Patents
Literature
32 results about "Device mapper" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
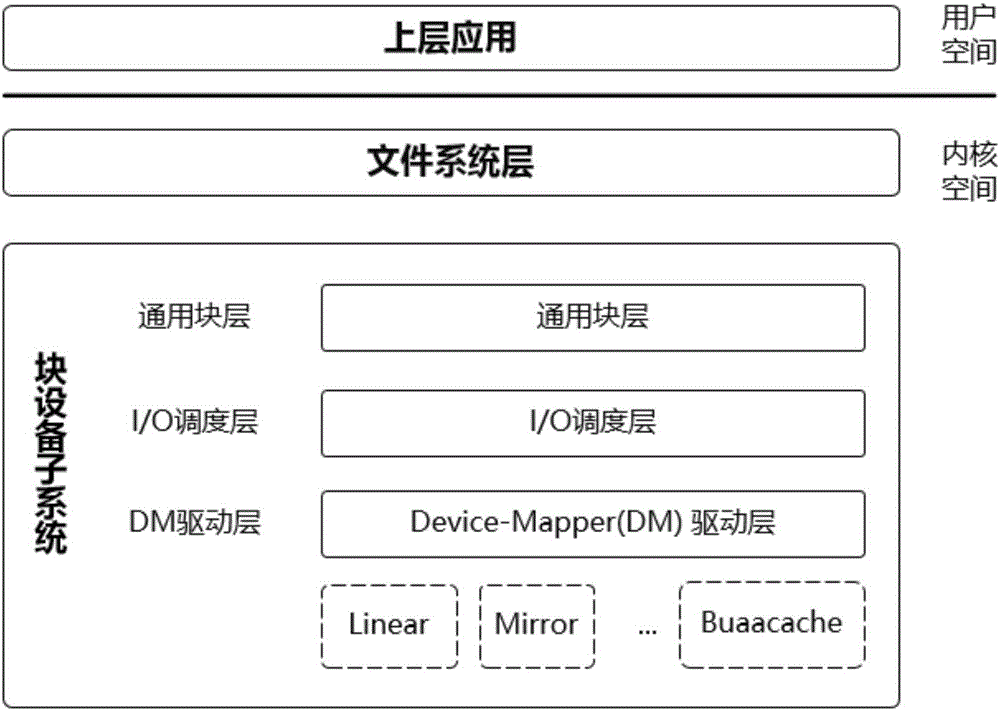
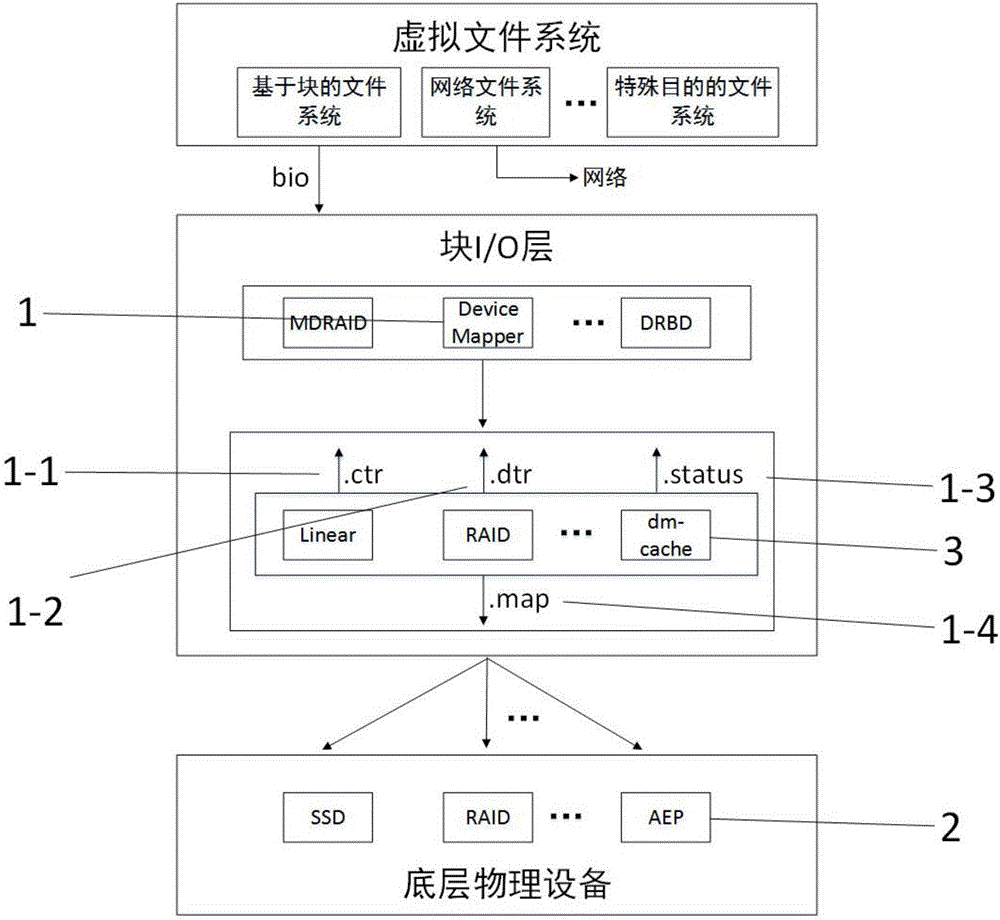
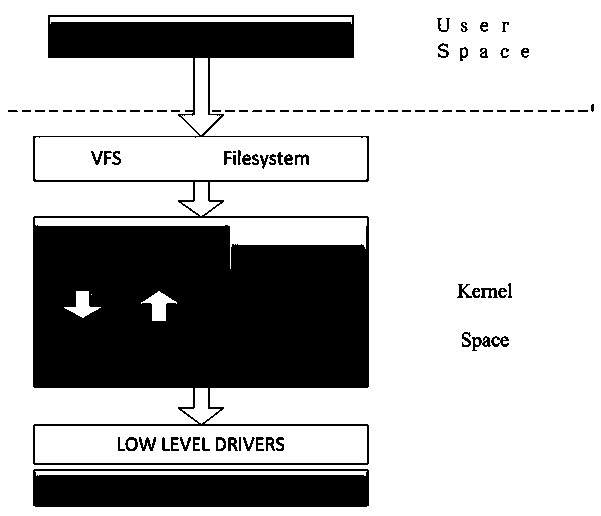
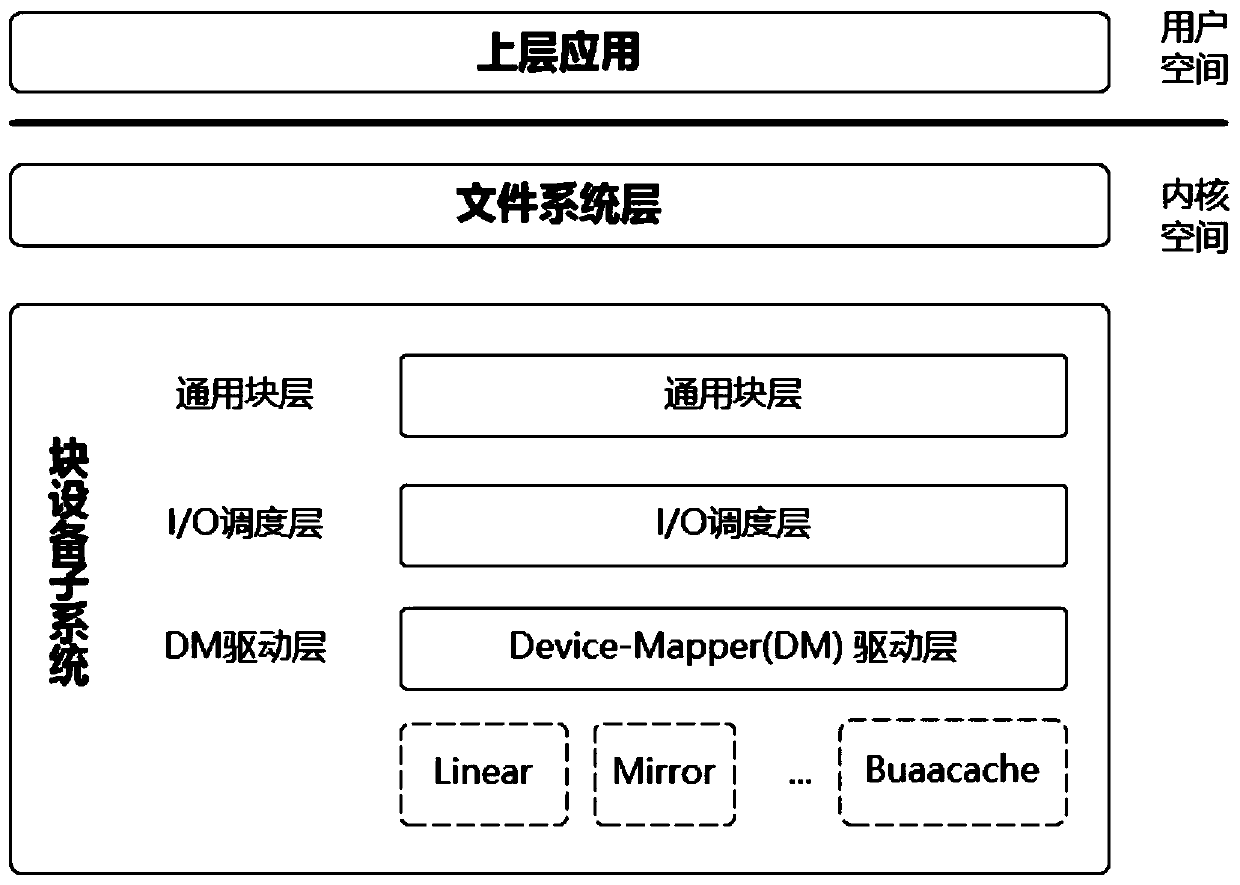
The device mapper is a framework provided by the Linux kernel for mapping physical block devices onto higher-level virtual block devices. It forms the foundation of the logical volume manager (LVM), software RAIDs and dm-crypt disk encryption, and offers additional features such as file system snapshots.
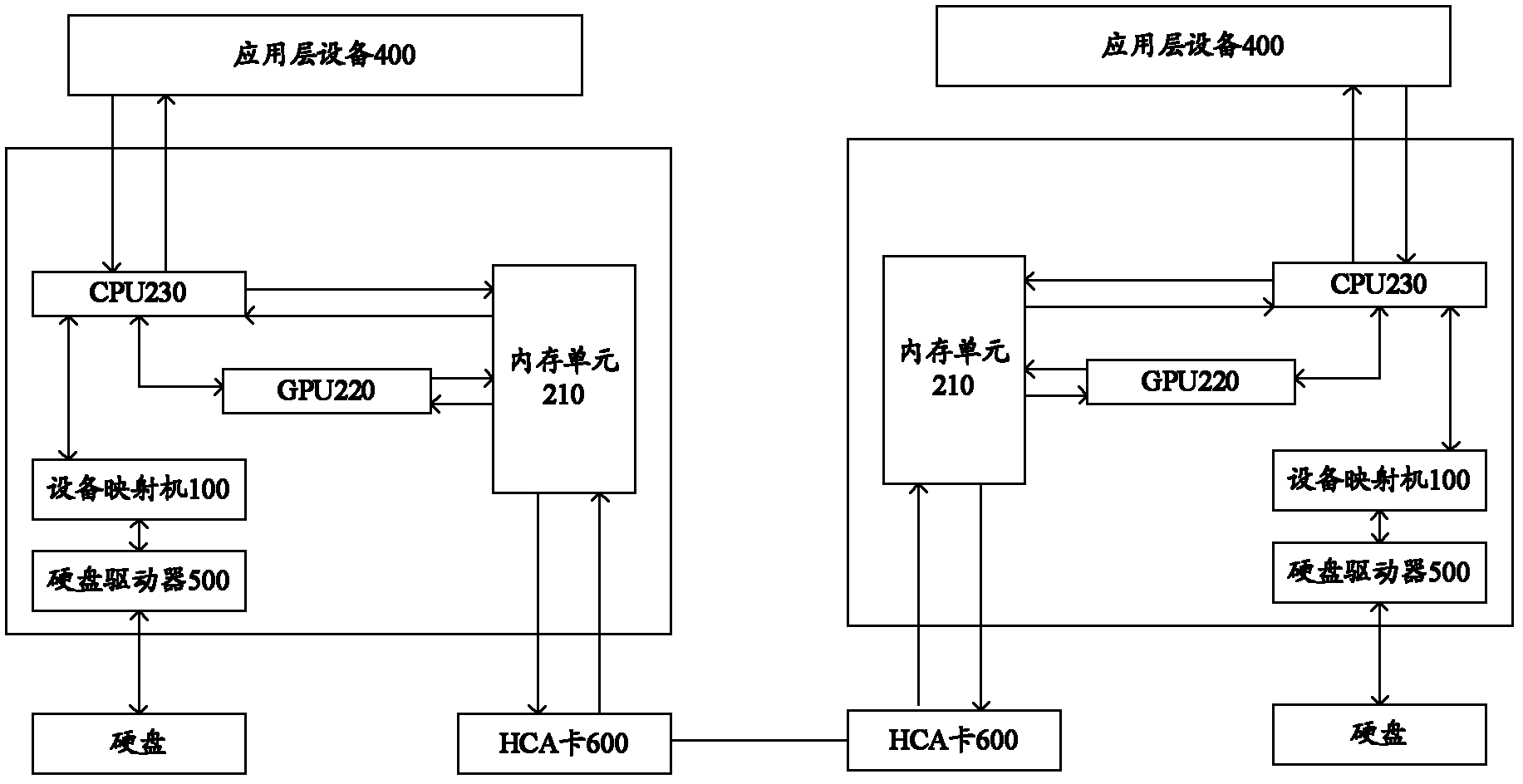
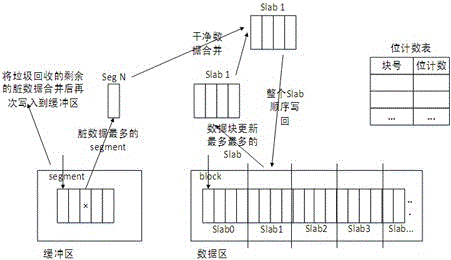
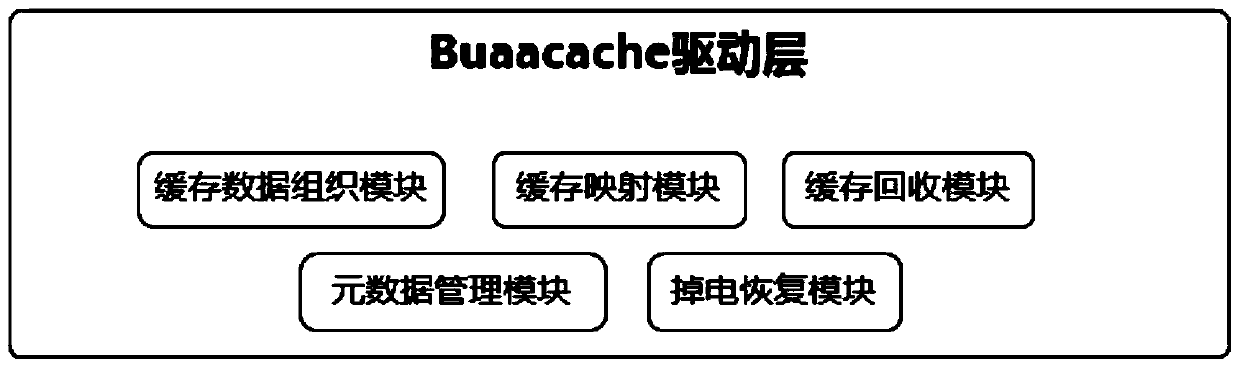
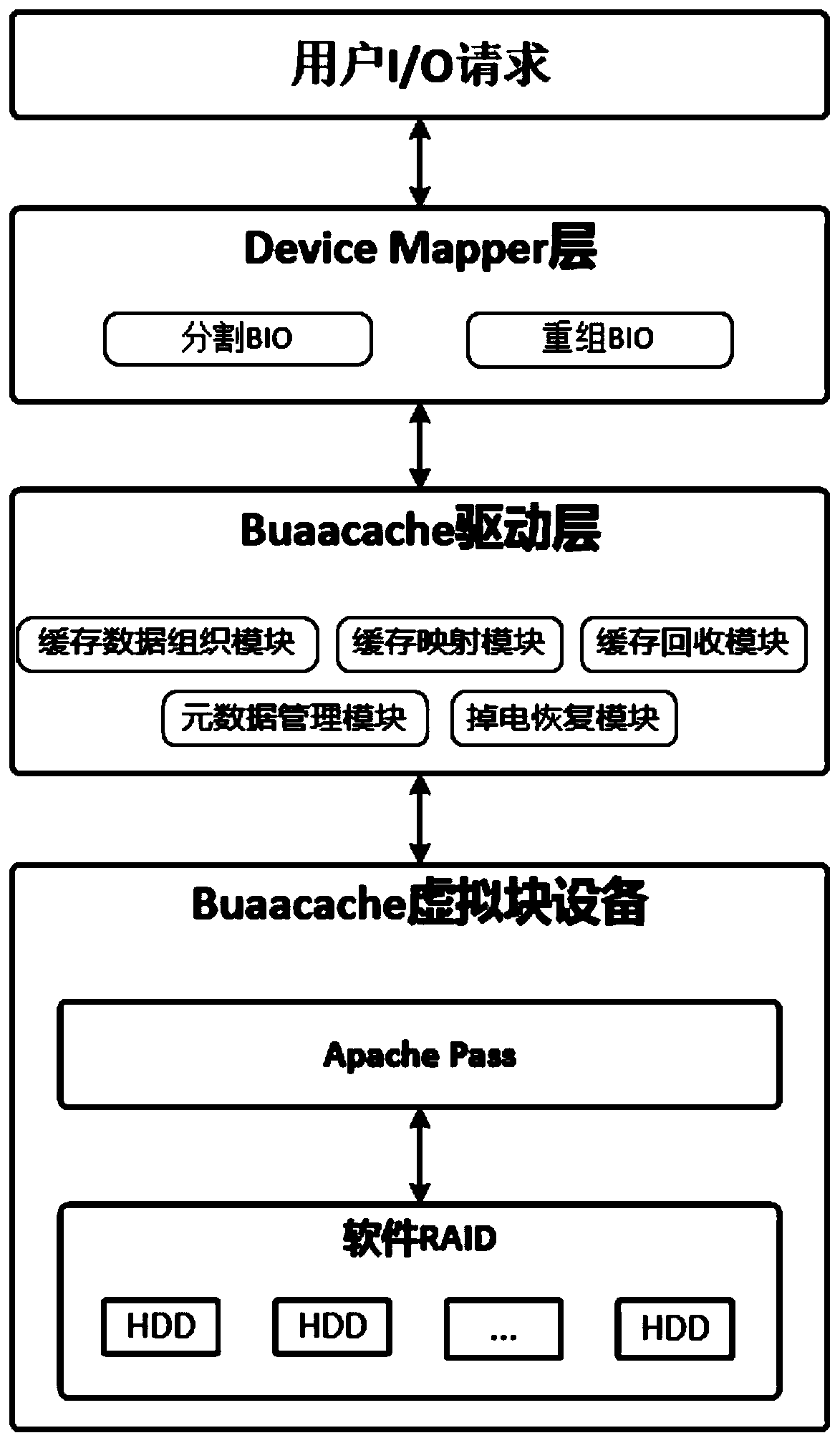
