Network security protection method and system based on IP address security credibility
An IP address and network security technology, applied in the field of network security protection based on IP address security reputation, can solve problems such as no solution proposed, the server cannot make adaptive adjustments, and it has nothing to do with the actual operating status of the server.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
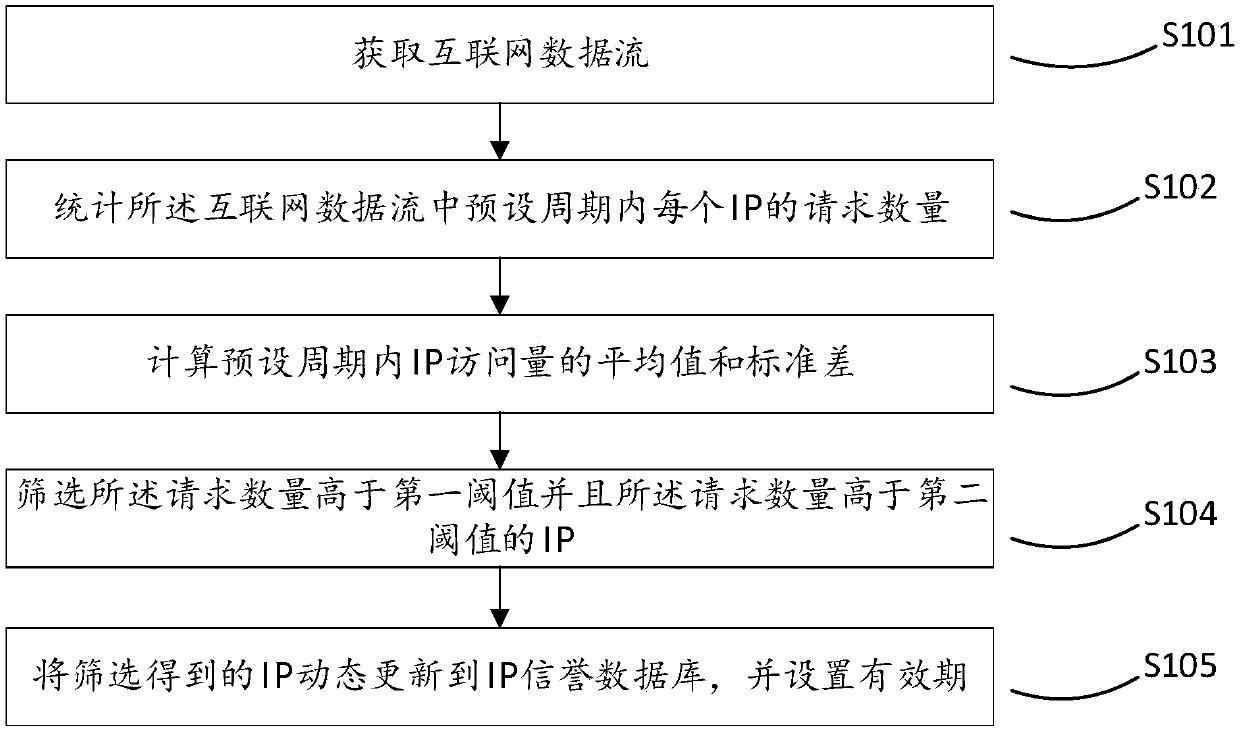
[0057] This embodiment proposes a method for determining the security reputation of a network IP address, such as figure 1 As shown, the method includes the following steps:
[0058] Step S101, counting the number of requests for each IP within a preset period.
[0059] Step S102, calculating the average value and standard deviation of IP visits within a preset period.
[0060] Step S103, screening IPs whose request quantity is higher than a first threshold and whose request quantity is higher than a second threshold, and the second threshold is related to the average value and standard deviation.
[0061] Step S104, dynamically update the filtered IP to the database, and set a valid period.
[0062] In step S101 and step S102, the preset period is the segmentation of the processing sequence. For example, in the specific implementation process, the preset period can be 1 minute, then step S101 is to count the number of requests for each IP within 1 minute , and step S102 al...
