Verification method and device
A verification method and a technology of a verification device, which are applied in the field of communication, can solve problems such as the inability to effectively prevent machine programs from recognizing verification codes, and achieve the effect of increasing difficulty and reducing the pass rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
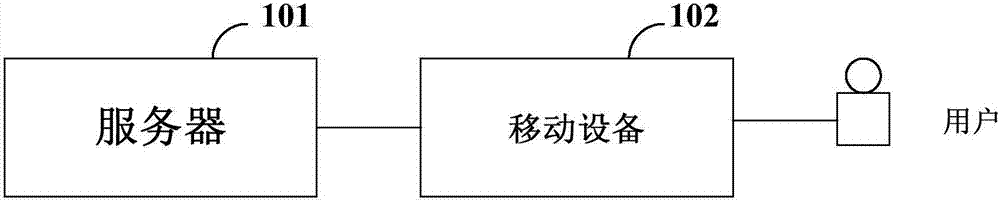
[0062] Combine below figure 1 application scenarios, combined below figure 1 application scenarios, refer to figure 2 A method of a verification method according to an exemplary embodiment of the present invention will be described. It should be noted that the above application scenarios are only shown for the purpose of understanding the spirit and principle of the present invention, and the implementation manners of the present invention are not limited in this respect. On the contrary, the embodiments of the present invention can be applied to any applicable scene.
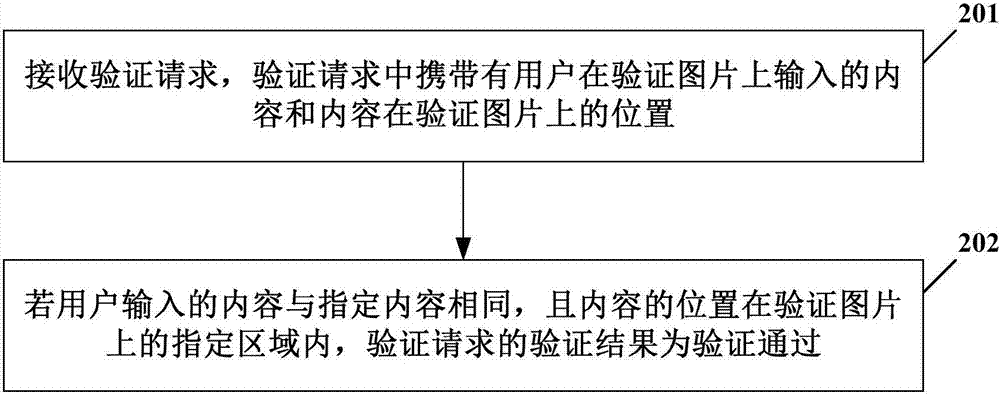
[0063] figure 2 It schematically shows the flow of an example of the verification method according to the implementation of the present invention.
[0064] like figure 2 As shown, the verification method in this embodiment may specifically include, for example:
[0065] Step 201 , receiving a verification request, which carries the content input by the user on the verification picture and the position ...
no. 2 example
[0078] Combine below figure 1 application scenarios, combined below figure 1 application scenarios, refer to image 3 A method of a verification method according to an exemplary embodiment of the present invention will be described. It should be noted that the above application scenarios are only shown for the purpose of understanding the spirit and principle of the present invention, and the implementation manners of the present invention are not limited in this respect. On the contrary, the embodiments of the present invention can be applied to any applicable scene.
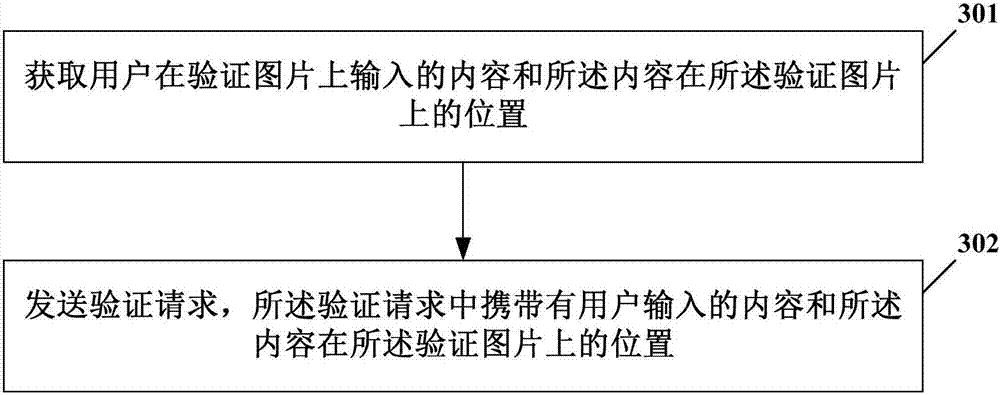
[0079] image 3 It schematically shows the flow of an example of the verification method according to the implementation of the present invention.
[0080] like image 3 As shown, the verification method in this embodiment may specifically include, for example:
[0081] Step 301 , acquire the content input by the user on the verification picture and the position of the content on the verification picture,...
no. 3 example
[0092] see Figure 4 , the figure shows the flow of the verification method. The scenarios of the verification method can be the verification scenario when mobile payment, the verification scenario when logging into the chat client, the verification scenario when retrieving the password or changing the password. It should be noted that, In this embodiment, the verification scenario is not specifically limited, and the specific steps are as follows:
[0093] Step 401, the verification code plug-in of the business client applies for a verification code question to the verification code platform.
[0094] The above-mentioned service client may be an existing application client, such as a payment client, a chat client, etc., and of course it is not limited thereto.
[0095] It should be noted that the verification code questions in this embodiment include coloring task pictures and coloring card pictures, wherein the coloring card picture is an interface for users to color, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com