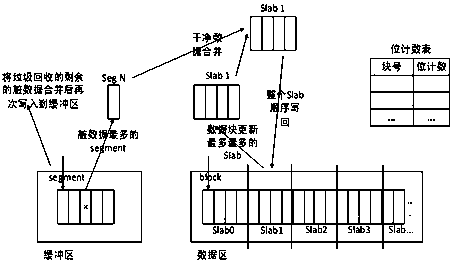
Cache system based on nonvolatile memory and software RAID
ActiveCN106528001AAvoid multiple visitsShorter read and write timesInput/output to record carriersRAIDGNU/Linux
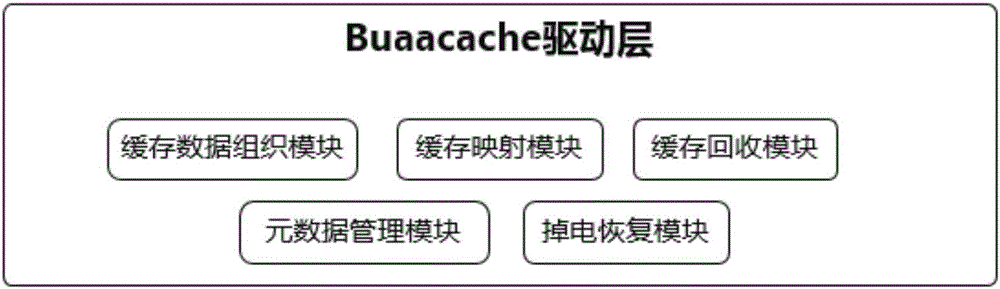
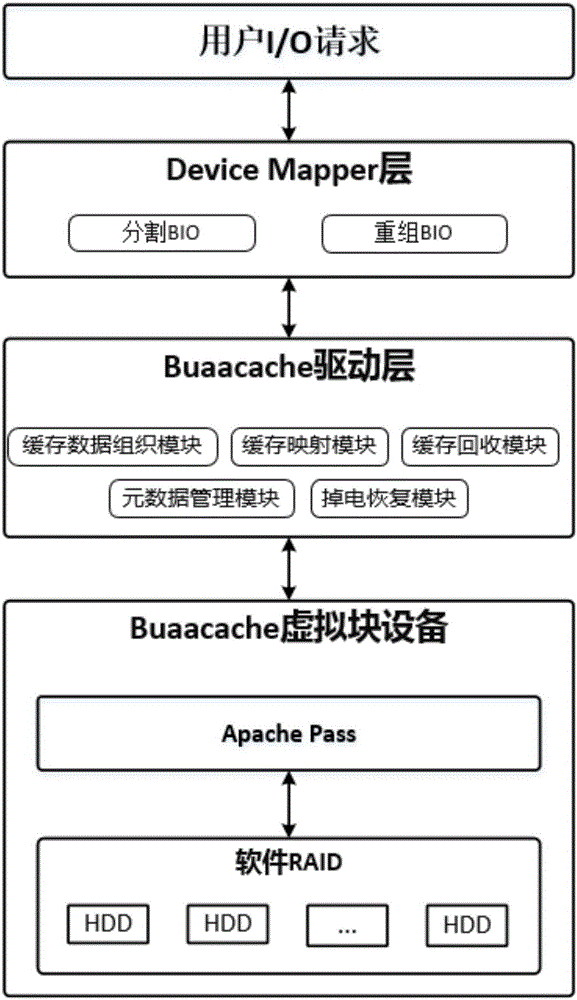
The invention provides a cache system based on a nonvolatile memory and a software RAID. The cache system is characterized in that the cache system is a novel storage system architecture by fusing a nonvolatile memory Apache Pass, a software RAID, and a Device Mapper driving module Buaacache. According to the invention, the software RAID is managed by means of the Device Mapper mechanism of the Linux, a high-speed device Apache Pass serves as the Cache of a low-speed RAID, and