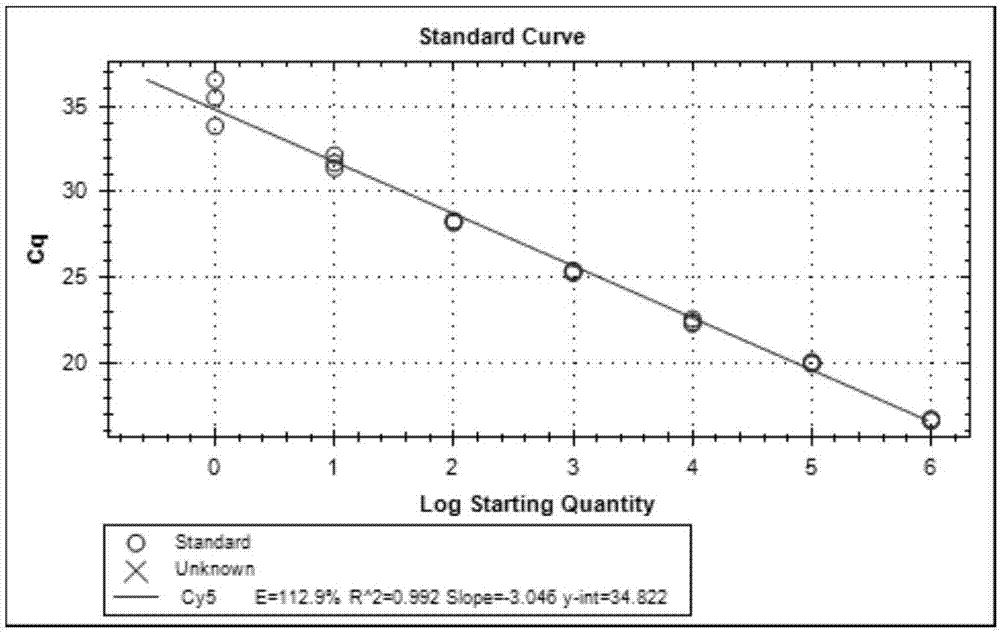
Patents
Literature
31results about How to "Guaranteed exclusivity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
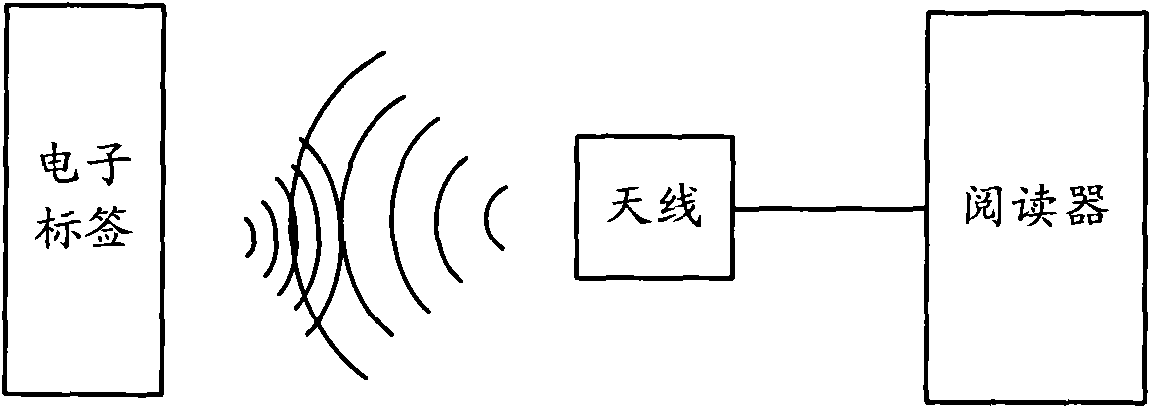
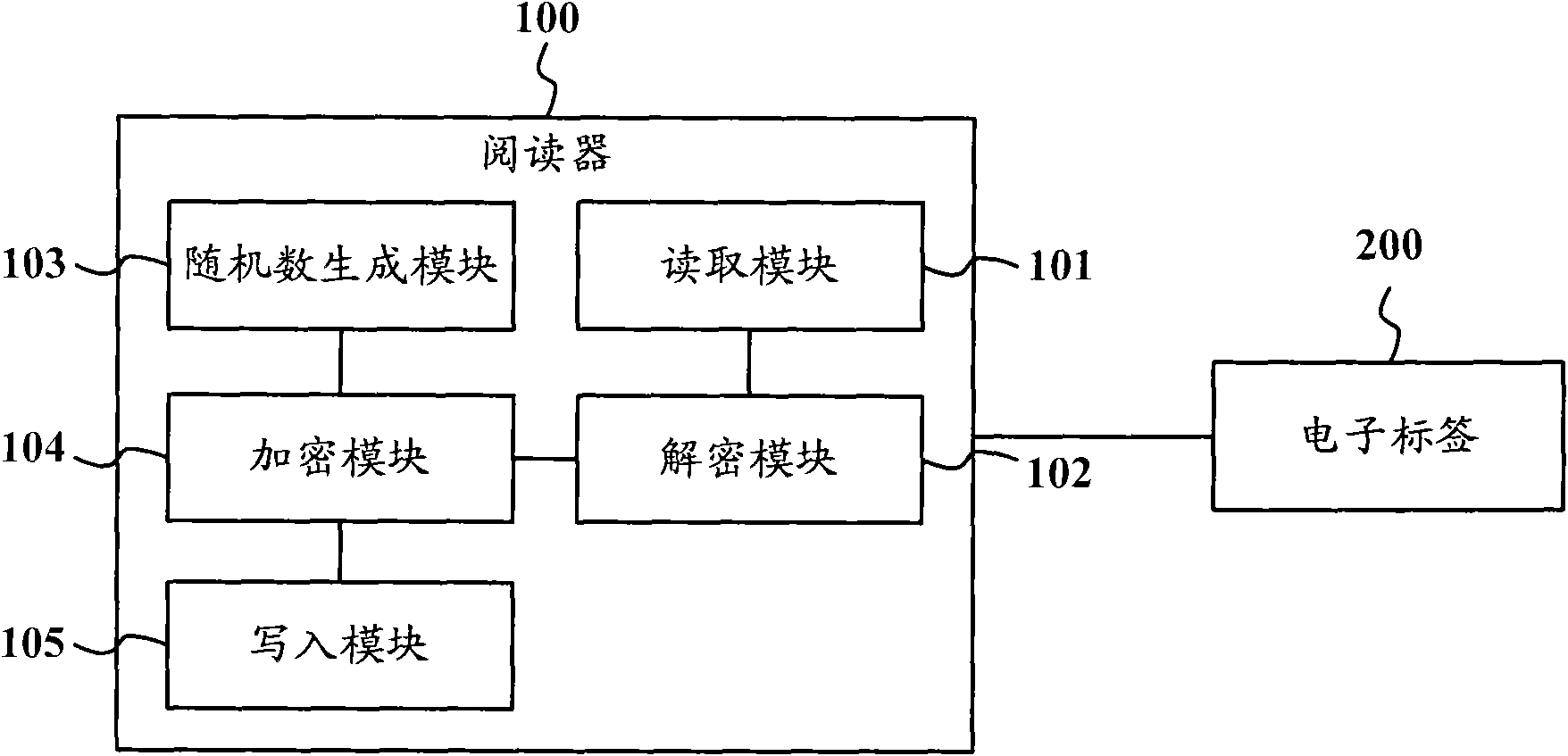
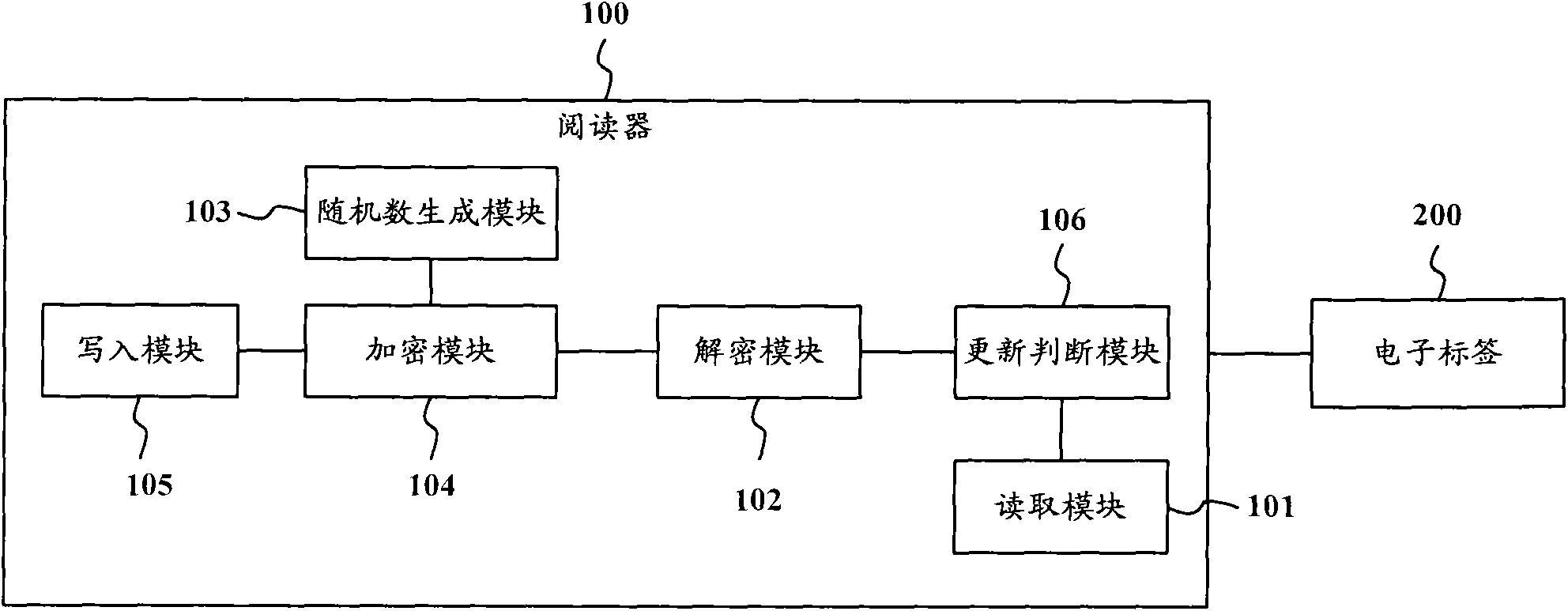
Radio frequency identification system, radio frequency identification method and reader
ActiveCN102063601AGuaranteed privacyGuaranteed exclusivitySensing record carriersRecord carriers used with machinesCiphertextRadio frequency
The invention provides a radio frequency identification system, a radio frequency identification method and a reader. The radio frequency identification system comprises an electronic tag and a reader, wherein the electronic tag is used for storing a first random number and a first cipher text datum which is obtained by ciphering a tag datum by using the first random number and a cipher of the radio frequency identification system, and the reader is used for reading the first random number and the first cipher text datum which are stored in the electronic tag, deciphering the first cipher text datum by suing the first random number and the cipher of the radio frequency identification system to obtain a tag datum, generating a second random number, ciphering the tag datum by using the second random number and the cipher of the radio frequency identification system to obtain a second cipher text datum, and writing the second random number and the second cipher text datum into the electronic tag. The invention can effectively guarantee the safety of the information of the electronic tag.
Owner:ZTE INTELLIGENT IOT TECH
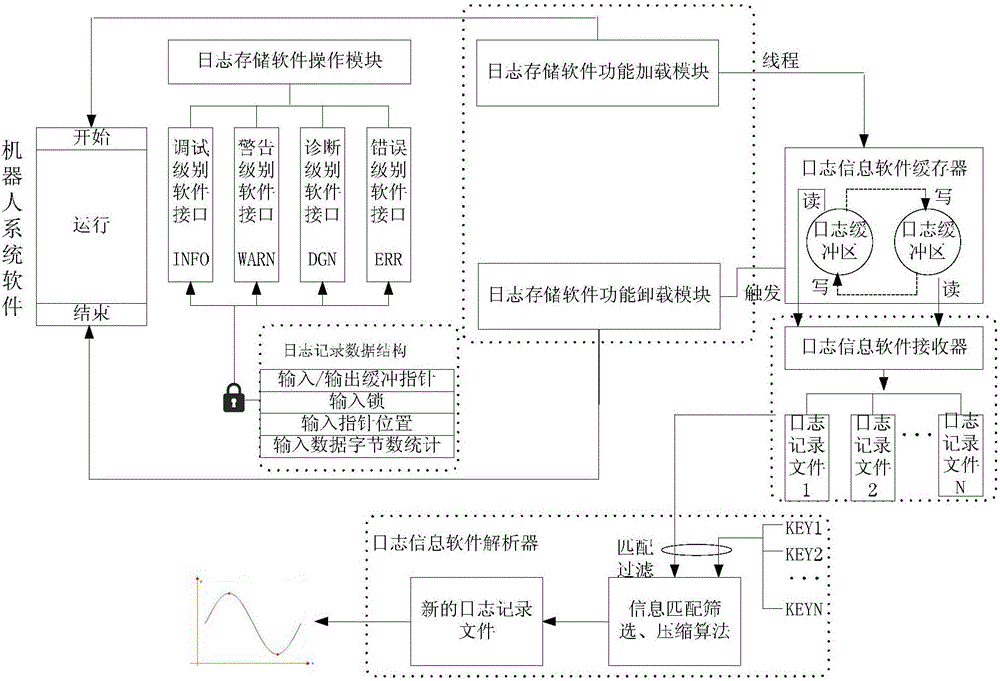
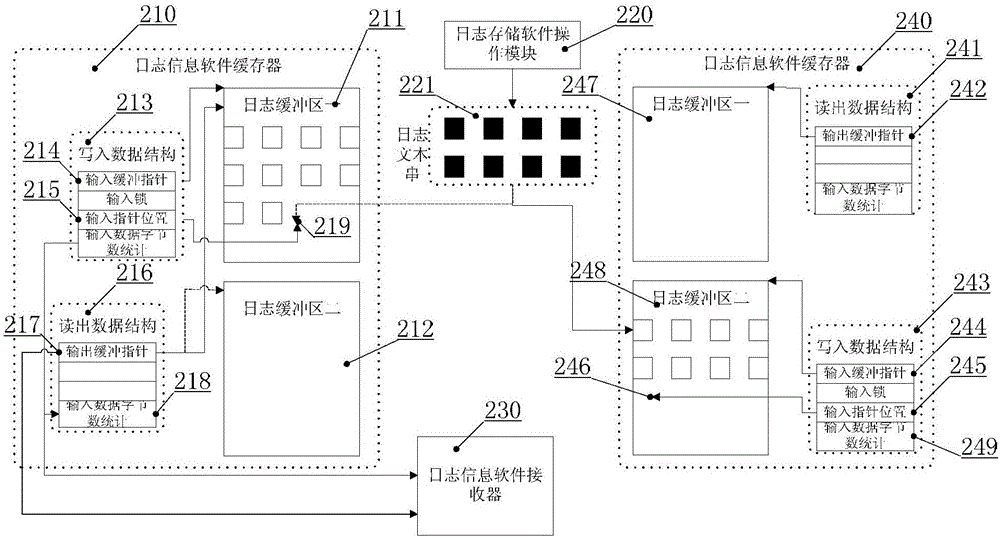
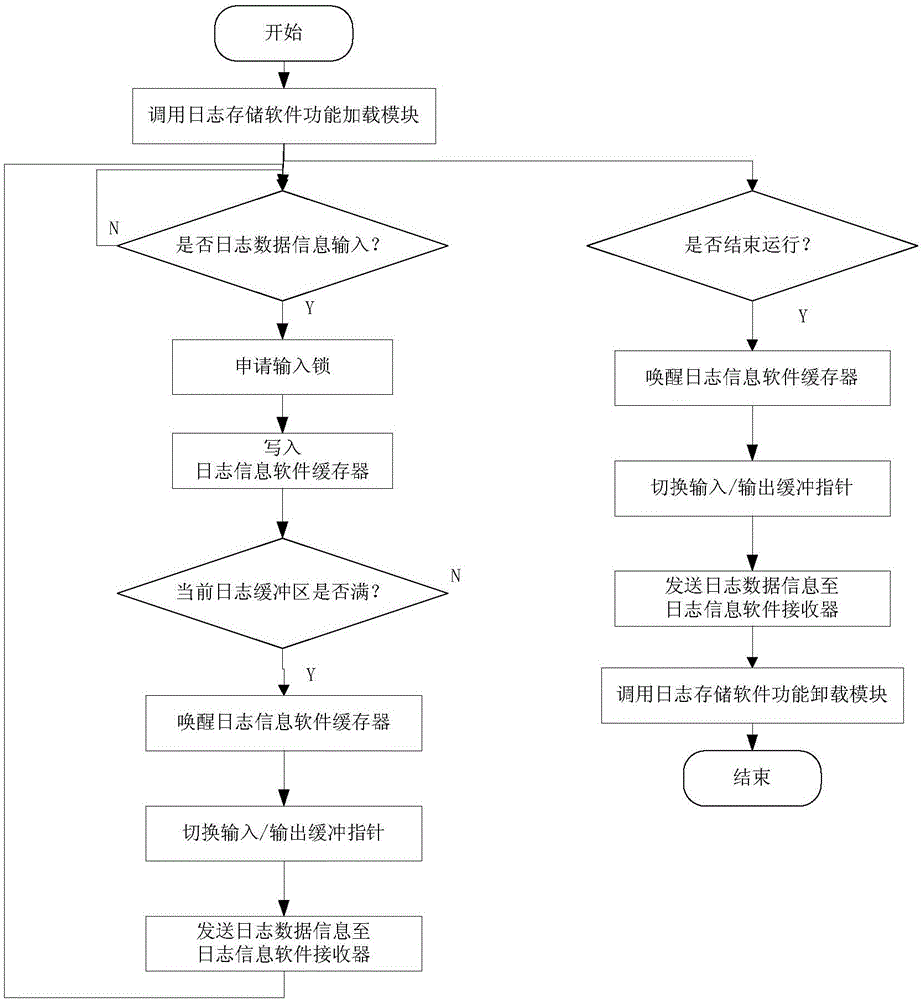
Double-buffering type robot software log storage method
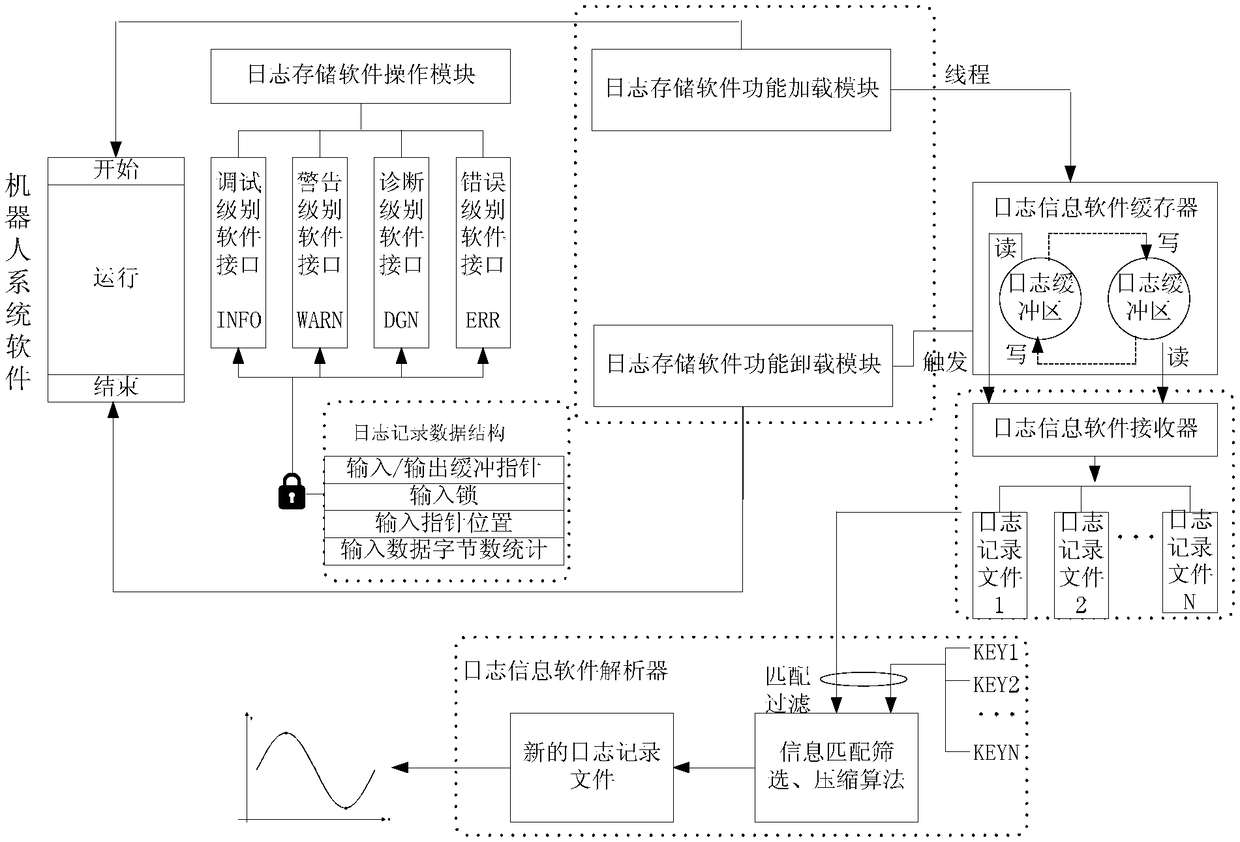
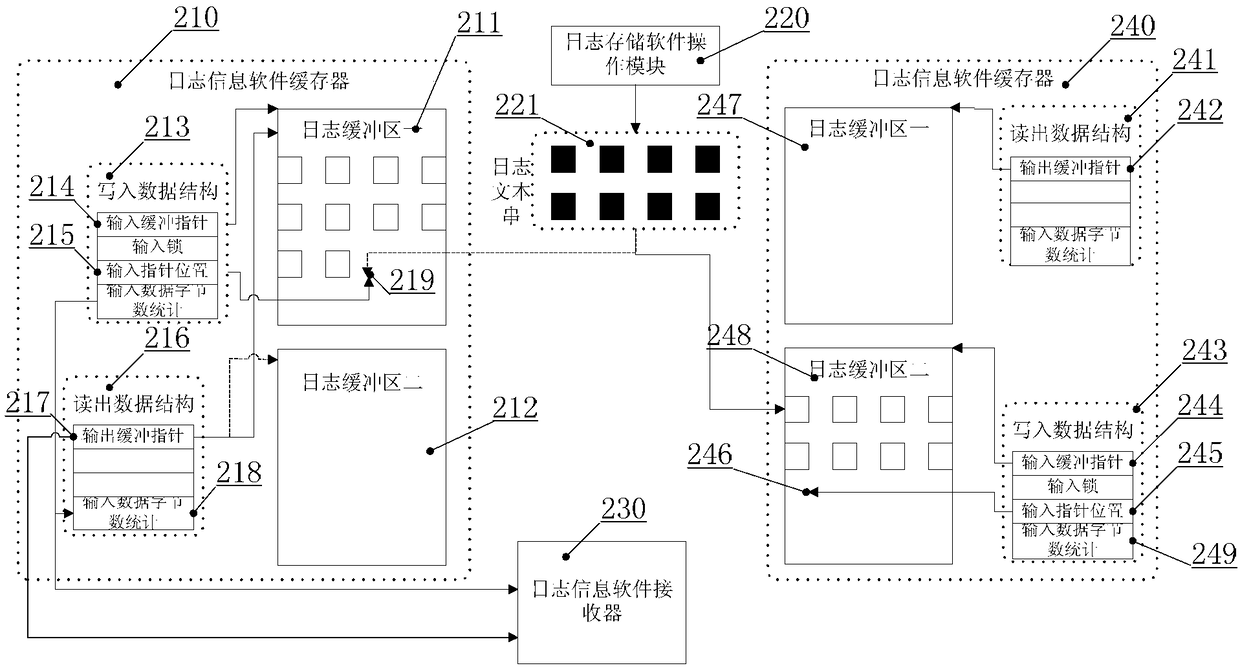
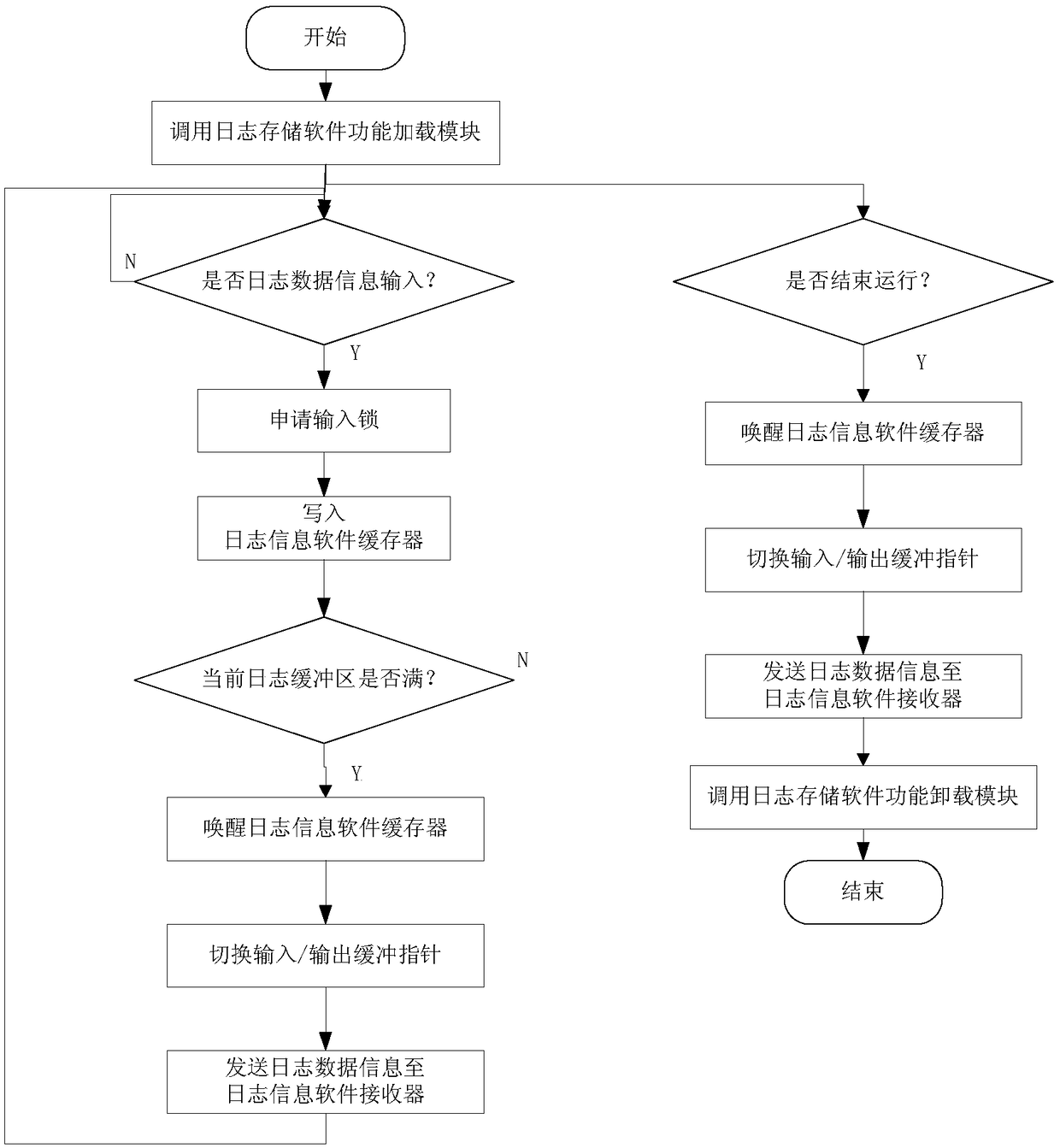
The invention provides a double-buffering type robot software log storage method. The method is characterized by comprising the following steps of: setting a log storage software function loading module, a log storage software function unloading module, a log storage software operation module, a log information software buffer, a log information software receiver and a log information software analyzer, wherein the log information software buffer comprises two log buffer areas with same storage spaces; when one log buffer area is full of data, switching an input pointer to the other log buffer area so as not to delay the data input; pointing an output pointer to the log buffer area full of data, outputting the log data information in the log buffer area full of data, and setting the log buffer area to be in an idle state. According to the method, the log data information can be stored, and the overall operation load of robot system software can be greatly reduced, so that benefit is brought to improve the software defect check efficiency.
