Ciphertext indexing method for fuzzy retrieval of encrypted field of database
A technology for encrypting fields and searching indexes, which is applied in the fields of information security and database encryption, can solve the problems of low operation efficiency of character-type encrypted fields, and achieve the effect of accelerating retrieval performance and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0044] This embodiment elaborates a specific example of the process of establishing a ciphertext index oriented to fuzzy retrieval of encrypted fields in a database by applying the present invention in detail.
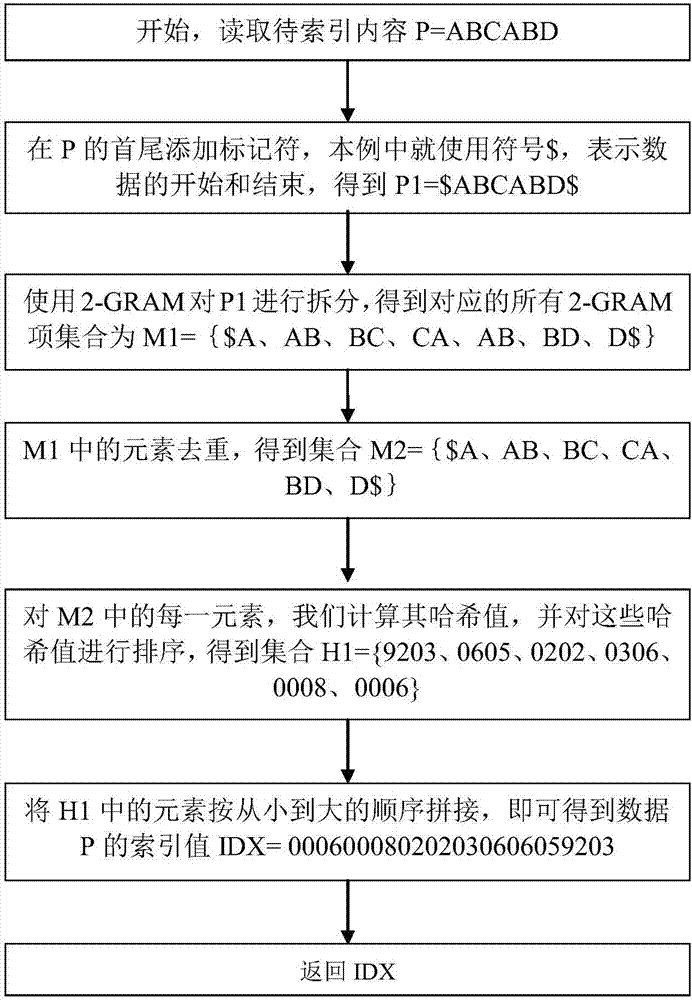
[0045] Set the content of the field to be indexed as a character string P=ABCABD, such as figure 1 As shown, the specific steps of the index building process are as follows:
[0046] (1) Add a marker at the beginning and end of P. In this example, the symbol $ is used as the marker to indicate the beginning and end of the data, and P1=$ABCABD$ is obtained; of course, those skilled in the art can also use other markers for marking ;
[0047] (2) Set K=2, use 2-GRAM to split P1, and obtain the set of all corresponding 2-GRAM items as M1={$A, AB, BC, CA, AB, BD, D$};
[0048] (3) Deduplicate the elements in M1 to obtain the set M2={$A, AB, BC, CA, BD, D$};
[0049] (4) For each element in M2, we calculate its hash value. Taking AB as an example, its hash value is (ASC...
Embodiment 2
[0054] This embodiment elaborates a specific example of a ciphertext index matching process oriented to fuzzy retrieval of database encrypted fields according to the present invention.