therefore a two-stage cache system is constructed. The Persistent Memory is characterized in that after the Persistent Memory is powered off, medium data is not lost, and the read-write performance is excellent. According to the invention, the Persistent Memory is selected as the cache of the software RAID, under the condition that the cost is far lower than that of a hardware RAID, the read-write performance of the software RAID approaches even exceeds the hardware RAID.
Owner:BEIHANG UNIV
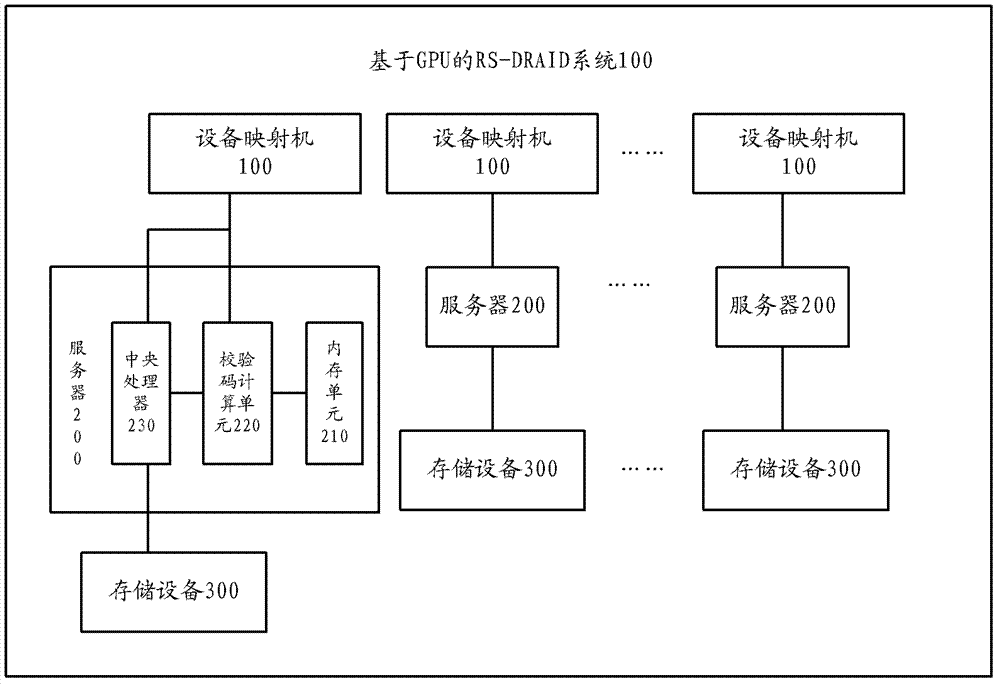
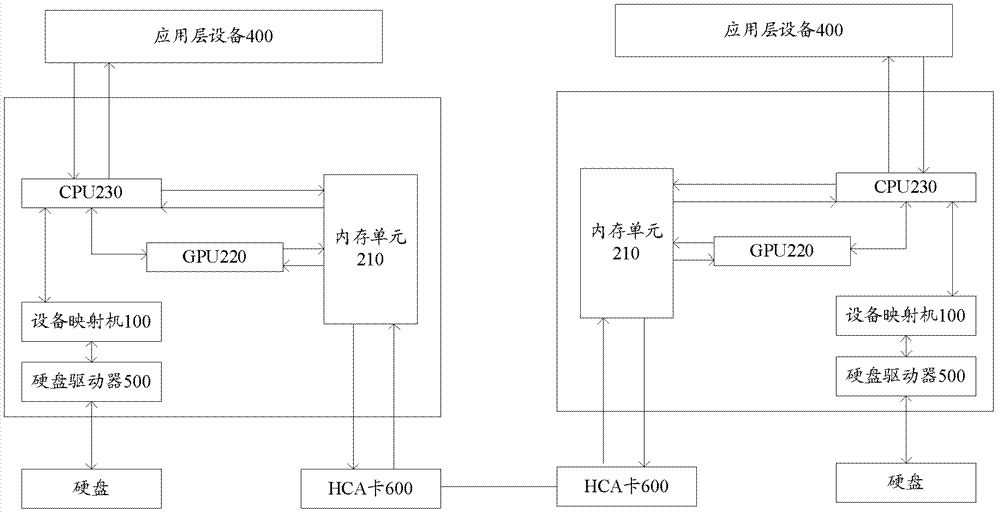
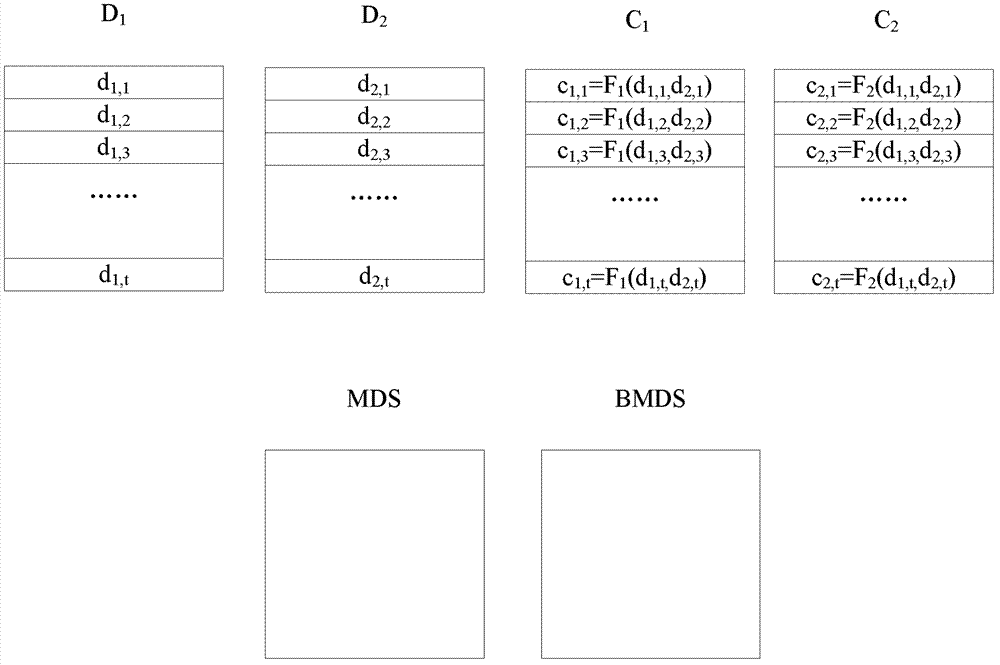
RS (Reed-Solomon) - DRAID( D redundant array of independent disk) system based on GPUs (graphic processing units) and method for controlling data of memory devices
