Software defined network-oriented DDoS attack defense system and method
A software- and network-oriented technology, applied in transmission systems, electrical components, etc., can solve problems such as safety issues that cannot be ignored
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0078] In order to make the technical problems and technical solutions to be solved by the present invention clearer, the following will describe in detail the embodiments of defending against DDoS attacks of portal websites with reference to the accompanying drawings.
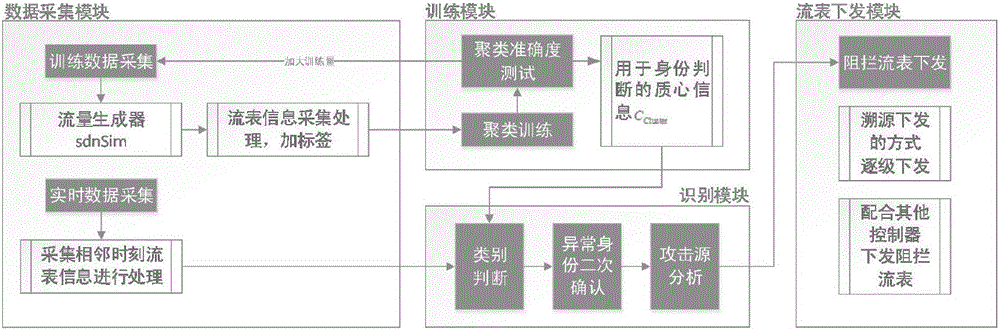
[0079] A software-defined network-oriented DDoS attack defense system realizes the identification and interception of DDoS attack traffic in the SDN network architecture environment. The invention is divided into three parts: an SDN network data collection part, a DDoS attack identification part and a DDoS attack interception part. The former part provides the decision-making basis for the latter part. The data collection part uses the OpenFlow flow table data of the switches in the SDN network, and the controller extracts and analyzes the data in real time to identify abnormal DDoS attack traffic; the attack interception part is based on Based on the judgment result in the previous part, a blocking flow table...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com