Internet-of-things vulnerability scanning system and scanning method
A vulnerability scanning and Internet of Things technology, applied in the Internet of Things vulnerability scanning system and scanning field, can solve problems such as low efficiency, affecting the quality of target network transmission, wireless network impact, etc., and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0062] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
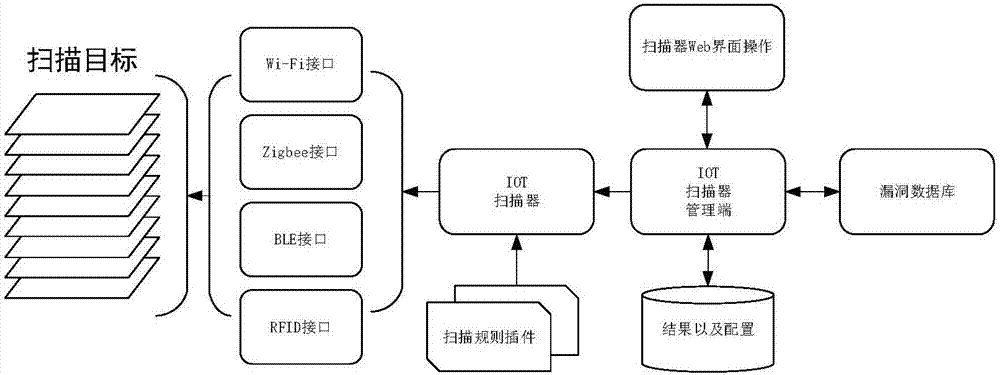
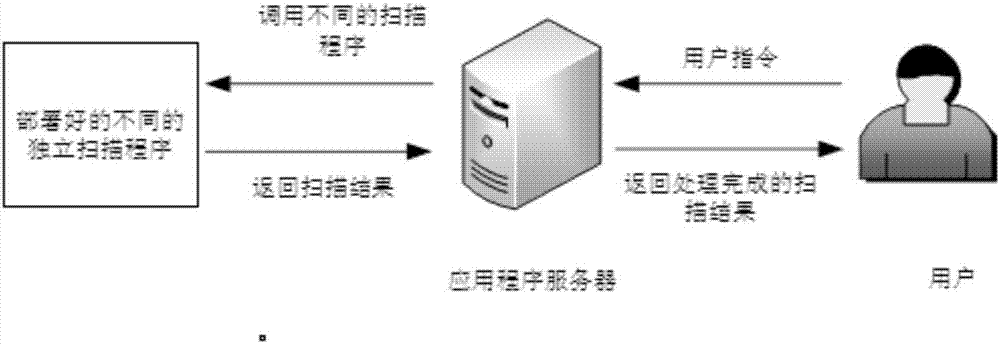
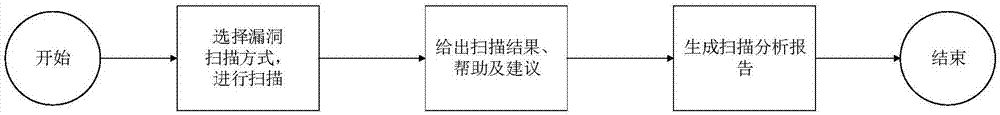
[0063] Such as Figure 1-7 As shown, an IoT vulnerability scanning device includes four modules, which are mainly divided into traffic sniffer, scanner, server, and Web visualization terminal. Next, the four modules are introduced:
[0064] 1. Traffic Interceptor: The traffic sniffer model provides a flexible bottom layer access to wireless communication. It is mainly used to passively monitor the communication traffic in the Internet of Things environment, and less active detection data packets. The current popular and low-cost software-defined radio technology is used to process the physical layer traffic, and then decapsulated and transmitted to the link layer. , being able to capture traffic packets of various protocols is a prerequisite, the system uses a device to process a protocol, so traffic sniffing devices include wireless network cards that...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com