Data acquisition method and system based on authorization and authentication
A data acquisition and data technology, applied in digital transmission systems, transmission systems, user identity/authority verification, etc., can solve problems such as slowing down data acquisition speed, potential security risks, and no visitor authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
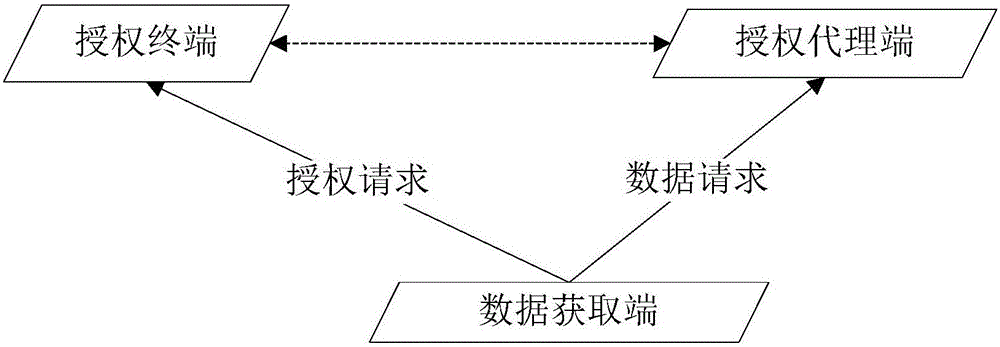
[0014] combine first figure 2 The data acquisition system based on authorization authentication of the present invention is introduced. like figure 2 As shown, the data acquisition system based on authorization authentication of the present invention includes an authorization terminal, a data acquisition terminal, an authorization proxy and a data center, and the data acquisition terminal sends a data request authorized by the authorization terminal to the authorization proxy. To acquire the data of the data center, before the data acquisition terminal sends the authorization request and the data request, the authorized terminal has already shared the first shared encryption key k1 with the data acquisition terminal, and the authorized terminal has already shared the first shared encryption key k1 with the data acquisition terminal. The authorized agents share the second shared encryption key k2. In addition, the encryption key ks (data key) between the data acquisition te...
Embodiment 2
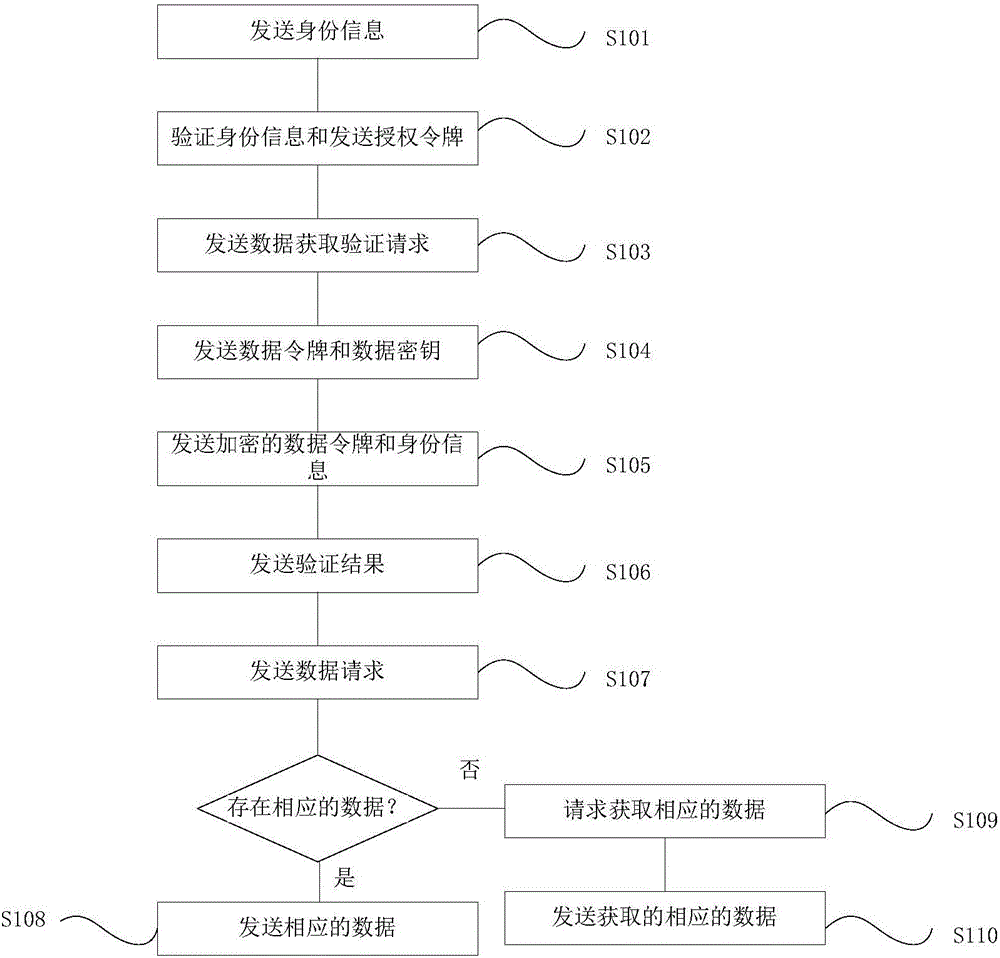
[0027] Next, refer to figure 1 The method for acquiring data by using the data acquisition system based on authorization and authentication in Embodiment 1 is described. like figure 1 As shown, the data acquisition method based on authorization authentication of the present invention comprises the following steps:
[0028] S101: Send identity information
[0029] Specifically, the data acquisition terminal sends its own identity information to the authorized terminal.
[0030] S102: Verify identity information and send authorization token
[0031] Specifically, the authorized terminal receives the identity information and extracts the authorization certificate (including the first shared encryption key k1), and sends to the data acquisition terminal encrypted with the first shared encryption key shared with the data acquisition terminal. The authorization token; at the same time, the authorization token is actually stored in the authorization log database.
[0032] S103: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com