Message forwarding method and device
A packet forwarding and packet technology, applied in the field of communication, can solve problems such as discarding high-priority packets, and achieve the effect of improving satisfaction and service quality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
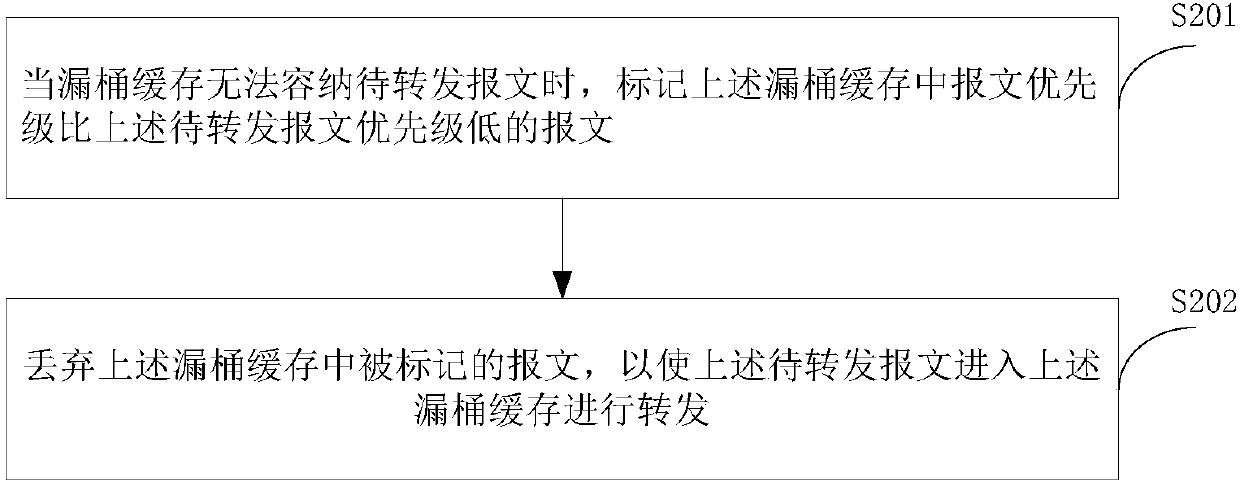
[0049] In this embodiment, a message forwarding method is provided, figure 2 is a flowchart of a message forwarding method according to an embodiment of the present invention, such as figure 2 As shown, the process includes the following steps:
[0050] Step S201, when the leaky bucket cache cannot accommodate the message to be forwarded, mark the message in the leaky bucket cache with a lower priority than the message to be forwarded;
[0051]In this step, before marking the packets in the leaky bucket cache with a lower priority than the packets to be forwarded, it further includes: judging whether the leaky bucket cache can accommodate the packets to be forwarded. When the sum of the number of tokens corresponding to the cached message in the above leaky bucket cache and the number of tokens corresponding to the above message to be forwarded is greater than the maximum number of tokens corresponding to the leaky bucket cache capacity, it is determined that the above leak...
Embodiment 2
[0056] Based on the technical solution of the above embodiment, the above technical solution will be described in detail below in conjunction with an embodiment.
[0057] In this embodiment, a message forwarding method is provided, and the process of the method includes the following steps:
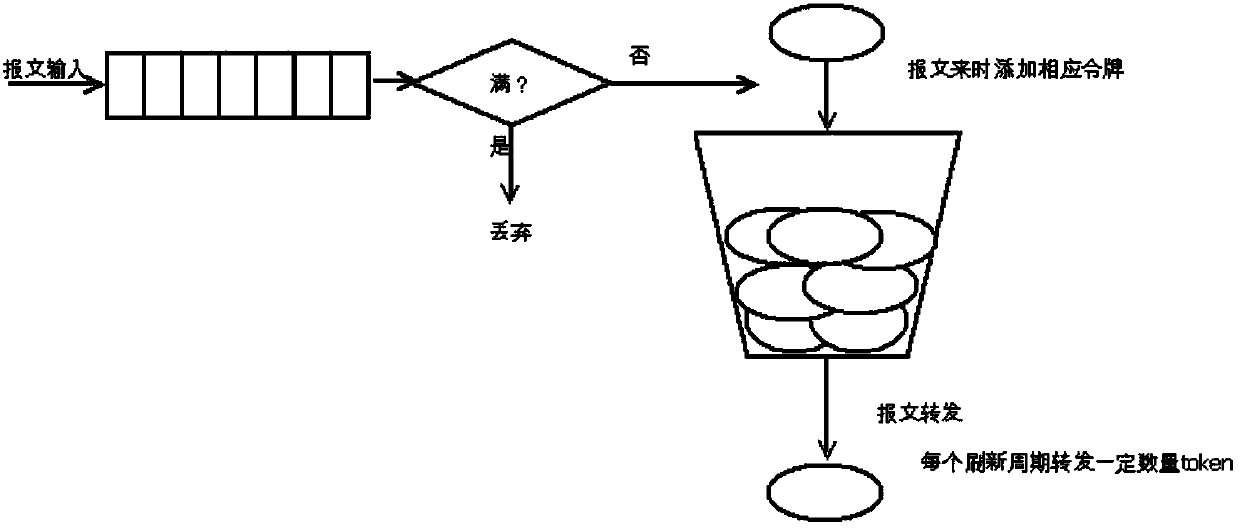
[0058] A: When configuring the scheduling mode first, if it is SP strict priority scheduling, and the leaky bucket rate limit is valid, initialize the module parameters. (The refresh rate V of the leaky bucket, the bucket depth setting B, the refresh cycle t, and calculate the refresh token T for a refresh interval.)
