Lock management method, access control terminal, server and system
A management method and management system technology, applied in the direction of instruments, time registers, single input port/output port registers, etc., can solve problems such as poor anti-theft effect, difficult evidence collection, insufficient records, etc., to ensure personal and property safety , safe, intelligent, convenient, and practical
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0058] Embodiment 1. A lock management method. Combine below Figure 1 to Figure 3 The method provided in this embodiment will be described in detail.
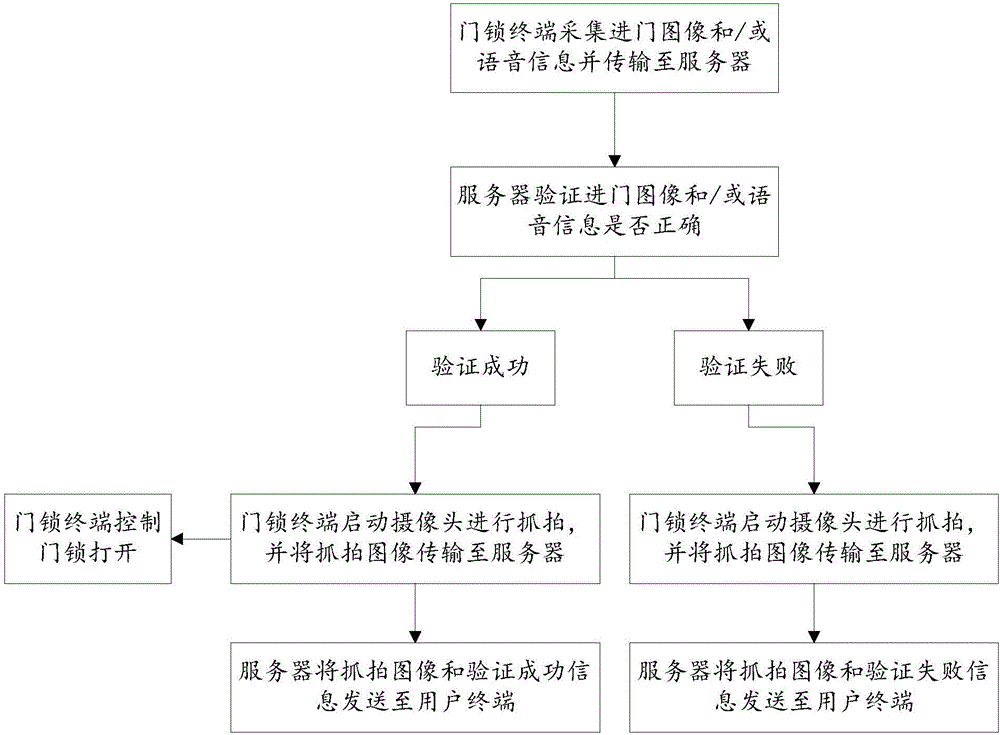
[0059] see figure 1 and figure 2 , a lock management method applied to a door lock terminal, comprising the following steps:
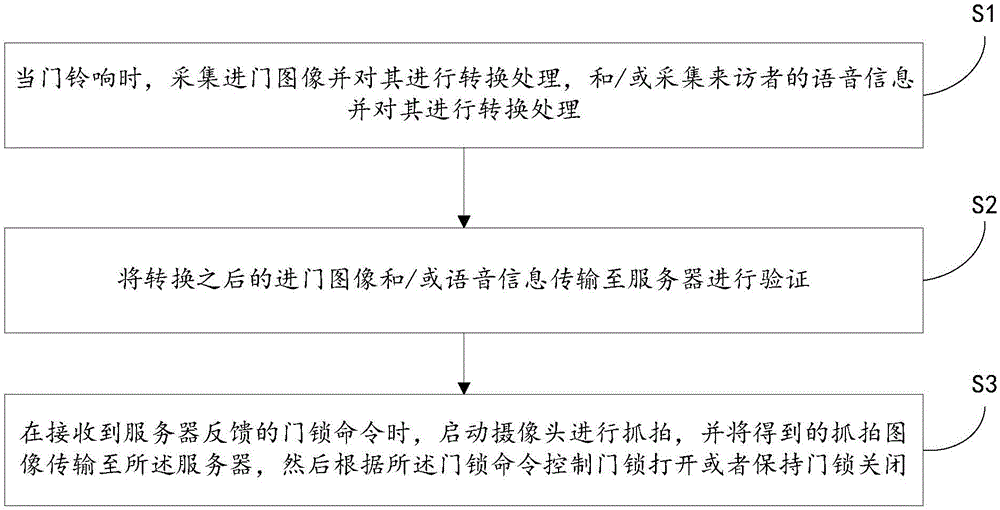
[0060] S1. When the doorbell rings, collect the entry image and convert it, and / or collect the visitor's voice information and convert it.
[0061] Specifically, when the doorbell rings, the image of entering the door is collected and subjected to light compensation, and then converted into a grayscale image, and / or the voice information of the visitor is collected and converted into a voice string. It can only collect the entrance image or only the visitor's voice information or both, which are set by the user.
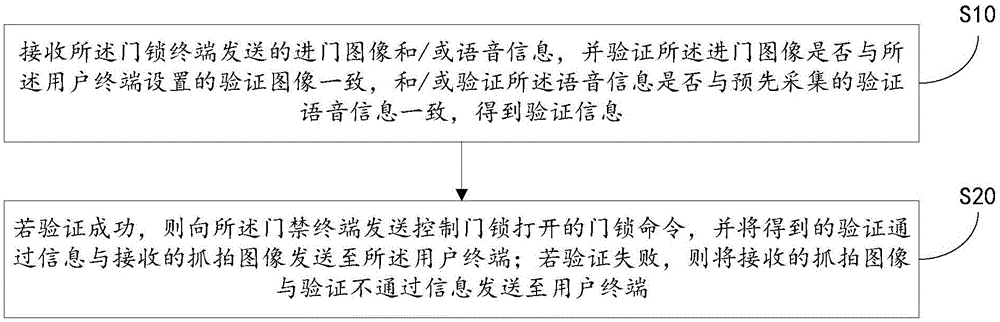
[0062] S2. Transmitting the converted door entry image and / or voice information to the server for verification.
[0063] Specifically, the converted door-entry image and / or voice infor...
Embodiment 2
[0080] Embodiment 2, a lock management system. Combine below Figure 4 The system provided in this embodiment will be described in detail.
[0081] see Figure 4 , a lock management system, the system includes a door lock terminal, a server and a user terminal. The door lock terminal specifically includes a collection unit, a processor, a first communication unit, a snapshot unit, a door lock control unit, a door lock sensing unit, an external force monitoring unit, a deformation monitoring unit, a local alarm unit and a storage unit.
[0082] The collecting unit is used for collecting the image of entering the door and / or collecting the voice information of the visitor when the doorbell rings.
[0083] Specifically, when the doorbell rings, the collection unit collects the image of entering the door and / or collects the voice information of the visitor. It can only collect the entrance image or only the visitor's voice information or both, and the door can be opened by col...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com