Embodiment 2
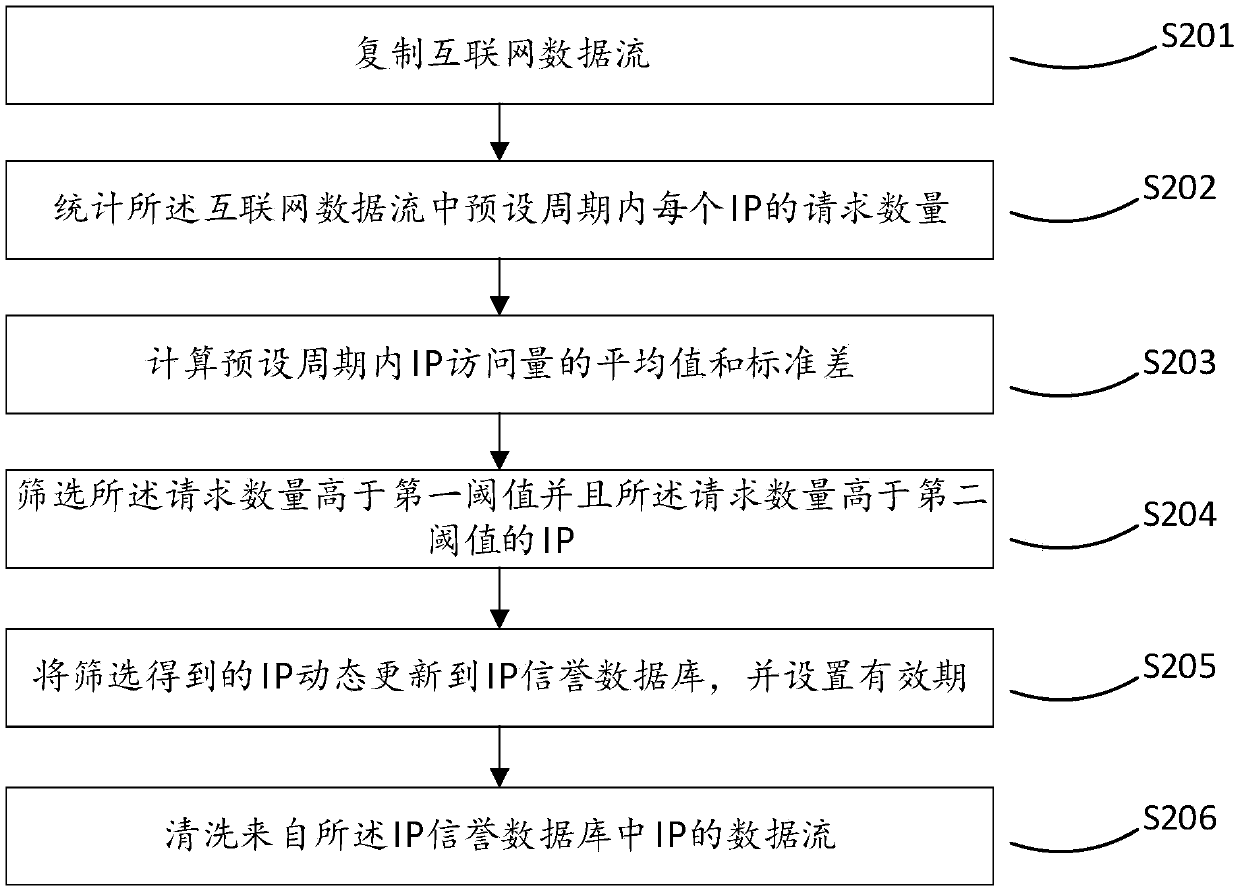
[0074] This embodiment proposes a network security protection method based on the network IP address security reputation, such as figure 2 As shown, the method includes the following steps:
[0075] Step S201, copying Internet data streams.
[0076] Step S202, counting the number of requests for each IP within a preset period in the Internet data stream.