[0059] B: Each queue at the exit of the device receives data packets, and forwards the packet P according to the scheduling algorithm (SP mode, forwards the high-priority queue first, and forwards the next priority queue when the high-priority queue is empty). First judge whether to enter the pre-buffer area, enter the pre-buffer area to wait when the pre-buffer area is no...
Embodiment 3
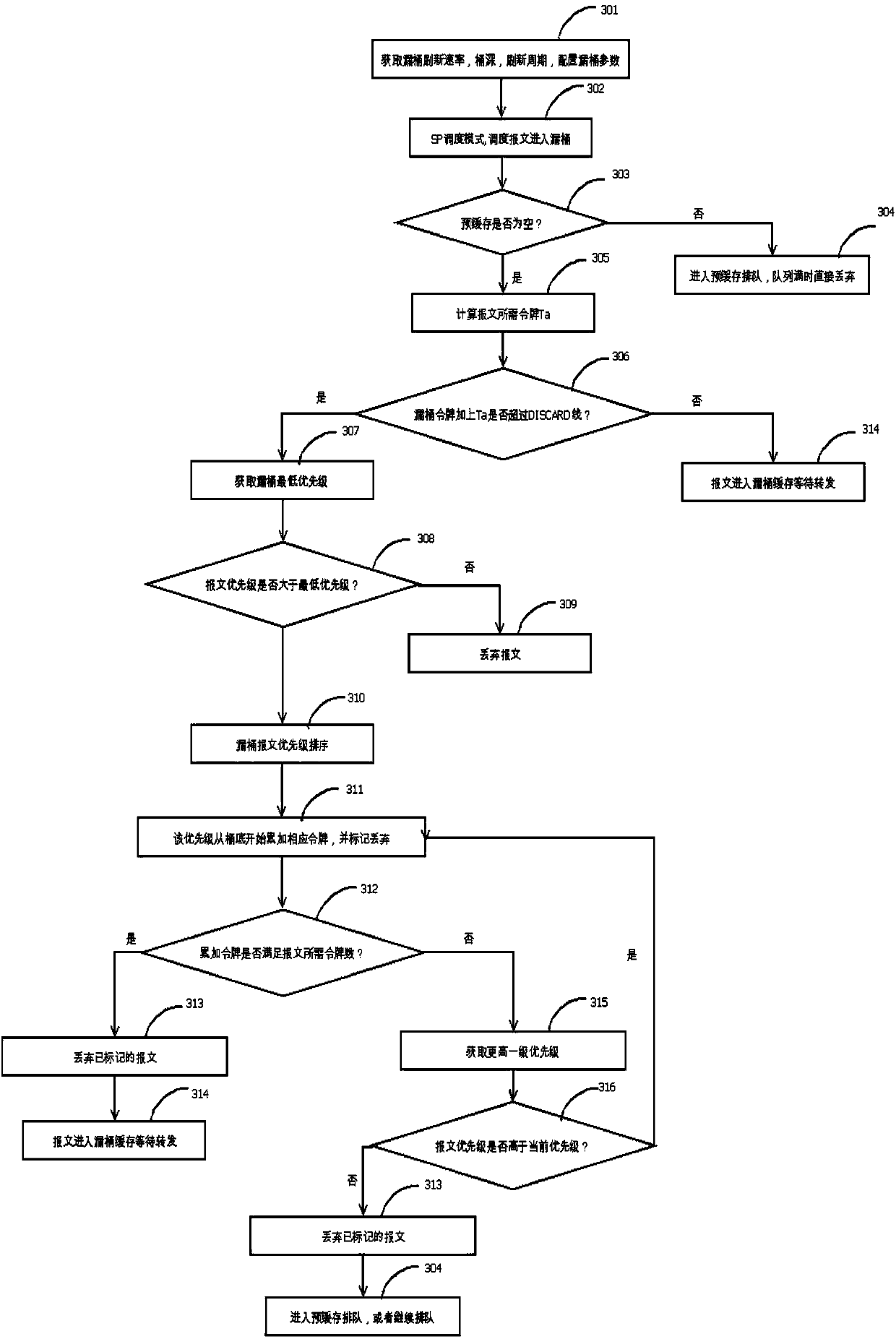
[0067] In this example, a message forwarding method is also provided, image 3 It is a flowchart of a message forwarding method according to an example of the present invention, such as image 3 As shown, the method includes the following processes:
[0068] Step 301: Obtain the leaky bucket refresh rate V, bucket depth B, refresh cycle t, and configure leaky bucket parameters. Computes the refresh token T for one refresh interval. Pre-buffer Bp.
[0069] Step 302: In SP scheduling mode, the high-priority queue buffer is not empty, and the scheduling message enters the next leaky bucket process.
[0070] Step 303: Determine whether the pre-buffer is empty? When the pre-buffer is not empty, go to step 304; if the pre-buffer is empty, go to step 305.
[0071] Step 304: Enter the pre-buffer queue, discard the message directly when the queue is full, and wait in line when the queue is not full.
[0072] Step 305: Calculate the token Ta required by the message. Formula Ta=P-...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com