Owner:FOSHAN INST OF INTELLIGENT EQUIP TECH +1
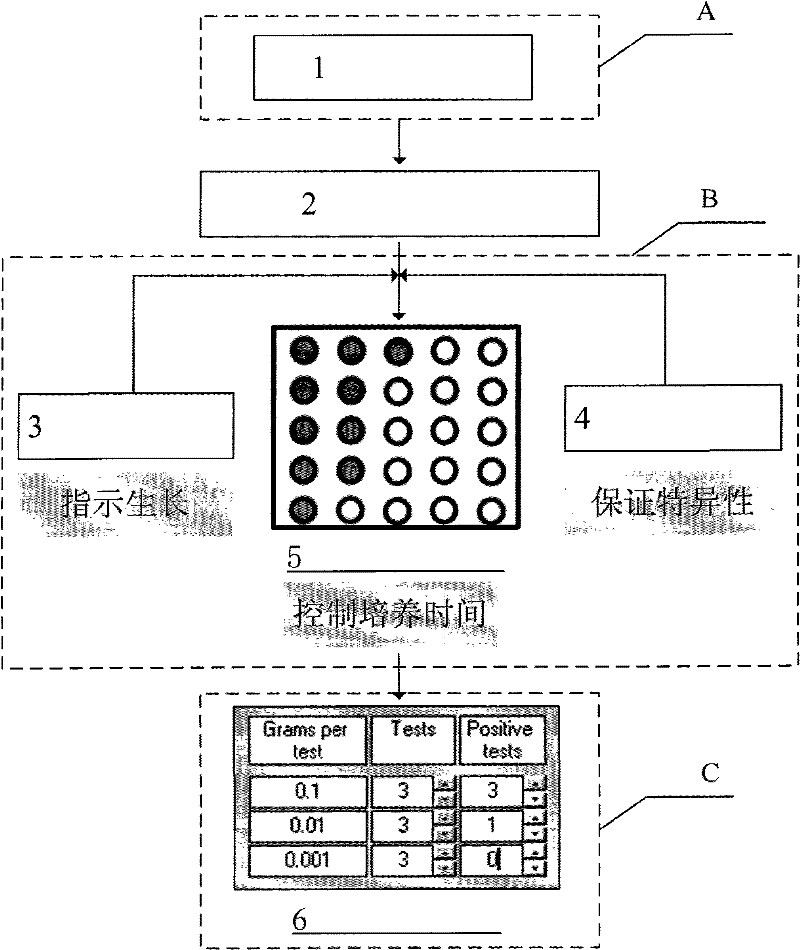
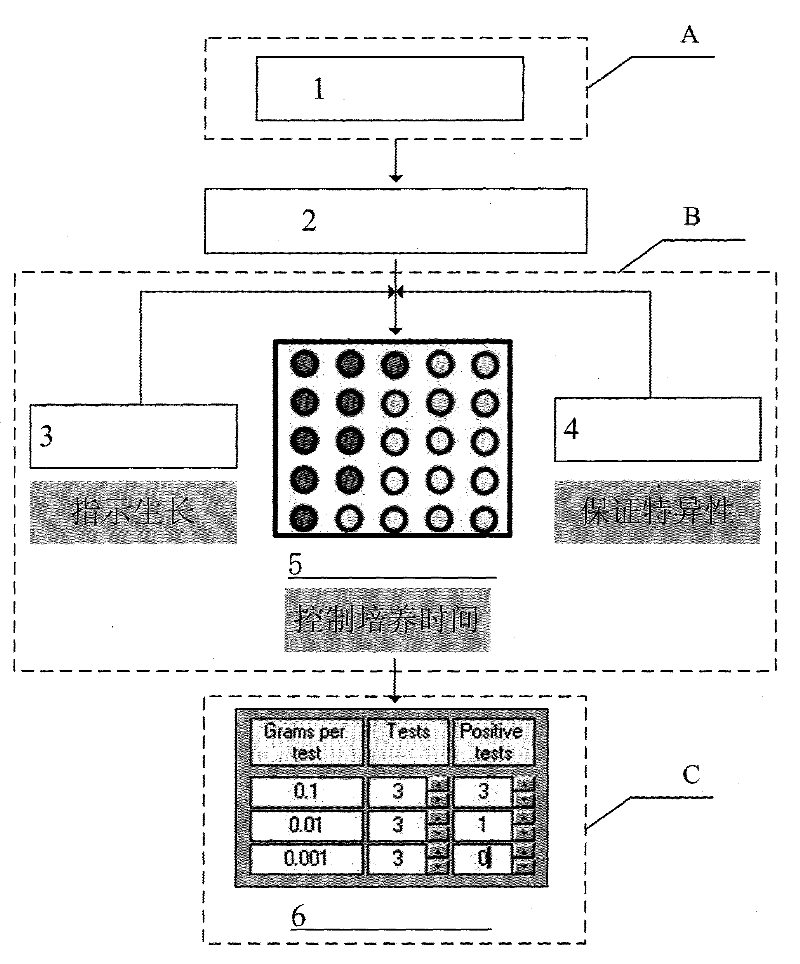
Detection method for obligate hydrocarbon oxidizing bacteria
ActiveCN102453746AEasy to operateShort training periodMicrobiological testing/measurementColor changesShort terms
The invention discloses a detection method for obligate hydrocarbon oxidizing bacteria, belonging to the technical field of microorganism detection methods. The detection method comprises the following steps of: suspending and diluting a soil sample with a basic culture medium; performing short-term culturing in combination with a selective culture carbon source and an oxidation reduction indicating dye for 3-5 days; and computing the quantity of obligate hydrocarbon oxidizing bacteria in the soil sample according to the color change of an airtight culture tube through a computer program. A detection technology for obligate hydrocarbon oxidizing bacteria disclosed by the invention has the advantages of simple operating process, economic efficiency, practicability, quickly-obtained result in a short period of time, high specificity, capability of effectively shielding the interference of other bacteria on counting and simple and accurate counting process, and is suitable for large-scale industrial exploration measurement with a large sample quantity.
Owner:CHINA PETROLEUM & CHEM CORP +1
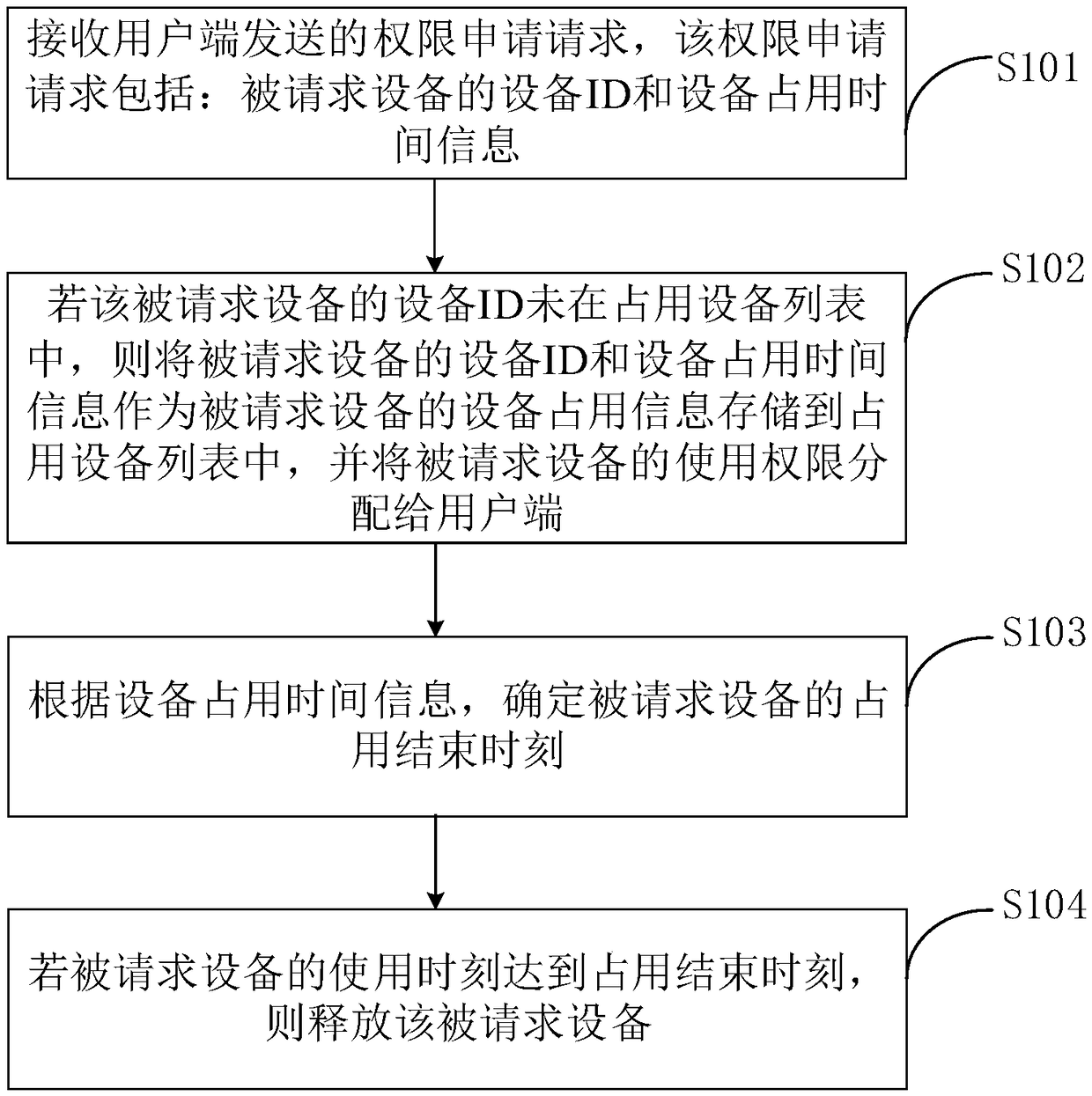
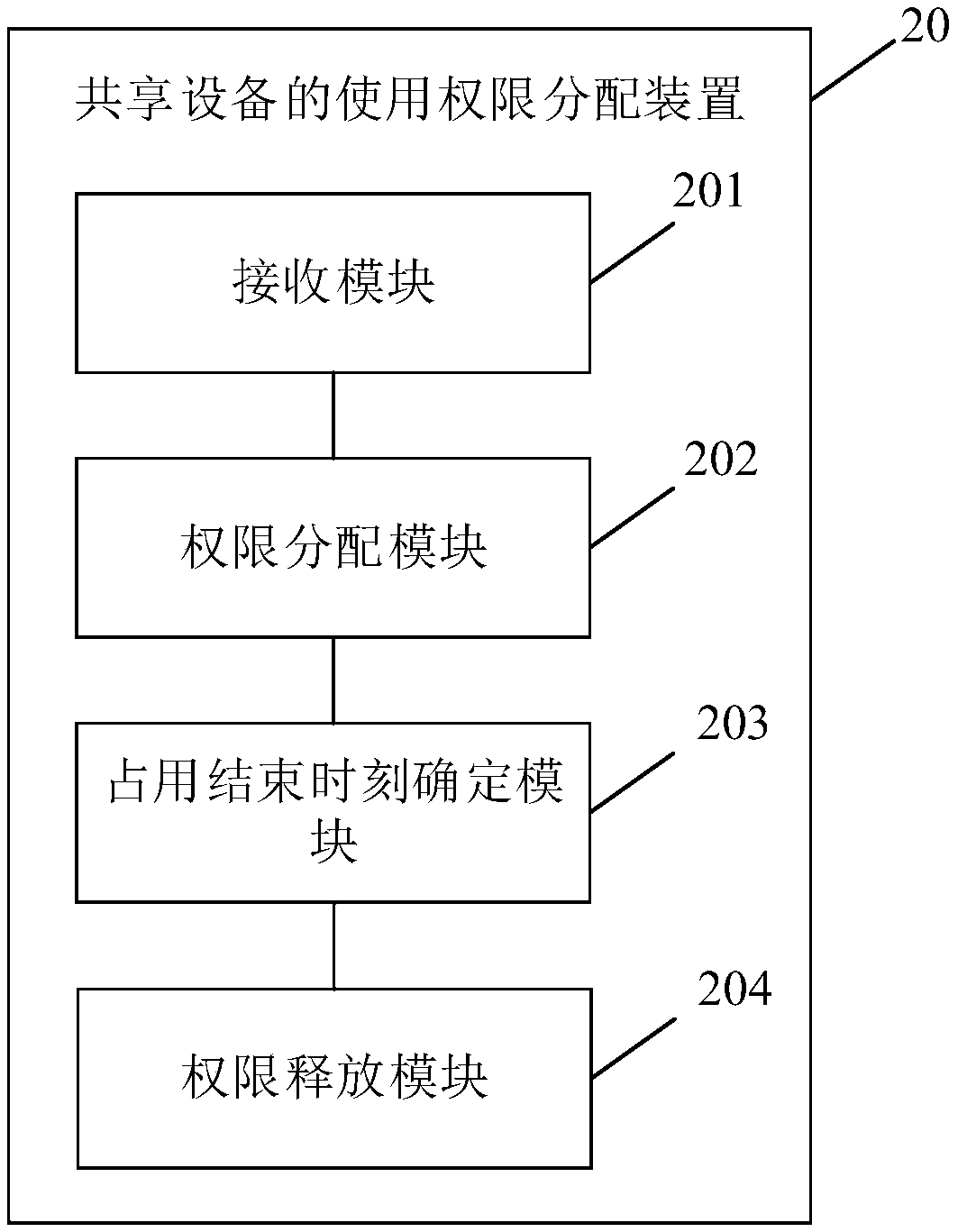
Method, device and electronic device for assigning use authority of shared equipment
InactiveCN109067748AGuaranteed exclusivityReasonable distributionData switching networksTime informationElectric equipment
Embodiments of the present application provide a method, an apparatus, and an electronic device for assigning usage rights to a shared device. The method comprises the following steps of: receiving aright application request sent by a user terminal; the right application request comprises: device ID of the requested device and device occupancy time information; if the device ID of the requested device is not in the occupied device list, storing the device ID and the device occupancy time information of the requested device in the occupied device list as the device occupancy information of therequested device, and assigning the use right of the requested device to the user terminal; determining an occupancy end time of the requested device according to the occupancy time information of the device; if the usage time of the requested device reaches the occupation end time, the requested device is released. Embodiments of the present application can reasonably allocate shared equipment resources according to the actual needs of users and ensure the exclusive right of users to the shared equipment.
Owner:BEIJING QIHOO TECH CO LTD
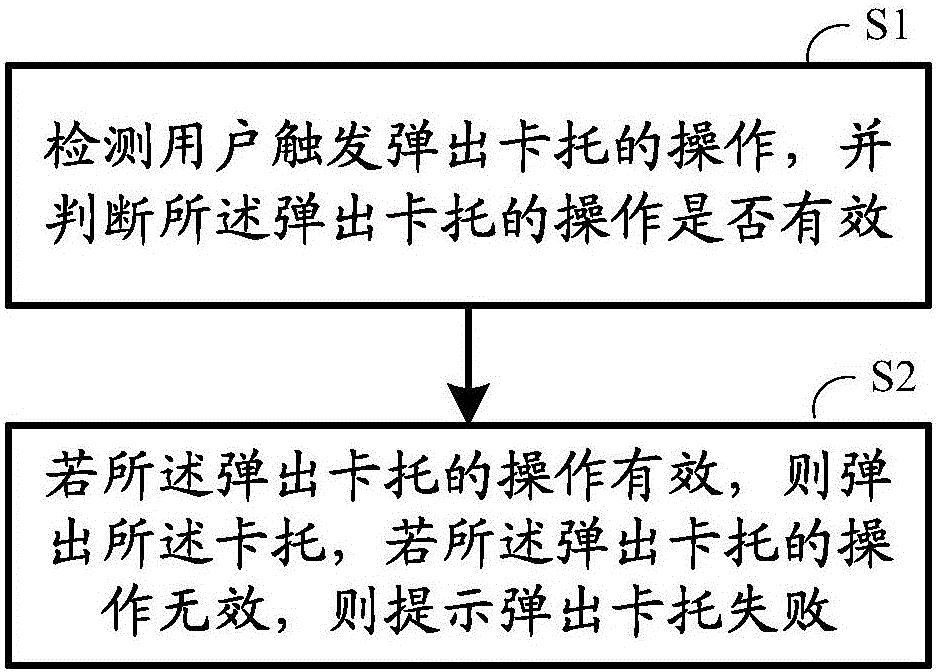
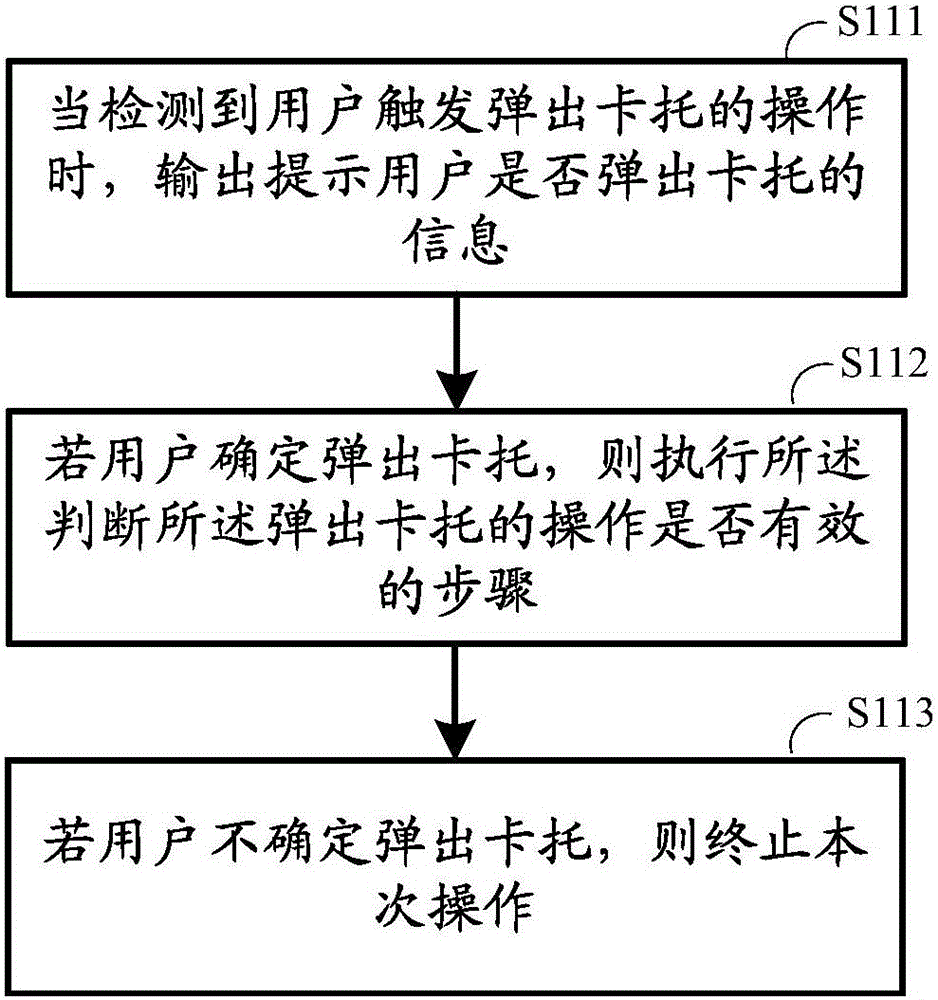
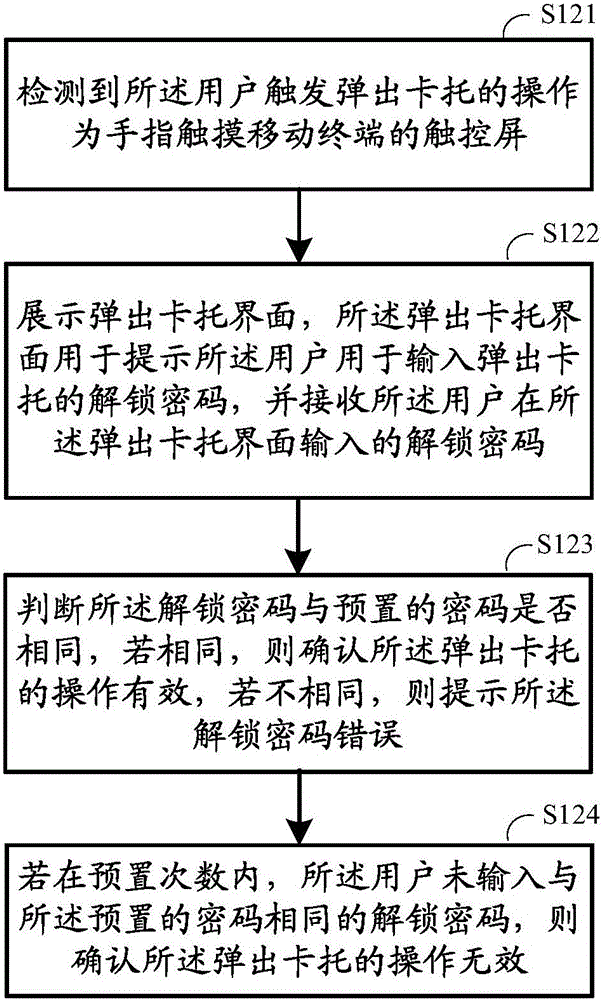
Method, apparatus, and system for moving in and out of card support
InactiveCN105915247AEasy to replaceGuaranteed aestheticsUser identity/authority verificationComputer terminalComputer science
The invention, which belongs to the technical field of a mobile terminal, discloses a method, apparatus, and system for moving in and out of a card support. The method comprises: an operation of trigging popping of a card support by a user is detected and whether the operation of popping of the card support is effective is determined; if so, the card support pops out; and if not, the failure of popping of the card support is prompted. According to the invention, because r the operation of trigging popping of the card support by the user is detected, a phenomenon that the card support can not pop out until a rear cover is opened or a card needle is used manually can be avoided, so that the card replacement becomes convenient; the integrated beauty and dustproof effect of the mobile terminal can be realized because of saving of opening the rear cover or a card needle hole. Besides, the operation of trigging popping of a card support is verified, so that the exclusive and secure properties of card support replacement are guaranteed.
Owner:LETV HLDG BEIJING CO LTD +1
Detection kit, primer and probe for simultaneously detecting and identifying classical swine fever, African swine fever and swine vesicular disease
InactiveCN106957926AGuaranteed FeaturesGuaranteed exclusivityMicrobiological testing/measurementDNA/RNA fragmentationSwine vesicular diseaseAfrican swine fever
The invention discloses a detection kit, a primer and a probe for simultaneously detecting and identifying classical swine fever, African swine fever and a swine vesicular disease. The primer and the probe are shown as a sequence table SEQ ID NO: 1 to SEQ ID NO: 16. The invention further discloses the one-step-method multi-fluorescent RT-PCR (Reverse Transcription-Polymerase Chain Reaction) detection kit which is rapid, accurate and convenient to use and can be used for simultaneously detecting and identifying the classical swine fever, the African swine fever and the swine vesicular disease. A detection method disclosed by the invention can be used for realizing one-time sampling and one-time analysis and can realize the aim of simultaneously detecting and distinguishing three important viruses, so that the working amount and cost of detection are reduced, the detection of epidemic diseases can be finished within shortest time and the time for preventing and controlling the diseases is earned.
