Transformer station network intrusion detection and analysis method based on character fingerprint
A substation network and feature fingerprint technology, applied in the field of network information security, can solve problems such as single detection and analysis, low efficiency, and false negatives
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The specific embodiments of the method for detecting and analyzing network intrusion in substations based on characteristic fingerprints involved in the present invention will be described in detail below with reference to the accompanying drawings.
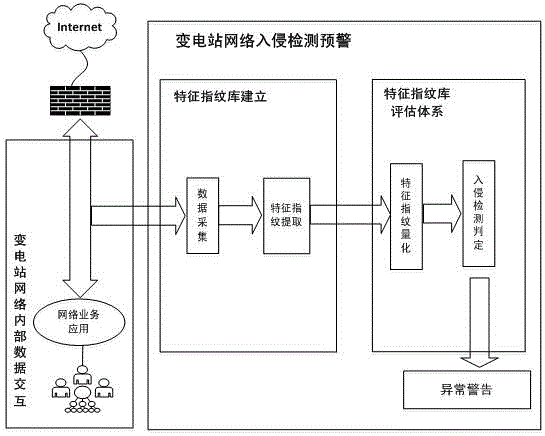
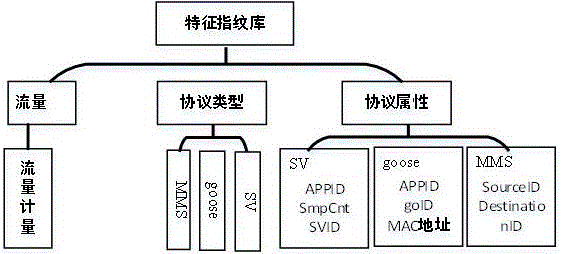
[0038] like figure 1 As shown, this embodiment establishes a flow chart of network intrusion detection based on feature fingerprint database. The network intrusion detection process is to obtain network intrusion information from the substation communication network through data collection, then extract characteristic fingerprints from the network intrusion information, establish a hierarchical characteristic fingerprint database, quantify the collected characteristic fingerprints, and then intrusion on the collected characteristic fingerprints. If it is abnormal, an abnormal alarm will be issued.
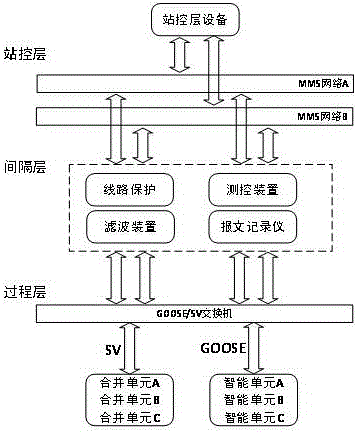
[0039] like figure 2 As shown, this embodiment establishes a frame diagram of a typical substation. The process layer inc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com