Method and system for classifying and predicting network security incidents
A network security and prediction method technology, applied in the field of network security event classification and prediction methods and systems, can solve the problem of lack of detection of attack behavior characteristics, and achieve the effect of improving classification detection accuracy, improving efficiency, and network security assurance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
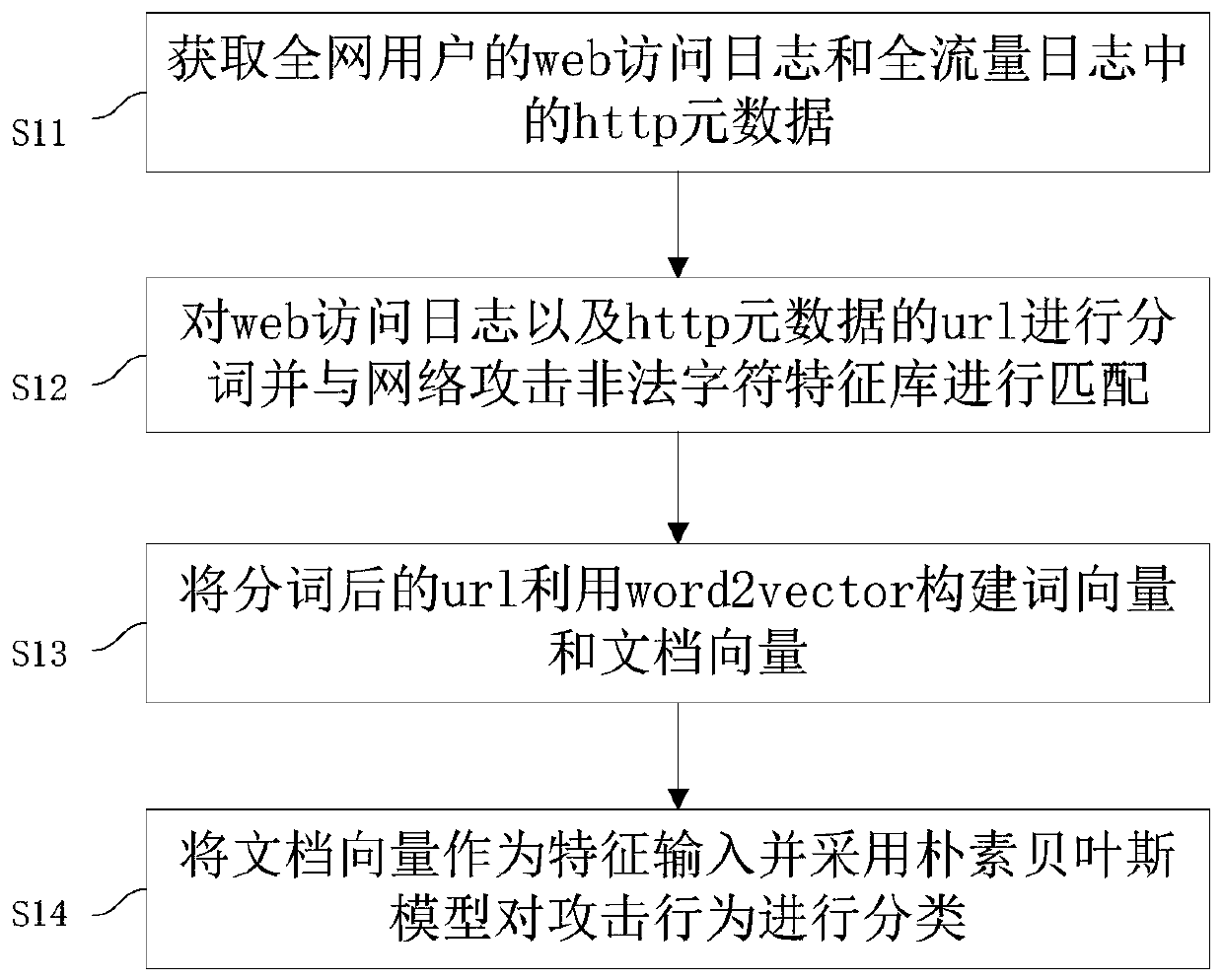
[0070] This embodiment provides a method for classifying and predicting network security events, such as figure 1 shown, including steps:
[0071] S11: Obtain the http metadata in the web access log and the full traffic log of the users of the whole network;
[0072] S12: Segment the URL of the web access log and http metadata and match it with the network attack illegal character feature library;
[0073] S13: use word2vector to construct word vectors and document vectors from the segmented url;
[0074] S14: The document vector is used as feature input and the naive Bayesian model is used to classify the attack behavior.
