Method and system for realizing filtering of malicious calls through real-time algorithm
A technology of malicious calls and algorithms, applied in the direction of telephone communications, transmission systems, electrical components, etc., can solve the problems of operators and mobile users lack of governance means, and achieve the effects of reducing pressure, accurate interception, and high efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0066] The technical solutions of the present invention will be further described and illustrated through specific examples below.
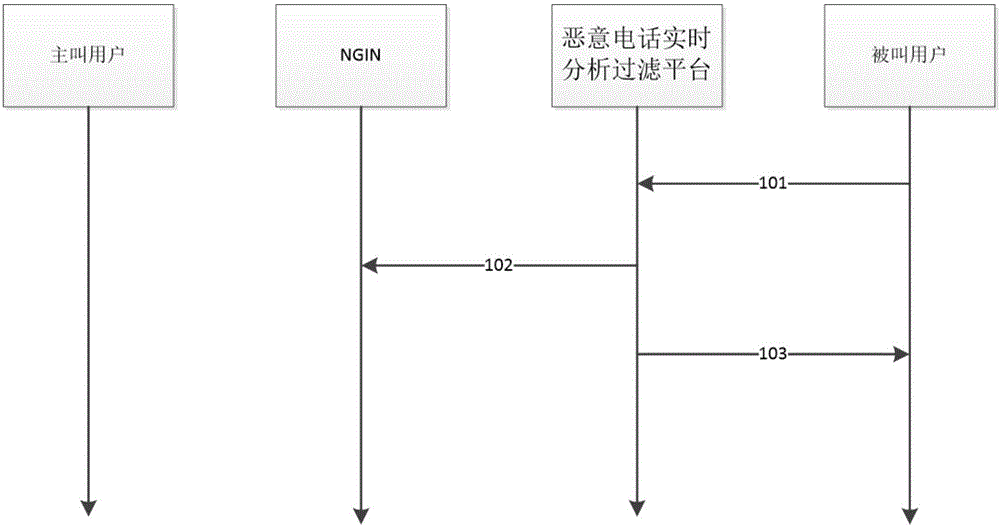
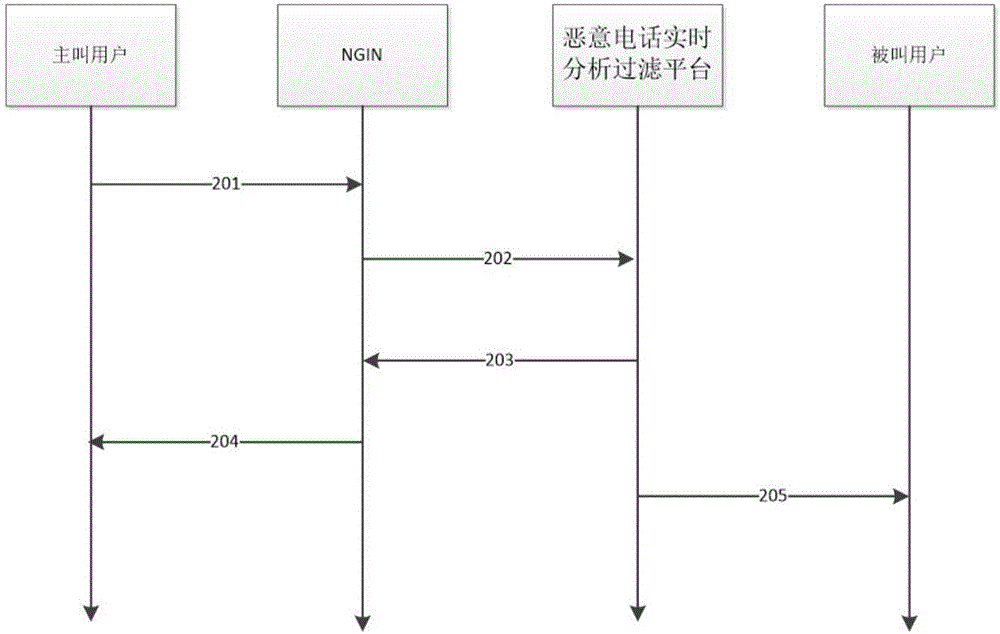
[0067] This software has the following characteristics: (1) 24-hour uninterrupted operation; (2) automatic redialing in case of busyness, and the number of redialing times can be set arbitrarily; (3) system working time can be set arbitrarily. Criminals take advantage of the above-mentioned features of the HUDEI software to maliciously harass mobile phone users, which brings great troubles to users. In view of the above situation, the present invention develops a method and system for filtering malicious calls by using real-time algorithms.
[0068] The method and system for realizing malicious call filtering by using a real-time algorithm require users to apply for services protected by you on the malicious call real-time analysis and filtering platform. The scope of acceptance of this business includes all China Telecom, China Unicom and mobil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com