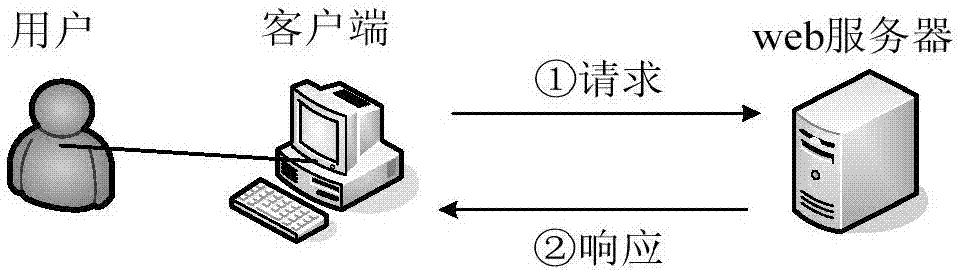
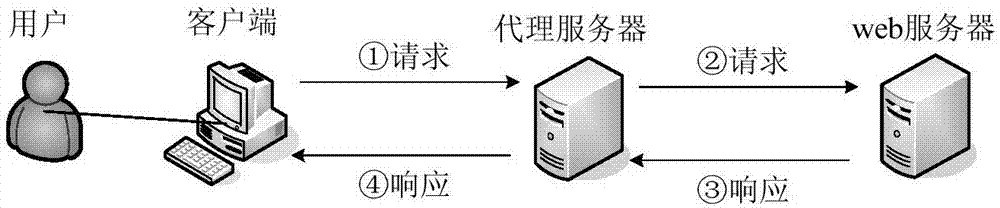
Monitoring method and device for preventing malicious security detection activity
A security detection and malicious technology, applied in the field of computing network security, can solve the problem of not being able to detect malicious attacks as soon as possible, and achieve the effect of reducing malicious attacks and alleviating communication pressure
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0074] Such as Figure 6 Shown is a schematic structural diagram of the monitoring device of this embodiment. In this embodiment, the monitoring device includes two parts: a monitoring unit and a processing unit. Such as Figure 7 Shown is a schematic diagram of the internal structure of the monitoring unit in the monitoring device of this embodiment. Under the same local area network, the monitoring unit is cyclically detected by the program, and the cyclic detection time interval can be adjusted. Considering the hardware I / O overhead, it is recommended to be 1 minute.
[0075] (1) Configuration file module, used for reading configuration file, determines monitoring object;
[0076] (2) an instruction sending module, used to send an instruction to monitor the activity state of the network card to each client;
[0077] (3) a temporary file generation module, used to determine whether the client with the network card in an active state is configured with a local agent; writ...
Embodiment 2
[0080] Such as Figure 9 Shown is a scheme diagram of the monitoring device of this embodiment. Such as Figure 10 Shown is the working flow chart of the monitoring device of this embodiment. Its working steps are:
[0081] (1) Perform parameter configuration on the monitoring module to determine the monitoring object, such as a certain client ip or an ip segment of a certain client, and write it into the configuration file.
[0082] (2) The monitoring module reads the configuration file and determines the monitoring object.
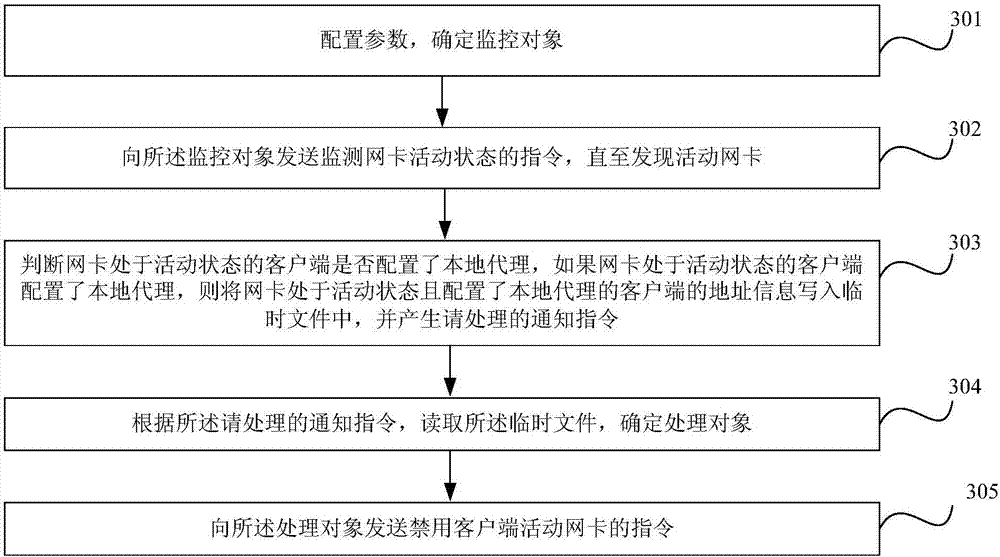
[0083] (3) Send an instruction to monitor the activity state of the network card to the detection object, and jump to the next step if an active network card is found, otherwise, this step is a 1-minute cycle.
[0084] (4) Determine whether the client whose network card is in an active state is configured with a local agent, and jump to the next step if the local agent is found, otherwise jump to step (3).
[0085] (5) Write the ip of the client who...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com