A method and system for confirming data rights based on encryption
一种加密数据、数据的技术,应用在信息处理领域,能够解决不能较好的支撑数据开放、共享、应用等问题,达到保证专有性的效果
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
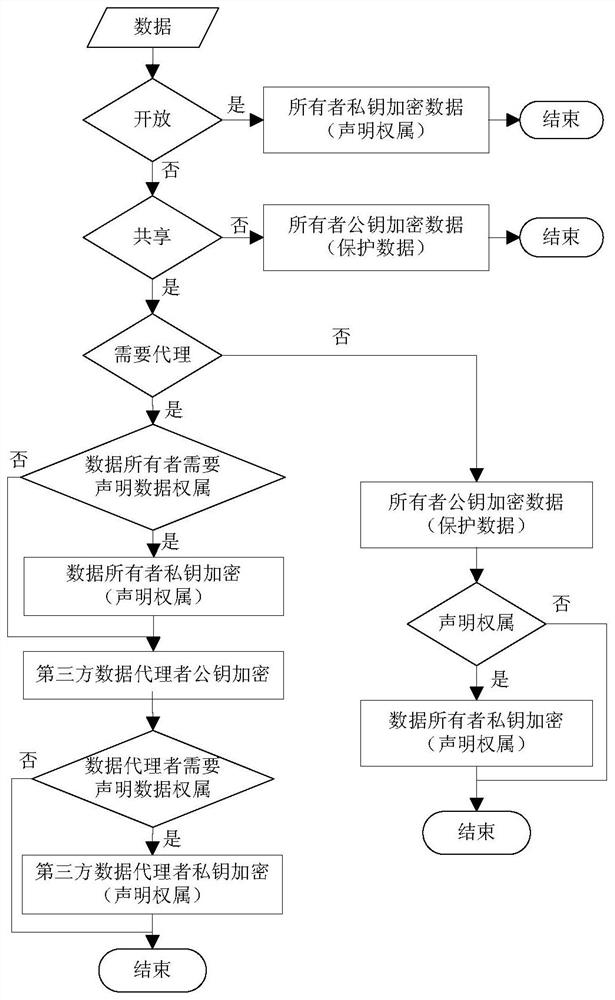
[0050] A method for confirming data rights based on encryption, comprising the following steps:
[0051] A. Determine whether the data is open. If the data is open, the data owner uses his private key to encrypt the data to complete the ownership declaration and end the process; if the data is not open, proceed to step B;
[0052] B. Determine whether the data is shared. If the data cannot be shared, the data owner uses his own public key to encrypt the data to complete the data protection and end the process; if the data can be shared, enter the ownership declaration and protection steps.
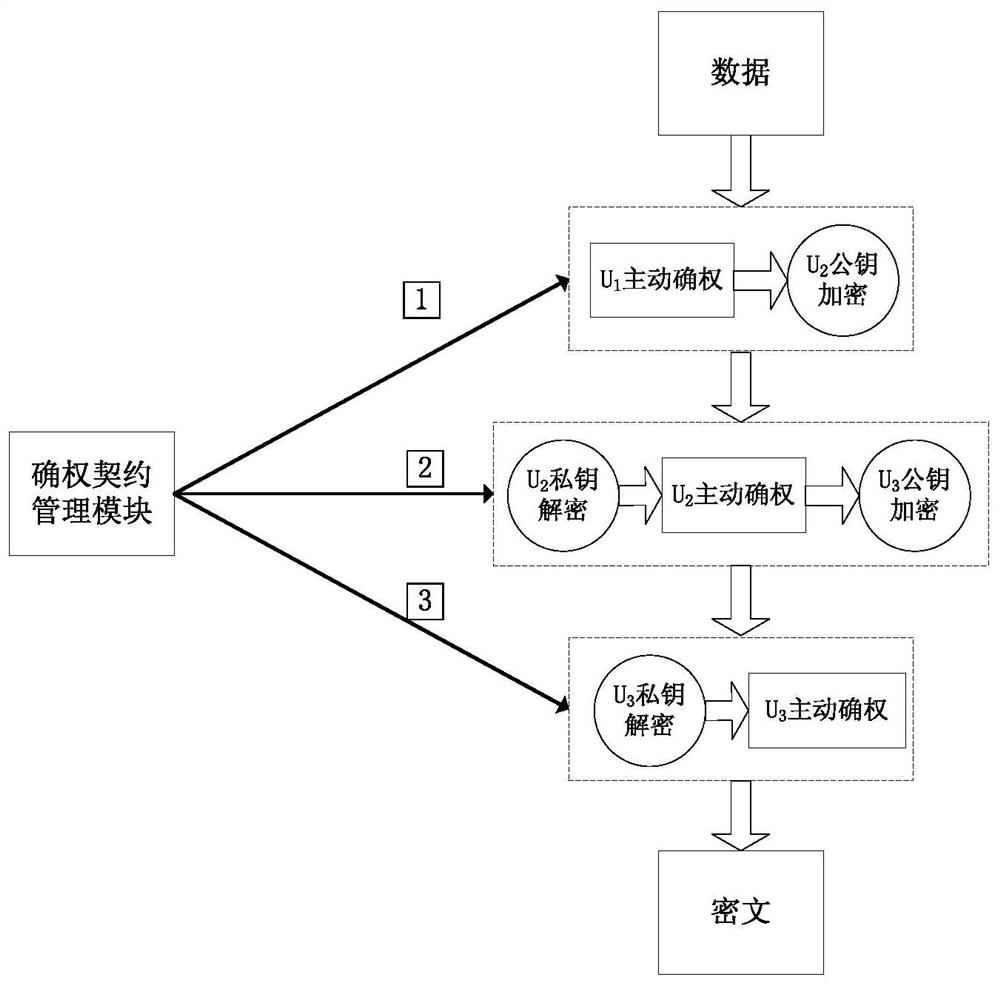
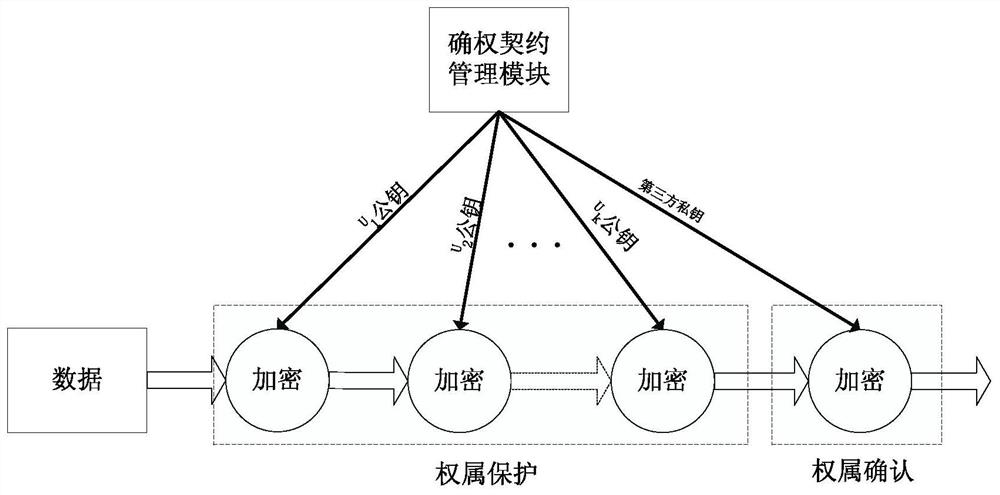
[0053] Such as figure 1 As shown, the ownership declaration and protection step includes the self ownership declaration and protection step and the agency ownership declaration and protection step, that is, includes an active right confirmation method and a passive right confirmation method.
[0054]That is to say, for different data and different usage situations, the above-mentioned met...
Embodiment 2
[0056] This embodiment is an active right confirmation method using self-declaration and protection steps. The method is specifically:
[0057] A. Determine whether the data is open. If the data is open, the data owner uses his private key to encrypt the data to complete the ownership declaration and end the process; if the data is not open, proceed to step B;
[0058] B. Determine whether the data is shared. If the data cannot be shared, the data owner uses his own public key to encrypt the data to complete the data protection and end the process; if the data can be shared, the data owner uses his own public key to encrypt the data to complete the data protection;
[0059] Determine whether the data ownership needs to be declared, and if not, end the process; if necessary, the data owner uses his private key to encrypt the data to complete the ownership declaration.
Embodiment 3
[0061] This embodiment is a passive right confirmation method that adopts proxy ownership declaration and protection steps. The method is specifically:
[0062] A. Determine whether the data is open. If the data is open, the data owner uses his private key to encrypt the data to complete the ownership declaration and end the process; if the data is not open, proceed to step B;
[0063] B. Determine whether the data is shared. If the data cannot be shared, the data owner uses his own public key to encrypt the data to complete the data protection and end the process; if the data can be shared, enter the step of judging whether it is an agent;
[0064] Judging whether the data needs a proxy, if no proxy is required, the data owner uses his own public key to encrypt the data to complete data protection; judging whether the data ownership needs to be declared, if not, the process ends; if necessary, the data owner uses Encrypt the data with your own private key to complete the owne...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com