[0075] The analysis object of this embodiment is the http metadata in the user's web access log and the global traffic log. After parsing and analyzing the data, it is found that the key features of mainstream network attacks are mainly reflected in the url. Since the url usually contains a large number of characters, it is necessary to perform natural la...
Embodiment 2
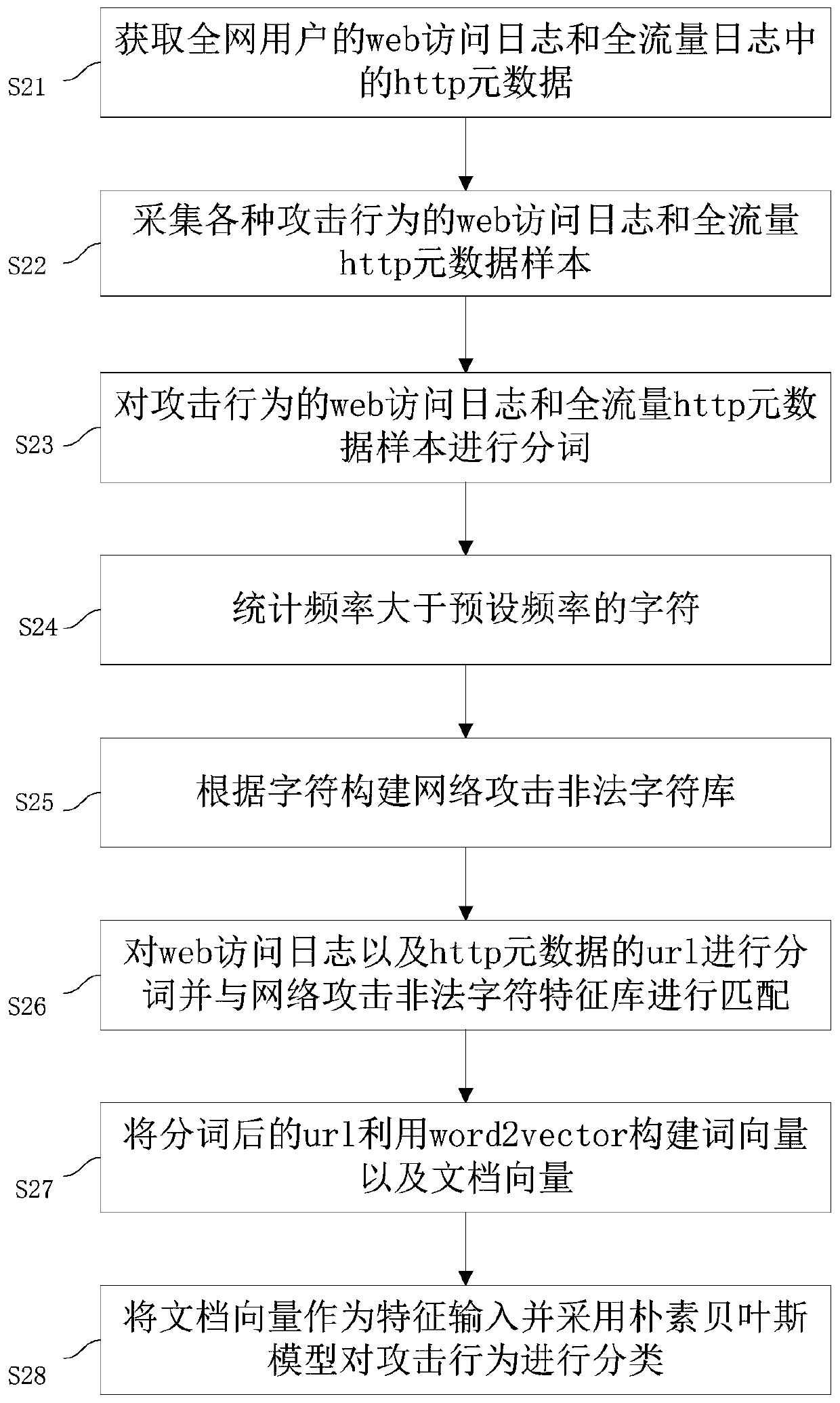
[0090] This embodiment provides a method for classifying and predicting network security events, such as figure 2 shown, including steps:
[0091] S21: Obtain the http metadata in the web access log and the full traffic log of the users of the whole network;
[0092] S22: collect web access logs and full-flow http metadata samples of various attack behaviors;
[0093] S23: Segment the web access log of the attack behavior and the full-traffic http metadata sample;
[0094] S24: count characters whose frequency is greater than a preset frequency;
[0095] S25: Construct a network attack illegal character feature library based on characters;
[0096] S26: Segment the URL of the web access log and http metadata and match it with the network attack illegal character feature library;
[0097] S27: use word2vector to construct word vector and document vector from the url after word segmentation;
[0098] S28: The document vector is used as a feature input and the naive Bayesia...
