Multi-tenant-based safe configuration method of virtual machine in cloud data center
A cloud data center and security configuration technology, applied in the field of computer networks, can solve problems such as insufficient multi-tenancy, system resource fragmentation cloud, etc., and achieve the effect of satisfying security allocation and improving service quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
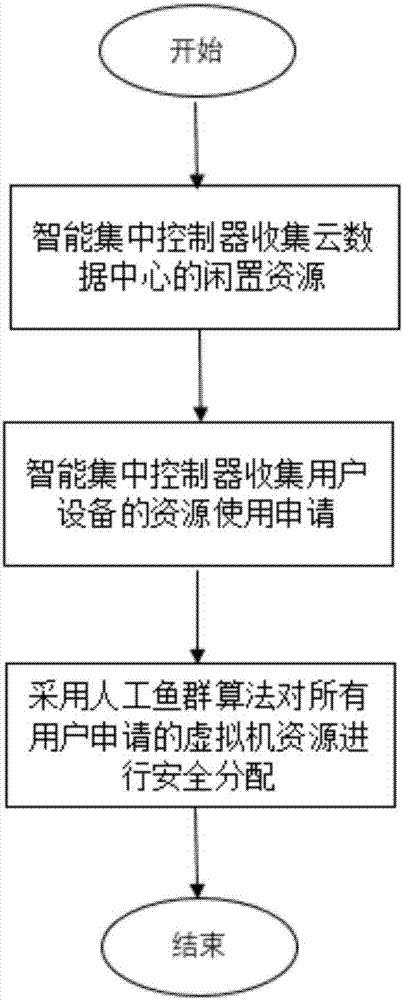
[0033] combine figure 1 , the present invention is based on the multi-tenant virtual machine security configuration method in the cloud data center, comprising the following steps:
[0034] Step 1, the intelligent centralized controller collects the idle resources of the cloud data center, and the resources are virtual machines in the cloud system that can be applied for by users;
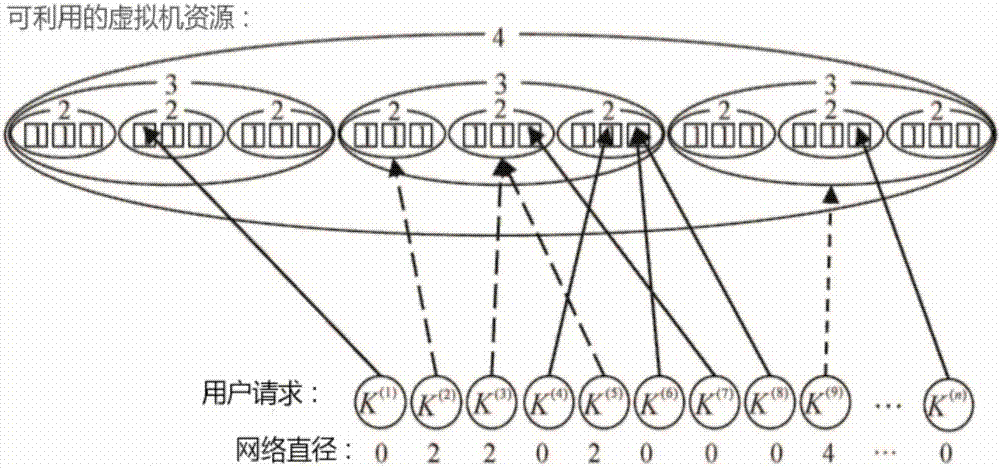
[0035] combine figure 2 , step 2, the intelligent centralized controller collects the resource usage application of the user equipment;
[0036] Further, the resource usage application mentioned in step 2 includes the time ratio required by the user equipment, the number of resources required by the user equipment, and the minimum rate required by the user equipment.
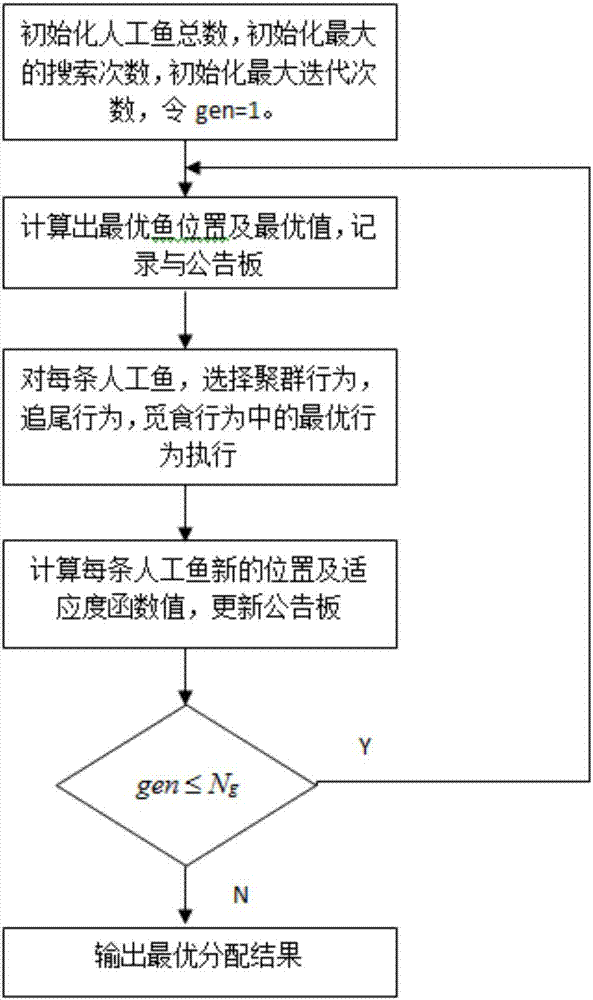
[0037] combine image 3 , step 3, the intelligent centralized controller uses the artificial fish swarm algorithm to securely allocate the virtual machine resources requested by all users, and the specific process is as follows: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com