Sample classification determination method for malware detection
A judgment method and sample technology, applied in the field of information security, can solve problems such as low detection efficiency and difficulty in finding similar samples, and achieve the effects of improving efficiency and accuracy, avoiding operations, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
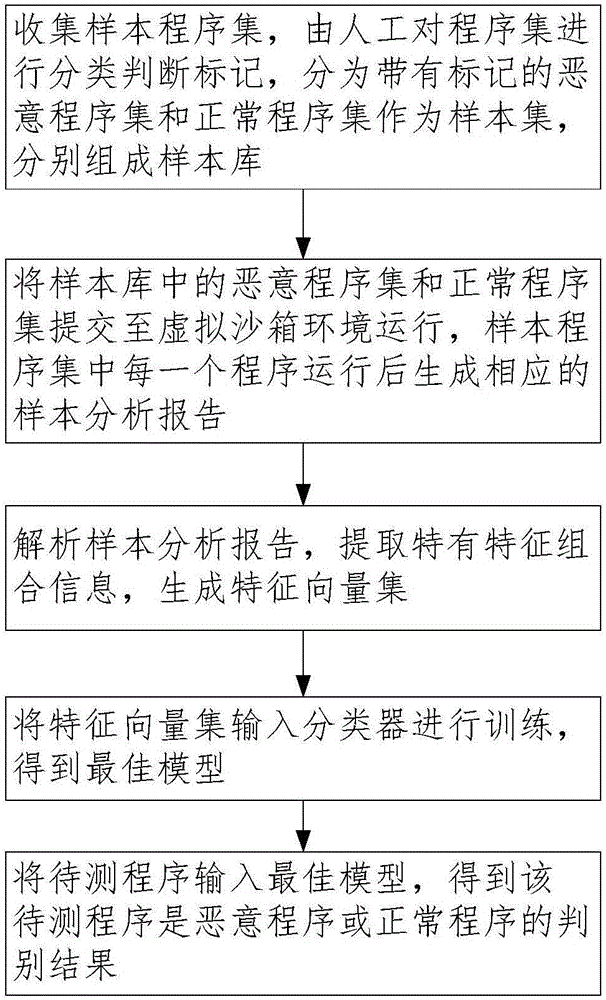
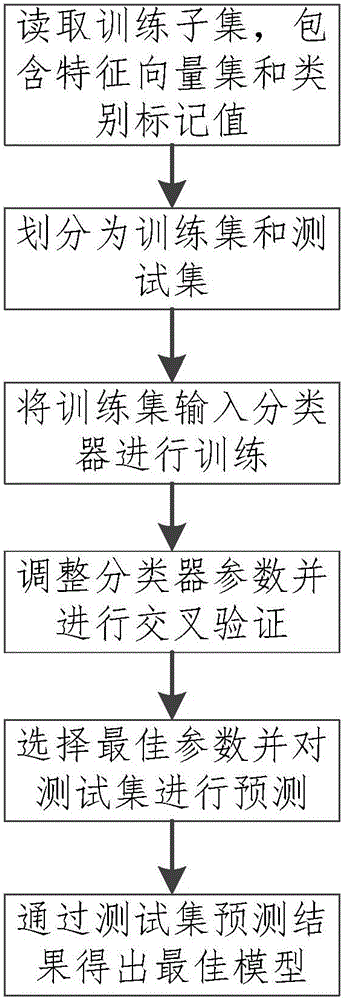
[0043] A sample category judgment method for malware detection, through training and learning of the labeled sample set, an optimal model is obtained to judge whether the program to be tested is a malicious program, the specific process is as follows figure 1 shown, including the following steps:
[0044] Step 1 collects sample programs, manually classifies, judges and marks the programs, divides them into malicious programs and normal programs, and forms sample libraries respectively.
[0045] Combining the scanning results of various existing program detection tools and the judgment of manual analysis results for programs, as the classification standard for malicious program sets and normal program sets, manually mark the program sets.
[0046] Step 2 Submit the malicious program set and normal program set in the sample library to the virtual sandbox environment for operation, and generate a corresponding sample analysis report after each sample program in the sample program...
Embodiment 2
[0068] A sample category judgment method for malware detection, the number of collected marked malicious programs is far greater than the number of normal programs, the specific steps are as follows:
[0069] Step 1 collects marked malicious program sets and normal program sets as sample sets to form sample libraries respectively.
[0070] Step 2 Submit the malicious program set and the normal program set in the sample library to the virtual sandbox environment for operation, and generate a corresponding sample analysis report after each program in the program set runs.
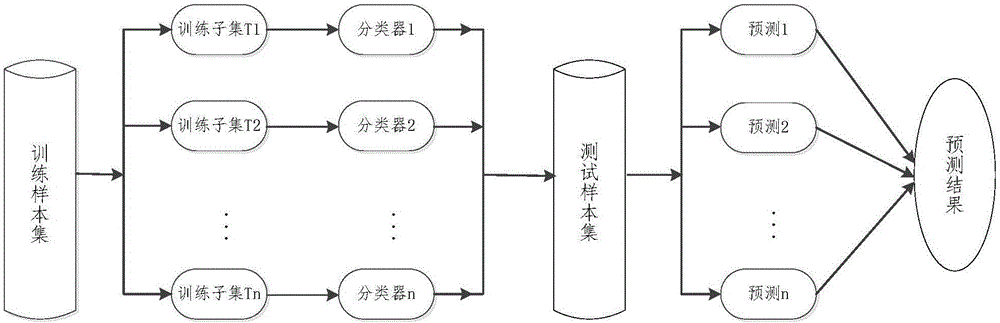
[0071] Step 3 Analyze the sample analysis report, extract the unique feature combination information, and generate a feature vector set; split the malicious program feature vector set so that the number of malicious programs in each pile after splitting is approximately 1:1 with the number of normal programs, forming multiple training samples set.
[0072] like Figure 4 As shown, the training sample set is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com