ActiveCN102520890AReduce resource utilizationImprove performanceInput/output to record carriersRedundant data error correctionInternal memoryData control
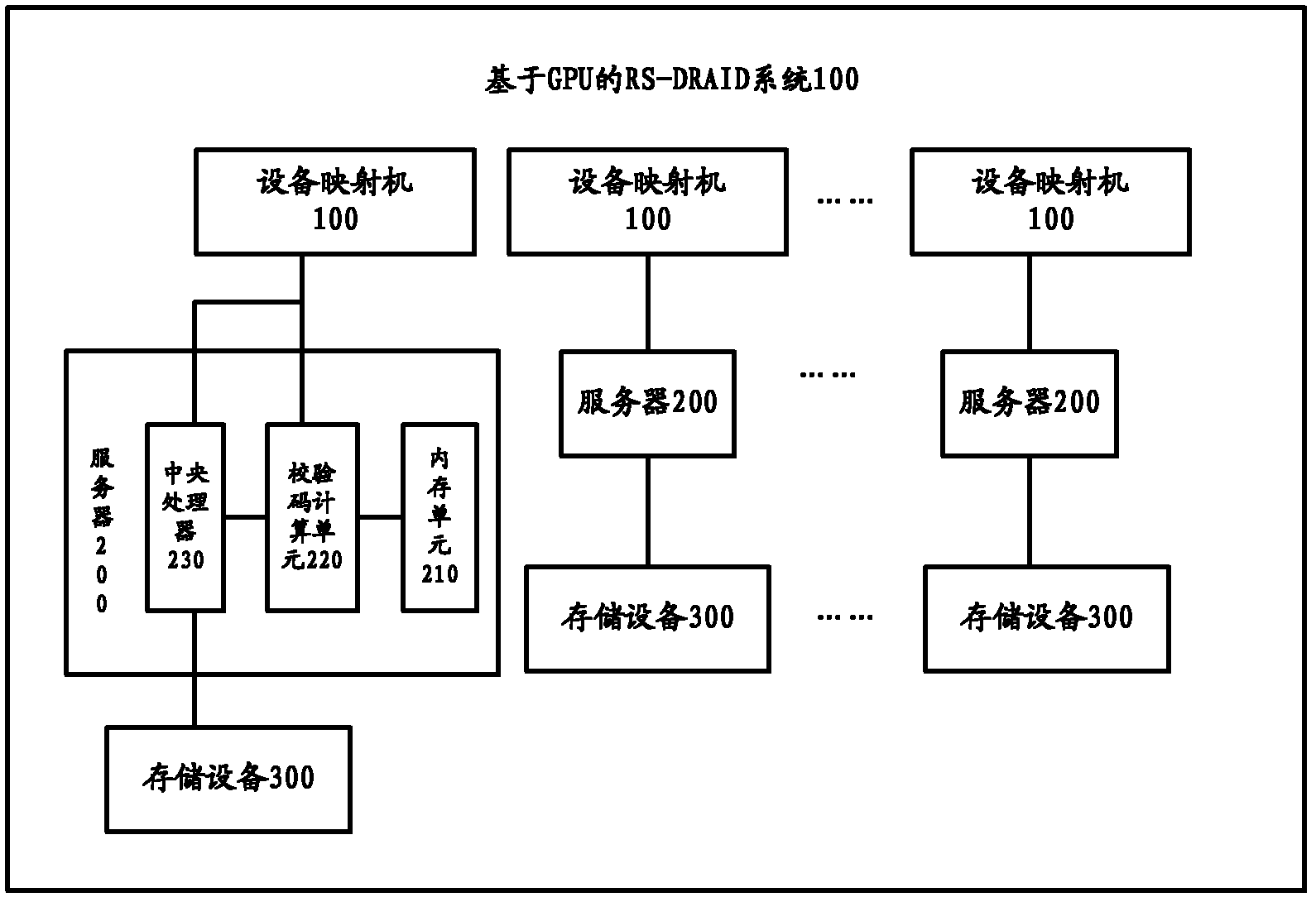
The invention provides an RS (Reed-Solomon)-DRAID (D redundant array of independent array) system based on GPUs (graphic processing units) and a method for controlling data of memory devices. The RS-DRAID system comprises a plurality of device mappers, a plurality of servers and a plurality of memory devices. The servers are used for receiving writing IO (input and output) requests, each writing IO requests into a plurality of chunks which are synchronously transmitted, the servers are used for controlling writing into the memory devices and restoring failure memory devices, each server comprises an internal memory unit and a check code computing unit, the check code computing units are used for parallelly computing check codes according to the chunks from the device mappers, the check codes are recomputed when the memory devices are failure, the recomputed check codes are written into the internal memory units to recover the failure memory devices, the check code computing units are the graphic processing units GPU, and a central processing unit CPU is used for controlling data written into the memory devices. RS-DRAID algorithm is realized in a server cluster, the GPUs realize a check code parallel computing process, and service rate of the memory devices can be improved.
