Information verification method
A technology for information verification and registration information, which is applied in the field of information verification and can solve problems such as inconvenience and high cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0069] The present invention will be further described below in conjunction with the embodiments shown in the accompanying drawings.
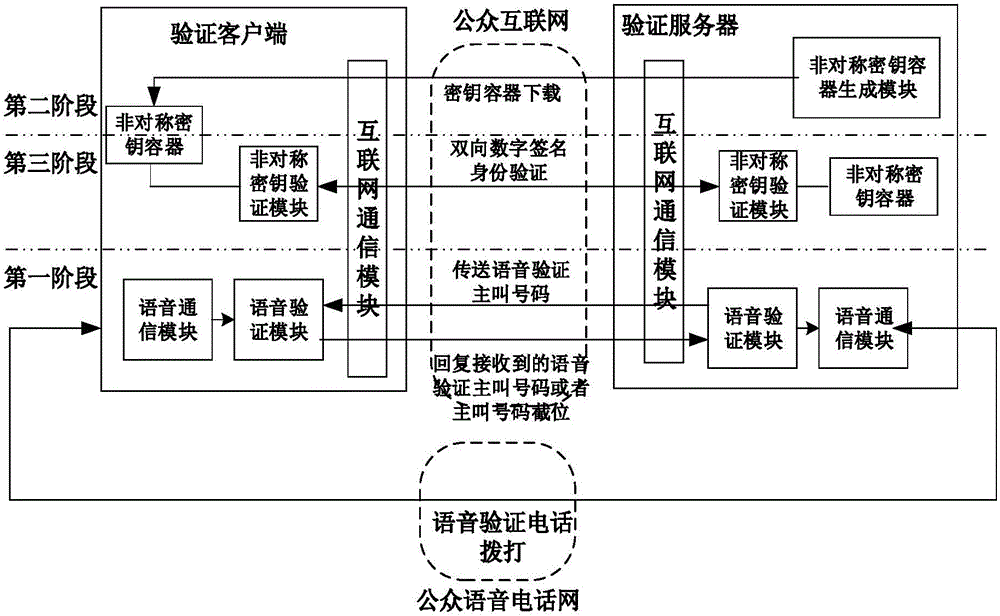
[0070] The present invention proposes a kind of information verification method, and this method comprises the following steps:
[0071] (1) The client sends user registration information to the server, requesting to verify the user's identity;
[0072] The above-mentioned server is used to verify the identity of the user, and after the identity of the user is successfully verified, according to the registration information of the user, a key container file corresponding to the client is generated.
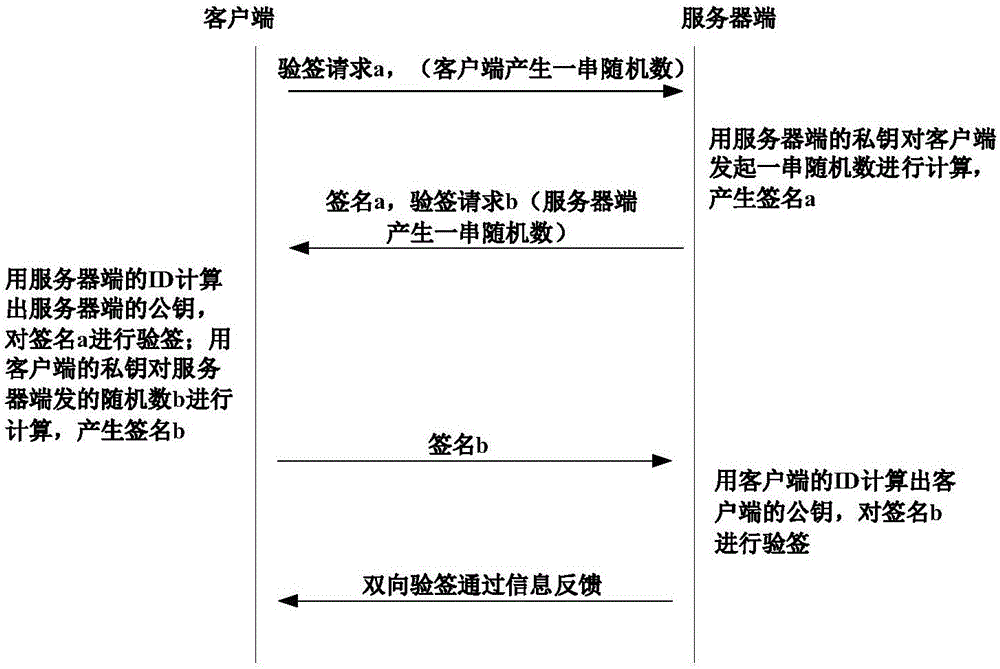
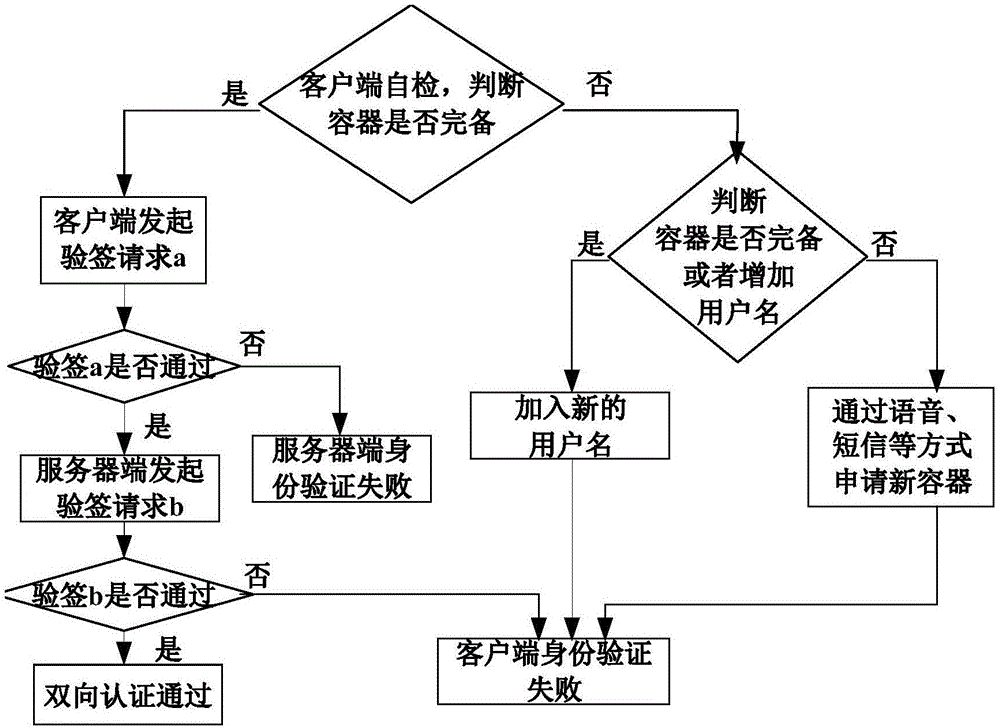
[0073] (2) After receiving the message from the server indicating that the user identity is successfully verified, the client downloads the above key container file from the server or updates the original key container file to the above key container file. The key container file contains the information to be matched, and the public-private key pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com