Voice fraud identification method and apparatus, terminal equipment and storage medium
A recognition method and voice technology, applied in voice analysis, automatic switching office, telephone communication, etc., can solve the problems of low efficiency and high labor cost, and achieve the effect of high processing efficiency and saving labor cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
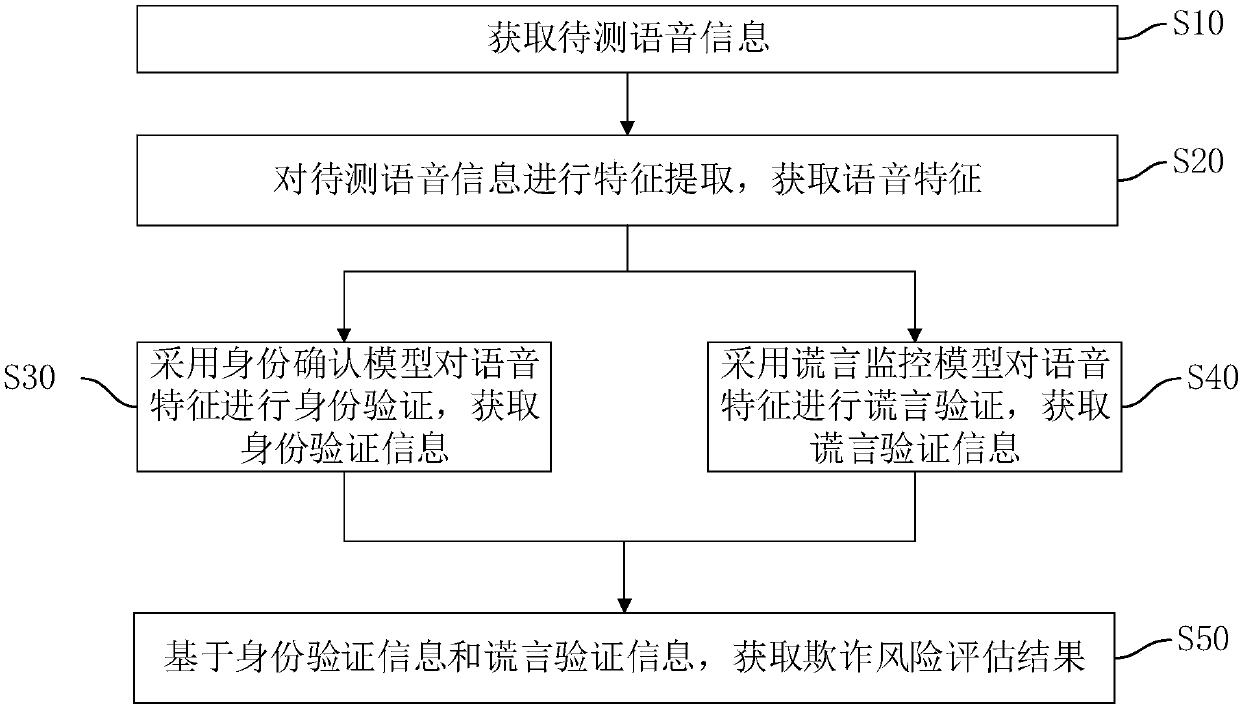
[0031] figure 1 A flow chart of the voice fraud recognition method in this embodiment is shown. The voice fraud recognition method is applied in the terminal equipment of financial institutions such as banks, securities, insurance, P2P, or other institutions that need voice fraud recognition, and is used to realize the intelligent recognition of the speaker's voice information to be tested, so as to identify the speaker Whether fraudulent activities are being committed. Such as figure 1 Shown, this speech fraud recognition method comprises the steps:
[0032] S10: Obtain the voice information to be tested.
[0033] Wherein, the voice information to be tested is the voice information of the speaker collected by the terminal device. The voice information to be tested may be voice information in wav, mp3 or other formats. Understandably, each voice information to be tested is associated with a user ID, and the user ID is an identifier for uniquely identifying the speaker of ...