Owner:无锡天云数据中心科技有限公司
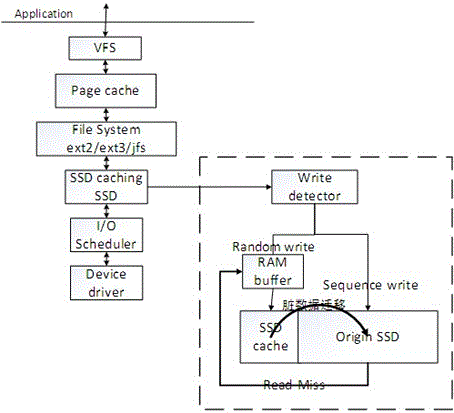
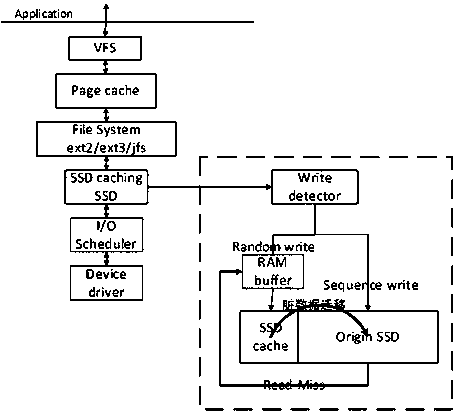
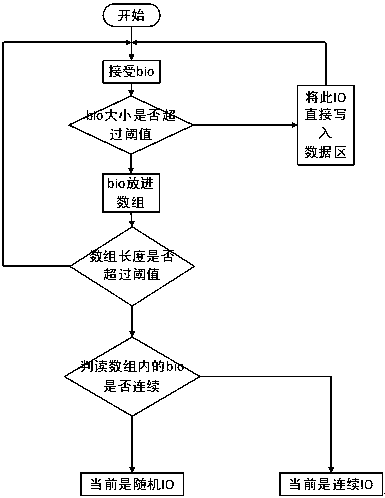
Nonvolatile cache mechanism facing SSD
ActiveCN106201916AImprove random write performanceExtend your lifeMemory adressing/allocation/relocationInterference problemDevice mapper
The invention relates to a nonvolatile cache mechanism facing SSD. The method comprises following steps: a SSD is divided into a large buffer area; small random write requests are first written in small RAM buffer; after the RAM buffer is full, those write requests are written together in the form of log into a buffer area sequentially; then data in the buffer area is written back to a data area by a backstage; in this way, the random write-in performance of SSD is effectively increased; the cache mechanism can also optimize read interference problems; the cache mechanism comprises: sequential and large I / O are filtered by an I / O detection algorithm; cache write can also be sequentially written in a data area by a garbage recovery strategy facing data area, at the same time, remaining data in the buffer area can also be written again in the cache sequentially; a read cache strategy is provided for solving the problem of SSD read interference; A SSD cache SSD system of a log structure based on device mapper is fulfilled.
Owner:NAT UNIV OF DEFENSE TECH
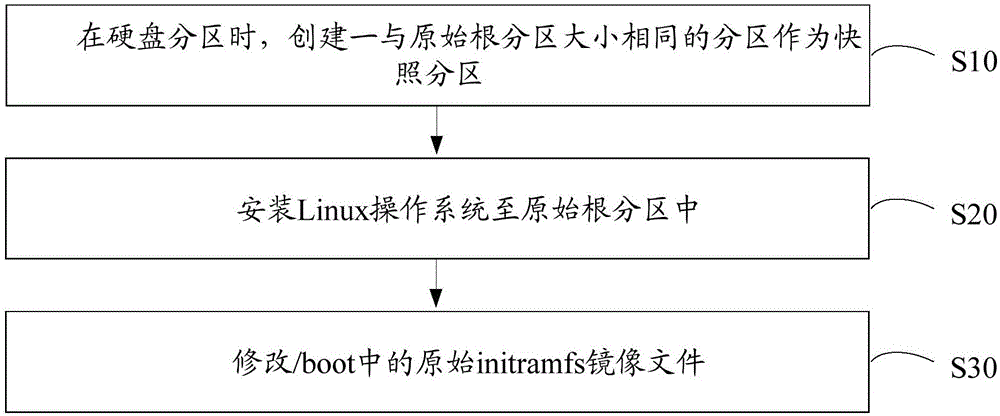
Method for ensuring normal start-up of Linux operating system
ActiveCN106776128AGuaranteed normal startupRedundant operation error correctionOperational systemGNU/Linux
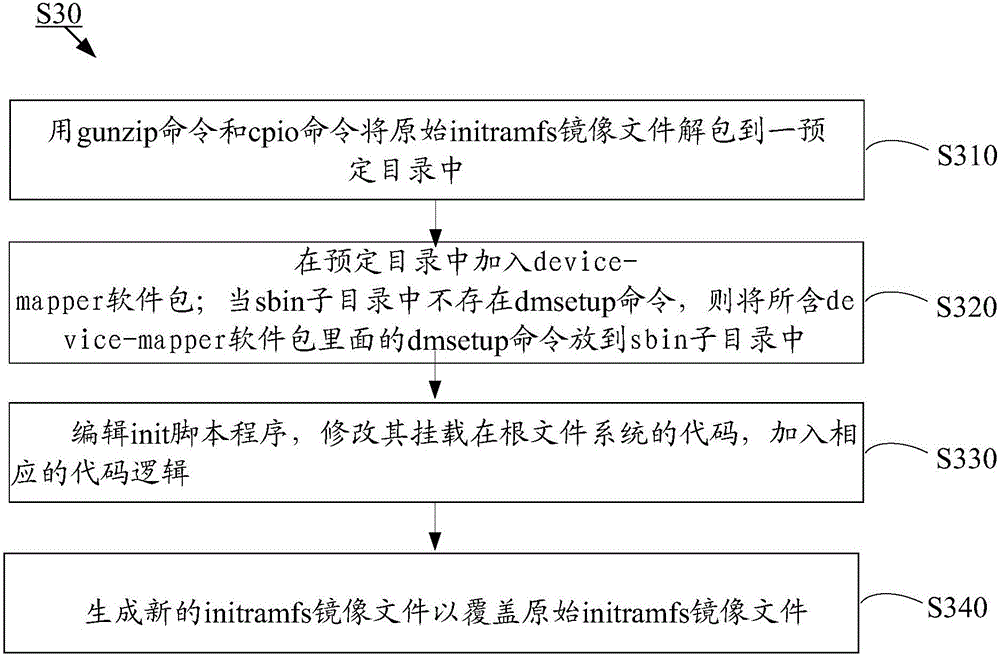
The invention discloses a method for ensuring a normal start-up of a Linux operating system. The method comprises the following steps that during hard disk partition, a partition that is the same size as an original root partition is created as a snapshot partition; the Linux operating system is installed in the original root partition; an original initramfs mirror file in / boot is modified; the steps to modify the original initramfs mirror file in the / boot comprise: using a gunzip command and a cpio command to unpack the original initramfs mirror file to a predetermined catalog; adding a device-mapping software package to the predetermined catalog; when a dmsetup command does not exist in a sbin subcatalog, the dmsetup command in the device-mapper software package is put in the sbin subcatalog; editing an init script program, modifying a code of the init script program that mounts the root file system, and adding a corresponding code logic; generating a new initramfs mirror file to overwrite the original initramfs mirror file. By adopting the method, when a file system of the hard disk is damaged, the system can be automatically restored and be started up normally without manual participation, and normal start-up of the operating system is ensured.
