Network anomaly flow detection and defense system based on SDN (software defined networking)
A software-defined network and network exception technology, applied in transmission systems, electrical components, etc., can solve problems such as no controller provided, and achieve the effect of good usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
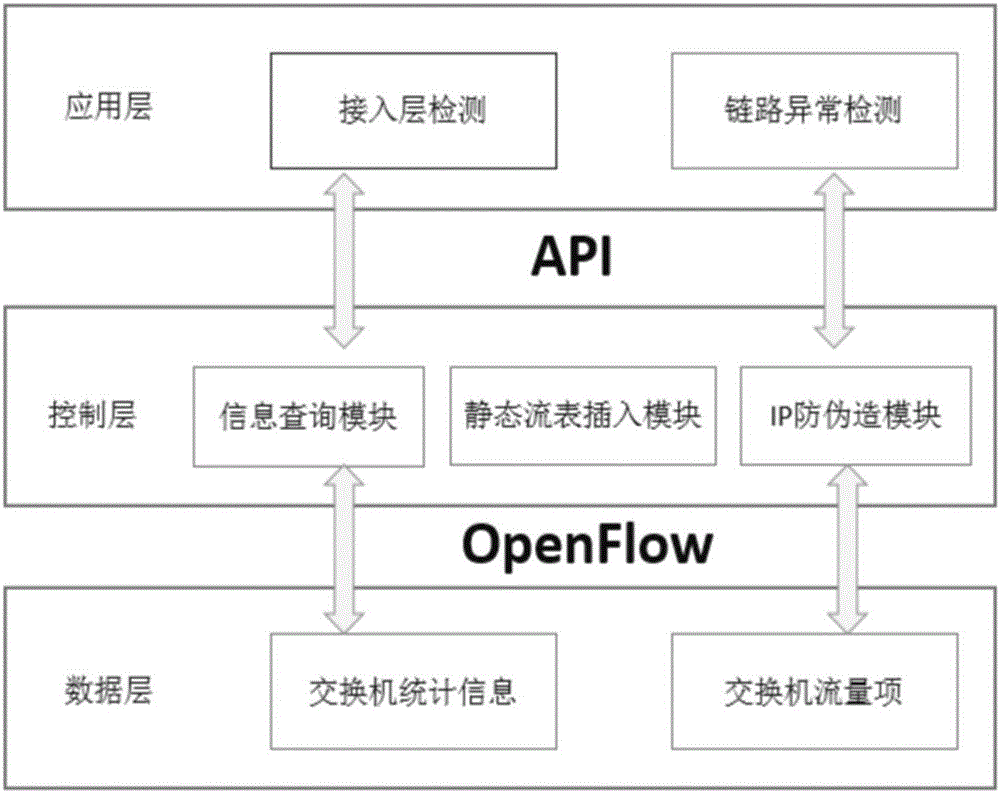
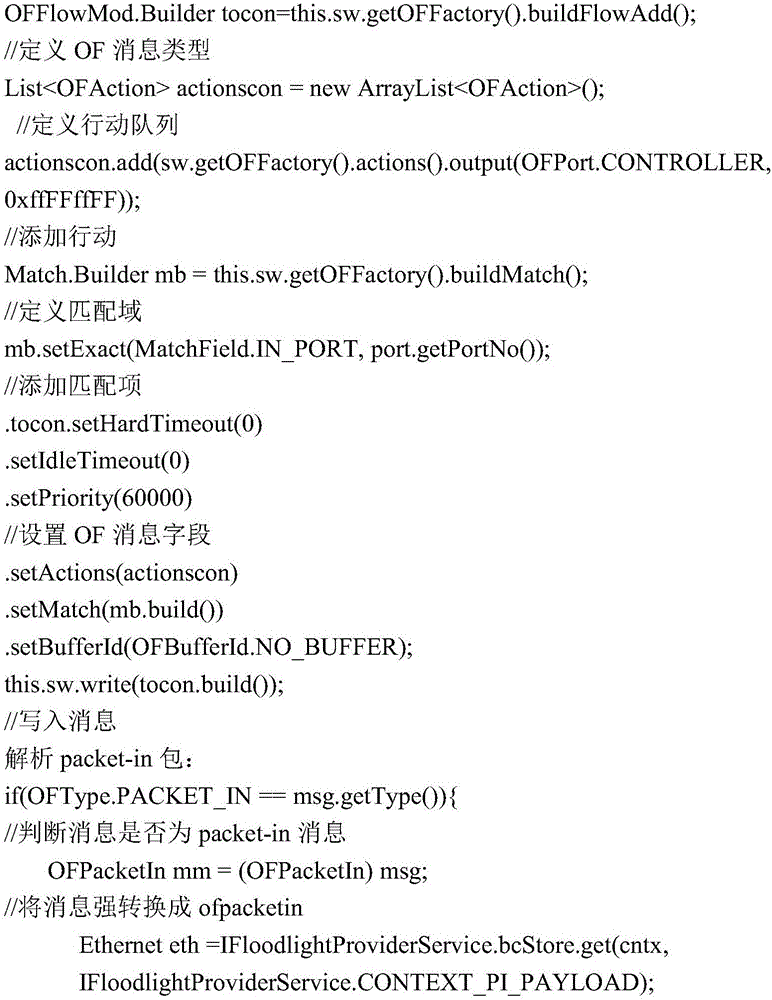
[0029] Start the controller, and the IP anti-counterfeiting module will start to work at this time, and perform IP binding for users who access the network with static IP configuration through the DHCP service. Turn on the access layer detection and link anomaly detection modules, and the two modules will start traffic learning. Calculate normal flow criteria and flow change thresholds. The algorithm will collect data to calculate the change of traffic every once in a while, and compare the change value with the abnormal judgment standard of the corresponding algorithm. The result is displayed, which is convenient for the administrator to find and partially block the attack traffic.
[0030] 1 Block source forgery of IP address
[0031] 1 design thinking
[0032] In the DDoS attack, the attack source address validity is divided into real source address and forged source address. The forged source IP address will occupy unnecessary connection bandwidth of the server and cons...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com