Owner:BEIJING ENTRY EXIT INSPECTION & QUARANTINE BUREAU INSPECTION & QUARANTINE TECH CENT
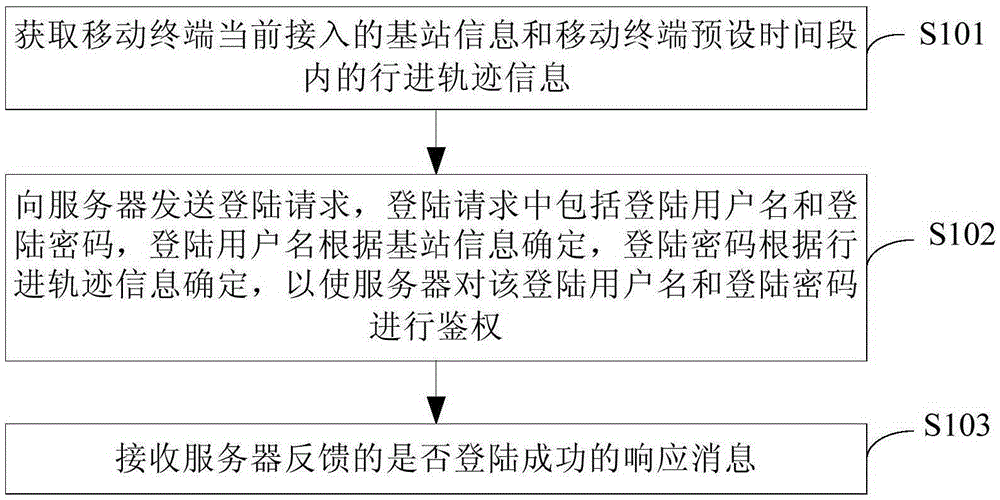
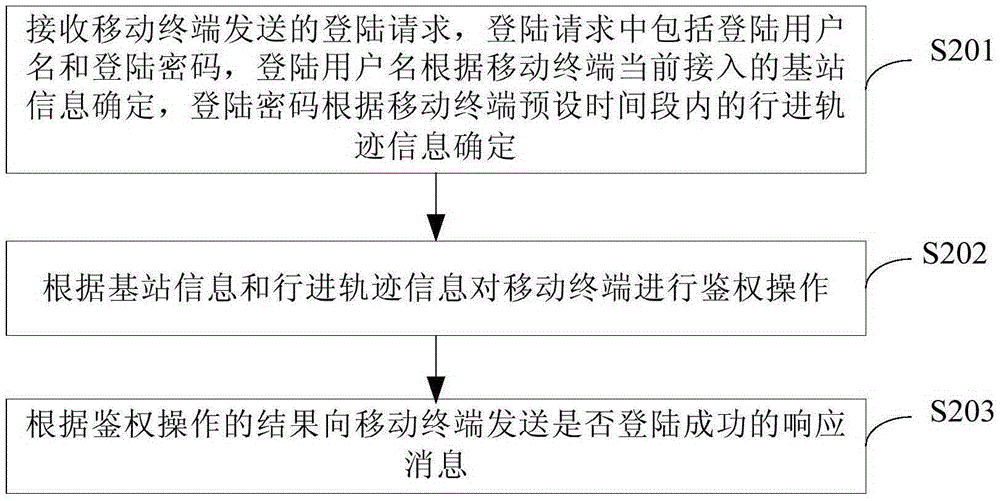
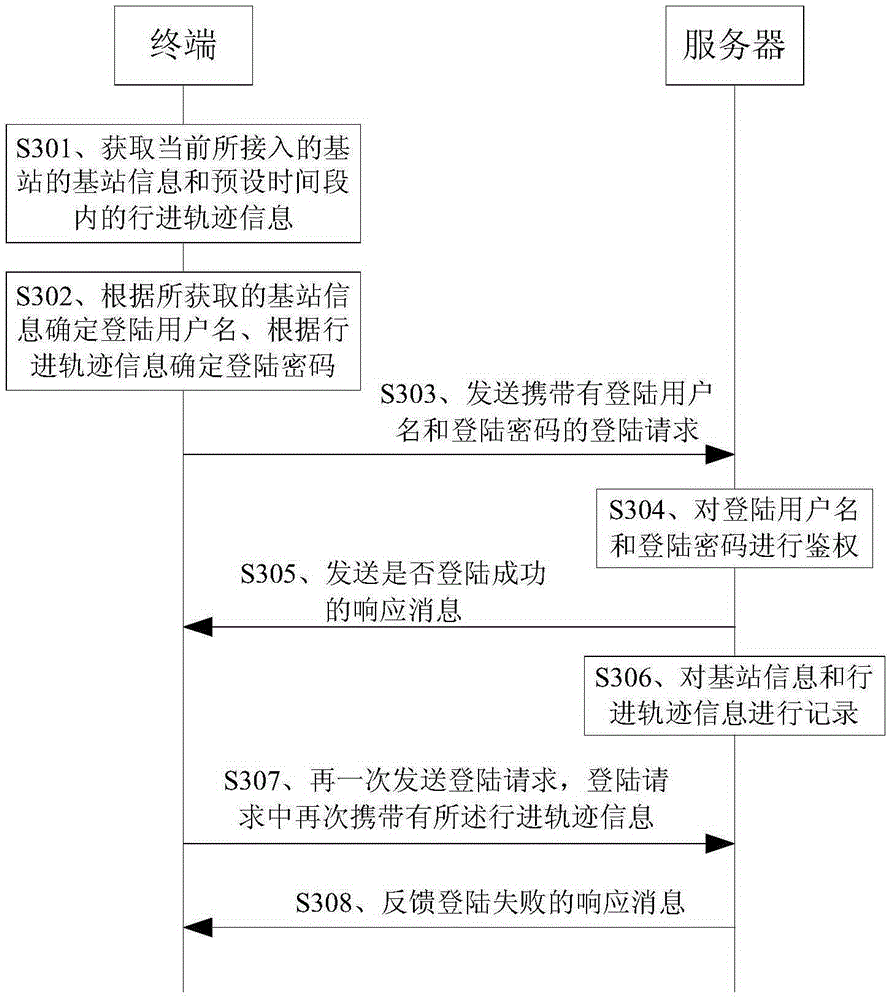
Server login method, terminal and server
InactiveCN105246042ARealize automatic loginEnsure safetyTransmissionLocation information based servicePasswordComputer terminal
The invention provides a server login method, a terminal and a server. The method comprises the steps that the information of a base station and the traveling trajectory information in a terminal preset period of time are acquired, wherein a mobile terminal currently accesses the base station; a login request is sent to the server, wherein the login request comprises a login user name which is determined according to the base station information and a login password which is determined according to the traveling trajectory information; the server authenticates the user name and the password; and a response message fed back by the server is received, wherein the response message is about whether login is successful. Due to the fact that the user name and the password are generated by the terminal in real time, the user name and the password are effective and unique in real time. After the server successfully authenticates the user name and the password, the terminal can successfully access the server. Automatic login of the server is realized. Input workload in a login process is reduced. Information leakage is avoided. Safe login of the server is ensured.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
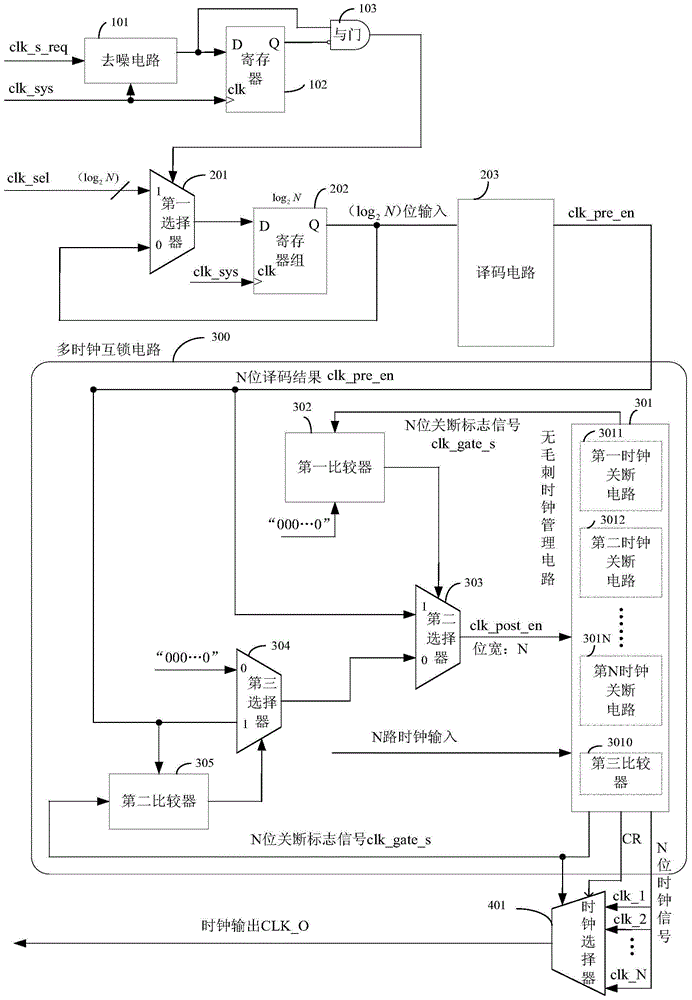
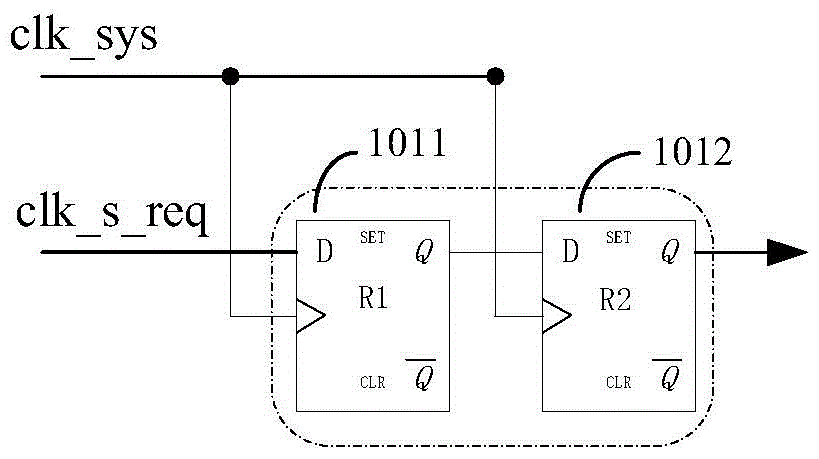
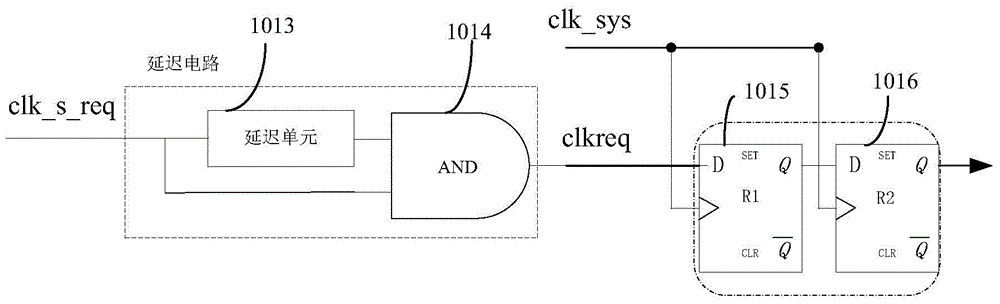
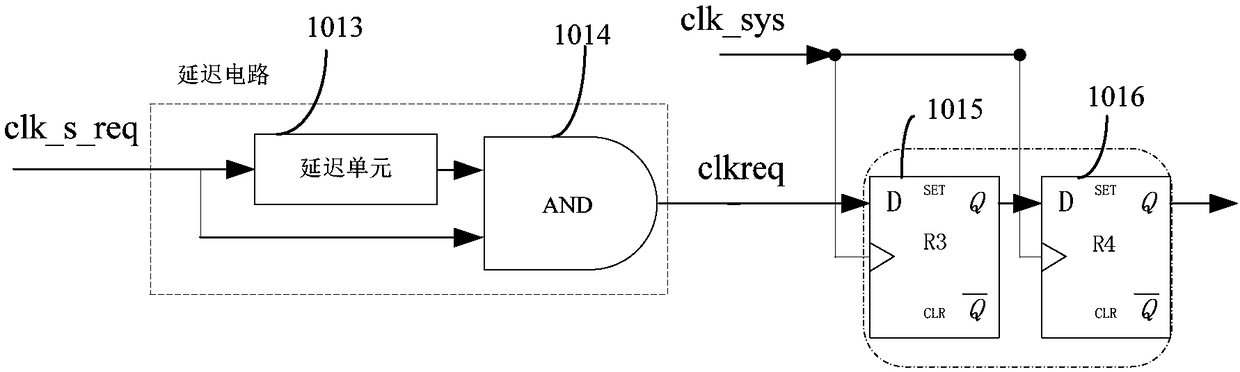
Burr-free switching circuit for supporting multi-way clock
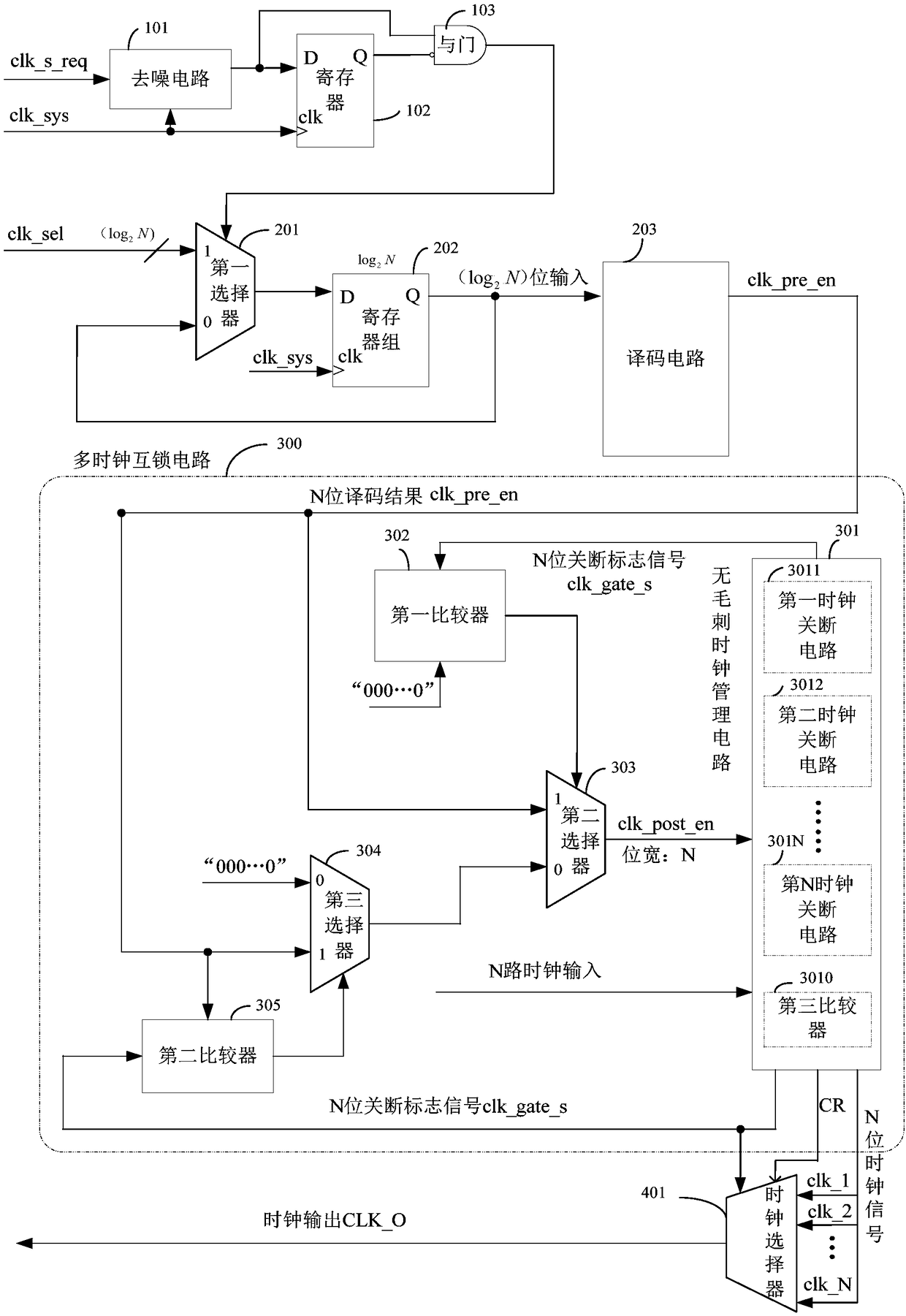
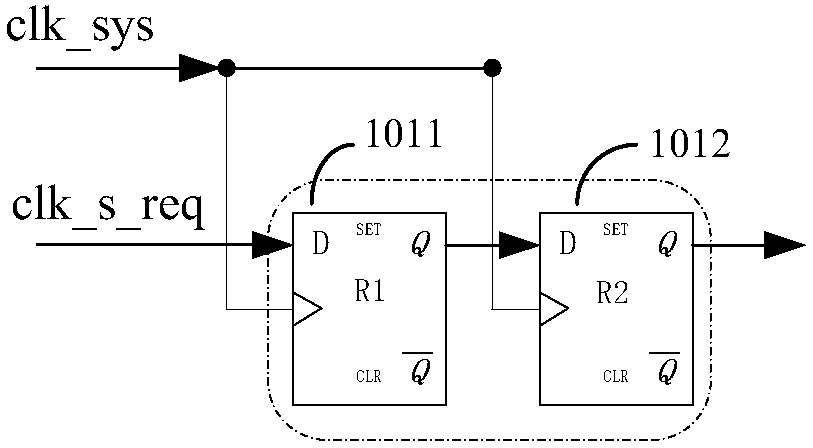
ActiveCN105680830AGuaranteed uniqueness and exclusivityStrong flexibilityPulse manipulationVIT signalsWork pattern
The invention provides a burr-free switching circuit for supporting a multi-way clock. The burr-free switching circuit comprises a register, an AND gate, a first selector, a register group, a decoding circuit, a multi-clock interlock circuit and a clock selector; the decoding circuit realizes decoding of a one-hot encoding mode on a clock selection signal, and a log2N bit clock selection signal is translated into a decoding result of N bit one-hot encoding, so that the uniqueness and excludability of an effective clock enable signal can be guaranteed; meanwhile, the multi-clock interlock circuit processes the decoding result according to the currently outputted clock enable; if the currently outputted clock enable is not equal to the decoding result, then all clock enables are firstly closed, and then the decoding result is used as a new clock enable signal to open corresponding clocks, so that burr-free switching of a clock signal can be realized. The burr-free switching circuit for supporting the multi-way clock provided by the invention can realize burr-free switching of N paths of input clocks, support random switching orders, and provide greater flexibility for a work pattern of the whole circuit.
Owner:NO 771 INST OF NO 9 RES INST CHINA AEROSPACE SCI & TECH
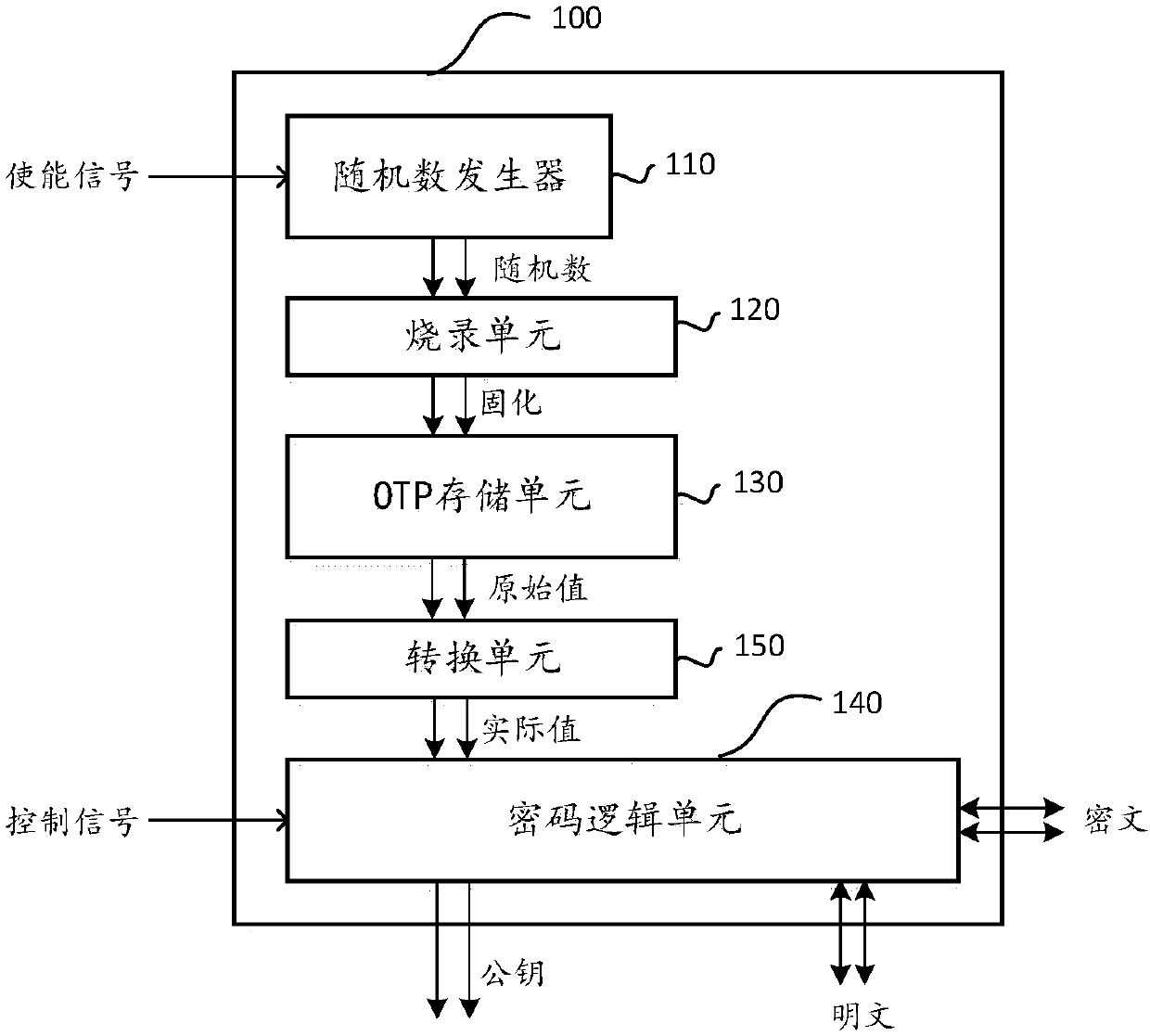
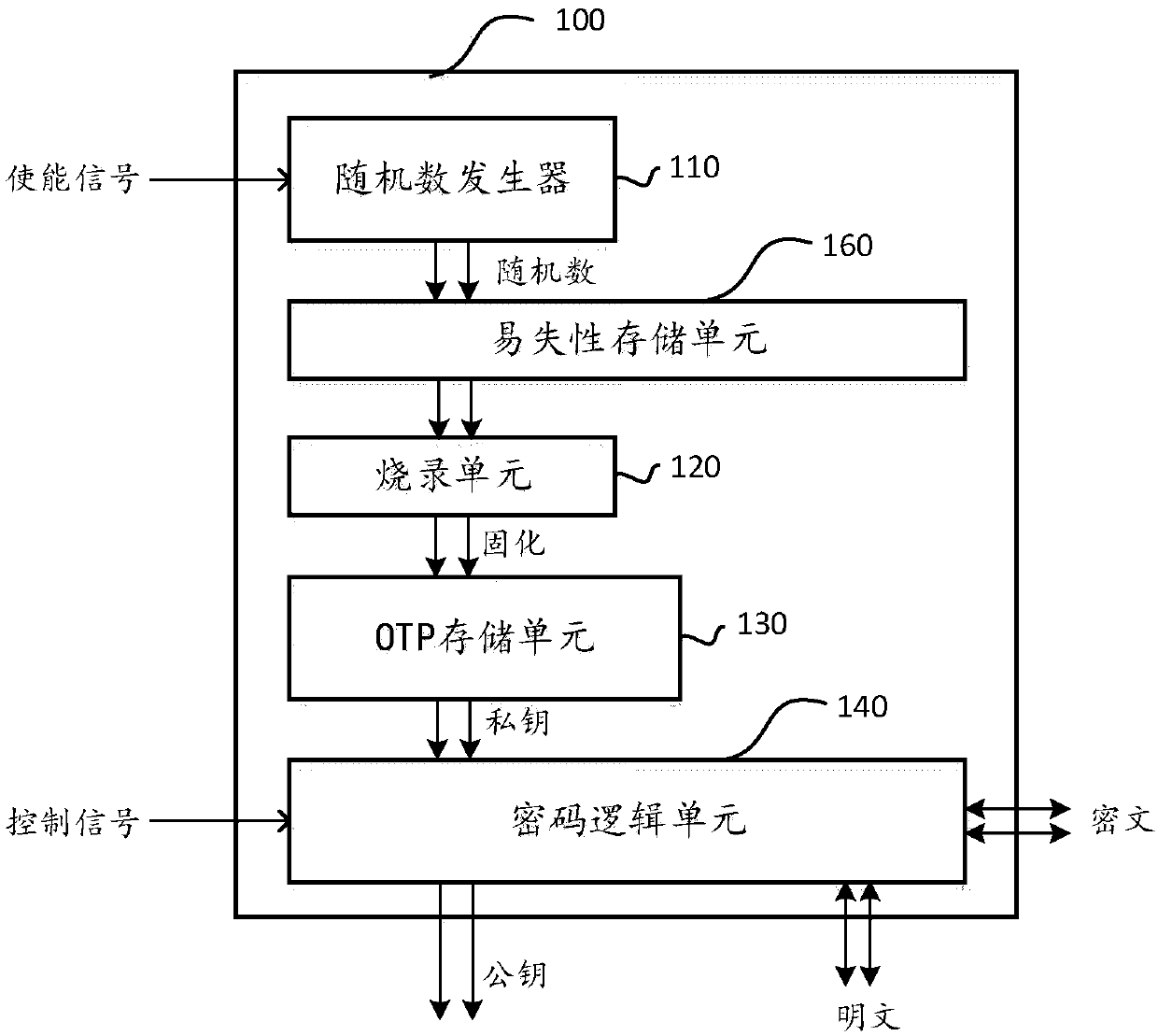
A key generation component for use within a physical chip
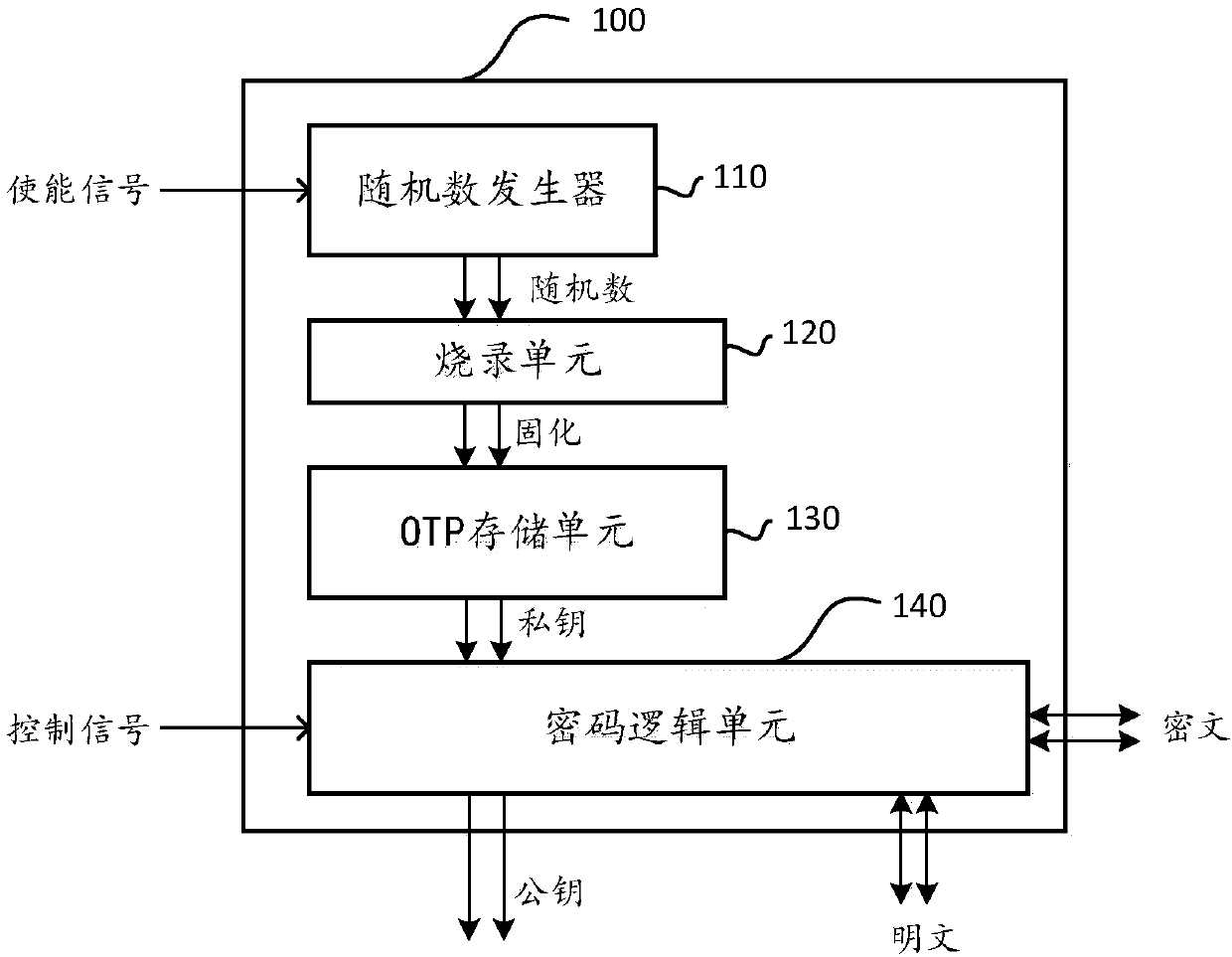
InactiveCN109842488AGuaranteed exclusivityEnsure safetyKey distribution for secure communicationBurn unitsComputer module
The invention provides a key generation assembly used in a physical chip, and the key generation assembly comprises a random number generator which is used for responding to a first signal so as to generate an unpredictable coding value; a burning unit which is used for executing the operation of burning the coded value into the OTP storage unit; and an OTP storage unit is used for solidifying thecoded value to serve as a private key. According to the invention, the private key in the key generation assembly is generated by the unpredictable random number in the chip; According to the invention, the private key value does not have any relation and interaction with the outside of the chip after being burnt into the OTP module, the uniqueness and undetectability of the private key are ensured, and the private key cannot be known no matter whether the component is externally provided with a development designer or an attacker, so that the security and reliability of the private key are ensured.
