Identity authentication method and apparatus
An identity authentication and identity technology, applied in the field of identity authentication methods and devices, can solve problems that are not suitable for identity authentication, and achieve the effect of improving security and reducing bandwidth occupation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
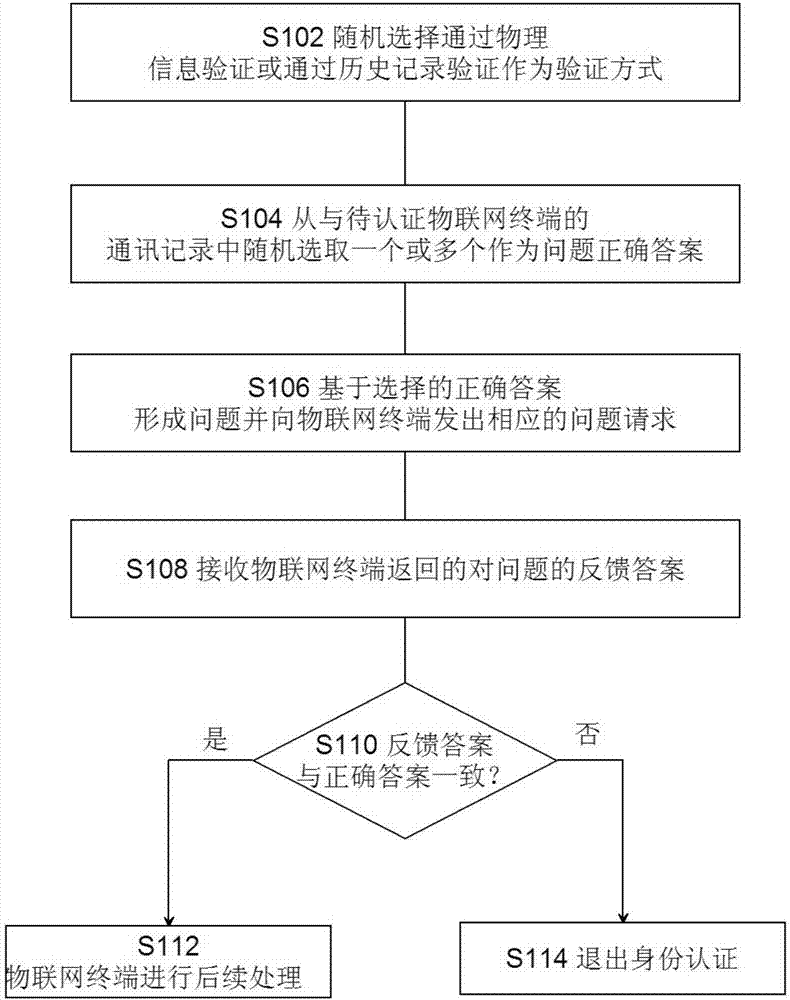
[0045] According to an embodiment of the method of the present invention, before using the method of the present invention for identity authentication, the traditional user name plus password verification method can also be used. After the authentication of the user name and password, the authentication of the method of the present invention is carried out to realize double authentication.
[0046] According to another embodiment of the method of the present invention, the method further includes, if the first end does not receive a feedback answer to the question from the second end within a predetermined time, then determine that the identity authentication has failed, and the second end cannot perform subsequent processing .
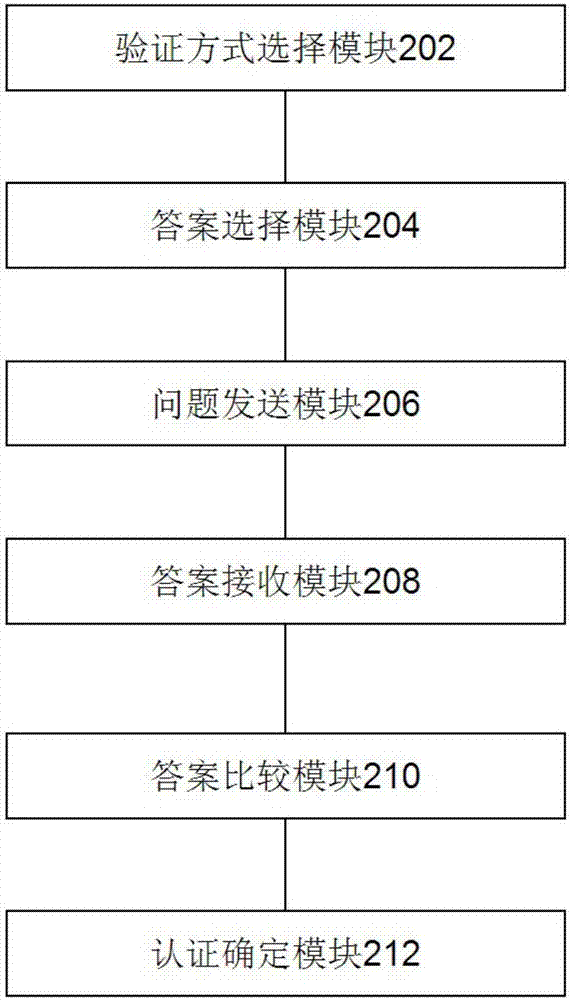
[0047] figure 2A schematic structural diagram of an embodiment of the present invention is shown. The device in this embodiment includes: a verification mode selection module 202, configured to, in response to authenticating the identity of the sec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com