Safety strategy adapting frame and method thereof
A security policy and strategy technology, applied in the field of information security, can solve the problem of not meeting the requirements of policy management, and achieve the effect of strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
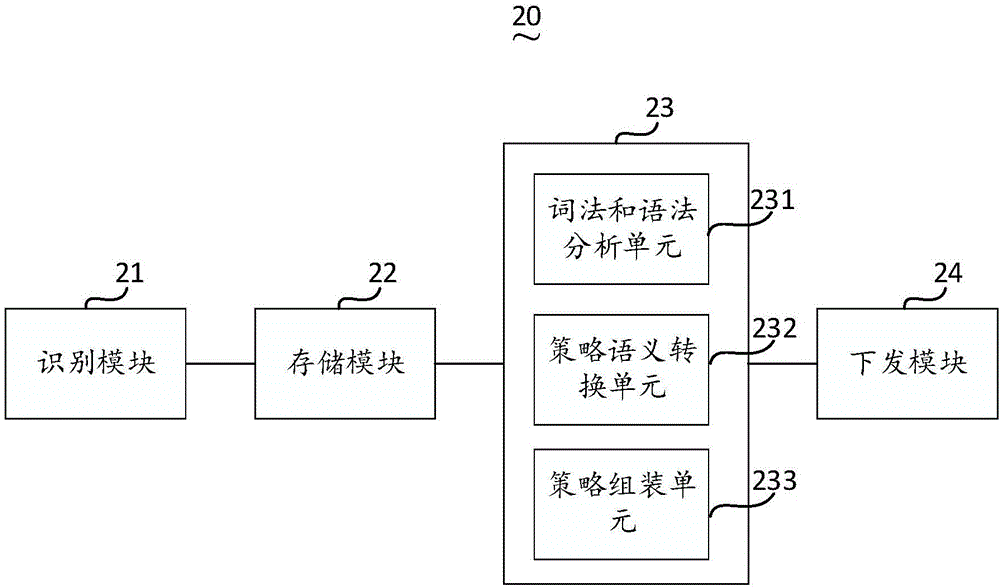
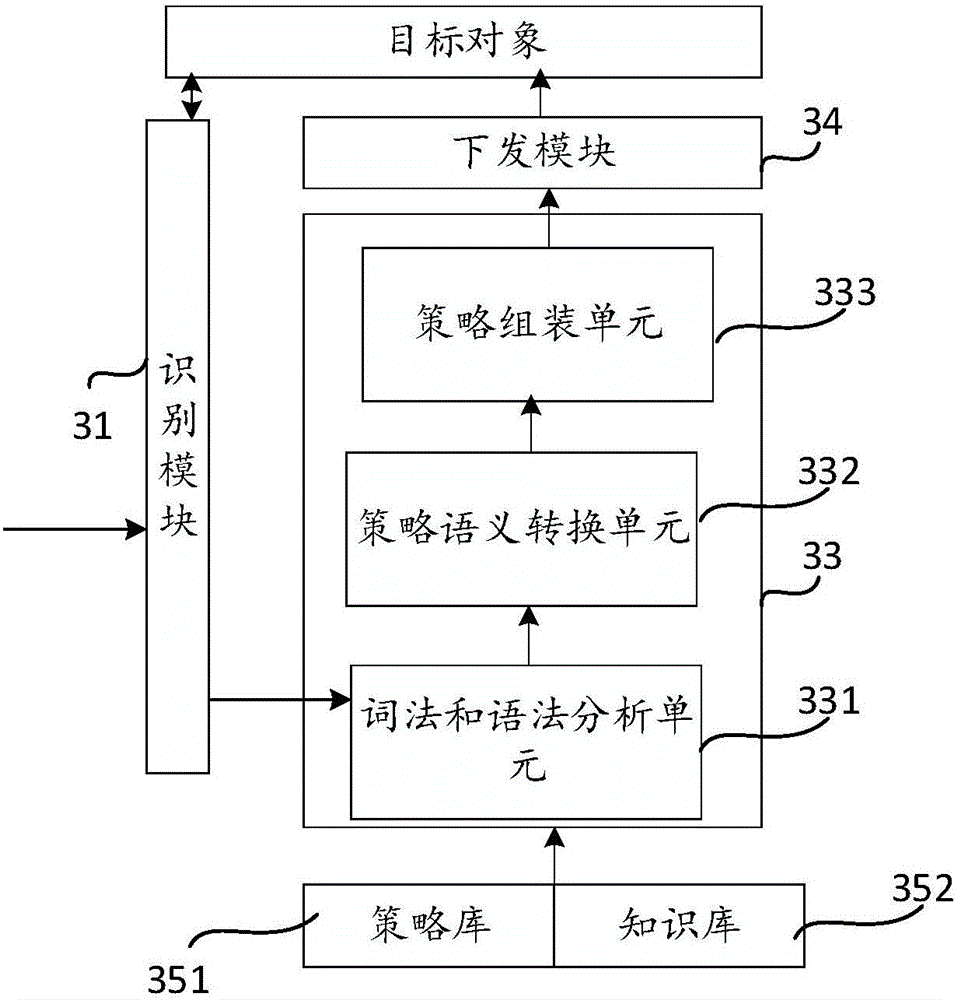
Image
Examples
Embodiment Construction
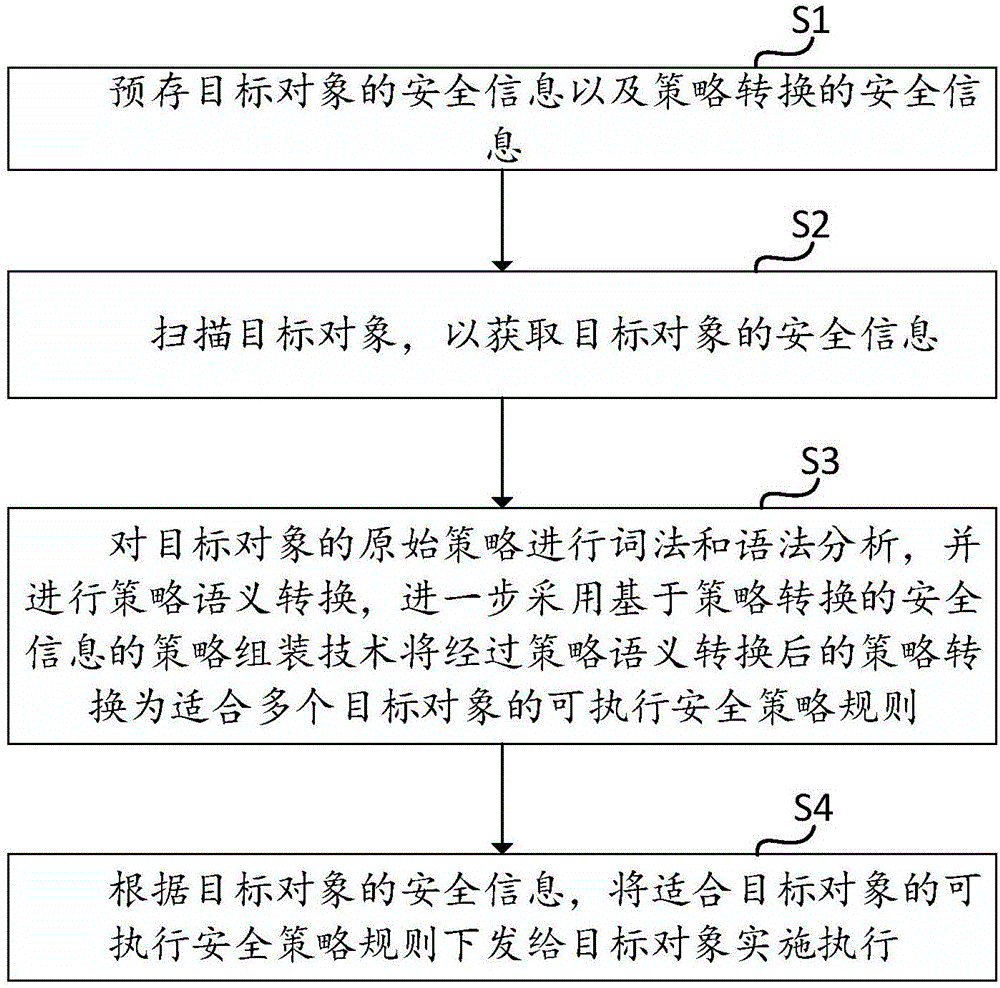
[0032] refer to figure 1 , figure 1 It is a flow chart of a security policy adaptation method provided by the embodiment of the present invention. Such as figure 1 As shown, the method of the embodiment of the present invention comprises the following steps:
[0033] Step S1: pre-store the security information of the target object and the security information of policy conversion.
[0034] Among them, the security information of the target object includes the device type of the target object, the system software in the target object, the type of business software and system patch information, the possible vulnerabilities and security risks of the target object, the deployed security policies in the target object, and the target object safety requirements.
[0035] Wherein, the device type includes a host type, a network type, and a security type. System software includes operating systems, databases, and middleware. Security requirements include class protection requirem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com