Locked resource configuration method based on shared storage
A technology of shared storage and configuration method, applied in the field of cloud storage virtualization, can solve the problems of inability to remove the mapping table, failure to release resources, affecting user experience, etc., to achieve the effect of improving high availability and stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention will be described in detail below in conjunction with the implementations shown in the drawings, but it should be noted that these implementations are not limitations of the present invention, and those of ordinary skill in the art based on the functions, methods, or structural changes made by these implementations Equivalent transformations or substitutions all fall within the protection scope of the present invention.
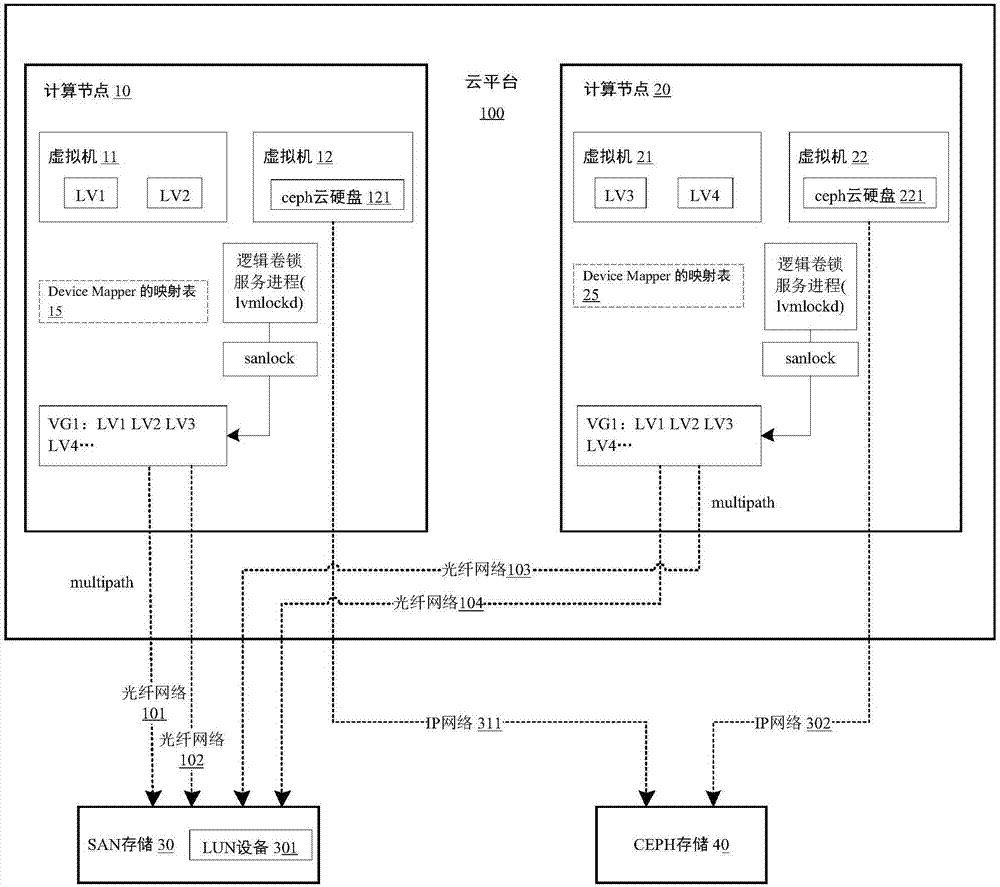
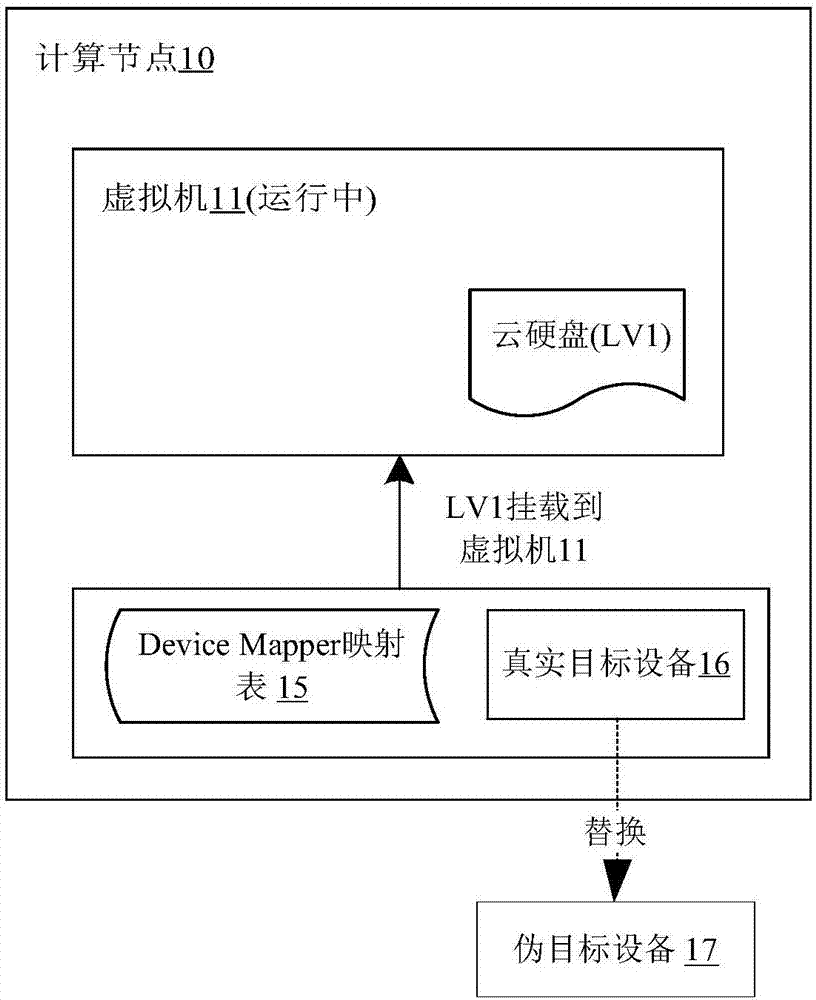
[0033] Before elaborating the specific implementation process of the present invention in detail, the names of proprietary technologies involved in the description are defined and explained.
[0034] 1. sanlock: lock service based on shared storage.
[0035] 2. LVM: Logical Volume Manager, Logical Volume Manager.
[0036] 3. Watchdog: Watchdog program for Linux system.
[0037] 4. lvmlockd: LVM lock service component, which calls sanlock service through lvmlockd.
[0038] 5. VG: Volume Group volume group.
[0039] 6. PV: Physi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com