Embodiment 3
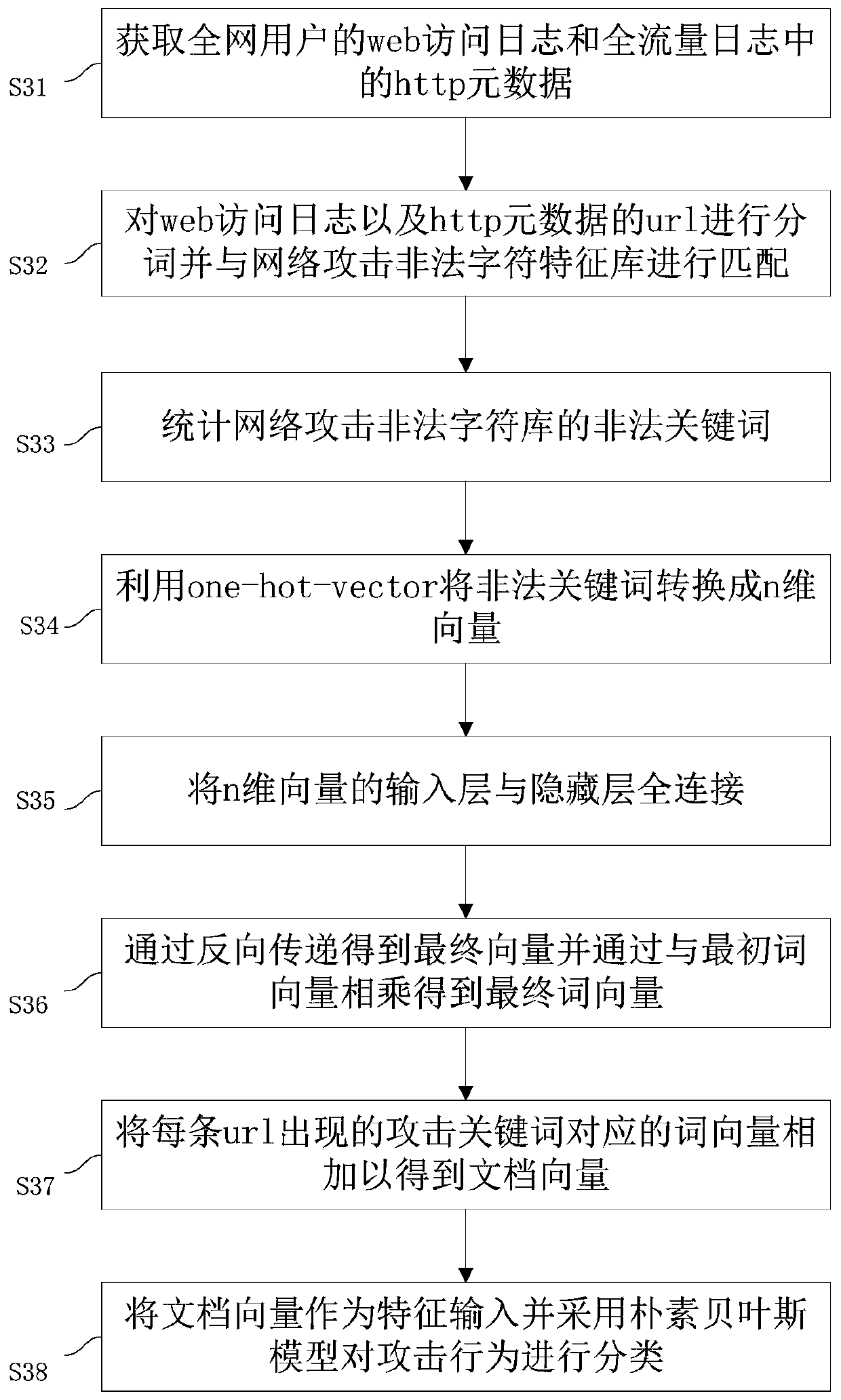
[0120] This embodiment provides a method for classifying and predicting network security events, such as image 3 shown, including steps:
[0121] S31: Obtain the http metadata in the web access log and the full traffic log of the users of the whole network;
[0122] S32: Segment the URL of the web access log and http metadata and match it with the network attack illegal character feature library;
[0123] S33: Statistically counting the illegal keywords of the network attack illegal character feature library;
[0124] S34: Using one-hot-vector to convert illegal keywords into n-dimensional vectors;
[0125] S35: Fully connect the input layer of the n-dimensional vector with the hidden layer;
[0126] S36: Obtain the final vector by backward transfer and multiply the initial word vector to obtain the final word vector;
[0127] S37: add the word vectors corresponding to the attack keywords appearing in each url to obtain the document vector;
[0128] S38: The document vecto...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com