UNP (Universal Network Passport) tunnel secure sharing method and system
A security and tunneling technology, applied in the field of network communication, can solve problems such as waste of network resources, complex configuration, repeated IP address configuration conflicts, etc., to achieve the effects of improving security, realizing data isolation, and saving resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
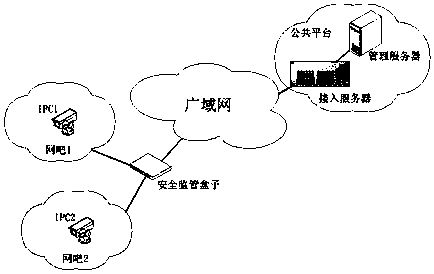
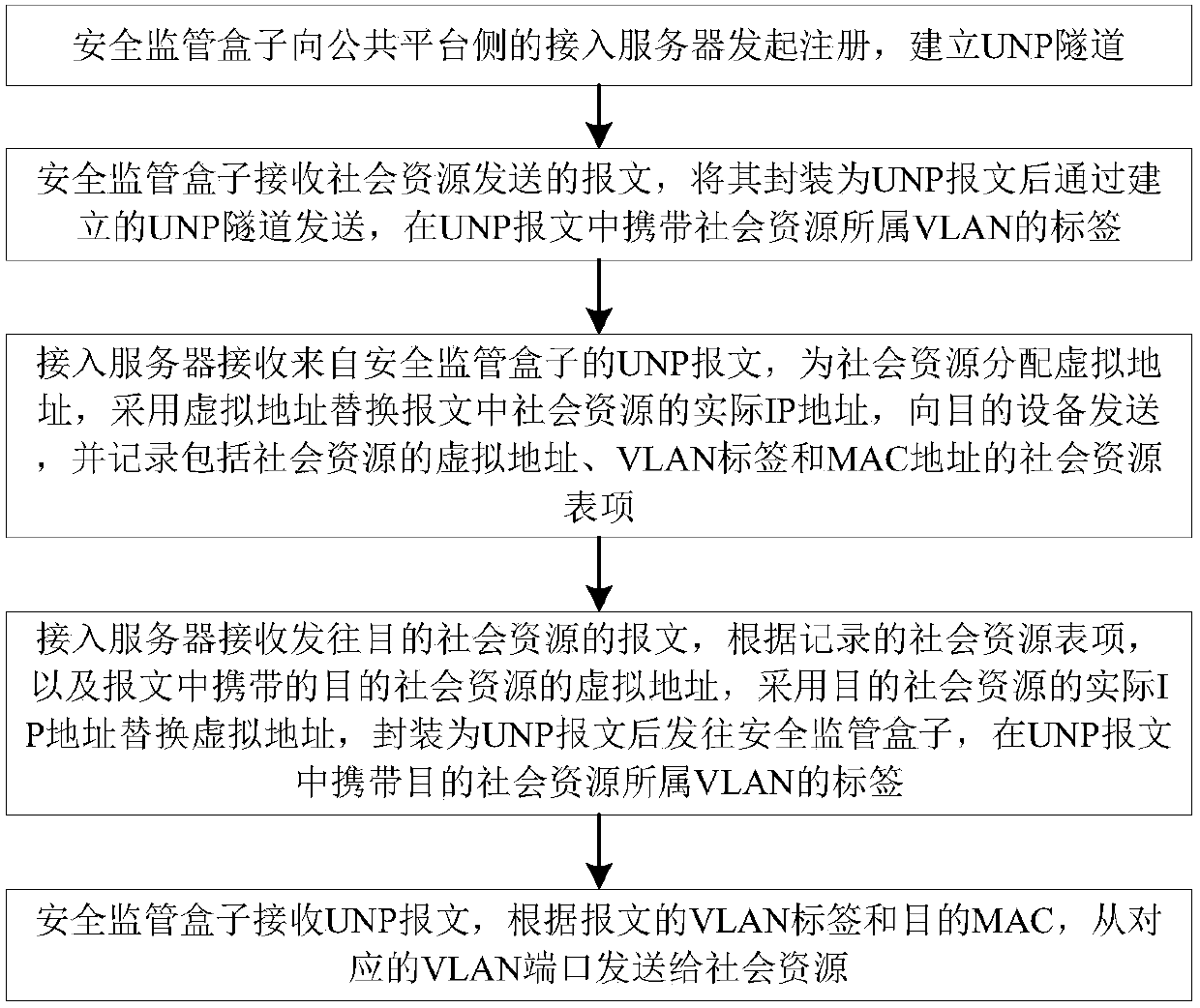
[0061] Embodiment 1. The social resource IPC sends a message to the management server of the public platform.
[0062] The access server decapsulates the UNP message from the security supervision box, restores the layer-2 message, and performs address translation, that is, changes the source IP in the layer-2 message to the virtual address corresponding to the social resource, and sends it to the management server.
[0063] The fields of the packet sent to the management server after address translation are:
[0064] The source MAC is the MAC address MAC1 of IPC1 (48:EA:63:00:11:01), and the destination MAC is the MAC address MAC100 of the management server (48:EA:63:88:88:88);
[0065] The source IP is the virtual address vIP1 (10.10.10.3) of IPC1, and the destination IP is the management server IP address IP100 (202.5.1.100).
[0066] The source IP is changed to the virtual address vIP1 (10.10.10.3) of IPC1 after address translation.
Embodiment 2
[0067] Embodiment 2. This embodiment also supports communication between social resources. The social resource sending the message is called the first social resource, and the destination device is called the second social resource. For example, in the communication between IPC1 and IPC2, IPC1 sends a message to IPC2, IPC1 is the first social resource, and IPC2 is the second social resource.
[0068] The IPC1 message is sent to the access server after the security monitoring box is tagged with VLAN10, and the access server assigns a virtual address vIP1 (10.10.10.3) to IPC1; similarly, the message sent by IPC2 is tagged with the VLAN20 tag on the security monitoring box Send it to the access server, and the access server assigns the virtual address vIP2 (10.10.10.4) to IPC2.
[0069] When the packet sent from IPC1 to IPC2 passes through the access server, the following address translation is performed:
[0070] The access server decapsulates the UNP message from the security ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com