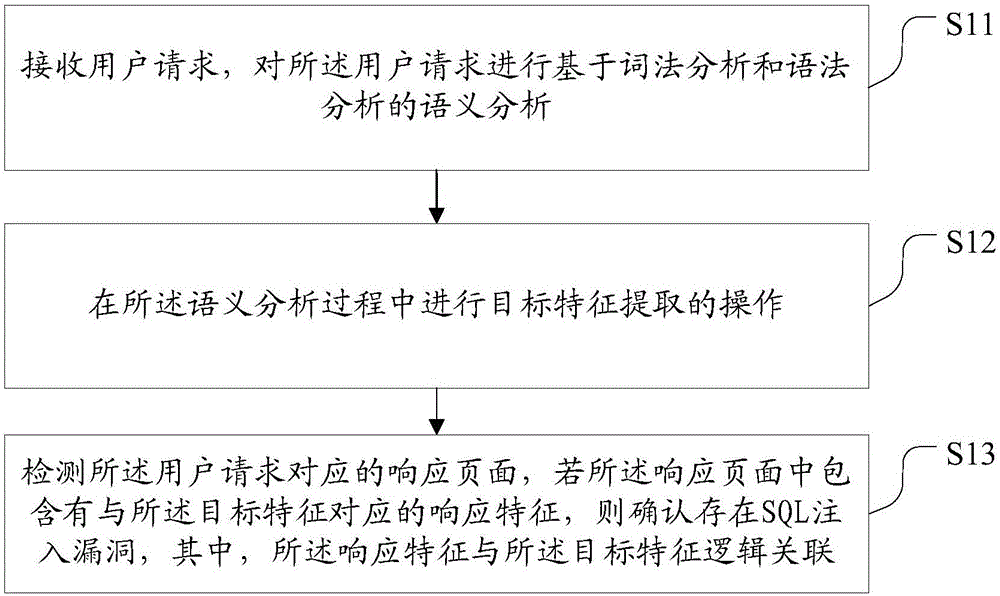
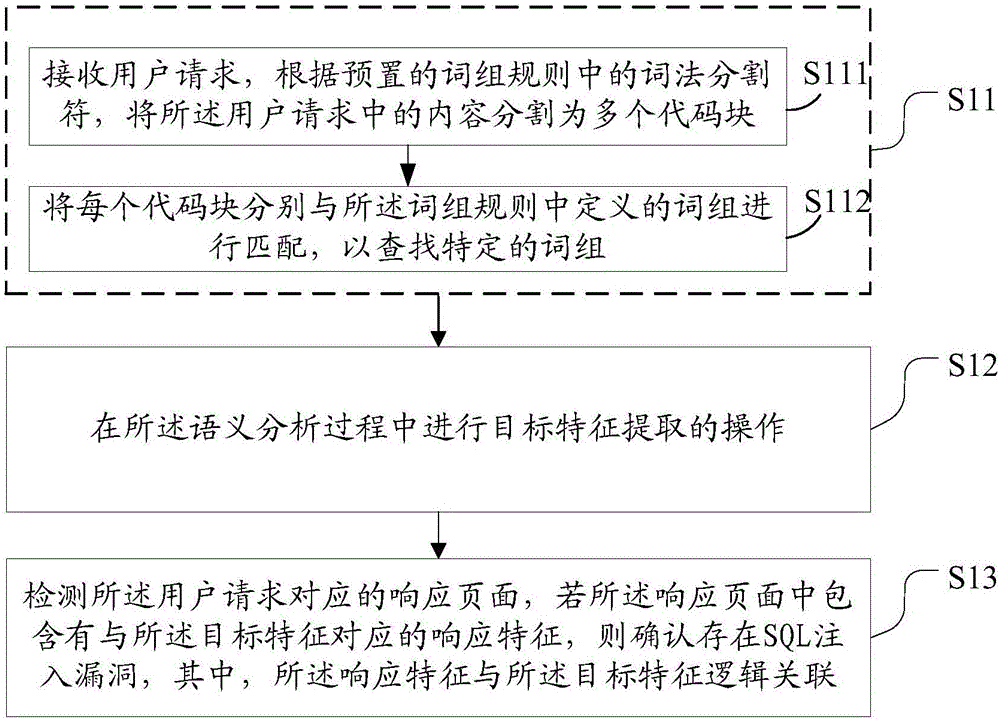
Detection method and device of SQL (Structured Query Language) injection vulnerabilities
A detection method and vulnerability technology, applied in the field of information security, can solve problems such as lack of flexibility, inability to accurately detect 0day vulnerabilities, easy to miss unknown vulnerabilities, etc., and achieve the effect of improving network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0084] User request:
[0085] / sqli / ? id=qwdwqd'UNION ALL SELECT NULL,CONCAT(0x7178767a71,0x55506c6c486474696776746d4f4573737877764e504e595a6343645866494b625263656171594576,0x717171717876#&Submit=Submit)
[0086] Corresponding response features:
[0087] qxvzqUPllHdtigvtmOEssxwvNPNYZcCdXfIKbRceaqYEvqqqxq.
[0088] 具体的,语义分析过程中提取的用户请求中的目标特征,通过对目标特征即CONCAT函数CONCAT(0x7178767a71,0x55506c6c486474696776746d4f4573737877764e504e595a6343645866494b625263656171594576,0x7171717871)进行计算,得到计算结果为qxvzqUPllHdtigvtmOEssxwvNPNYZcCdXfIKbRceaqYEvqqqxq,然后检测该用户请求对应的响应页面, If the response page contains a response feature corresponding to the target feature, that is, qxvzqUPllHdtigvtmOEssxwvNPNYZcCdXfIKbRceaqYEvqqqxq, it is confirmed that there is a SQL injection vulnerability.
example 2
[0090] User request:
[0091] / ? question / search / %27%75nion%20select%201,2,3,4,5,6,7,8,md5(1122),10,11,12,13,14,15,16,17,18, 19,20%23
[0092] Corresponding response features:
[0093] 3b712de48137572f3849aabd5666a4e3
[0094] Specifically, the target feature in the user request extracted in the semantic analysis process is calculated by calculating the target feature, that is, the md5 function md5(1122), and the calculation result is 3b712de48137572f3849aabd5666a4e3, and then the response page corresponding to the user request is detected. If the page contains the response feature corresponding to the target feature, that is, 3b712de48137572f3849aabd5666a4e3, it is confirmed that there is a SQL injection vulnerability.
example 3
[0096] User request:
[0097] / information / oa_infordislist.asp? class=1UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,char(119)%2bchar(101)%2bchar(98)%2bchar(115)%2bchar(99)%2bchar(97)%2bchar( 110)%2bchar(58)%2bchar(105)%2bc har(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100),NULL,NULL,NULL,NULL,NULL, NULL,NULL,NULL,NULL,NULL,NULL—
[0098] Corresponding response features:
[0099] 'webscan:i;find'
[0100] Specifically, the target features in the user request extracted during the semantic analysis process are analyzed by comparing the target features, that is, multiple char functions char(119)% 2bchar(101)% 2bchar(98)% 2bchar(115)% 2bchar(99)% 2bchar(97)%2bchar(110)%2bchar(58)%2bchar(105)%2bchar(59)%2bchar(102)%2bchar(105)%2bchar(110)%2bchar(100) The calculation result is performed Character splicing, the calculation result obtained is 'webscan:i; find', and then the response page corresponding to the user request is detected, if the response page contains the respon...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com