Data security detection method and terminal
A technology for data security and detection methods, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as narrow applicability, inconvenient operation, inability to capture data packets of other protocols, etc. The effect of wide applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
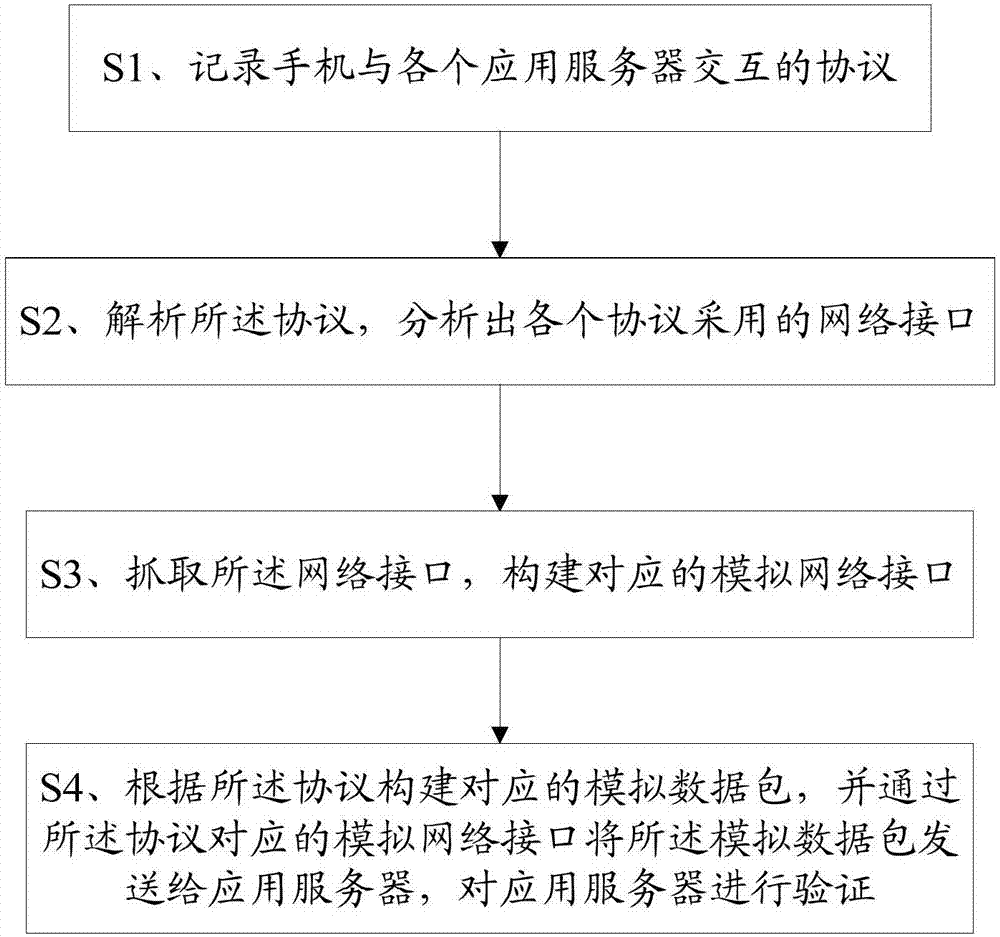
[0051] A data security detection method, comprising the steps of:
[0052] S1. Record the protocol for interaction between the mobile phone and each application server;
[0053] Described agreement comprises HTTP / HTTPS agreement, websockets agreement etc. mobile phone and each application server carry out the commonly used agreement of interaction;
[0054] S2. Analyzing the protocols, and analyzing the network interfaces adopted by each protocol;
[0055] For example, analyze the protocol status when posting, and analyze the network interface it uses; analyze the protocol status during live broadcast, and analyze the network interface it uses;
[0056] S3. Grab the network interface and build a corresponding simulated network interface;
[0057] In order to improve the efficiency of data security detection, the working mode of each simulated network interface can be set to parallel working mode;
[0058] S4. Construct a corresponding simulated data packet according to the ...
Embodiment 2
[0065] Apply the method described in Embodiment 1 to a specific scene, such as posting a talk on the AR community.
[0066] Locally limit the published comment to no more than 256 characters; analyze the protocol used to interact with the business server in the AR community, obtain the network interface used by it, capture the network interface, and build the corresponding Simulate the network interface; then construct a simulated data packet, which is used to simulate the talk published by the user on the AR community, and the said talk contains 257 characters; after the construction is completed, pass the constructed talk through the simulated network interface Said to be sent to the corresponding business server, if you get a successfully sent message fed back by the server after submission, it means that the server does not limit the number of characters published by the user, the limit only exists locally, if you get the server feedback after submission For failed message...
Embodiment 3
[0068] Apply the method described in Embodiment 1 to specific scenarios, such as checking teammate information on the Hero Blade mobile assistant and participating in activities.
[0069] It is restricted locally that only the teammate can view each other’s information and participate in activities; analyze the protocol adopted by the hero blade mobile assistant to interact with the business server, obtain the network interface used by it, grab the network interface, and build Corresponding simulated network interface; Then construct the simulated data packet, be used for simulating the user to check teammate information, participate in the activity, and described user is not the teammate of the team member who will check information; After constructing, pass described simulated network interface The constructed team member information viewing request is sent to the corresponding business server. If you get the corresponding team member information fed back by the server after ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com