Authority authentication method, encryption method, device and system for network video access
A technology of network video and encryption algorithm, applied in the field of Internet video information, can solve problems such as security risks, achieve the effect of ensuring security and improving user experience
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
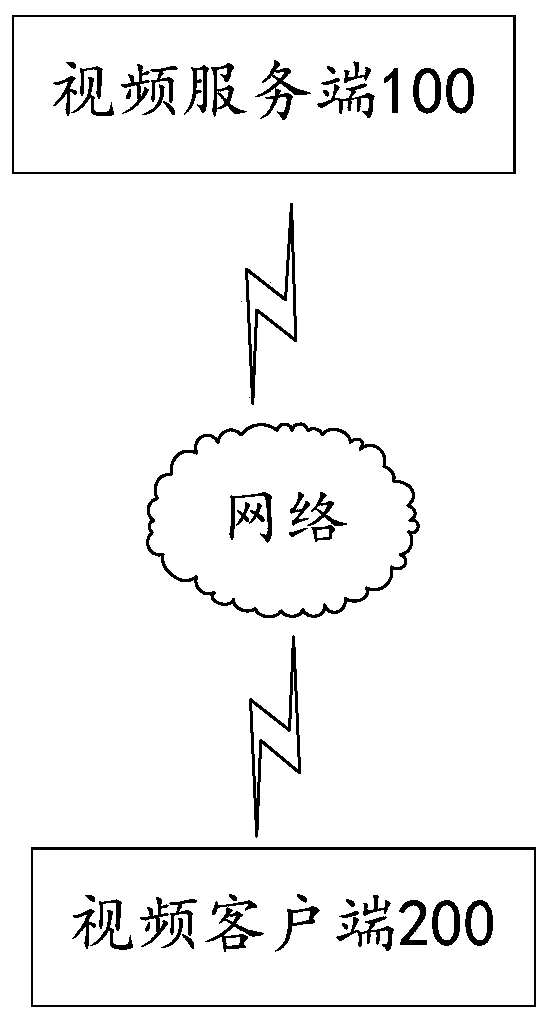
[0050] The embodiment of the present invention provides a network video access authentication method, which is applied to the video server 100. The video server 100 can provide video services for the video client 200. The video client 200 can be used by the user and can communicate with the video The communication device with which the server 100 establishes a connection, such as a personal computer, a mobile phone, a tablet computer, and the like. When the user needs the video service end 100 to provide video services when using the video client 200, different video client 200 users can have personalized services, and realize the authority identification to the video client 200 by the video server 100 to determine the video client. Whether the terminal 200 has the correct access rights. Such as figure 1 As shown, it is a schematic diagram of the interaction between the video client 200 and the video server 100 .
[0051] Such as figure 2 As shown, the authorization method...
no. 2 example
[0099] The authorization authentication method for network video access described above is an authentication method applied to the video server 100, and the corresponding video client 200 also needs to encrypt the authorization information. The embodiment of the present invention also provides a permission encryption method, which is applied to the video client 200, such as Figure 4 As shown, the method includes the following steps.
[0100] Step S201, determine at least one encryption algorithm and at least one encryption key corresponding to the permission information according to preset rules.
[0101] As mentioned above, when the video client 200 sends a video service request to the video server 100 , the permission information corresponding to the video client 200 may be sent to the video server 100 . And the permission information sent is encrypted.
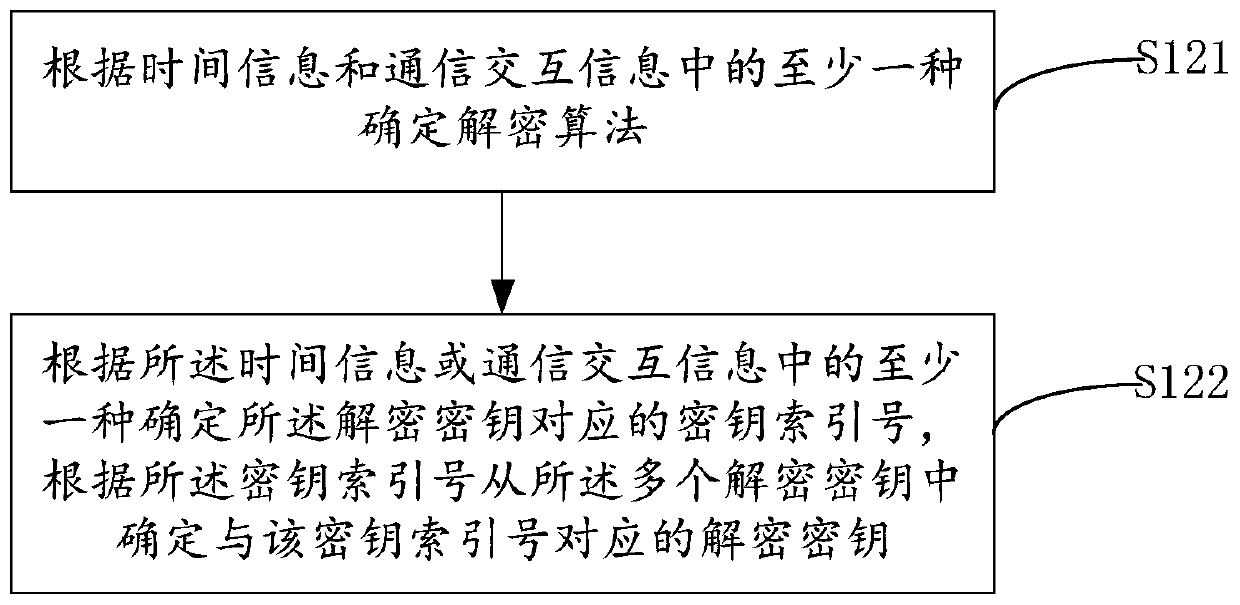
[0102] In detail, the video client 200 is configured with multiple encryption algorithms and multiple encryption keys,...