Owner:BANGYAN TECH
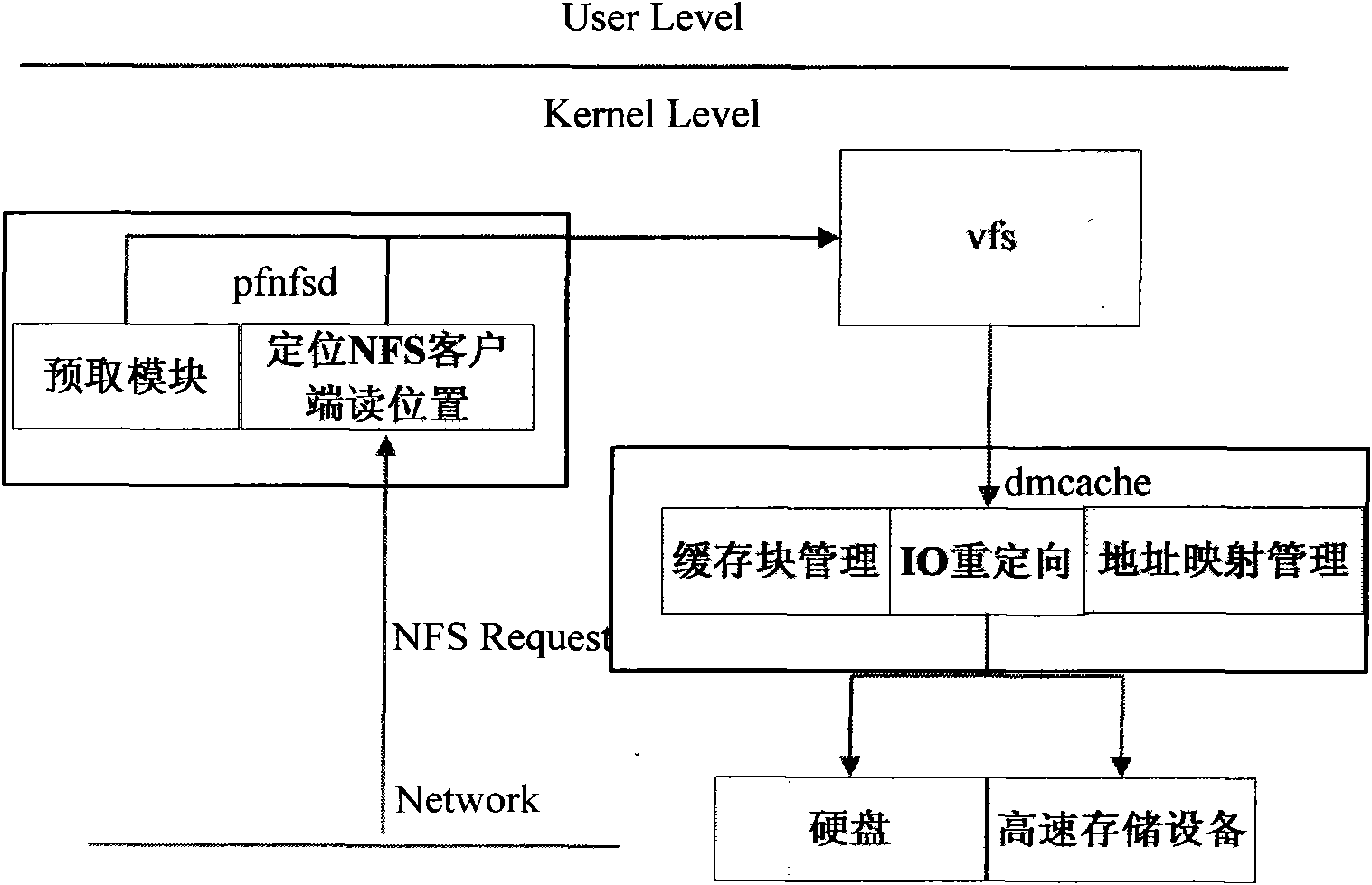
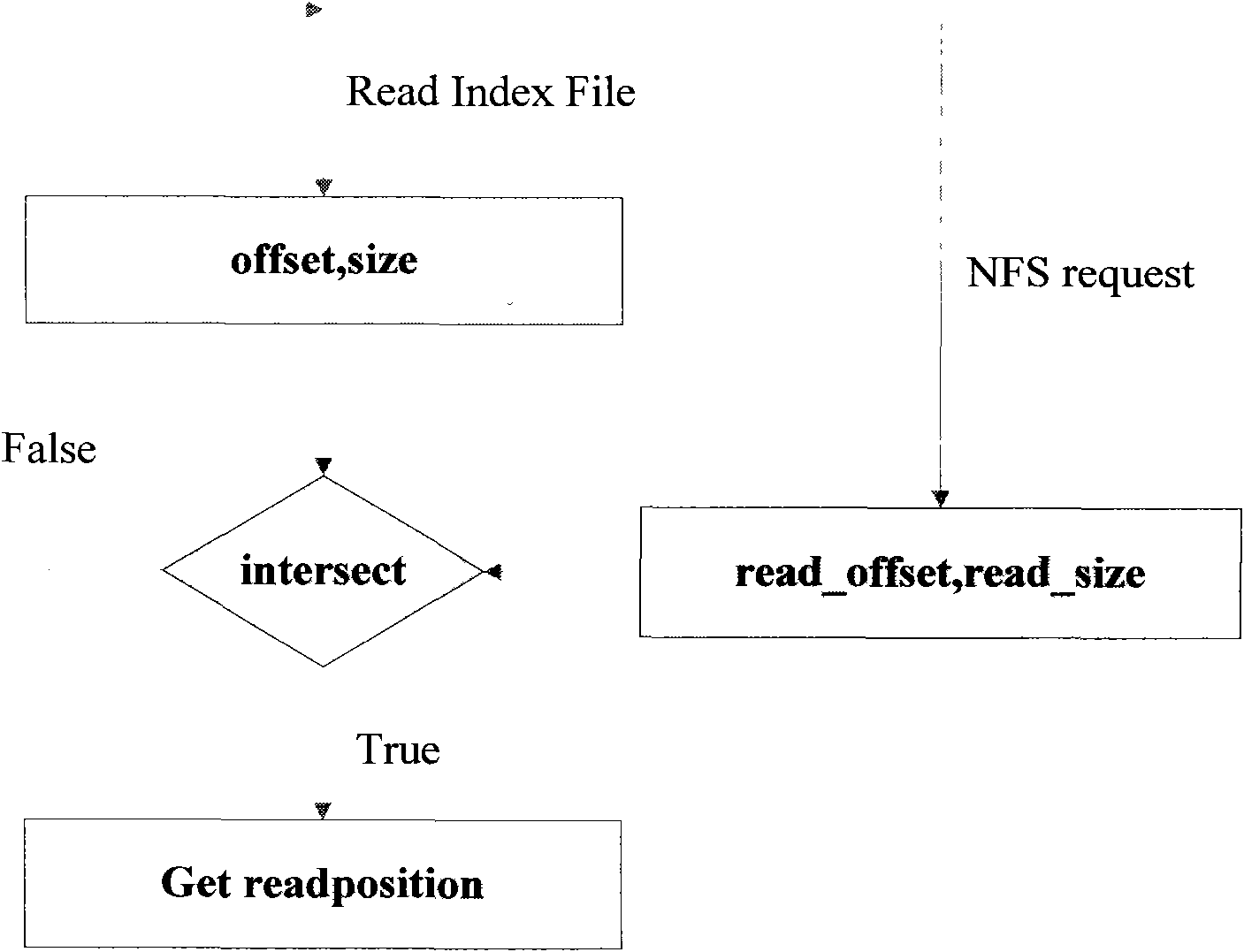
