Method for secret communication of chaotic neural network under signal quantization circumstance
A neural network, secure communication technology, applied in secure communication through chaotic signals, secure communication devices, digital transmission systems, etc., can solve problems such as inability to handle signal quantization
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0088] Embodiment 1: The above-mentioned method of the present invention is used to simulate the ciphertext signal, and the ciphertext signal is the sound signal when the window7 system is shut down.
[0089] The parameters used are:
[0090]
[0091]
[0092]
[0093] Sampling period T=0.02s;
[0094] Quantization precision Δ=0.02;
[0095] Drive system initial value x 0 =[0.1,0.2,-0.1] T ;
[0096] Response system initial value y 0 =[1,2,3] T ;
[0097] constant matrix
[0098] Solve the controller gain matrix by formula (6)
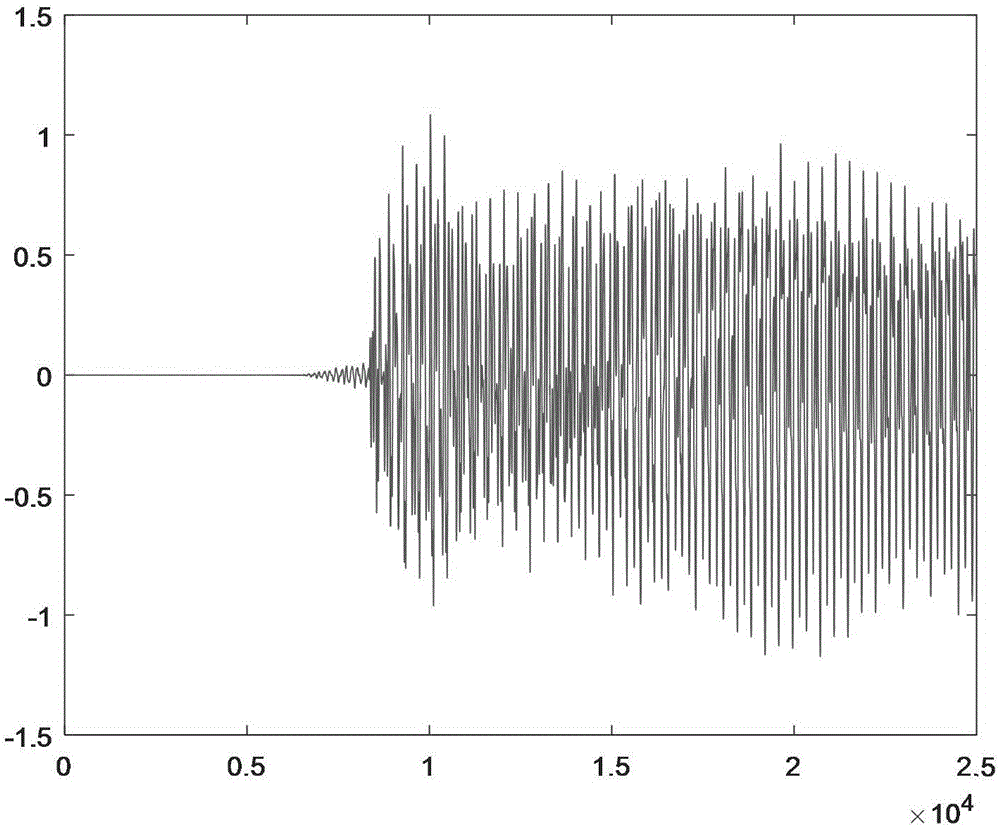
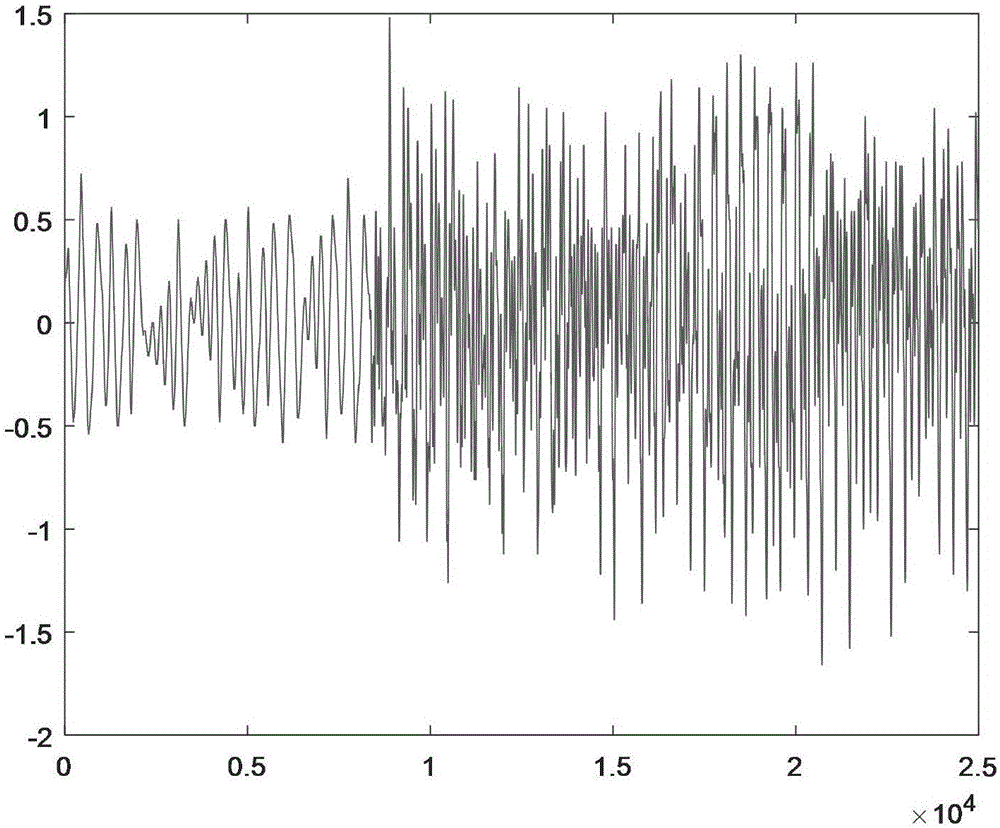
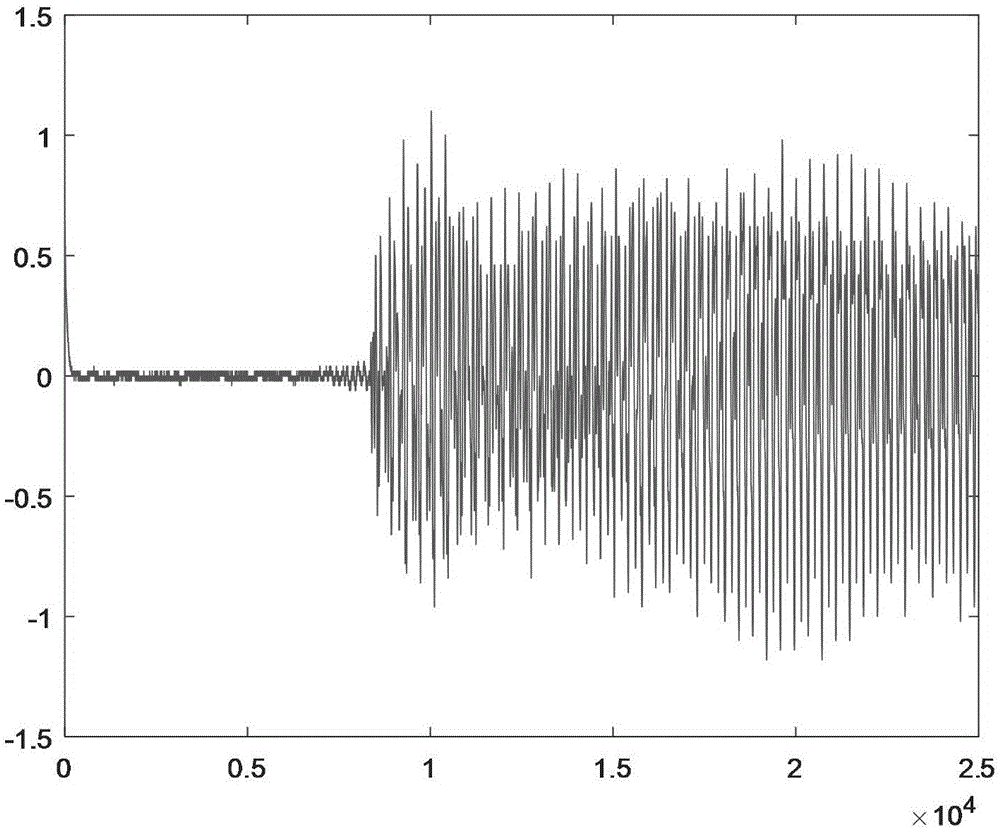
[0099] For the time-domain diagram of the original ciphertext signal at the sender, see Figure 5 , for the time-domain diagram of the encrypted signal in the network transmission channel see Image 6 , the time-domain diagram of the ciphertext signal recovered by the receiving end is shown in Figure 7 , the original ciphertext signal s(k) and the restored ciphertext signal Make a difference to get a secure communication erro...
Embodiment 2
[0101] Embodiment 2: The above-mentioned method of the present invention is used to simulate the ciphertext signal, and the ciphertext signal is the sound signal of the song "You and Me" by Liu Huan.
[0102] The parameters used are:
[0103]
[0104]
[0105]
[0106] Sampling period T=0.02s;
[0107] Quantization precision Δ=0.02;
[0108] Drive system initial value x 0 =[0.1,0.2,-0.1] T ;
[0109] Response system initial value y 0 =[2,1.5,2] T ;
[0110] constant matrix
[0111] Solve the controller gain matrix by formula (6)
[0112] For the time-domain diagram of the original ciphertext signal at the sender, see Figure 9 , for the time-domain diagram of the encrypted signal in the network transmission channel see Figure 10 , the time-domain diagram of the ciphertext signal recovered by the receiving end is shown in Figure 11 , the original ciphertext signal s(k) and the restored ciphertext signal Make a difference to get a secure communication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com