[0077] Step S203, calculating the average value and standard deviation of IP visits within a preset period.
[0078] Step S204, screening IPs whose request quantity is higher than a first threshold and whose request quantity is higher than a second threshold, and the second threshold is determined by the average value and standard deviation.
[0079] Step S205, dynamically update the screened IP to the IP reputation database, and set a validity period.
[0080] Step S206, based on the IP reputation database, clean or intercept the IP data flow in the IP reputation database.
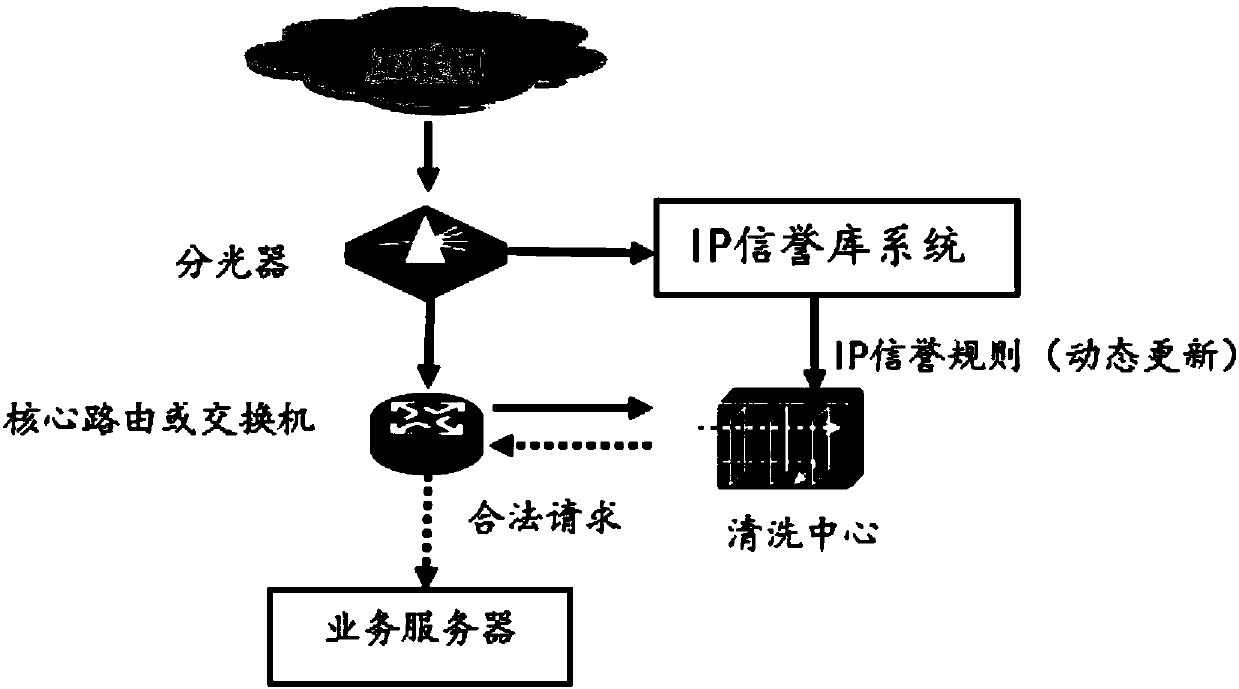
[0081] In order to realize the interaction o...
Embodiment 3
[0098] This embodiment proposes a system for determining the security reputation of a network IP address, and the system includes the following modules:
[0099] The traffic statistics module is used to count the number of requests for each IP within a preset period.
[0100] The calculation module is used to calculate the average value and standard deviation of IP visits within a preset period.
[0101] The abnormal IP screening module is configured to screen IPs whose number of requests is higher than a first threshold and whose number of requests is higher than a second threshold, and the second threshold is related to the average value and standard deviation.
[0102] The dynamic IP credit library module dynamically updates the filtered IP to the database and sets the validity period.
[0103] In a specific implementation process, the traffic statistics module extracts the IP protocol header, and counts the number of requests for each IP within the period according to a s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com