A security network attachment device and method for blockchain
An additional device and security network technology, applied in the field of blockchain information security protection devices, to achieve the effect of avoiding access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
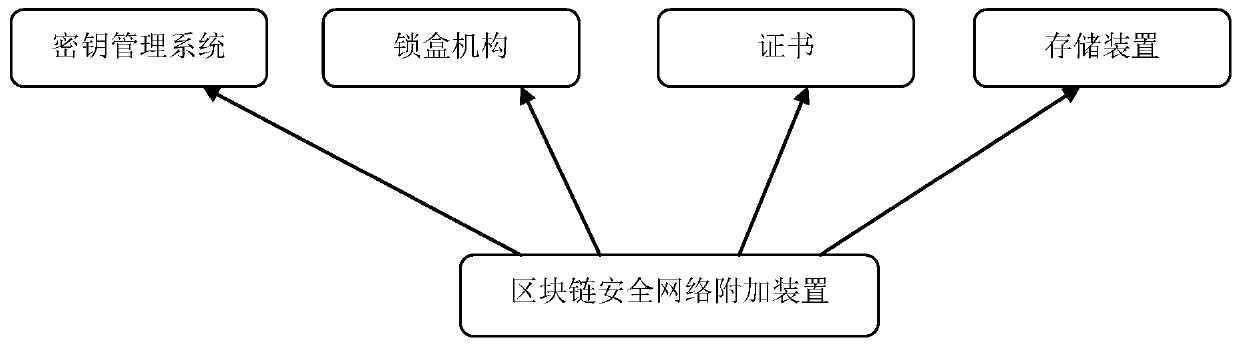
[0018] Example: see figure 1 , an additional device and method for a blockchain security network, by encrypting data and only decrypting it on the client side to prevent any unauthorized user from accessing the data, it can avoid threats caused by system administrator access and physical capture of the disk potential threat. The client's decryption depends on the decryption key provided by the key management system. Wherein the confidentiality of the attachment relies on a lock box mechanism which stores the key. Each file is encrypted with a symmetric key. Inside the metadata of the file is a pointer to the key body. Inside the metadata of the key body are the ID of the file, the ID of the user who created the file, and the ID of the last modified file. User's signature. This signature can prove to other users that the key body itself has not been altered (of course any authorized user can verify this signature). The key body here is composed of some tuples consistent wit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com