Owner:ANTAIOS (BEIJING) INFORMATION TECH
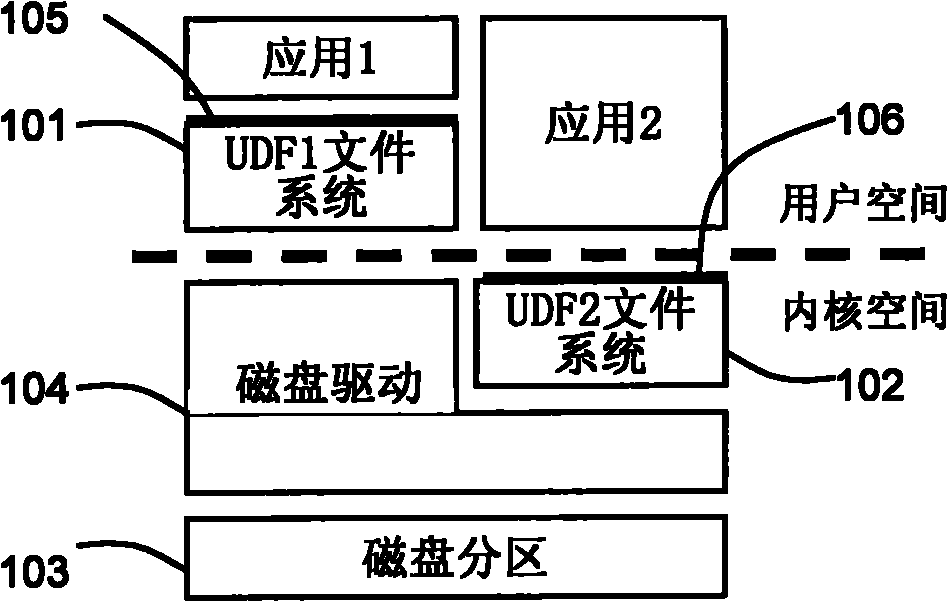
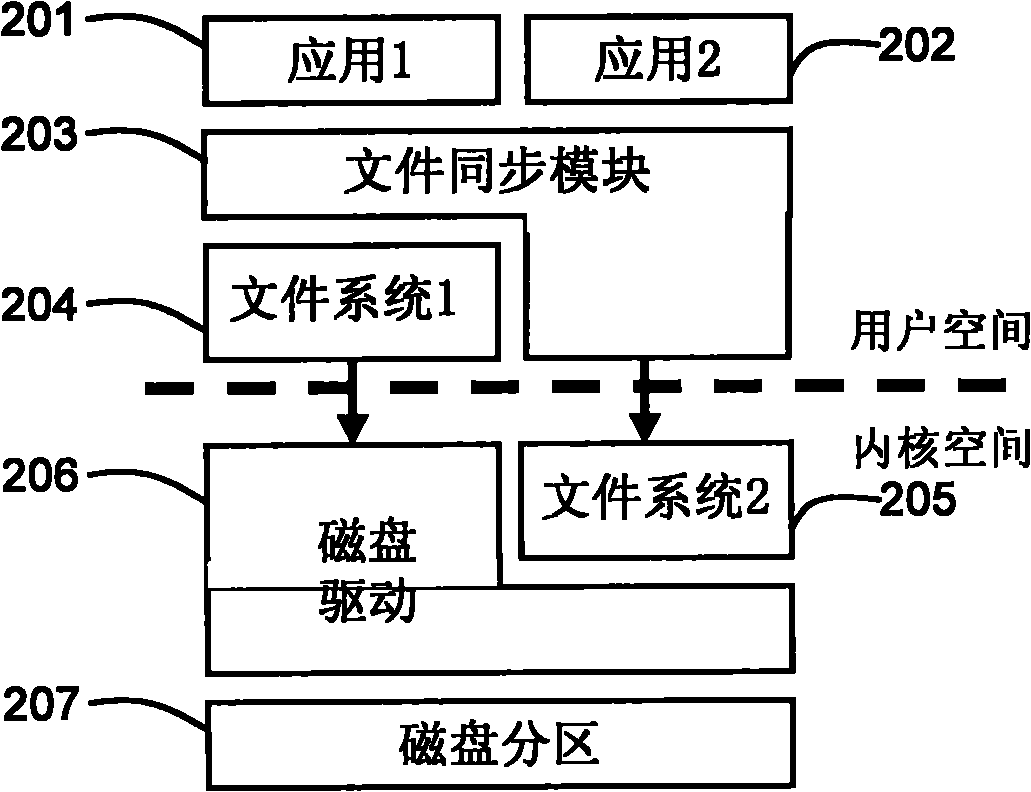
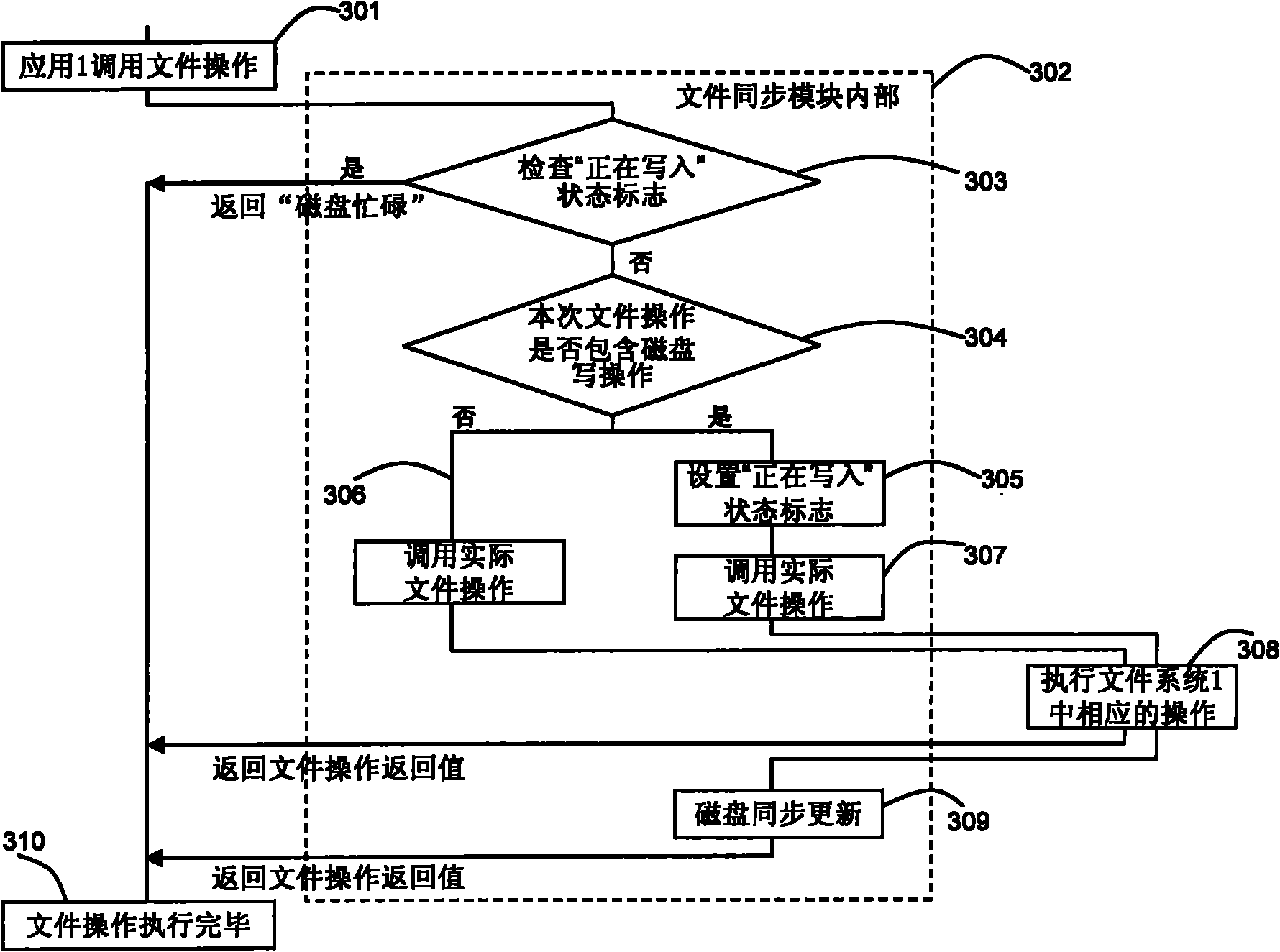
Device and method for regulating interface access of plurality of file systems on same disk partition
InactiveCN102419757AResolve data conflictsGuaranteed exclusivitySpecial data processing applicationsFile systemData contention
The invention provides a device and a method for regulating interface access of a plurality of file systems on the same disk partition. A plurality of file systems comprise a first file system and at least one second file system, wherein the first file system is a file system positioned on a kernel layer; and the second file system is a file system positioned on a user layer. The regulating device is provided with a synchronization module for coordinating the operation of each file system on the disk partition. When any one of the file systems is used, the following operations of a detection step, an allowance step, a protection step and a synchronization step are carried out by the synchronization module. The invention effectively solves the problem of data contention which is possibly generated when a plurality of file systems simultaneously work.
Owner:HITACHI LTD
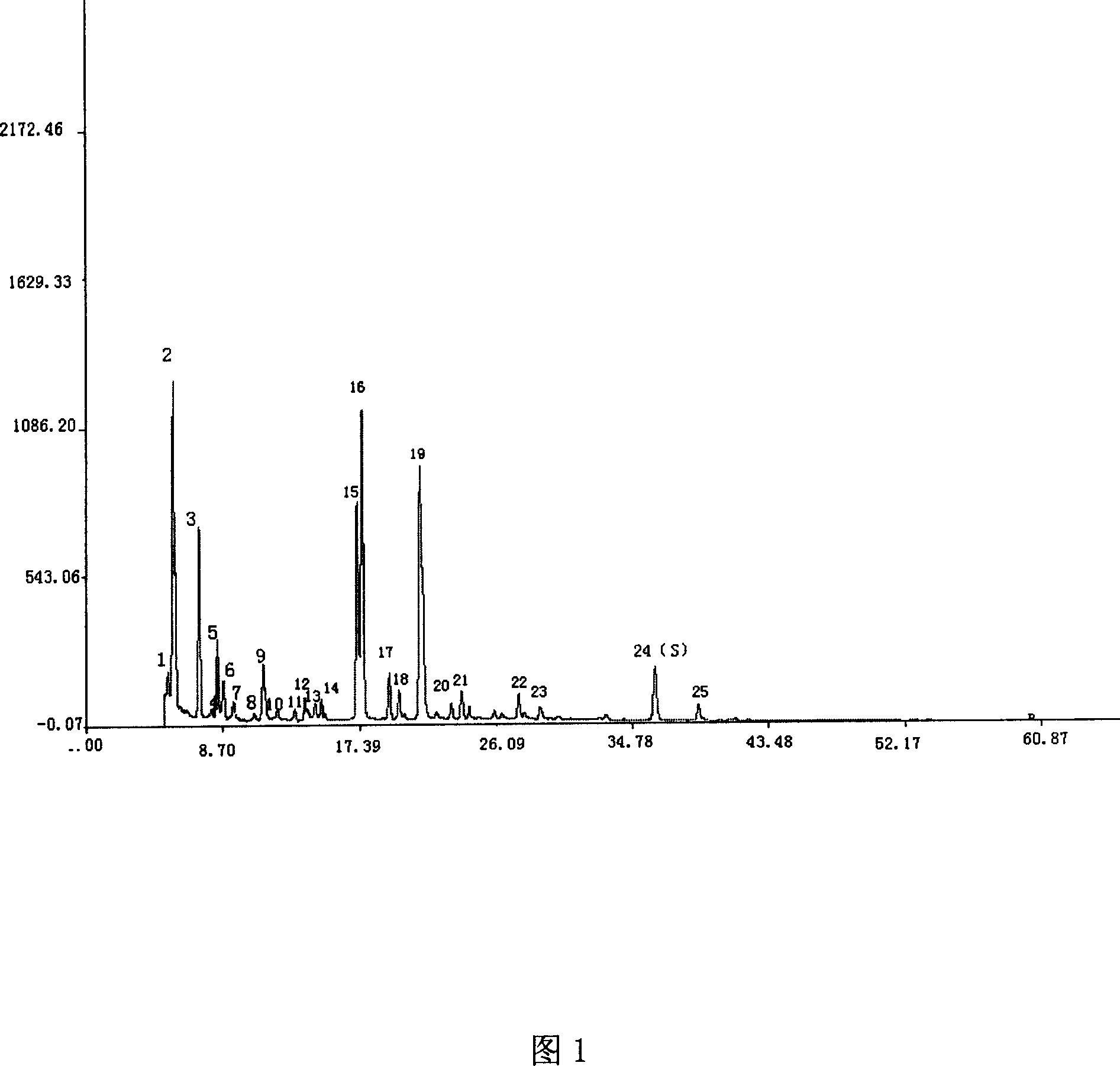
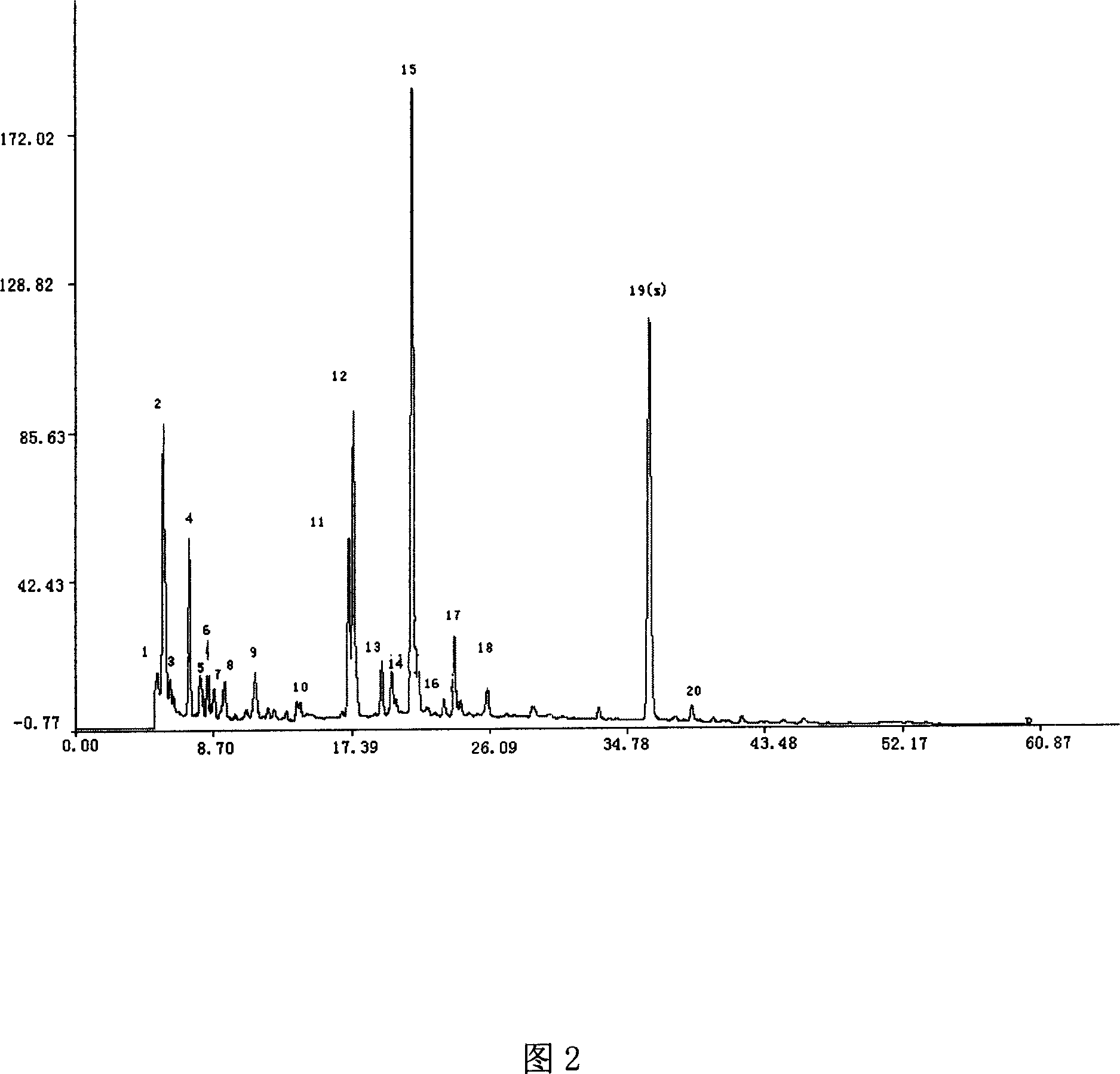
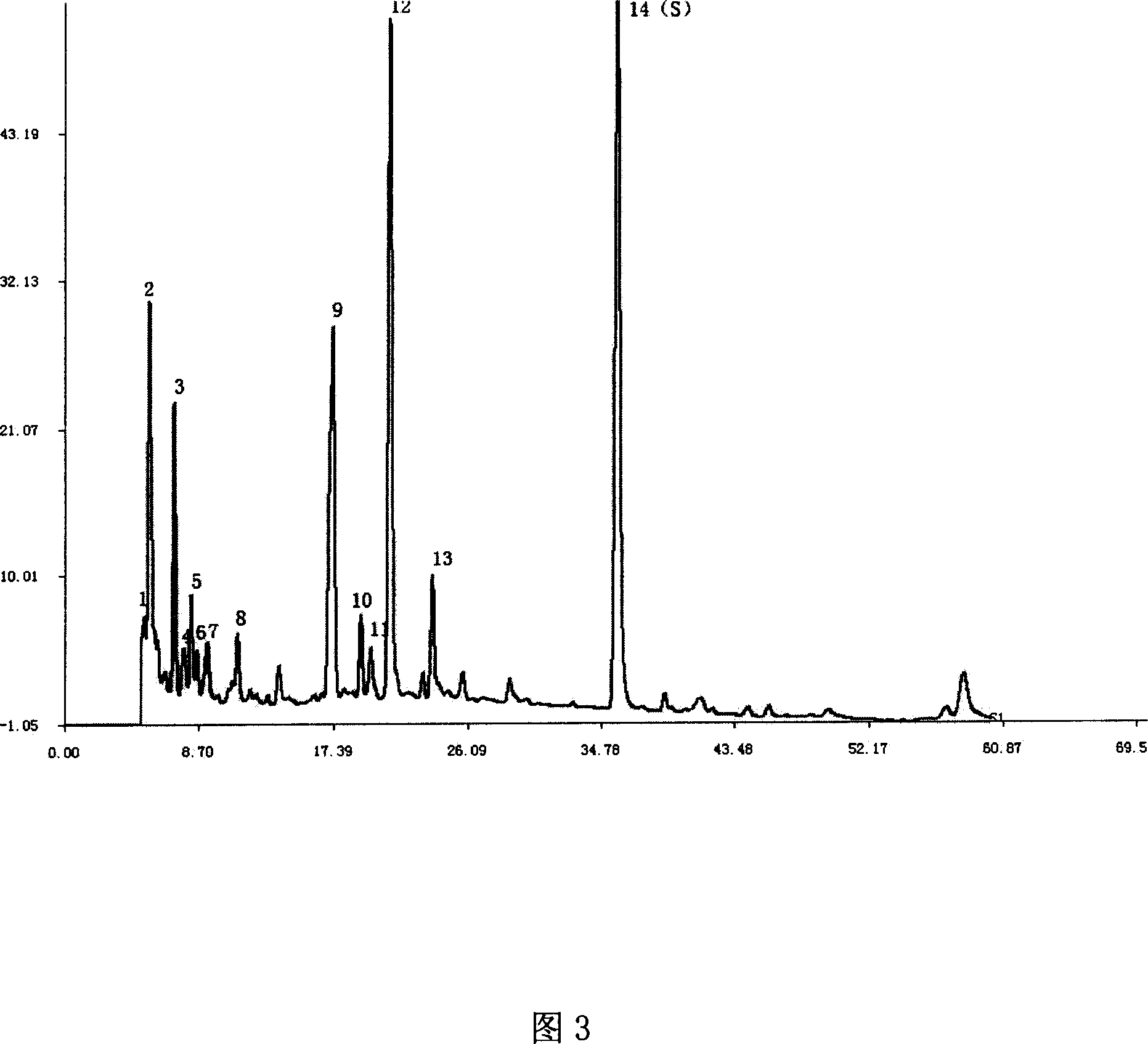
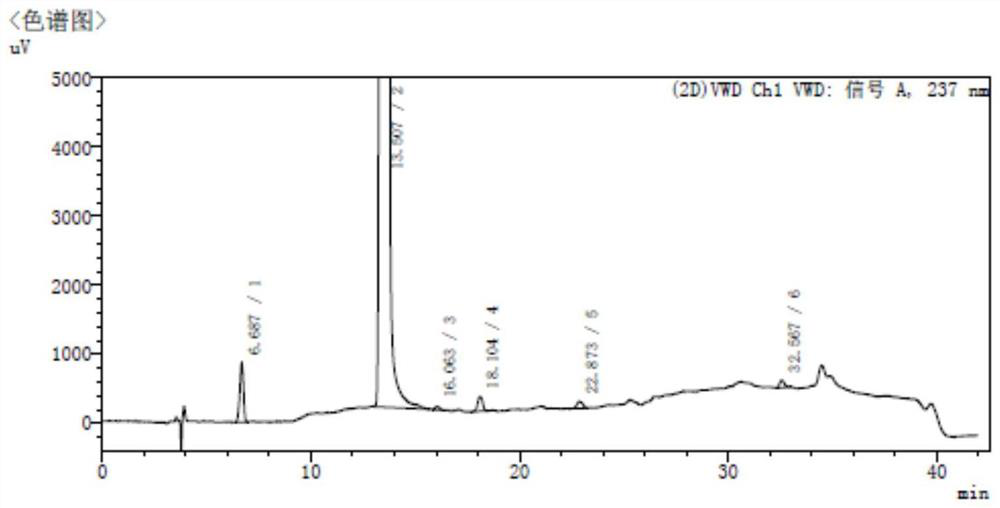
Single herb medicine, intermediate and its injection liquid finger-print atlas quality testing method
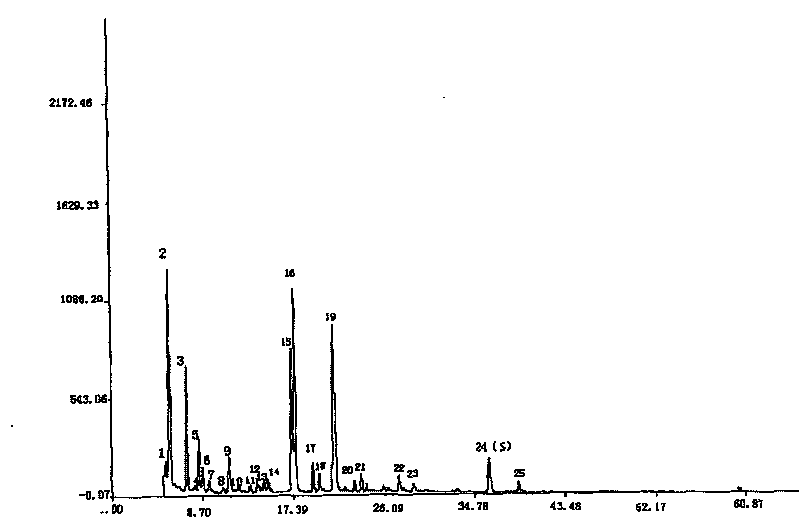
InactiveCN1947740ATrue Fingerprint FeaturesGood correlationComponent separationPlant ingredientsHerb medicineSilica gel
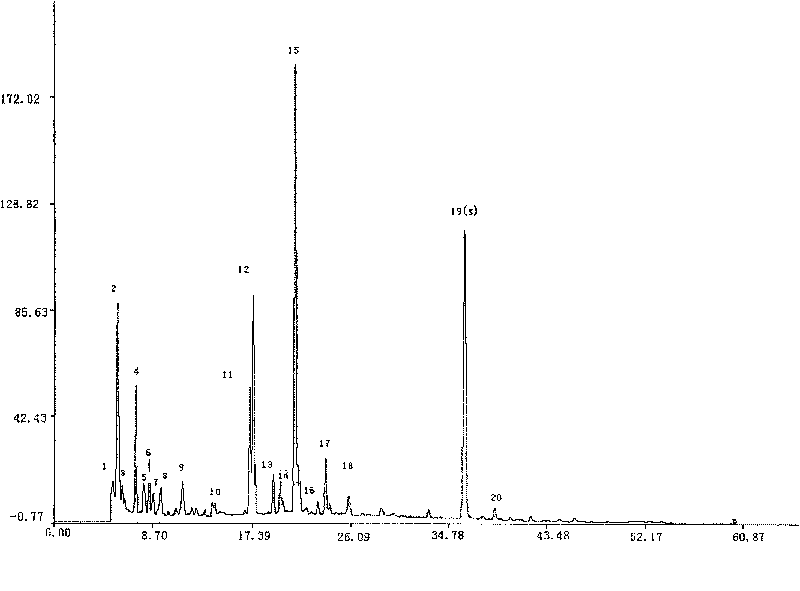
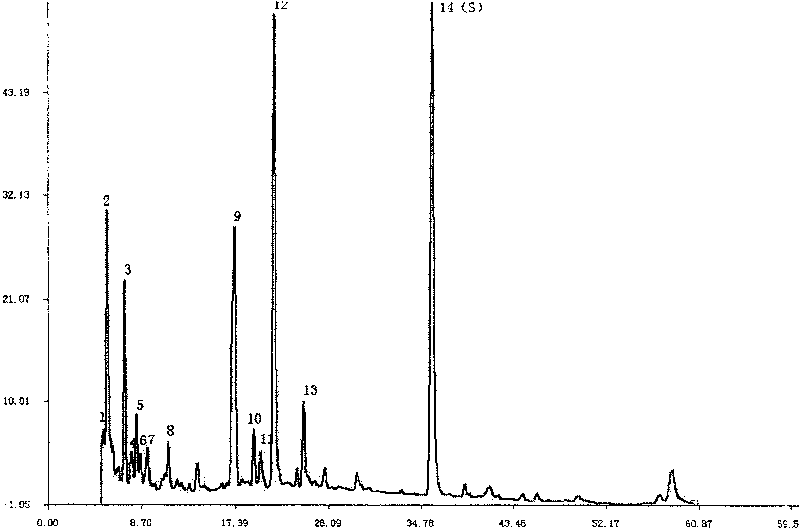
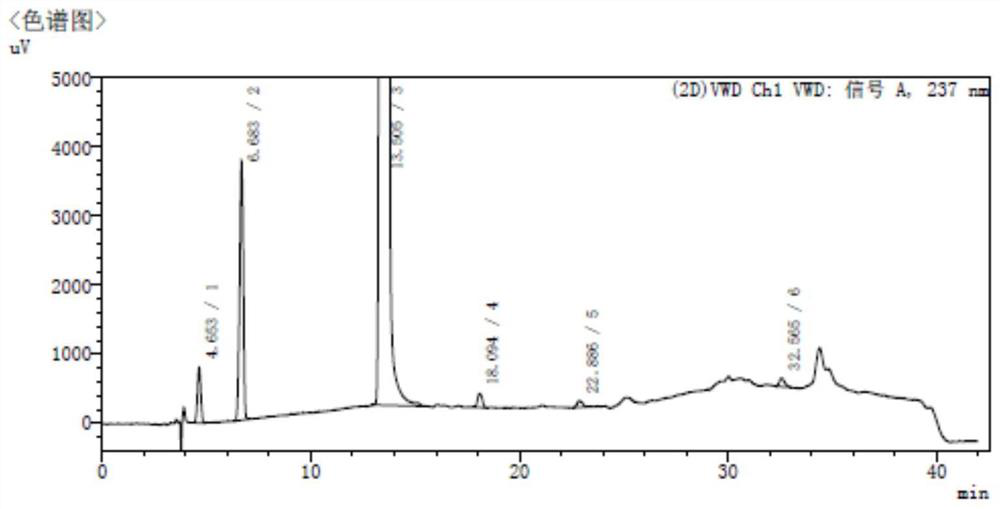
A fingerprint method for testing the quality of common lamiophlomis, its intermediate and its injection includes such steps as preparing the reference solution from quercetin, preparing three solutions of common lamiophlomis, its intermediate and its injection, filling the reference solution and one solution to be tested into liquid-phase chromatograph, and testing the similarity between their fingerprints, which must be greater than 0.90.
