terminal may be a terminal capable of information dissemination and sharing, such as a smart phone, a tablet computer, a notebook, and a PC. Such as figure 1 As shown, the information security dissemination method includes the following steps:
[0064] S11: Obtain a fingerprint feature code associated with the orientation code based on the orientation code. Wherein, the directional code may be a code that can be assigned to a specific user, such as a user ID or an email address of the specific user, so as to send information to the specific user. ...
Embodiment 2
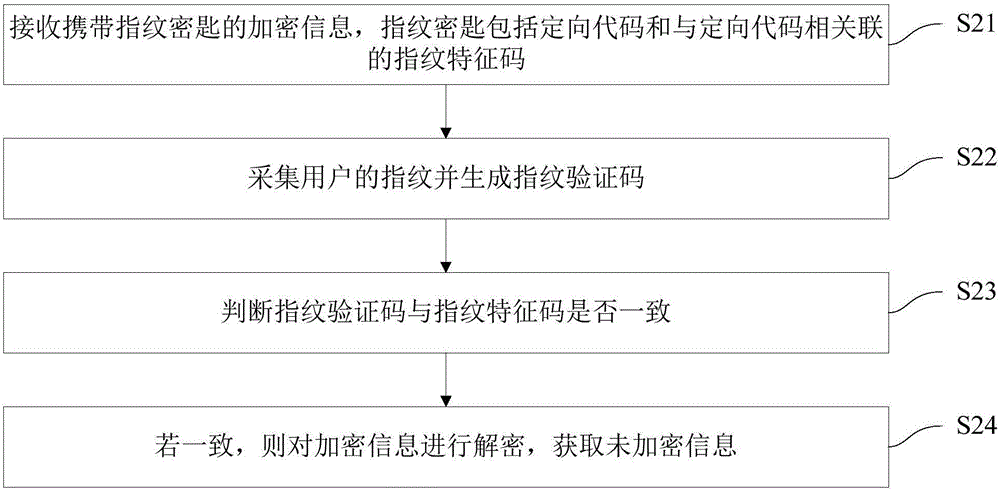
[0071] figure 2 A flow chart of the information security dissemination method in this embodiment is shown. The method for safe dissemination of information is executed on a receiving terminal that receives information, and is used to implement encryption protection during the process of receiving information, so as to avoid leakage of information content during the process of disseminating or sharing information. In this embodiment, the receiving terminal may be a terminal capable of information dissemination and sharing, such as a smart phone, a tablet computer, a notebook, and a PC. Such as figure 2 As shown, the information security dissemination method includes the following steps:
[0072] S21: Receive encrypted information carrying a fingerprint key, where the fingerprint key includes an orientation code and a fingerprint feature code associated with the orientation code. It can be understood that the transmission process of the encrypted information can take place ...
Embodiment 3
[0080] Figure 4 A flow chart of the information security dissemination method in this embodiment is shown. The method for safe dissemination of information is executed on a sending terminal that sends information, and is used to implement encryption protection during the information sending process, so as to avoid leakage of information content during the information dissemination or sharing process. In this embodiment, the sending terminal may be a terminal capable of information dissemination and sharing, such as a smart phone, a tablet computer, a notebook, and a PC. Such as Figure 4 As shown, the information security dissemination method includes the following steps:
[0081] S31: Receive the request information and acquire the device identification code; the request information includes the device identification code of the specific device sending the request information. Specifically, request information from specific devices (such as smartphones, tablet computers, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com