Access method and system of unmanned aerial vehicle air traffic control system
An access method and air traffic control technology, applied in the field of control of unmanned aircraft, can solve problems such as unfavorable air traffic management, irregular use of airspace, and unlawful flight tasks, so as to improve soundness and safety, The effect of preventing accidents and eliminating management loopholes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042]The present invention will be further described in detail below with reference to the accompanying drawings and specific embodiments.
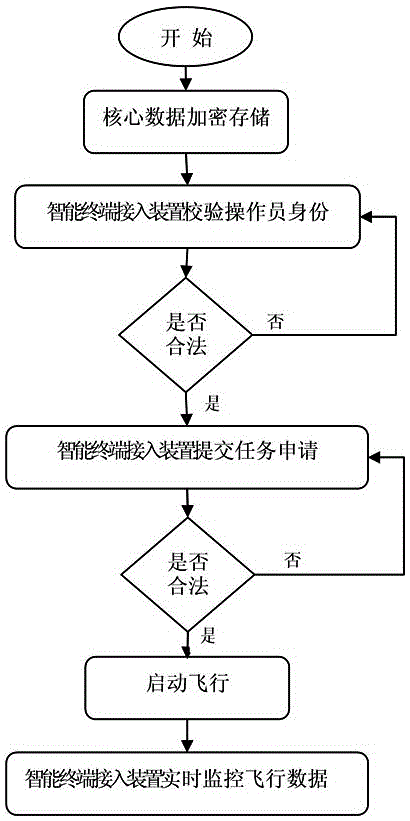
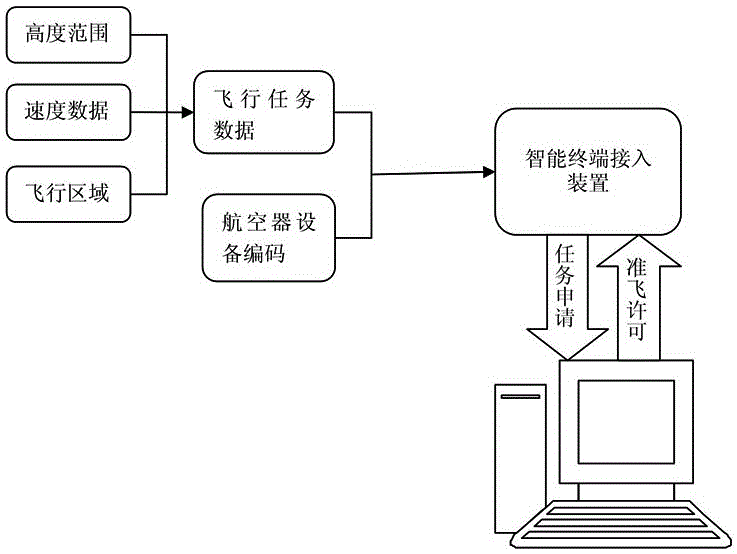
[0043] As shown in Figure 1, a method for accessing an unmanned aerial vehicle air traffic control system of the present invention includes the following steps:
[0044] S1: Encrypted storage of core data, ready for later verification.
[0045] The above-mentioned core data can be set according to actual needs, for example, it can include no-fly data, operator identity information, and equipment verification data.
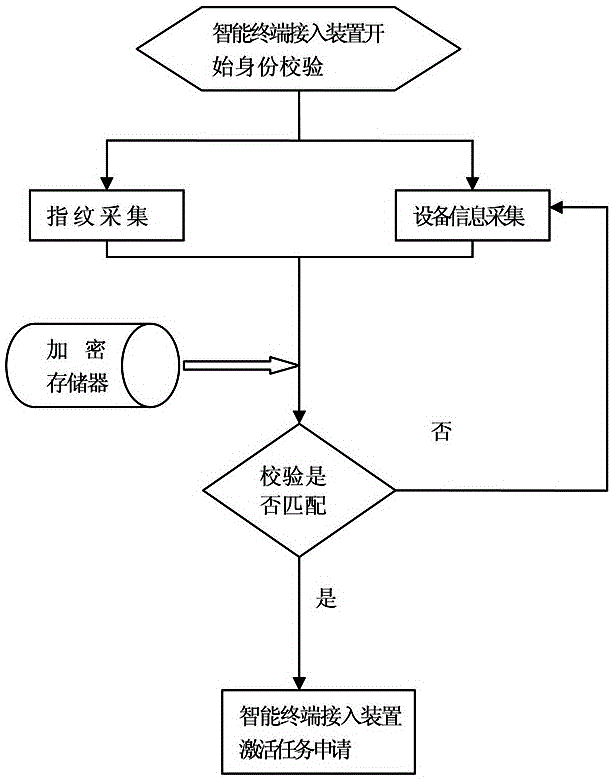
[0046] No-fly data includes information about sensitive airspace that users cannot read.
[0047] The operator's identity verification can be fingerprint verification, face recognition, or other existing identity recognition methods. In this example, the operator identity information is verified by fingerprint, and the encrypted storage core data stores fingerprint information.
[0048] In this example, the device verifica...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com