no. 3 example
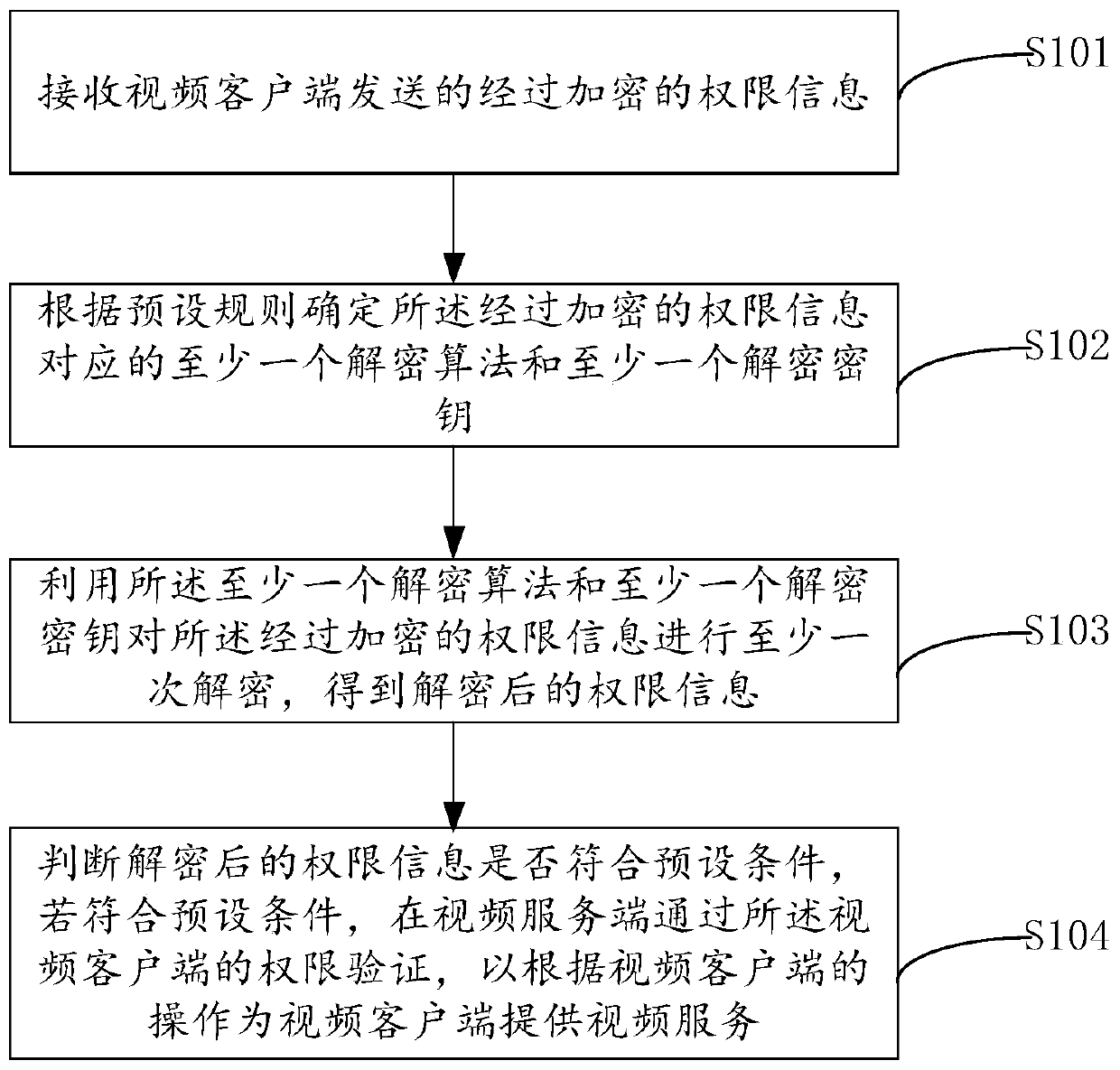
[0137] The embodiment of the present invention also provides a permission identification device 10, which is applied to the video server 100, such as Figure 6 As shown, the authority authentication device 10 includes an information acquisition module 101 , a decryption algorithm and key determination module 102 , a decryption module 103 and an authentication module 104 .
[0138] An information acquisition module 101, configured to receive encrypted permission information sent by the video client 200;
[0139] Decryption algorithm and key determination module 102, configured to determine at least one decryption algorithm and at least one decryption key corresponding to the encrypted permission information according to preset rules;
[0140] A decryption module 103, configured to decrypt the encrypted permission information at least once by using the at least one decryption algorithm and at least one decryption key to obtain decrypted permission information;
[0141] The iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com