Data encryption method based on NFC chip security authentication
A data encryption and data technology, applied in the usage of multiple keys/algorithms, transmission systems, electrical components, etc., can solve the problems of ciphertext data restoration, inability to decipher ciphertext data, etc., to achieve the effect of ensuring absolute security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The present invention will be further described below in conjunction with specific embodiments, and the advantages and characteristics of the present invention will become clearer along with the description. However, these embodiments are only exemplary and do not constitute any limitation to the scope of the present invention. Those skilled in the art should understand that the details and forms of the technical solutions of the present invention can be modified or replaced without departing from the spirit and scope of the present invention, but these modifications and replacements all fall within the protection scope of the present invention.
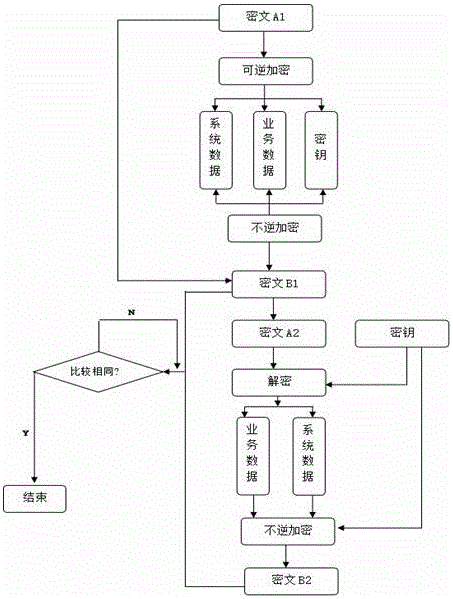
[0026] The invention relates to a data encryption method based on NFC chip anti-counterfeiting authentication, comprising the following steps:
[0027] Step 1: The user enters the correct user name and password through the mobile terminal to verify the login;
[0028] Step 2: After verifying that the user has successfully log...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com