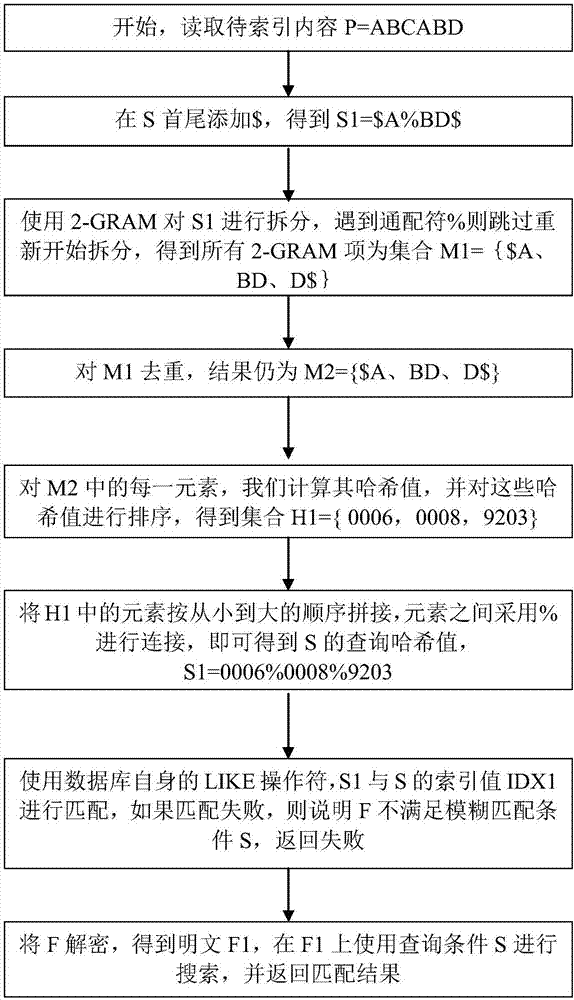
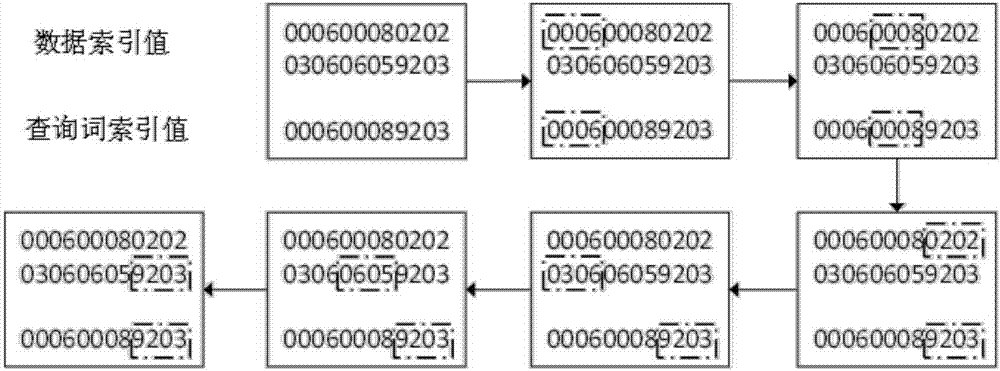
[0055] Suppose that the query condition for fuzzy retrieval is S=A%BD, the retrieved ciphertext is F, and the ciphertext index value of F is IDX1, such as figure 2 As shown, the specific steps of the matching process are as follows:
[0056] (1) Add markers at the beginning and end of S. In this example, $ is used to indicate the beginning and end of the data, and S1=$A%BD$ is obtained;
[0057] (2) Use 2-GRAM to split S1, skip and start splitting again when wildcard % is encountered, and obtain all 2-GRAM items as set M1={$A, BD, D$};
[0058] (3) Deduplication is performed on the set M1. In this example, the result after deduplication is still M2={$A, BD, D$};
[0059] (4) For each 2-GRAM in M2, we calculate its hash value. Taking $A as an example, its hash value is (ASCII($)*ASCII(A))MOD ...
Embodiment 3
[0064] This embodiment elaborates a specific example of a ciphertext index oriented to fuzzy retrieval of database encrypted fields in an ORACLE database according to the present invention.
[0065] Table 1 shows the original data table T1 before encryption in this embodiment. It includes two fields C1 and C2 and there are already some records. The field ROWID is a pseudo-column provided by the ORACLE system, and its value indicates the physical location of each record, and is also the unique identifier of the encrypted record. C1 is a character field, which is a sensitive field and needs to be encrypted.
[0066] Table 1: T1
[0067] ROWID C1 C2 1 ABCABD 1
[0068] First, for the above table T1, rename the field C1 to EC1, store the ciphertext encrypted by the original C1 plaintext in EC1, and add the ciphertext index field IDX_C1 in T1 to store the ciphertext index value of C1, as shown in the table 2 shows:
[0069] Table 2: Encrypted table T1
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com