Owner:SICHUAN HENGKANG DEV
Mobile power supply charging device
PendingCN107147186ANot easy to shiftEnsure safetyBatteries circuit arrangementsElectric powerGear driveGear wheel
Owner:DONGGUAN CHANGJINCHENG ELECTRIC APPLIANCE CO LTD
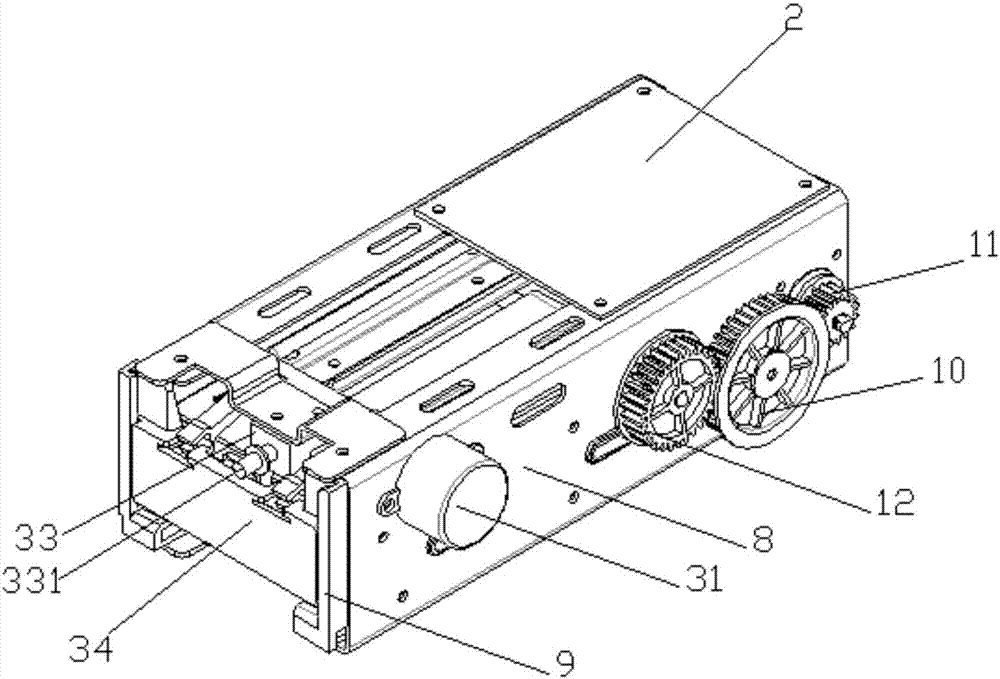
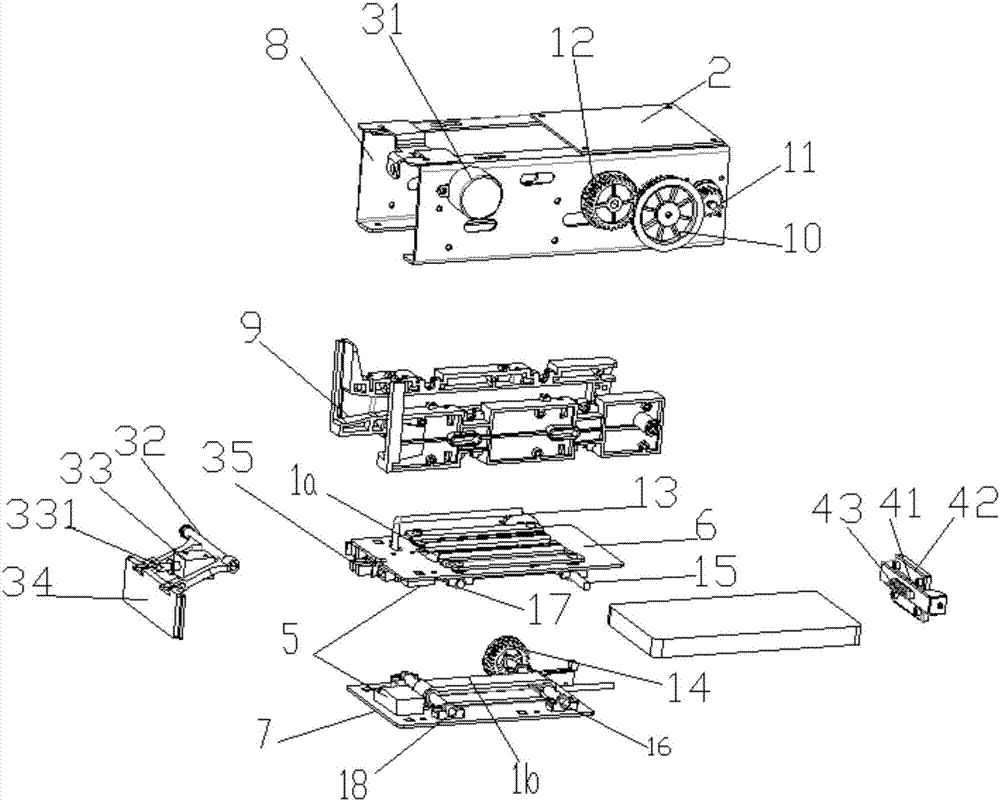
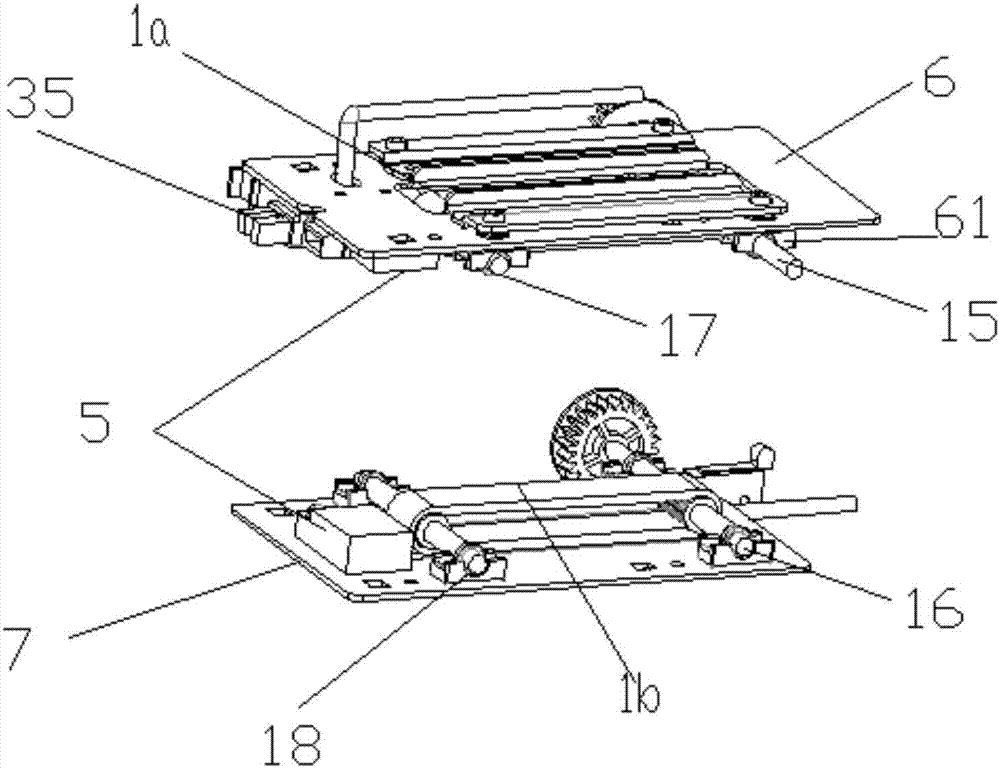
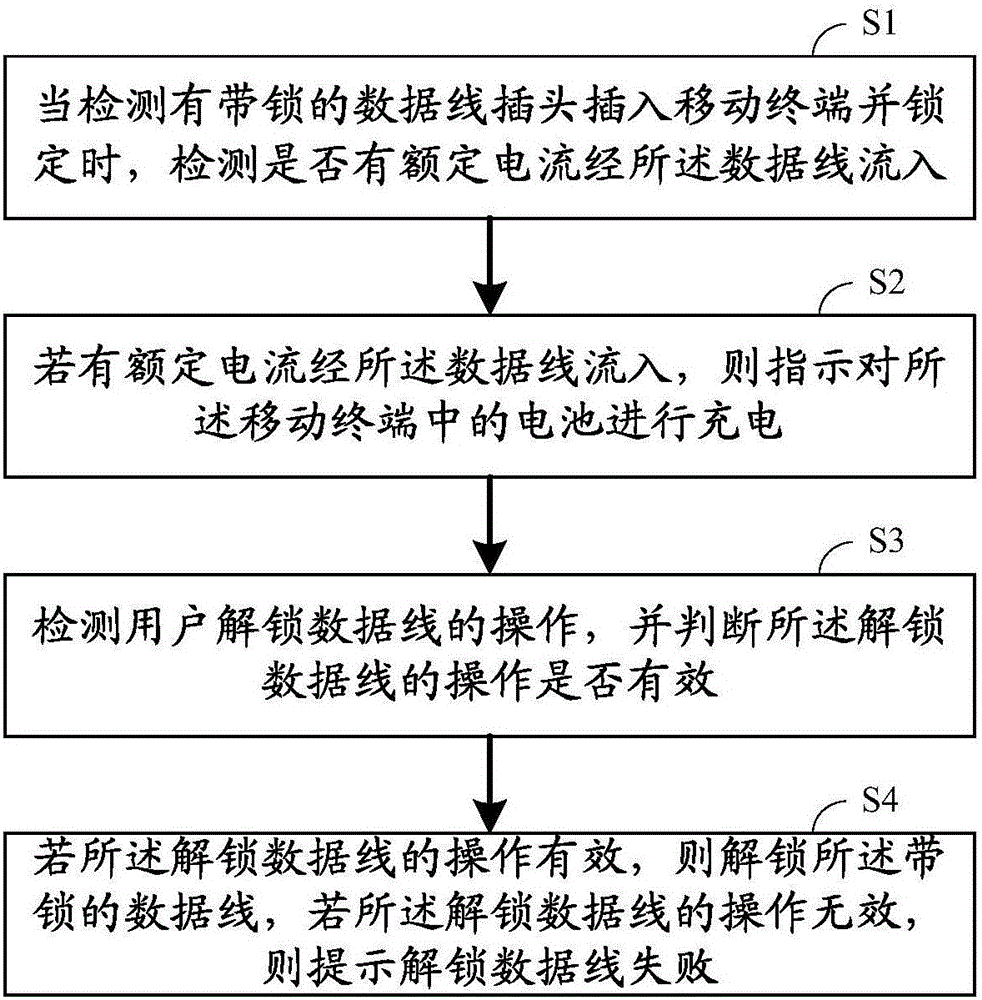
Charging method, charging device and charging system of data line with lock
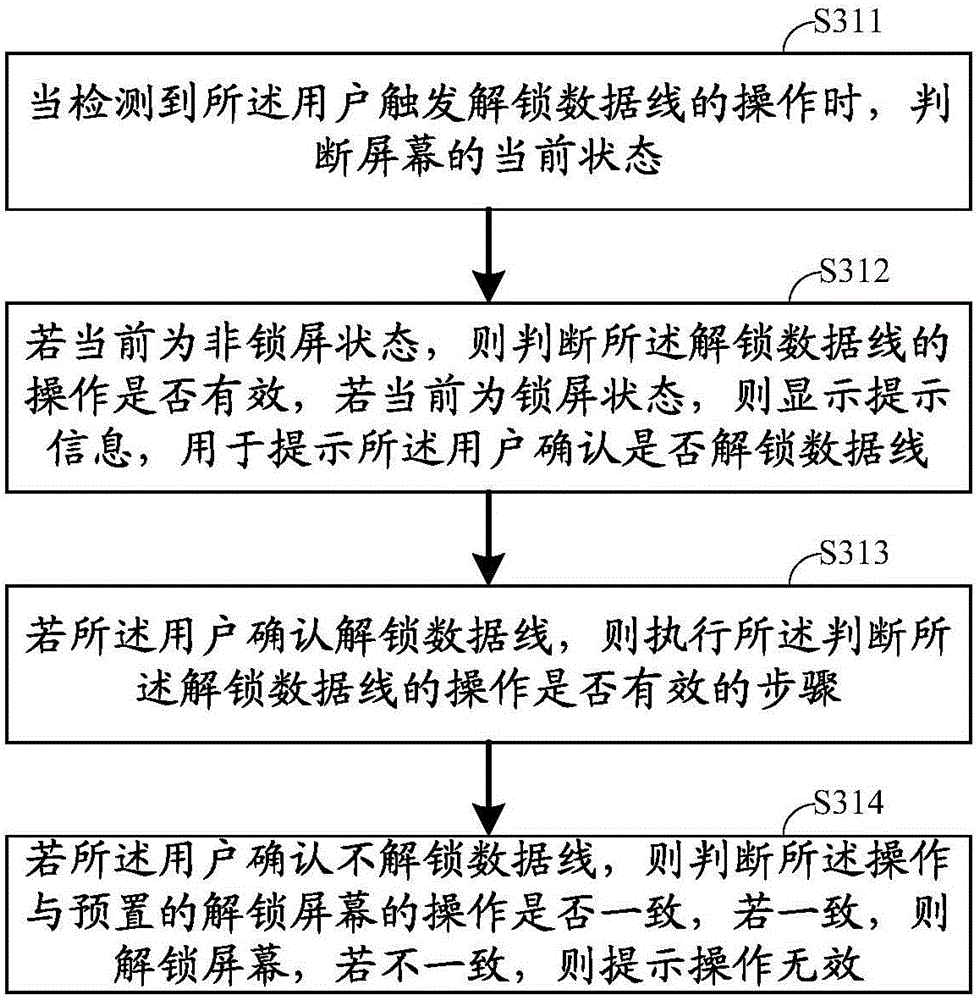
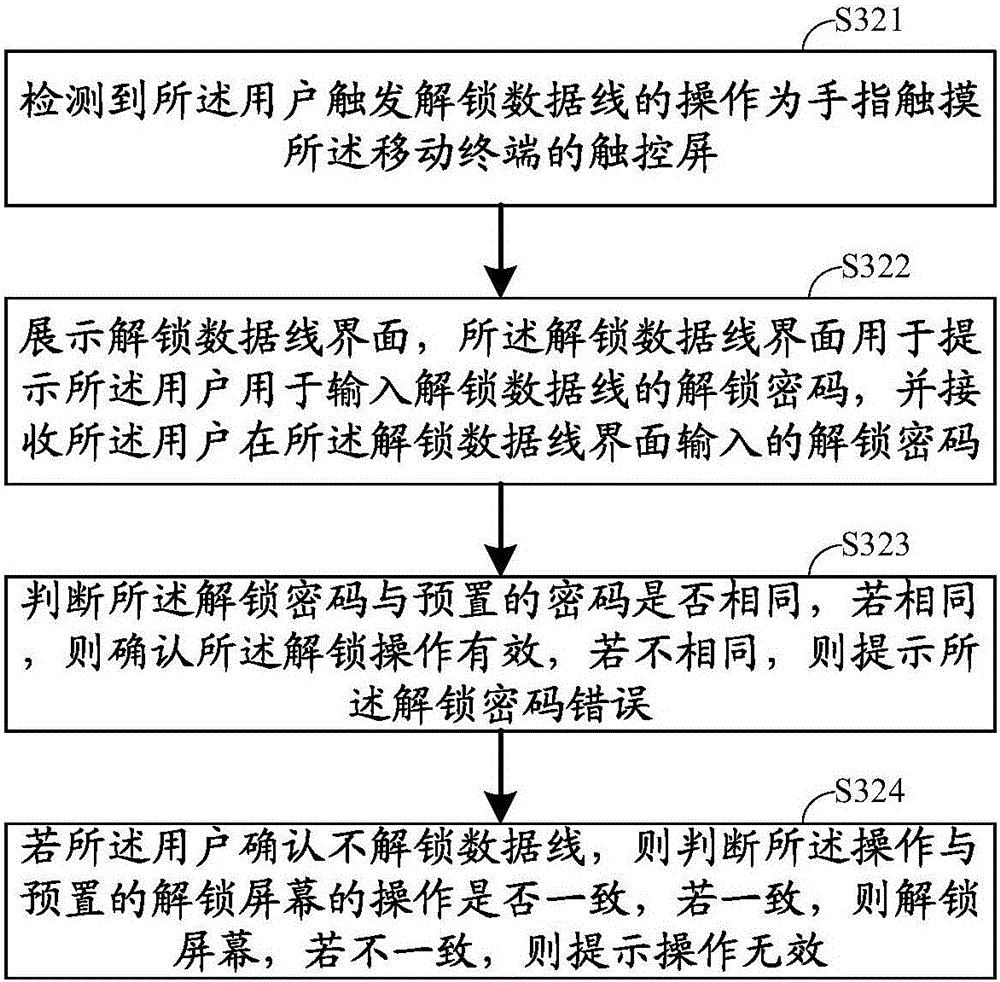
InactiveCN105870995AGuaranteed exclusivity and securityEnsure safetyDigital data authenticationElectric powerFingerprintElectrical battery
The invention belongs to the technical field of a mobile terminal, and discloses a charging method of a data line with a lock. The charging method comprises the following steps of detecting whether rated current flows through the data line or not when a plug of the data line with the lock is inserted into the mobile terminal and is locked; indicating a battery in the mobile terminal to charge if the rated current flows through the data line; detecting operation of unlocking the data line by a user, and judging whether the operation of unlocking the data line is valid or not; and unlocking the data line with the lock if the operation of unlocking the data line is valid, and reminding of failure unlocking of the data line if the operation of unlocking the data line is invalid. An intelligent terminal is locked by the data line with the lock, the connection of the data line can be prevented from being disconnected by other users expect the user of the mobile terminal, and the exclusivity and the safety during charging in a public place are ensured; and meanwhile, the unlocking of the data line is arranged and is verified by a password, fingerprint, iris and the like, and thus, the safety of the mobile terminal during the charging process is ensured.
