Trusted BMC (Baseboard Management Controller)-based server safe-starting method
A server security and server technology, applied in the field of server security startup based on trusted BMC, can solve problems such as inability to guarantee BMC security interface call capability, high system overhead, lack of security function support, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The trusted BMC-based server secure startup method will be further described in detail below with reference to the implementation manner and the accompanying drawings.
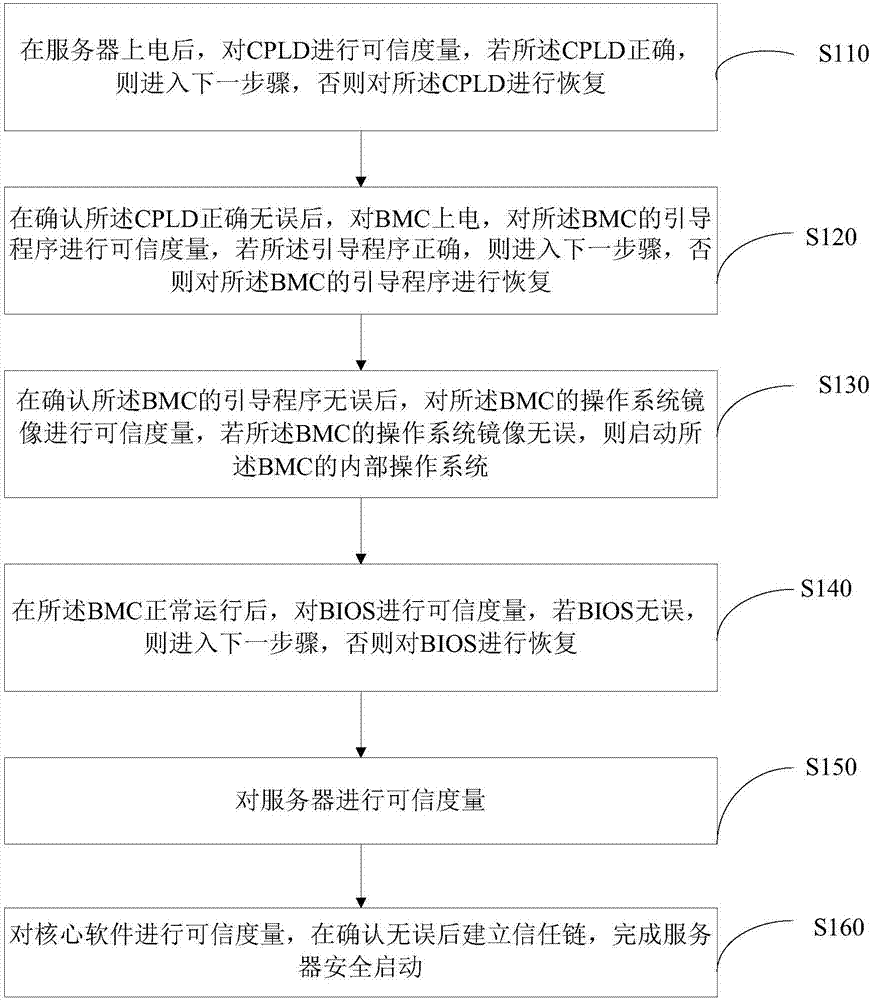
[0035] see figure 1 , a trusted BMC-based server secure startup method of an embodiment, comprising steps:
[0036] S110. After the server is powered on, measure the reliability of the CPLD. If the CPLD is correct, proceed to the next step; otherwise, restore the CPLD.
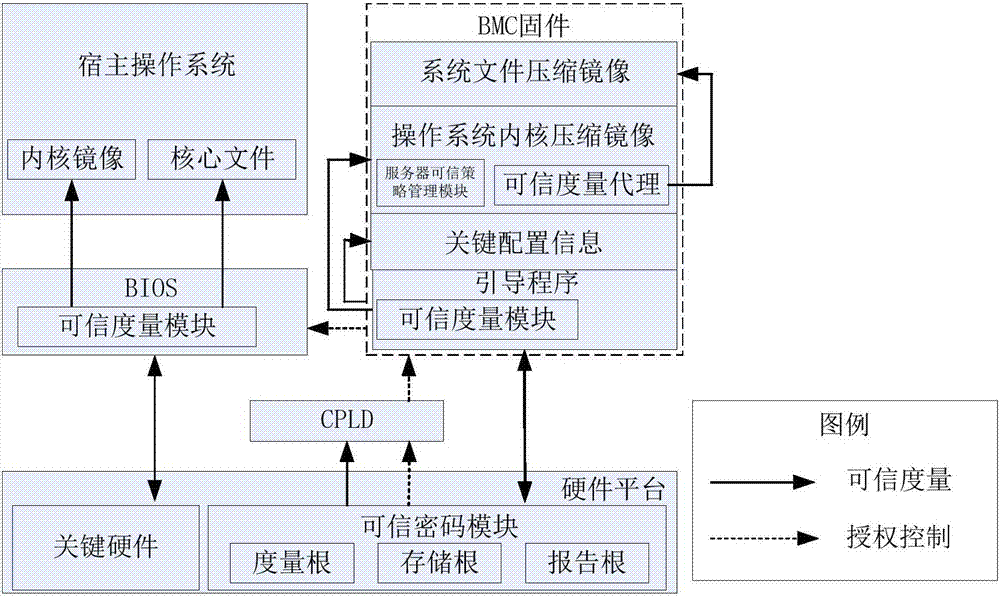
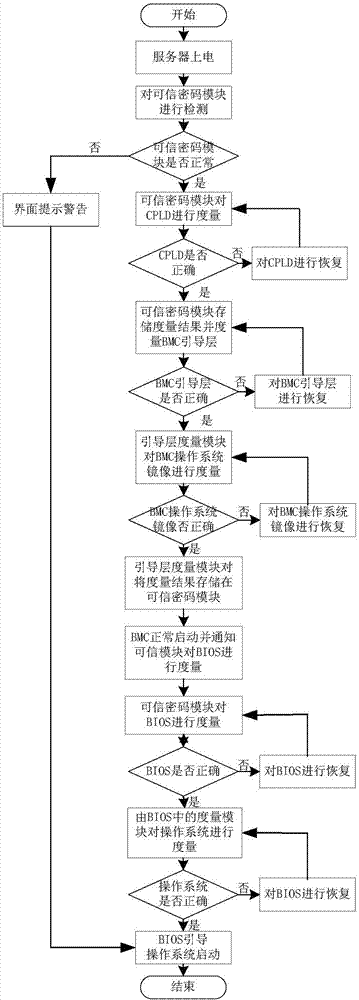
[0037] see figure 2 and 3 , in one embodiment, the trusted cryptographic module is used to measure the integrity of the code in the CPLD to determine whether the CPLD is correct, and the CPLD measurement result is stored in the trusted cryptographic module. If the CPLD is correct, go to step S120, otherwise restore the CPLD.
[0038] Specifically, the trusted cryptographic module includes TPM, TCM, TPCM and other software / hardware modules with trusted computing functions. The module can complete trusted computing tasks in at least...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com