Registration authenticating method
A technology for registration and authentication and authentication information, applied in the field of communication, can solve the problems of private key leakage, single method, certificate attack, etc., to solve the contradiction between security and convenience, reduce technical difficulty, and improve the effect of speed.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
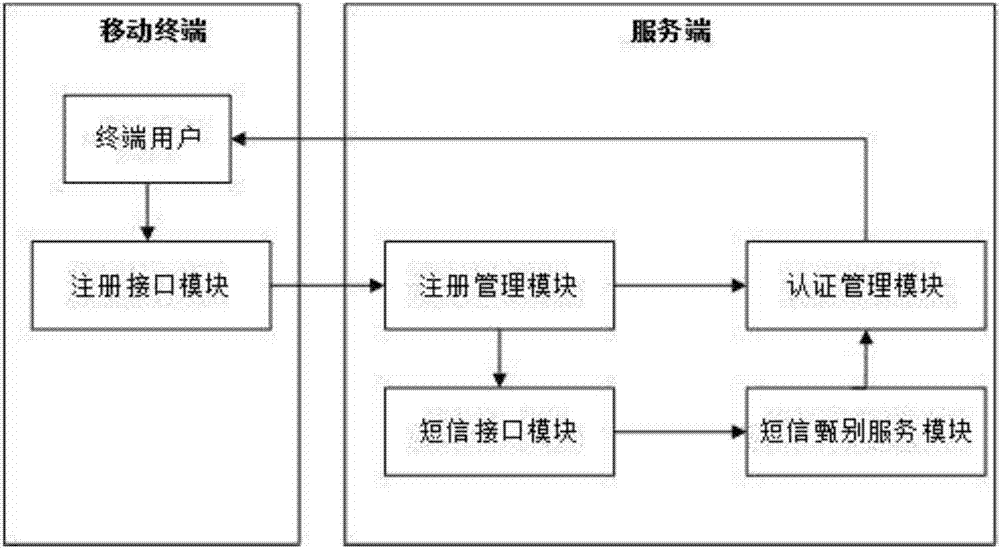
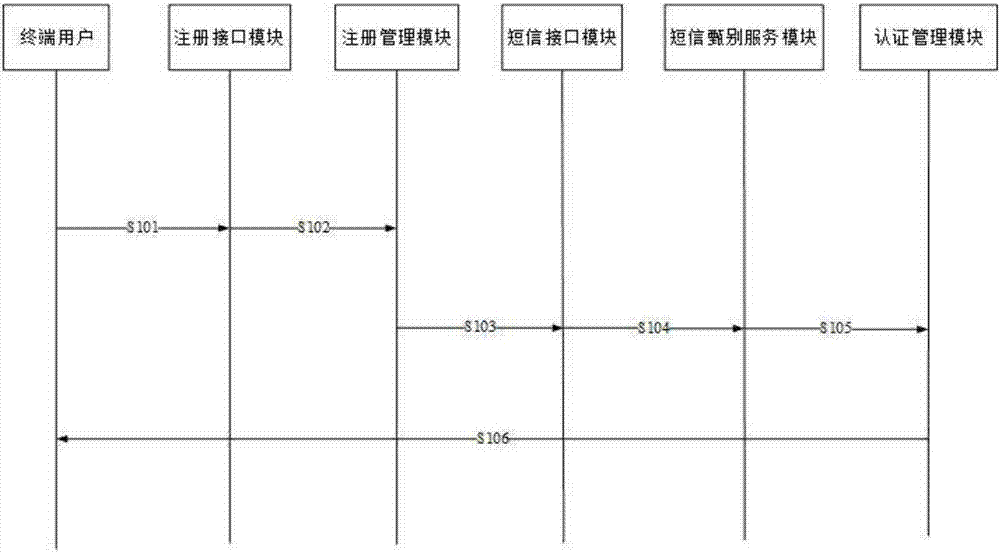
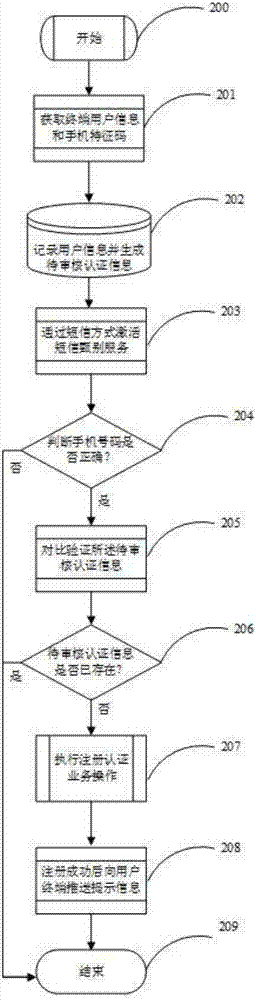
[0025] figure 1 It is a structure of an embodiment of a registration authentication method, mainly composed of a mobile terminal and a server, wherein a registration interface module is used to obtain terminal user information and mobile phone feature codes; a registration management module is used to record user information and mobile phone feature codes And generate the authentication information to be audited; the SMS interface module is used to activate the SMS screening service for the authentication information to be audited by SMS; the SMS screening service module is used to verify the correctness of the mobile phone number in the authentication information to be audited; the authentication management module uses By comparing and verifying the authentication information to be reviewed that has passed the SMS screening, and after the user information is successfully registered or updated, a prompt message of successful registration or update is pushed to the user terminal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com