Owner:LETV HLDG BEIJING CO LTD +1
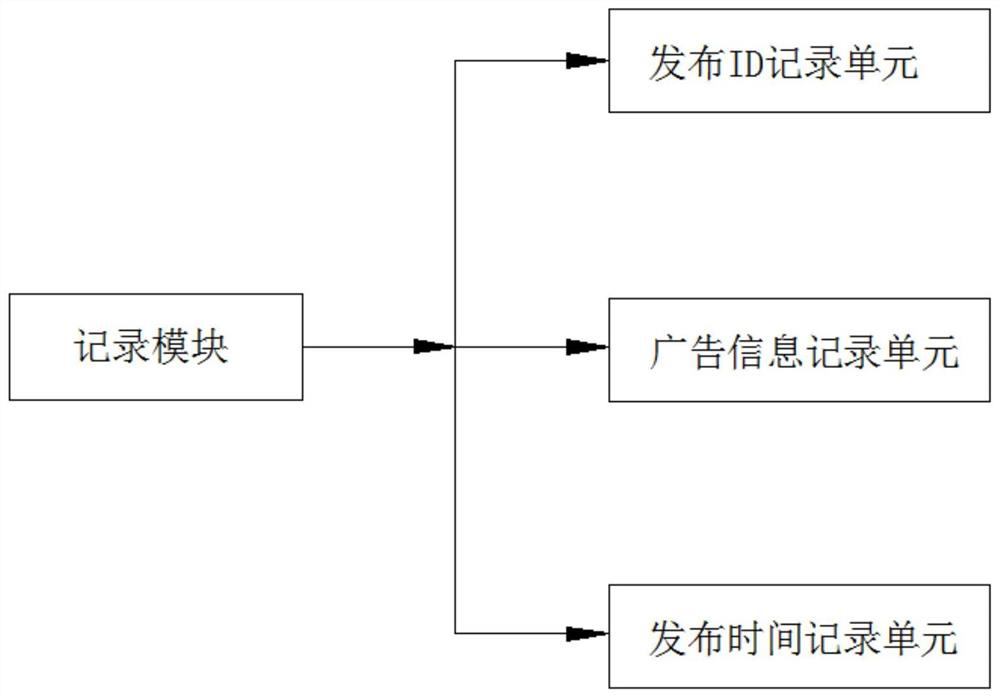
Mobile terminal network bidding promotion method and system
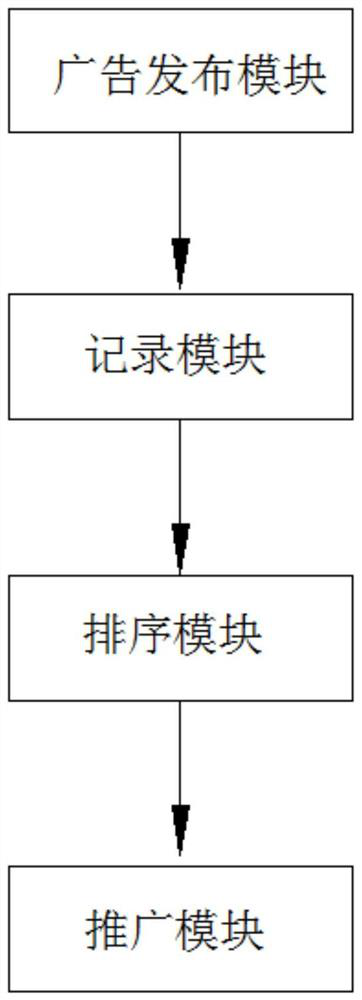
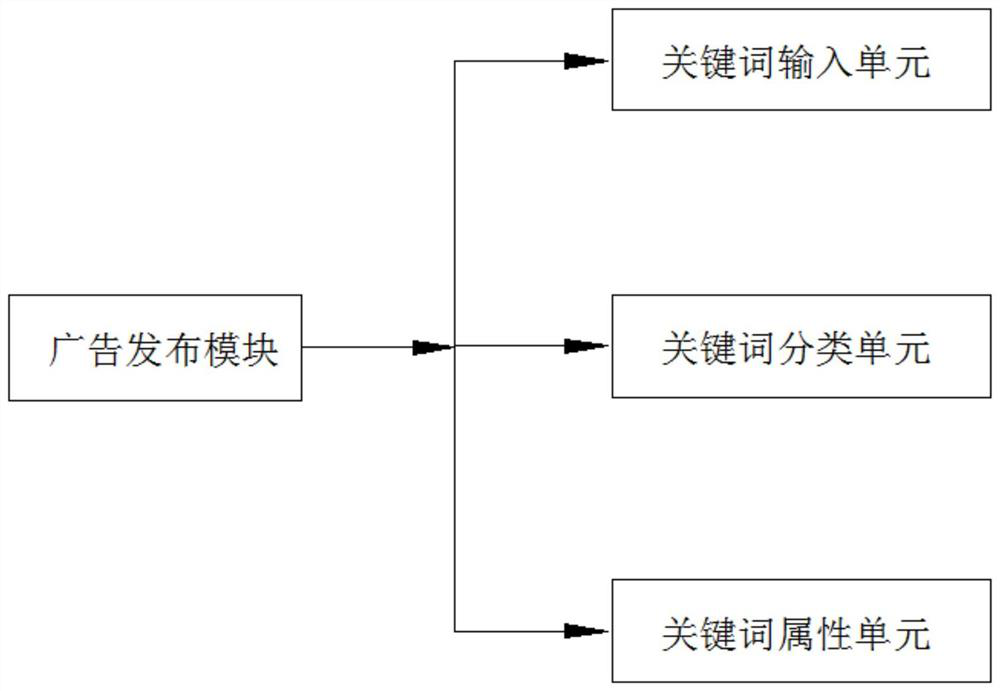
PendingCN111681046AGuaranteed exclusivityAdvertisementsSpecial data processing applicationsBusiness enterpriseMobile end
The invention provides a mobile terminal network bidding promotion method and system. The mobile terminal network bidding promotion method comprises the following steps: S1, putting an advertisement prepared by an enterprise, and checking whether a keyword in the advertisement is qualified or not; S2, recording the advertisement information released by the enterprise in the S1 in real time; S3, ranking all the advertisement information in the S2 in real time according to a preset ranking rule, and feeding back the ranking information to the enterprise in real time; and S4, performing graded popularization according to the ranking in the S3. According to the mobile terminal network bidding promotion method and system provided by the invention, the uniqueness of the advertisement position iseffectively ensured, and the situation that multiple advertisements are put in one advertisement position at the same time is avoided, so that enterprises obtaining the advertisement position can obtain the maximum benefit.
Owner:苏州远迪网络科技有限公司
Detection method for obligate hydrocarbon oxidizing bacteria
ActiveCN102453746BEasy to operateShort training periodMicrobiological testing/measurementColor changesShort terms
The invention discloses a detection method for obligate hydrocarbon oxidizing bacteria, belonging to the technical field of microorganism detection methods. The detection method comprises the following steps of: suspending and diluting a soil sample with a basic culture medium; performing short-term culturing in combination with a selective culture carbon source and an oxidation reduction indicating dye for 3-5 days; and computing the quantity of obligate hydrocarbon oxidizing bacteria in the soil sample according to the color change of an airtight culture tube through a computer program. A detection technology for obligate hydrocarbon oxidizing bacteria disclosed by the invention has the advantages of simple operating process, economic efficiency, practicability, quickly-obtained result in a short period of time, high specificity, capability of effectively shielding the interference of other bacteria on counting and simple and accurate counting process, and is suitable for large-scale industrial exploration measurement with a large sample quantity.
Owner:CHINA PETROLEUM & CHEM CORP +1
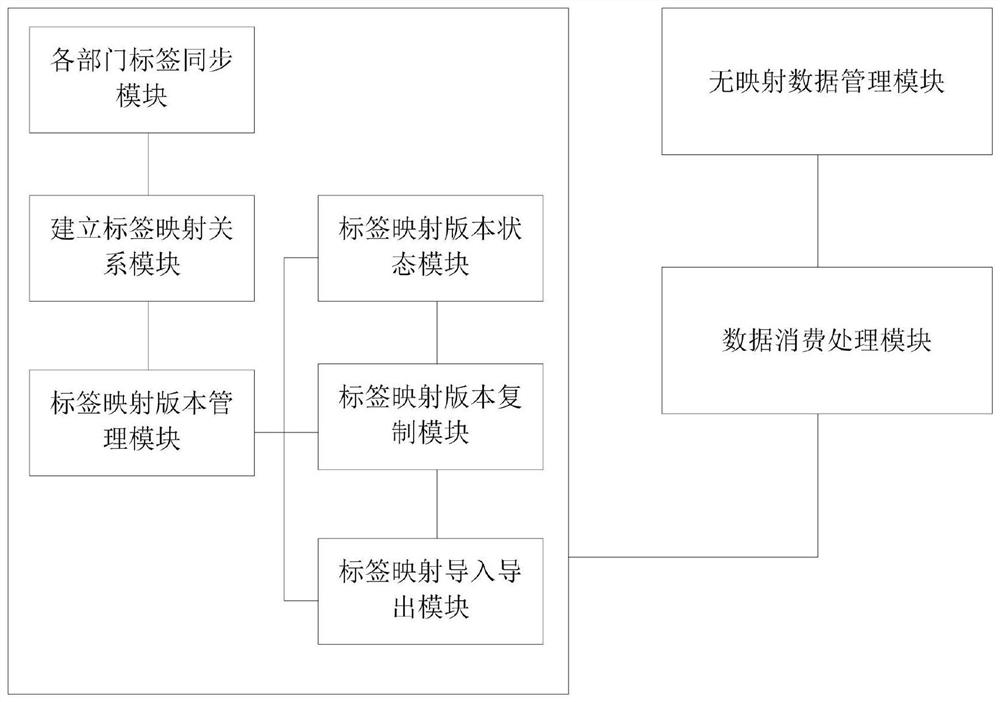
System for supporting multi-system label mapping to realize unified label management
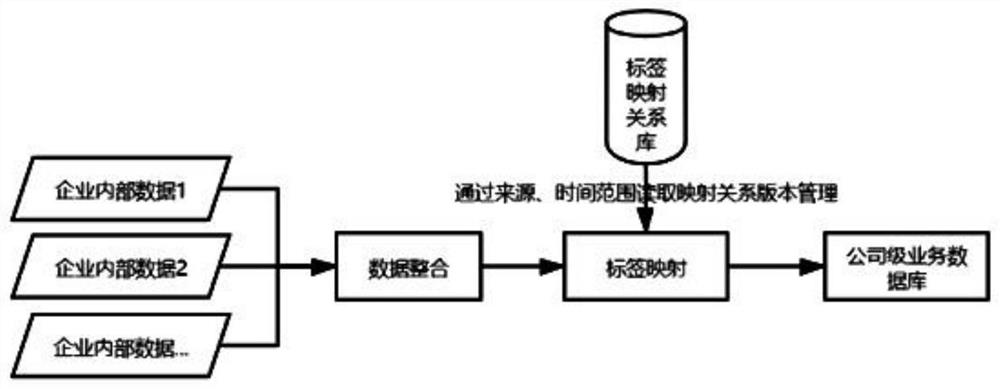
PendingCN112559495AGuaranteed uniformityKeep exclusiveDatabase management systemsDatabase distribution/replicationBusiness enterpriseEngineering
The invention discloses a system for supporting multi-system label mapping to realize unified label management. The system comprises a label synchronization module of each department, a label mappingrelationship establishing module, a label mapping version management module, a label mapping version state module, a label mapping version copying module and a label mapping import and export module.The system can support the data of different service departments of the data in different historical stages and continuously keep an original service classification system, and the data uniformity isensured in the company unified analysis dimension in a label mapping mode. The uniqueness and particularity of historical data and service department data are maintained, and the unity of company dataanalysis is ensured, so that the company data is reasonably analyzed and utilized. An enterprise can be helped to convert service data of all departments into company-level service data in a label mapping mode, induction and analysis of all the service data according to a unified dimension are supported, and the problem of unification of service labels in a company can be solved.
Owner:SHENZHEN ZHONGYI TECH CO LTD
Electroluminescent semiconductor plate surface defect AI detection method
PendingCN113822870ACracked withoutDark spot abnormality NoneImage enhancementImage analysisData setImage detection
The invention relates to an electroluminescent semiconductor plate surface defect AI detection method. The method comprises the steps of carrying out first image enhancement processing, carrying out image defect labeling and conversion, training random distribution of verification test images, carrying out second image enhancement processing, establishing a target detection neural network, carrying out data training to obtain optimal weight parameters, and carrying out plate image AI detection. The objective of the invention is to solve the problems of low defect identification speed, low accuracy and lack of accurate classification and positioning capability due to limitation of quality and quantity of image data sets, single image data preprocessing method and small pixel algorithm network scale when defect detection is carried out on the surface of an electroluminescent semiconductor plate in the prior art. The method is suitable for detecting semiconductor chips and panels such as silicon, germanium, gallium arsenide and silicon carbide.
Owner:陈博源
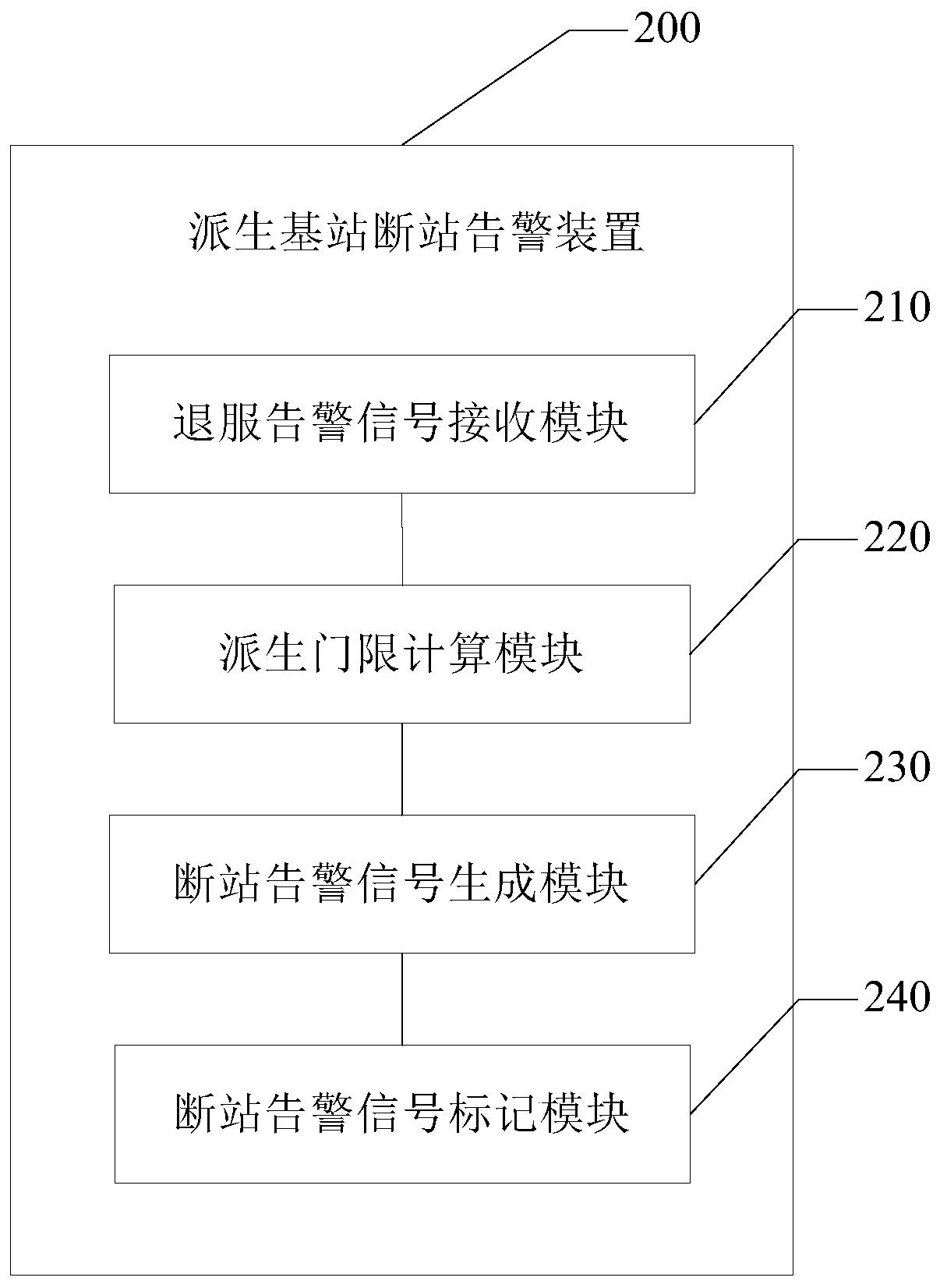
Derivation base station disconnection warning method and device
InactiveCN110289998AImprove reliabilityImprove real-time performanceData switching networksWireless communicationMessage queueAlarm signal
The invention relates to a derived base station disconnection warning method and device, electronic equipment and a computer readable storage medium. The method comprises the following steps: receiving a cell out-of-service alarm signal from a message queue, and positioning a base station to which a cell belongs; dynamically calculating a derivation threshold of a base station to which the cell belongs, and judging whether the derivation threshold receives a cell out-of-service alarm signal or not; if all the derivation thresholds receive the cell out-of-service alarm signals, generating station breaking alarm signals of the base stations to which the cells belong; and generating a derived mark by the base station of the cell corresponding to the station-breaking alarm signal. According to the invention, through dynamic calculation and generation of the derivation base station disconnection alarm signal, integrity and exclusiveness of the whole derivation process are ensured, and reliability and real-time performance of derivation alarm are effectively improved.