Embodiment 2
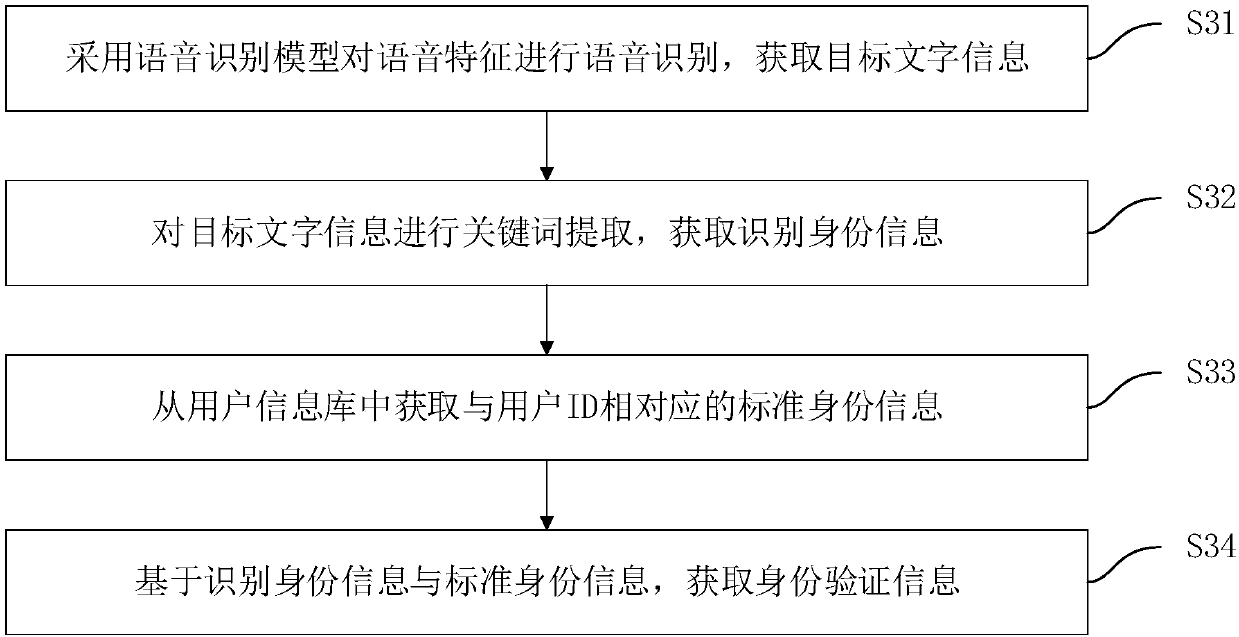
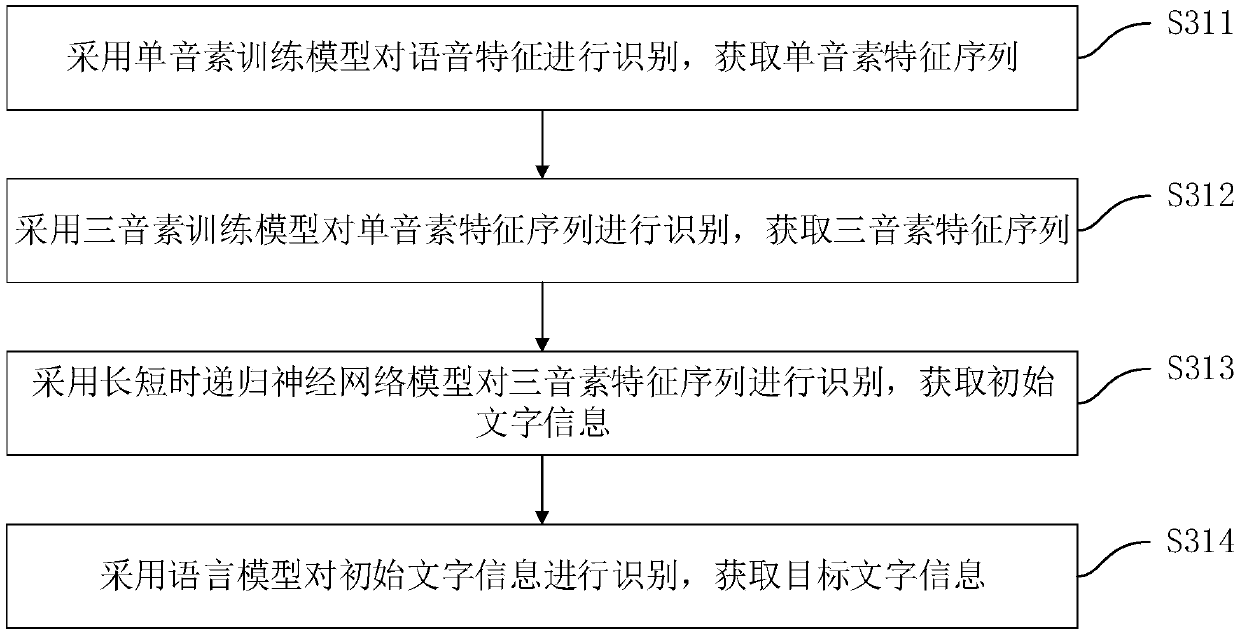
[0119] Figure 8 A functional block diagram of a voice fraud recognition device corresponding to the voice fraud recognition method in Embodiment 1 is shown. Such as Figure 8 As shown, the voice fraud recognition device includes a test voice acquisition module 10 , a voice feature acquisition module 20 , an identity verification acquisition module 30 , a lie verification acquisition module 40 , a fraud risk assessment module 50 and an assessment result sending module 60 . Wherein, the implementation functions of the voice acquisition module 10 to be tested, the voice feature acquisition module 20, the identity verification acquisition module 30, the lie verification acquisition module 40, the fraud risk assessment module 50 and the assessment result transmission module 60 are the same as the voice fraud recognition method in Embodiment 1 The corresponding steps S10-S60 or steps S10'-S60' are in one-to-one correspondence, and to avoid redundant description, this embodiment do...
Embodiment 3
[0148] This embodiment provides a computer-readable storage medium, and a computer program is stored on the computer-readable storage medium. When the computer program is executed by a processor, the voice fraud recognition method in Embodiment 1 is implemented. To avoid repetition, details are not repeated here. Alternatively, when the computer program is executed by the processor, the functions of the modules / units in the voice fraud recognition in Embodiment 2 are realized, and to avoid repetition, details are not repeated here.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com