Owner:BEIJING MATARNET TECH
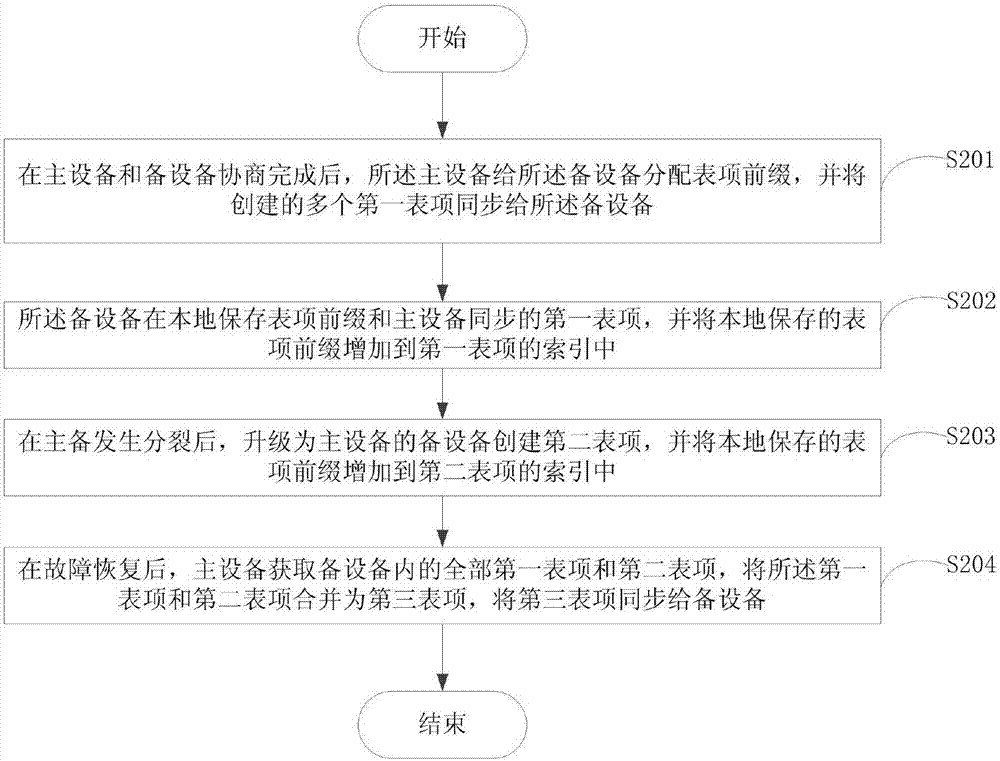
Entry management method and system
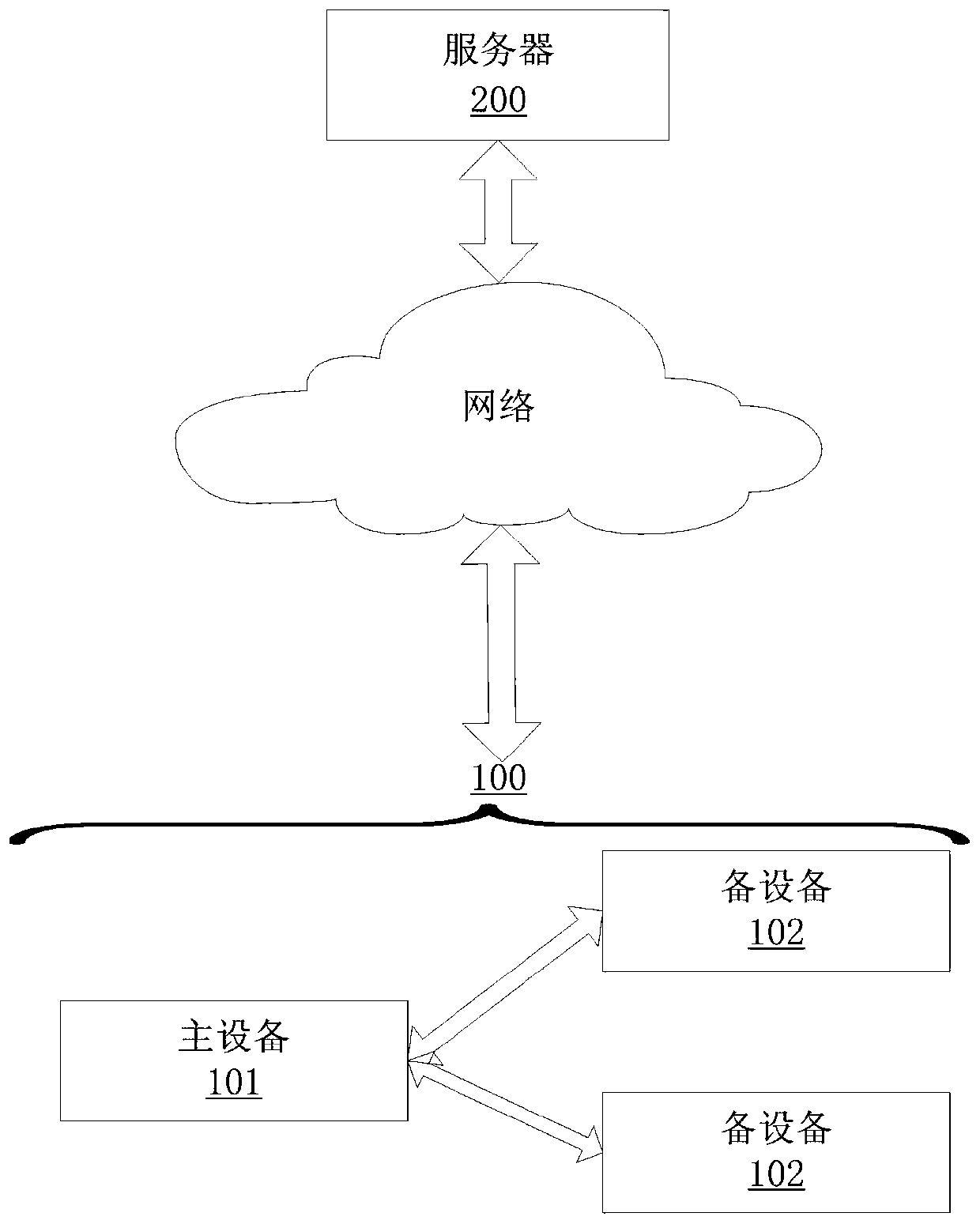
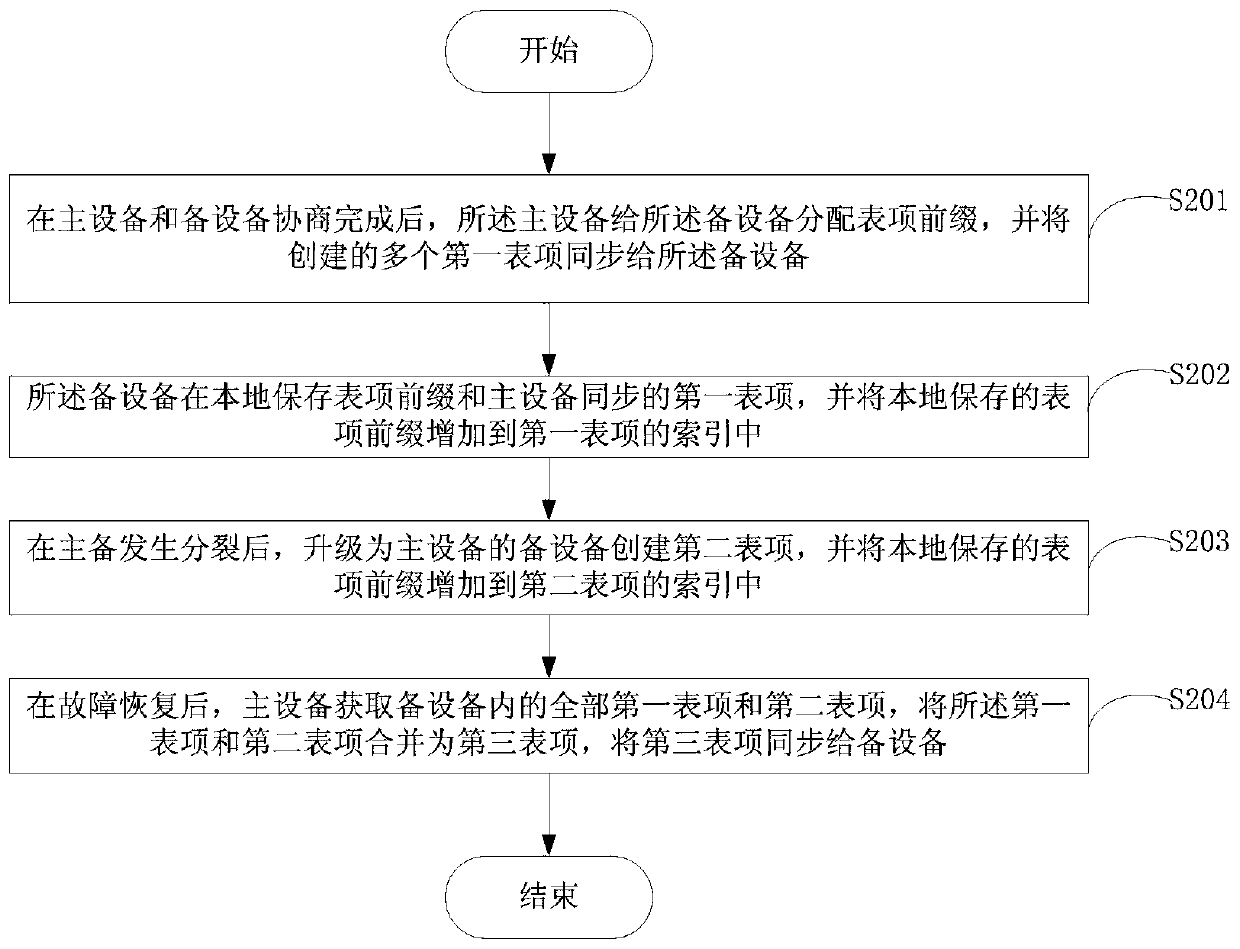
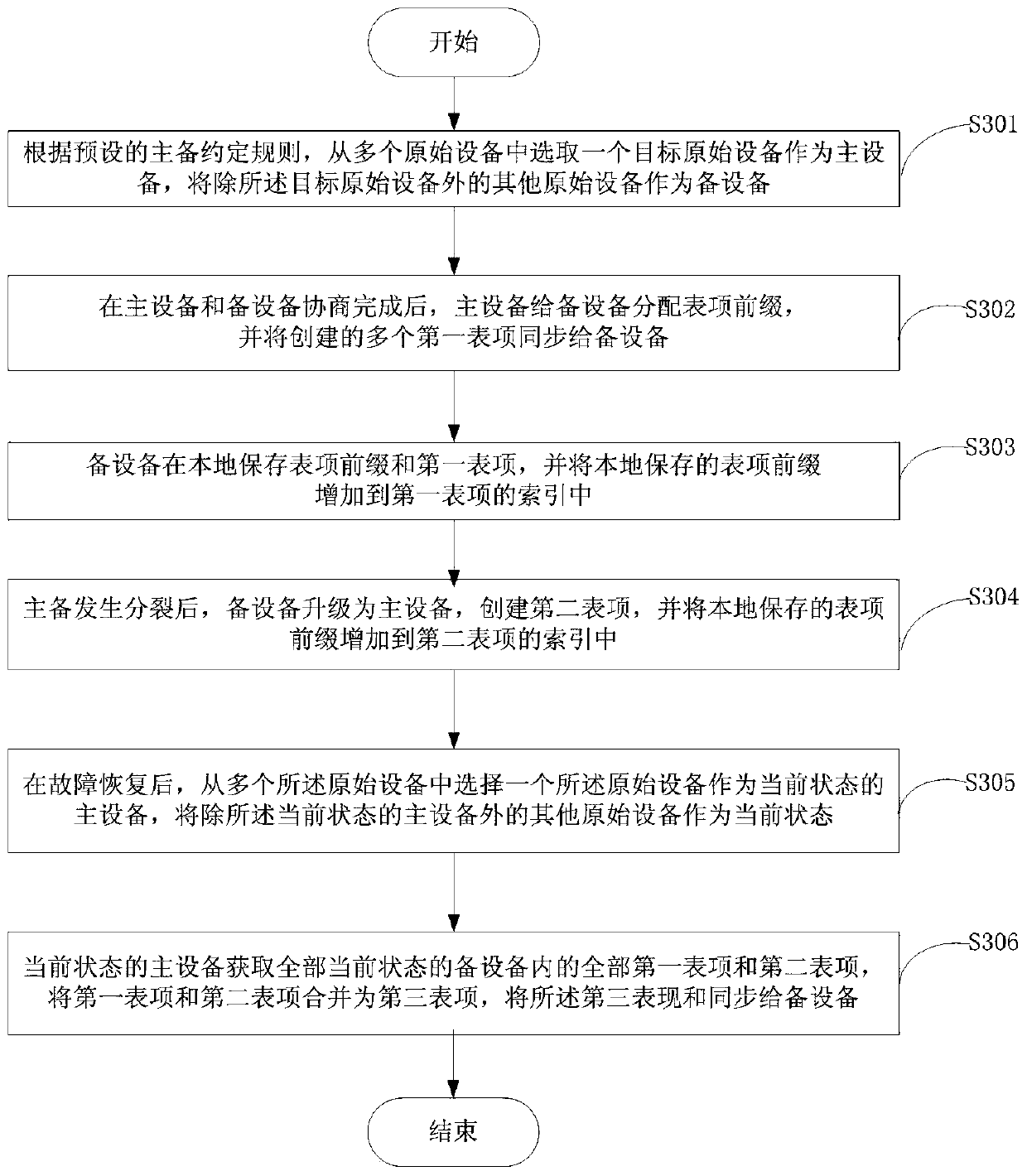
ActiveCN106936641AAvoid missingIntegrity guaranteedData switching networksNetwork deploymentOperating system
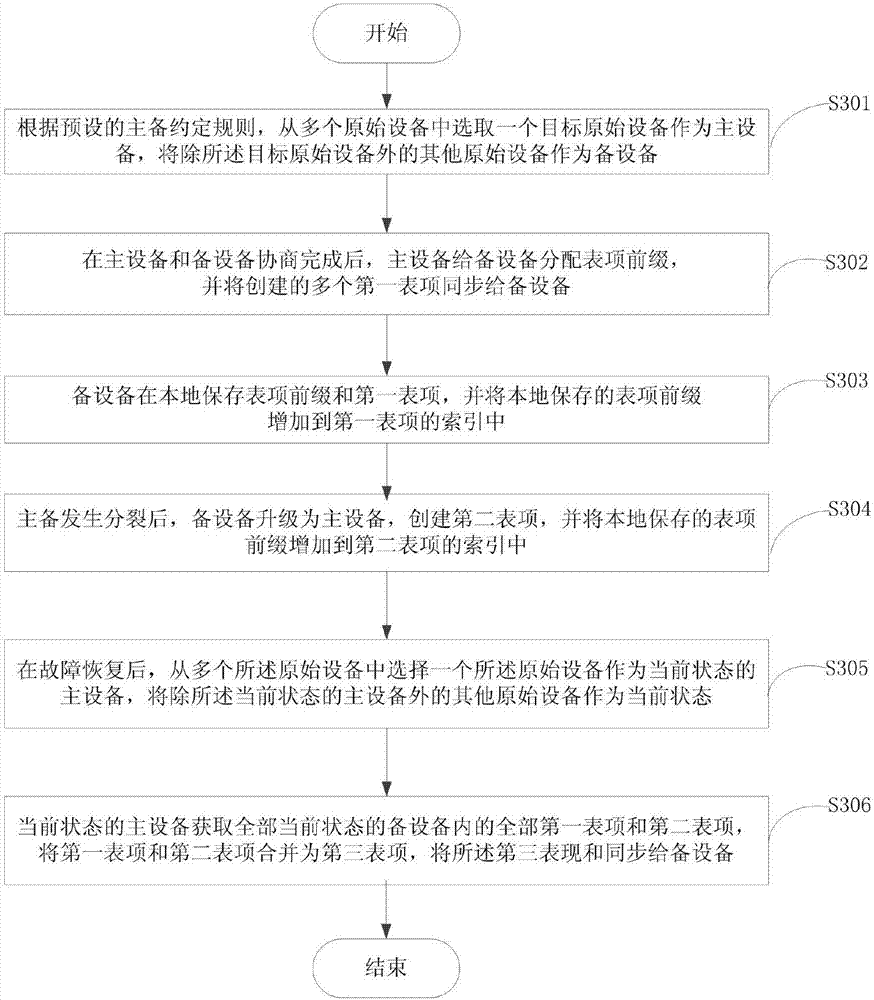
The invention provides an entry management method and system, which are applied to the technical field of communication. The method comprises the following steps that a primary device distributes entry prefixes to backup devices and synchronizes a plurality of created first entries to the backup devices; the backup devices add the entry prefixes to an index of a first entry; after the primary device and the backup devices are split, the backup device which is upgraded to the primary device creates a second entry and adds the locally-stored entry prefixes into an index of the second entry; and after fault recovery, the primary device obtains all first entries and second entries in the backup devices, merges the first entries and the second entries to a third entry and synchronizes the third entry to the backup devices. The primary device creates the corresponding distribution of the entries and the local storage of the entry prefixes of the first entry and merges all obtained entries in the initial state, so that the integrity and the exclusiveness after merging of the entries are guaranteed, and thus the stability and the accuracy of entry management of the primary and backup devices during network deployment are guaranteed.
Owner:MAIPU COMM TECH CO LTD
A double-buffering robot software log storage method
The invention provides a double-buffering type robot software log storage method. The method is characterized by comprising the following steps of: setting a log storage software function loading module, a log storage software function unloading module, a log storage software operation module, a log information software buffer, a log information software receiver and a log information software analyzer, wherein the log information software buffer comprises two log buffer areas with same storage spaces; when one log buffer area is full of data, switching an input pointer to the other log buffer area so as not to delay the data input; pointing an output pointer to the log buffer area full of data, outputting the log data information in the log buffer area full of data, and setting the log buffer area to be in an idle state. According to the method, the log data information can be stored, and the overall operation load of robot system software can be greatly reduced, so that benefit is brought to improve the software defect check efficiency.
Owner:FOSHAN INST OF INTELLIGENT EQUIP TECH +1
A detection kit capable of simultaneously detecting and differentiating foot-and-mouth disease and vesicular stomatitis, as well as primers and probes
ActiveCN106929605BGuaranteed FeaturesGuaranteed exclusivityMicrobiological testing/measurementMicroorganism based processesMultiplexDisease
The invention discloses a detection kit, primer and probe capable of simultaneously detecting and identifying a foot-and-mouth disease and vesicular stomatitis. The primer and the probe are shown as sequence tables SEQ ID NO:1 to SEQID NO:14. The invention further discloses a one-step-method multiplex fluorescence RT-PCR detection kit rapid, accurate and convenient to use and simultaneously detecting and identifying the foot-and-mouth disease and the vesicular stomatitis. By adopting the detection method, one-time sampling and one-time analysis can be achieved, the purpose of simultaneously detecting and distinguishing three types of important viruses can be achieved, the working amount and cost for detection is reduced, epidemic disease detection can be completed within the shortest time, and time is won for disease prevention and treatment.
Owner:中国海关科学技术研究中心
Terminal access control method, terminal and storage medium
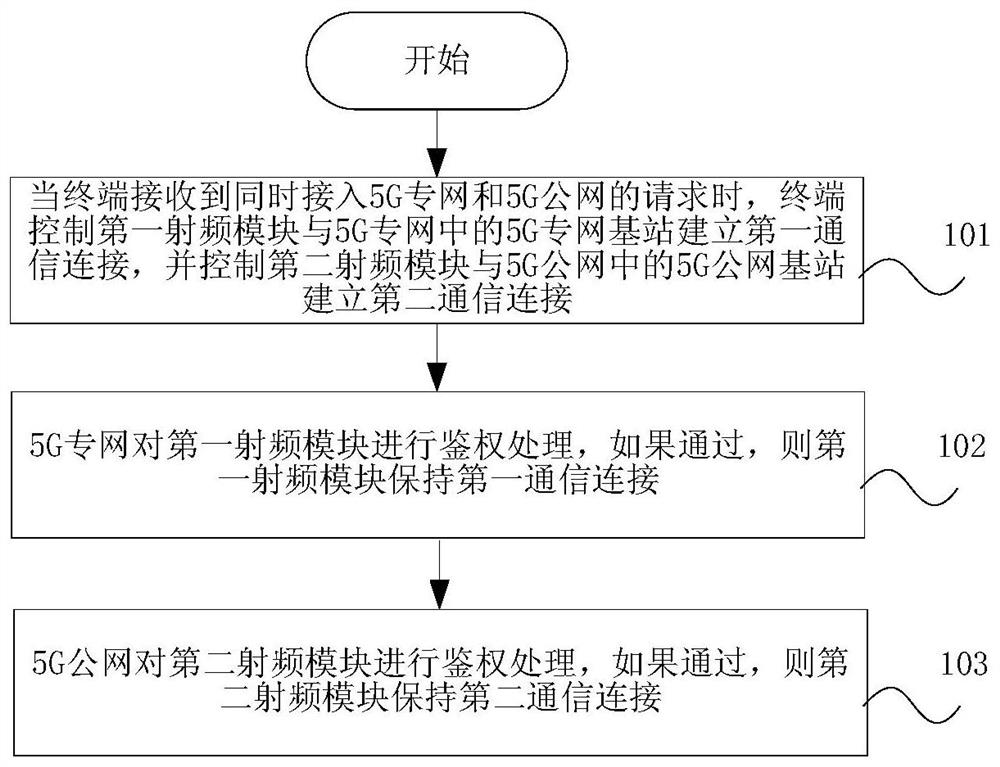
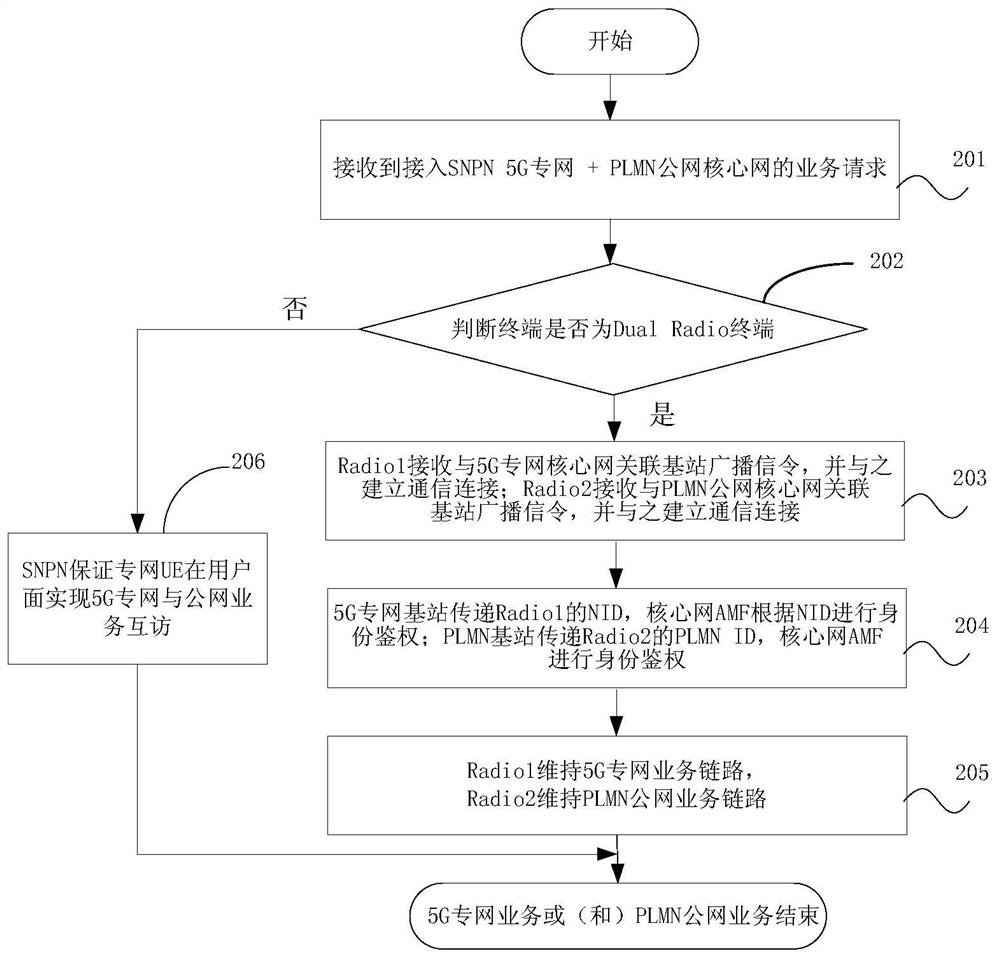
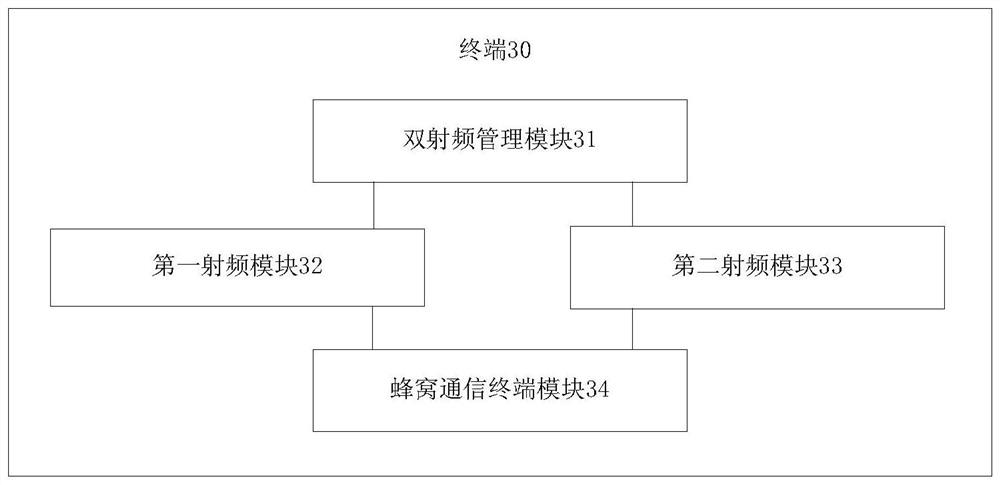
PendingCN113993130ARealize exclusive accessHigh bandwidthConnection managementSecurity arrangementPrivate networkRF module
The invention provides a terminal access control method, a terminal and a storage medium. The method comprises the steps that a terminal controls a first radio frequency module to establish a first communication connection with a 5G private network base station in a 5G private network, and controls a second radio frequency module to establish a second communication connection with a 5G public network base station in a 5G public network; the 5G private network performs authentication processing on the first radio frequency module, and if the first radio frequency module passes authentication processing, the first radio frequency module keeps the first communication connection; and the 5G public network performs authentication processing on the second radio frequency module, and if the second radio frequency module passes authentication processing, the second radio frequency module keeps the second communication connection. According to the method, the terminal and the storage medium disclosed by the invention, the terminal can simultaneously access the core networks of the SNPN 5G private network and the PLMN public network and the base stations associated with the core networks, and simultaneously process the scheduling of the two base stations, so that the exclusive use of private network resources can be fully ensured, the advantages of the PLMN public network are fused, and specific high-reliability and high-security customized services are provided for industry users.
Owner:CHINA TELECOM CORP LTD
A method and system for sharing a parking space based on an intelligent ground lock
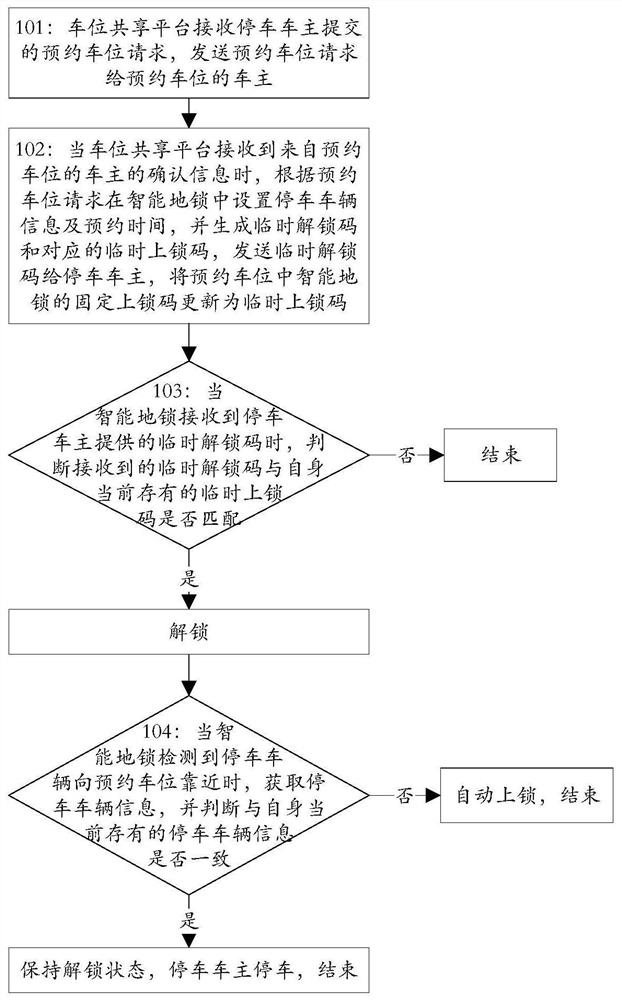
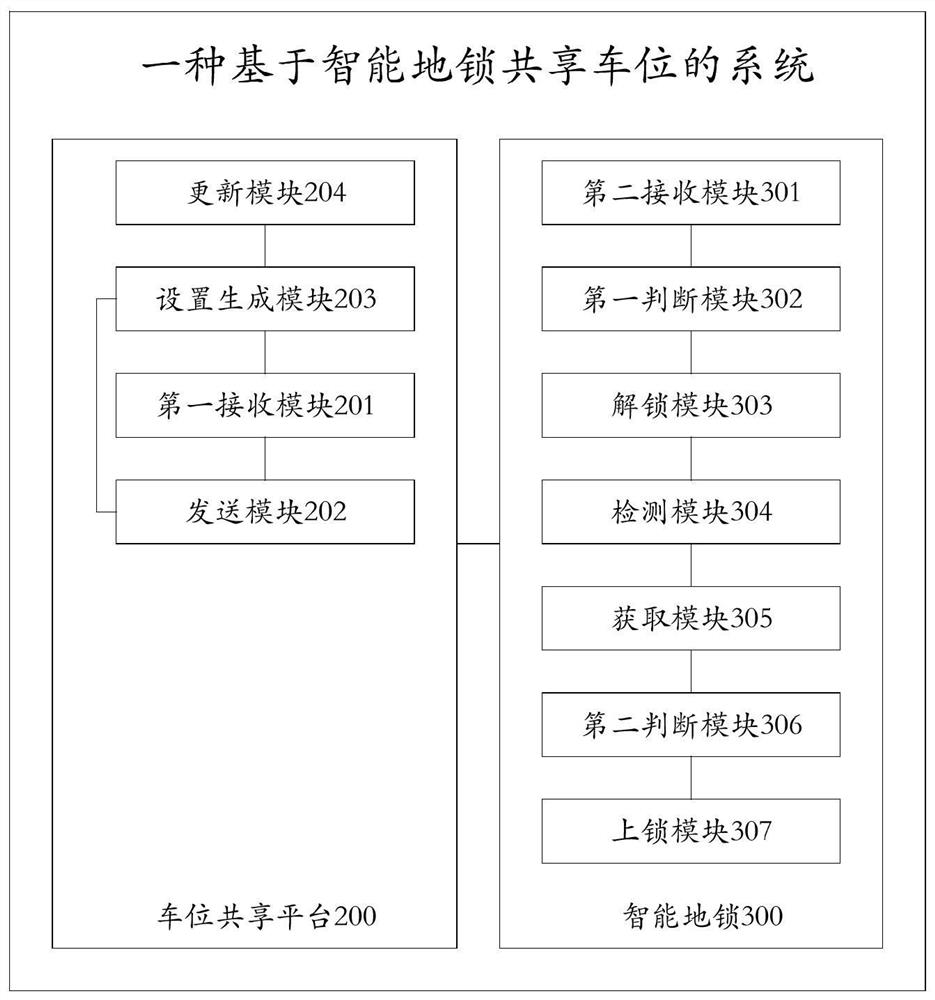
ActiveCN107527518BEasy to shareSafe sharingReservationsIndication of parksing free spacesShared parkingReliability engineering
Owner:TERMINUSBEIJING TECH CO LTD
Entry management method and system
ActiveCN106936641BAvoid missingIntegrity guaranteedData switching networksNetwork deploymentOperating system
The invention provides an entry management method and system, which are applied to the technical field of communication. The method comprises the following steps that a primary device distributes entry prefixes to backup devices and synchronizes a plurality of created first entries to the backup devices; the backup devices add the entry prefixes to an index of a first entry; after the primary device and the backup devices are split, the backup device which is upgraded to the primary device creates a second entry and adds the locally-stored entry prefixes into an index of the second entry; and after fault recovery, the primary device obtains all first entries and second entries in the backup devices, merges the first entries and the second entries to a third entry and synchronizes the third entry to the backup devices. The primary device creates the corresponding distribution of the entries and the local storage of the entry prefixes of the first entry and merges all obtained entries in the initial state, so that the integrity and the exclusiveness after merging of the entries are guaranteed, and thus the stability and the accuracy of entry management of the primary and backup devices during network deployment are guaranteed.
Owner:MAIPU COMM TECH CO LTD
Lamiophlomis rotata medicine material, intermediate and its injection liquid finger-print atlas quality testing method
InactiveCN1947740BTrue Fingerprint FeaturesGood correlationComponent separationPlant ingredientsSilica gelQuercetin
A fingerprint method for testing the quality of common lamiophlomis, its intermediate and its injection includes such steps as preparing the reference solution from quercetin, preparing three solutions of common lamiophlomis, its intermediate and its injection, filling the reference solution and one solution to be tested into liquid-phase chromatograph, and testing the similarity between their fingerprints, which must be greater than 0.90.
Owner:SICHUAN HENGKANG DEV
A Glitch-Free Switching Circuit Supporting Multiple Clocks
ActiveCN105680830BUniqueness guaranteedGuaranteed exclusivityPulse manipulationComputer architectureHemt circuits
The invention provides a burr-free switching circuit for supporting a multi-way clock. The burr-free switching circuit comprises a register, an AND gate, a first selector, a register group, a decoding circuit, a multi-clock interlock circuit and a clock selector; the decoding circuit realizes decoding of a one-hot encoding mode on a clock selection signal, and a log2N bit clock selection signal is translated into a decoding result of N bit one-hot encoding, so that the uniqueness and excludability of an effective clock enable signal can be guaranteed; meanwhile, the multi-clock interlock circuit processes the decoding result according to the currently outputted clock enable; if the currently outputted clock enable is not equal to the decoding result, then all clock enables are firstly closed, and then the decoding result is used as a new clock enable signal to open corresponding clocks, so that burr-free switching of a clock signal can be realized. The burr-free switching circuit for supporting the multi-way clock provided by the invention can realize burr-free switching of N paths of input clocks, support random switching orders, and provide greater flexibility for a work pattern of the whole circuit.
Owner:NO 771 INST OF NO 9 RES INST CHINA AEROSPACE SCI & TECH
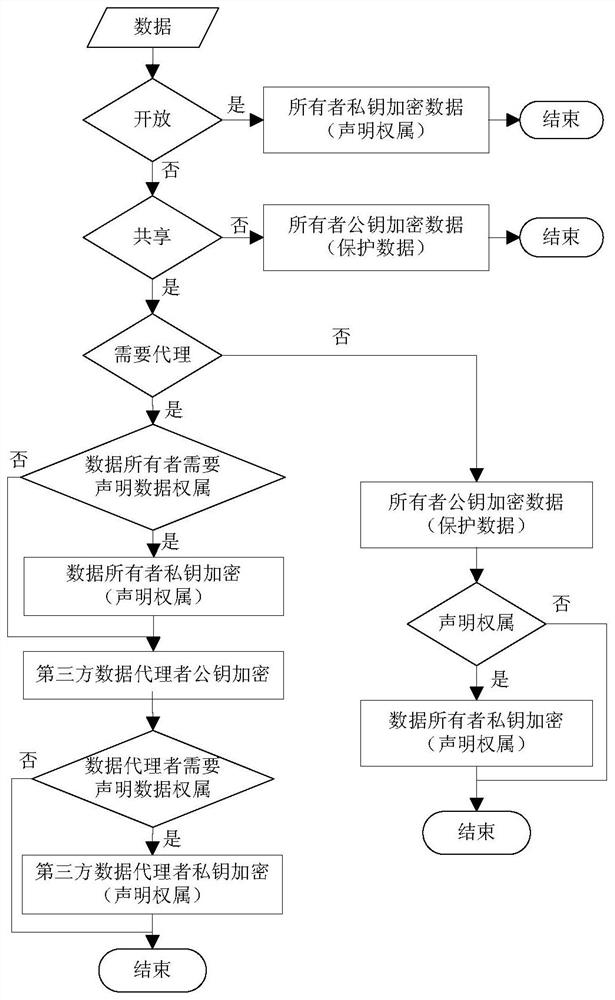
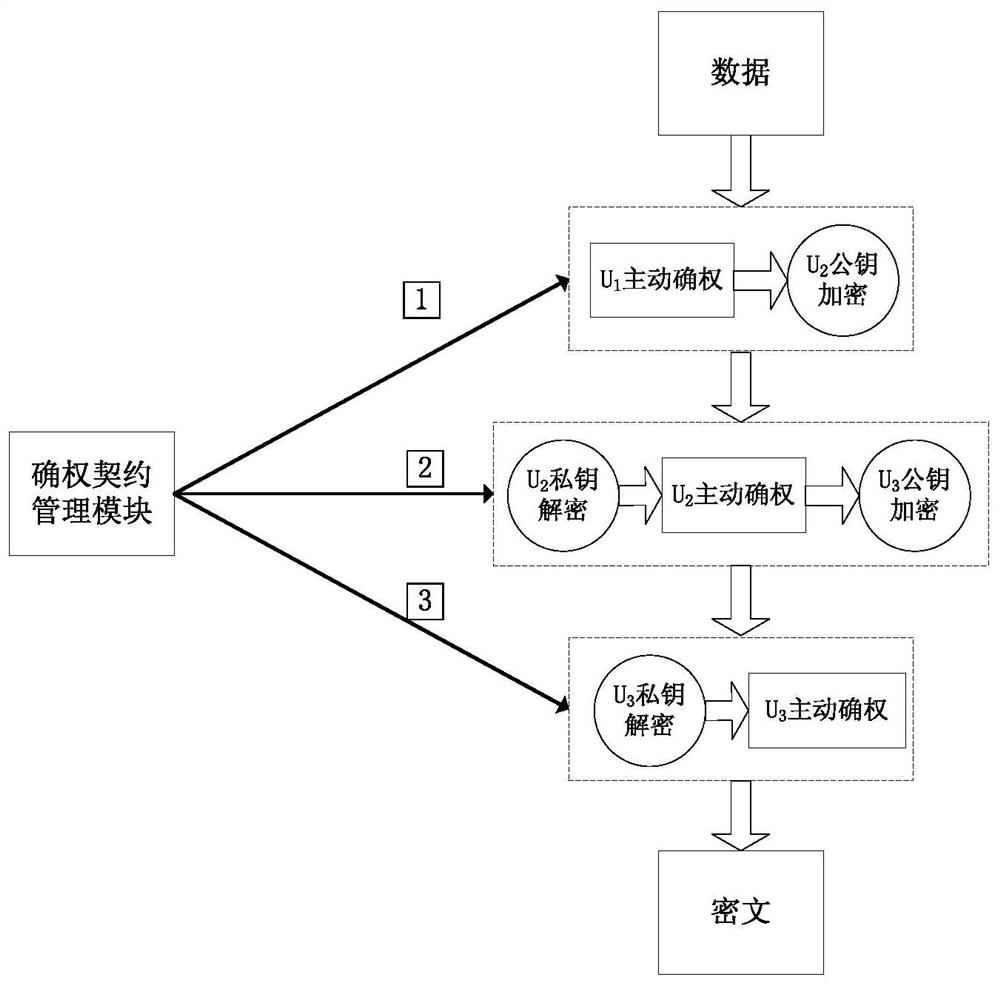
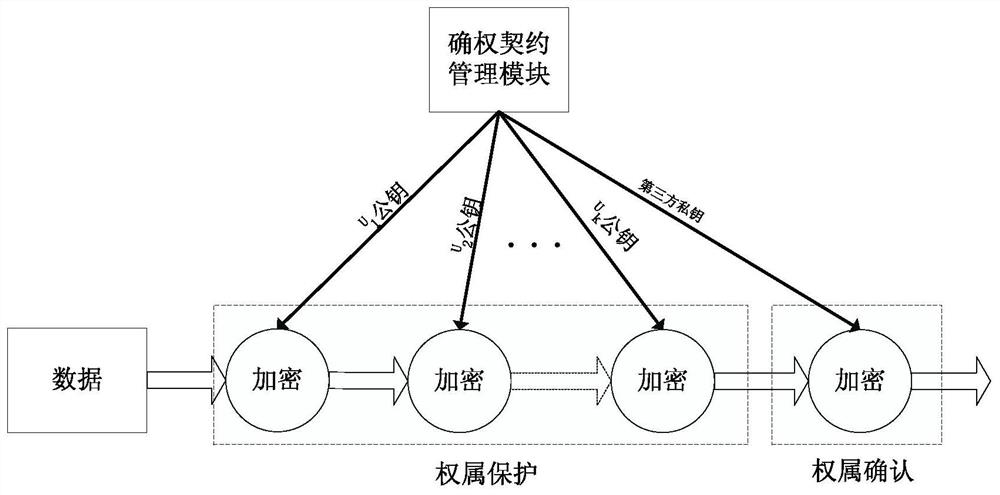
A method and system for confirming data rights based on encryption
ActiveCN107563869BRealize confirmation of rightsRealize ownershipPublic key for secure communicationUser identity/authority verificationEngineeringFinancial transaction
The invention discloses a method and system for confirming data rights based on encryption. The method includes the following steps: A. Judging whether the data is open, if the data is open, the data owner uses his private key to encrypt the data to complete the ownership statement and End the process; if the data cannot be opened, enter step B; B, determine whether the data is shared, if the data cannot be shared, the data owner uses his own public key to encrypt the data to complete the data protection and end the process; if the data can be shared, enter Claiming and protection steps. The method of the present invention realizes data right confirmation, technically guarantees the exclusiveness of data ownership, realizes data owner's unique ownership of data, lays the foundation for the distribution of data responsibilities and rights, ensures that data has an owner and can be found, and facilitates data transactions. Provide the basis.
Owner:苗放
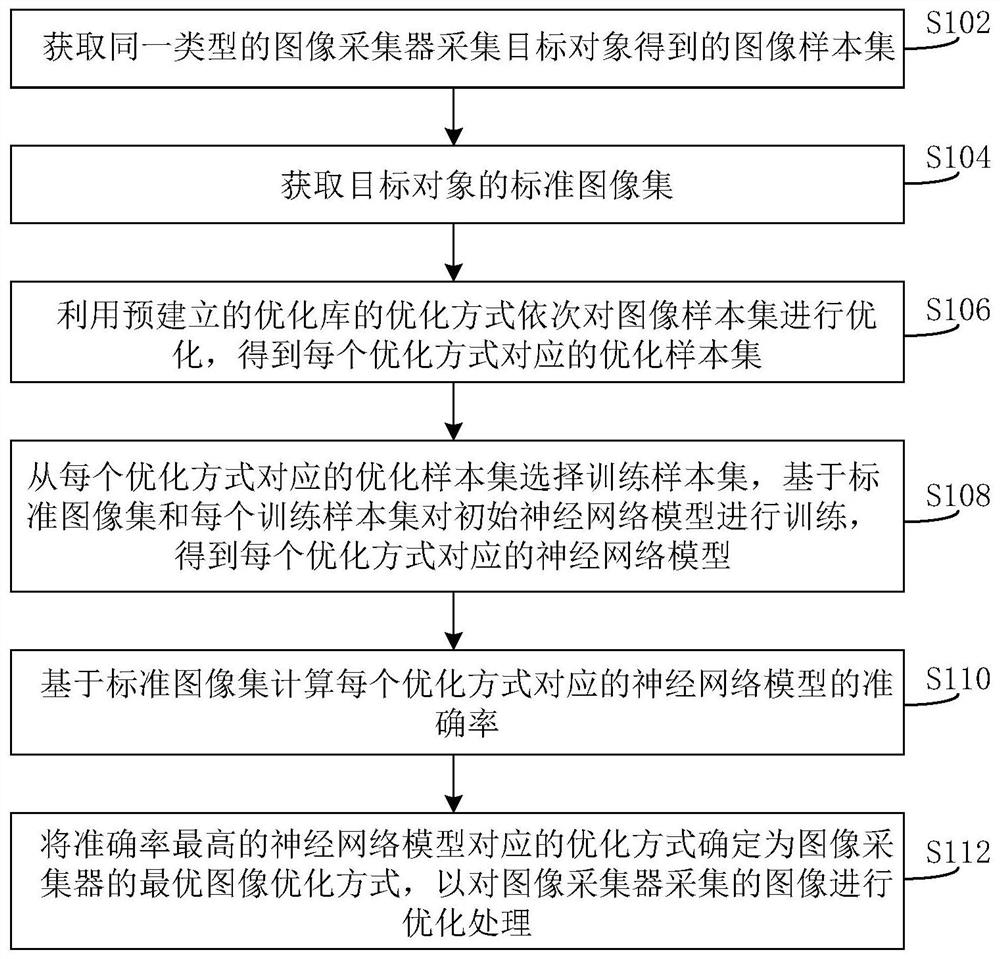
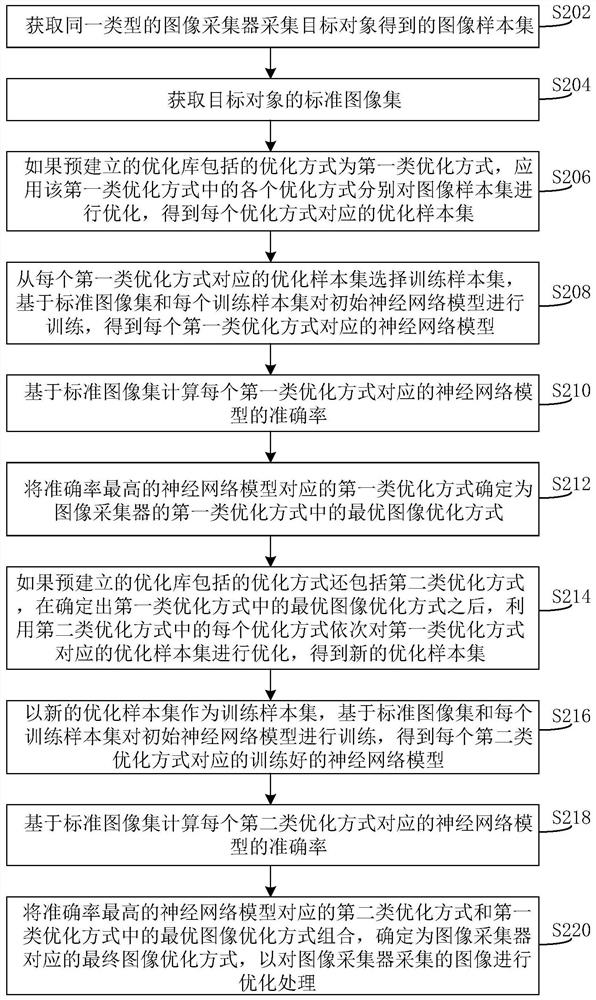
Method and device for determining image optimization mode
ActiveCN110111286BGuaranteed exclusivityGuaranteed suitabilityImage enhancementImage analysisAlgorithmNetwork model
The present invention provides a method and device for determining an image optimization mode, which relate to the field of image technology, and obtain an image sample set obtained by acquiring a target object and a standard image set of the target object obtained by the same image collector; using a pre-established optimization library The optimization method optimizes the image sample set in turn to obtain the optimized sample set; selects the training sample set from the optimized sample set corresponding to each optimization method, and trains the initial neural network model to obtain the neural network model corresponding to each optimization method; The standard image set calculates the accuracy rate of the neural network model corresponding to each optimization method; the optimization method corresponding to the neural network model with the highest accuracy rate is determined as the optimal image optimization method of the image collector. This method of optimizing image samples using different optimization methods and finding out the optimal image optimization method based on the neural network model ensures the specificity and applicability of the optimal image optimization method to the image collector.
Owner:BEIJING INSTITUTE OF GRAPHIC COMMUNICATION
Method for determining related substances of 6-acetoxy-7-methoxy-3H-quinazoline-4-ketone
InactiveCN112730702AEasy to separateGuaranteed exclusivityComponent separationKetoneMonopotassium phosphate
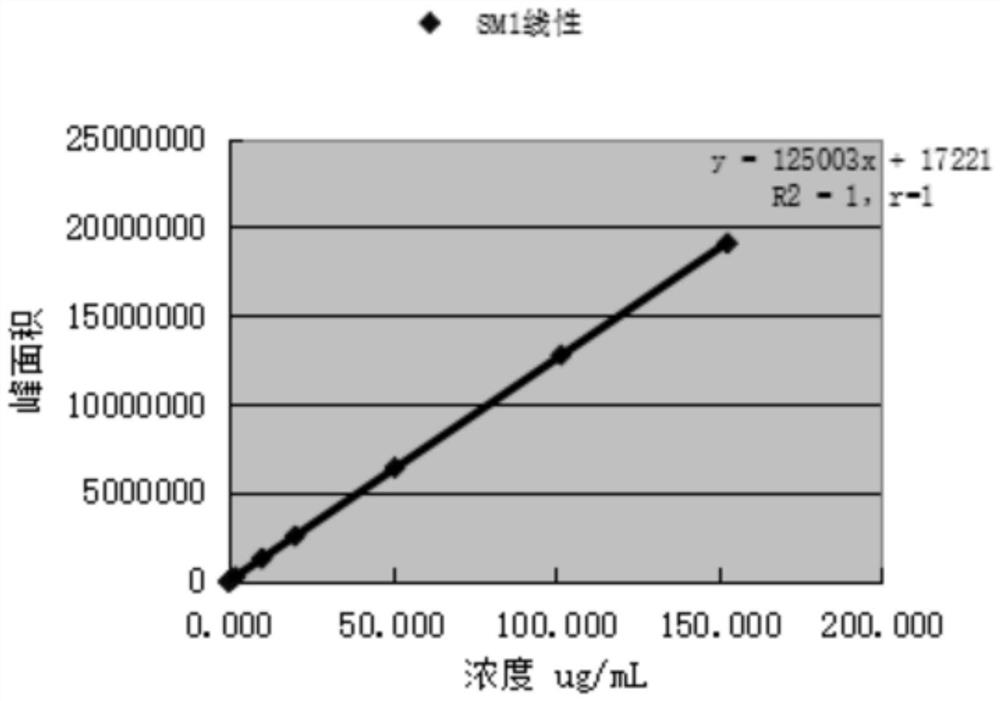
The invention discloses a method for determining related substances of 6-acetoxy-7-methoxy-3H-quinazoline-4-ketone. The metohd adopts fluorophenyl silane bonded silica gel as a filler and a potassium dihydrogen phosphate buffer acetonitrile mixed solution as a mobile phase, gradient elution is carried out, and a sample solvent is an acetonitrile aqueous solution. The detection method is accurate, simple and convenient to operate, good in reproducibility, good in sensitivity and specificity, capable of meeting detection of related substances of an antitumor drug gefitinib starting material 6-acetoxyl-7-methoxy-3H-quinazoline-4-ketone, capable of well controlling special impurities in a sample, capable of ensuring the product quality and high in practicability in work.
Owner:南京百泽医药科技有限公司
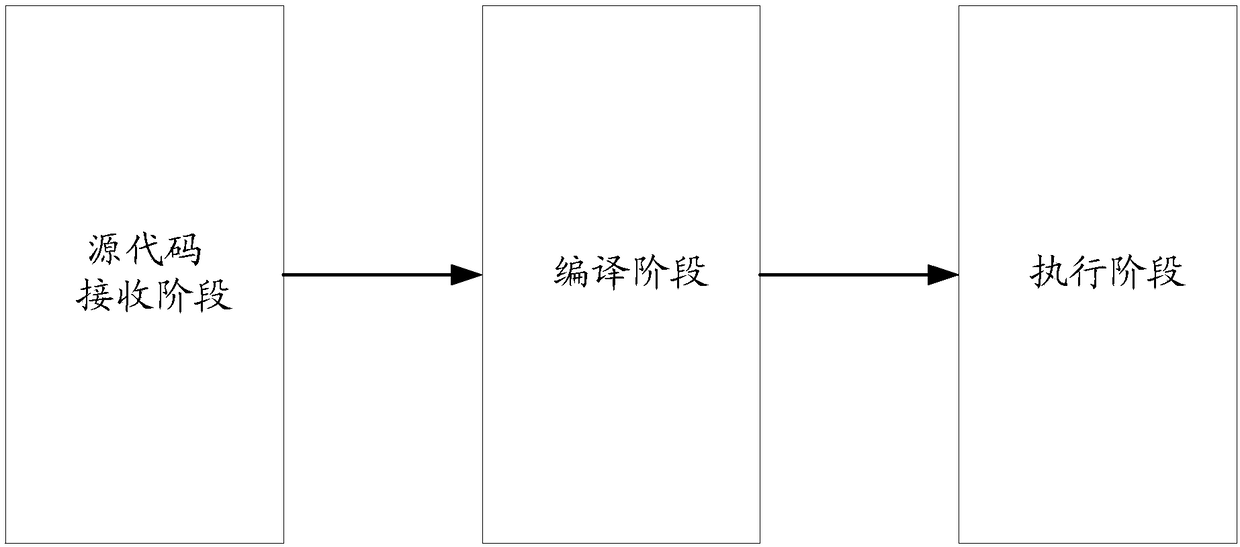
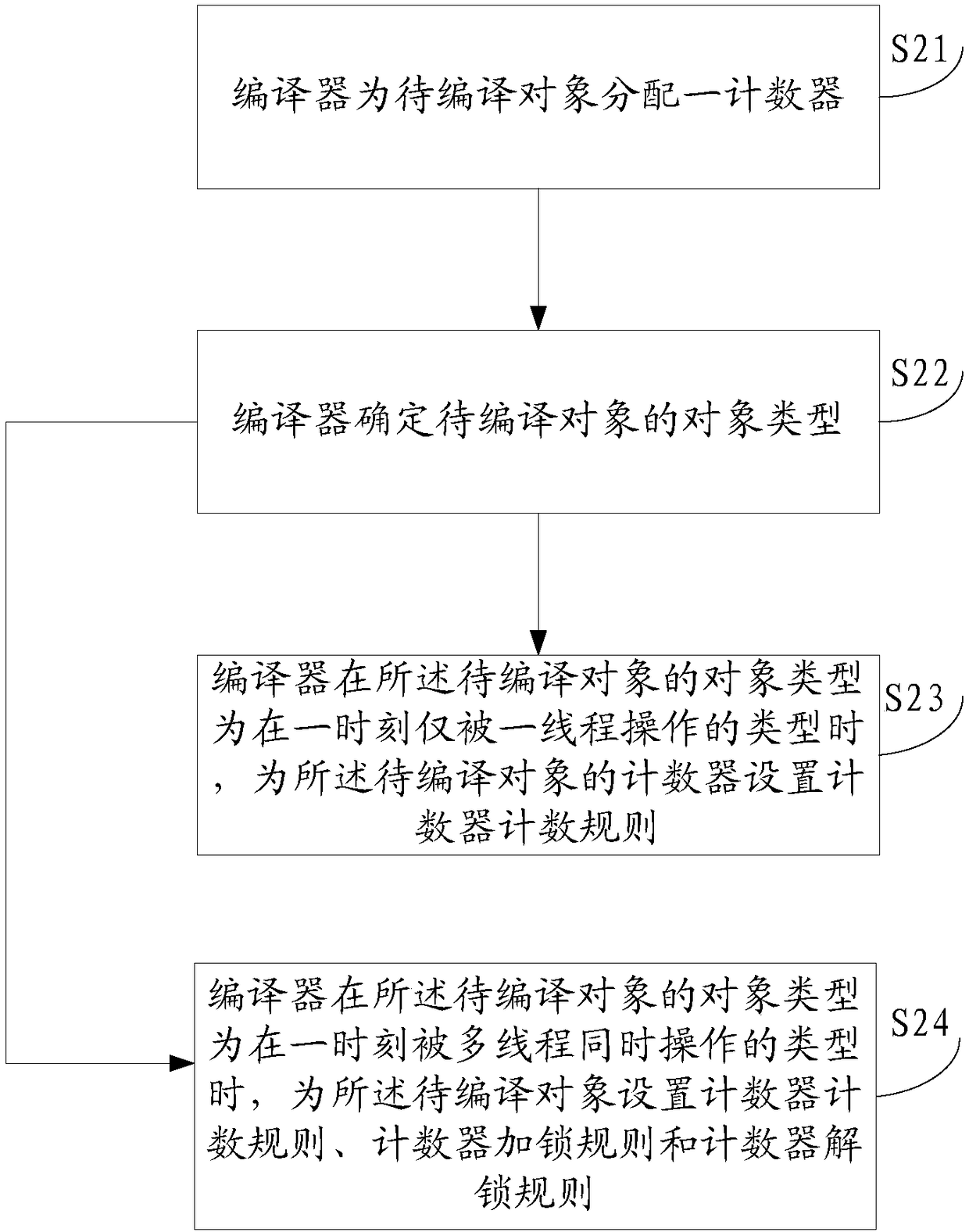
Source code object compiling method and device and computer
InactiveCN108376070AGuaranteed exclusivityImprove compilation efficiencyProgram synchronisationCode compilationSource codeCounting rule
The invention discloses a source code object compiling method and device and a computer. The method comprises the steps that the object type of a to-be-compiled object in source codes is determined bya compiler, wherein the to-be-compiled object is provided with a counter; counter counting rules are set for the counter of the to-be-complied object when the object type of the compiler in the to-be-complied object is the type which can only be operated by a thread at a moment. By means of the method, the device and the computer, the compiling efficiency of the object in the source codes can beimproved.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com