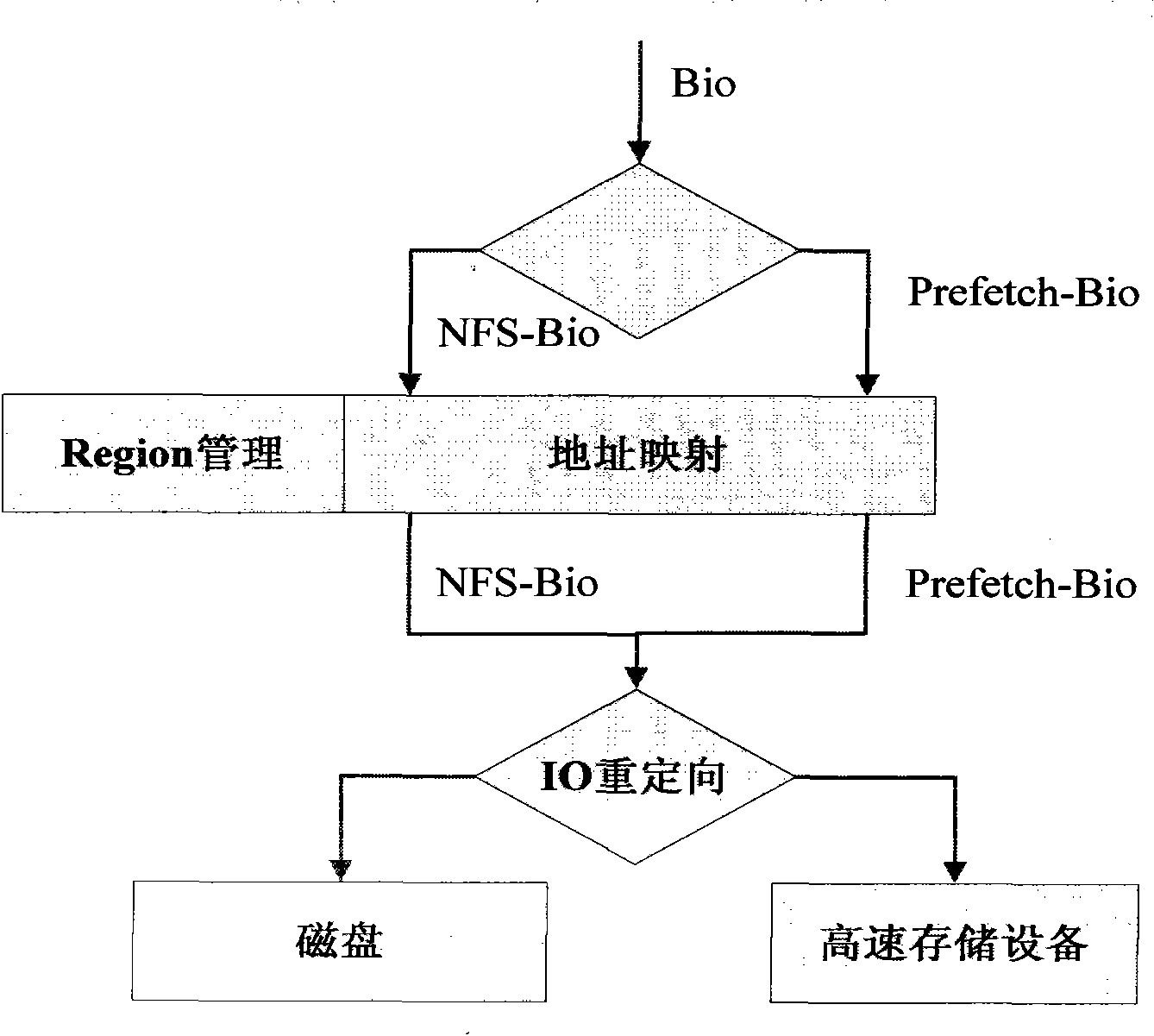
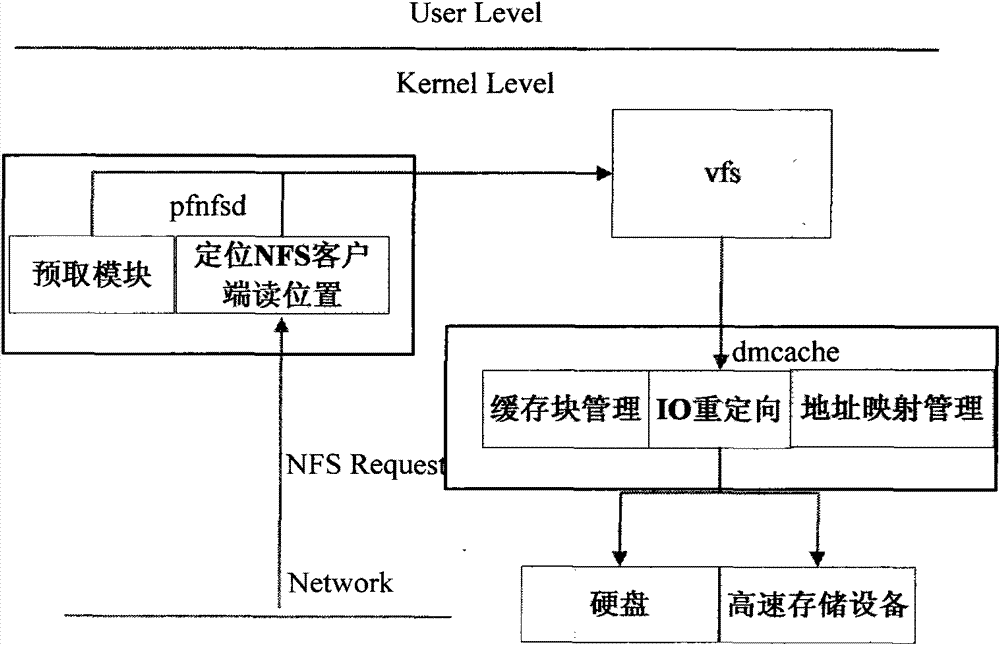
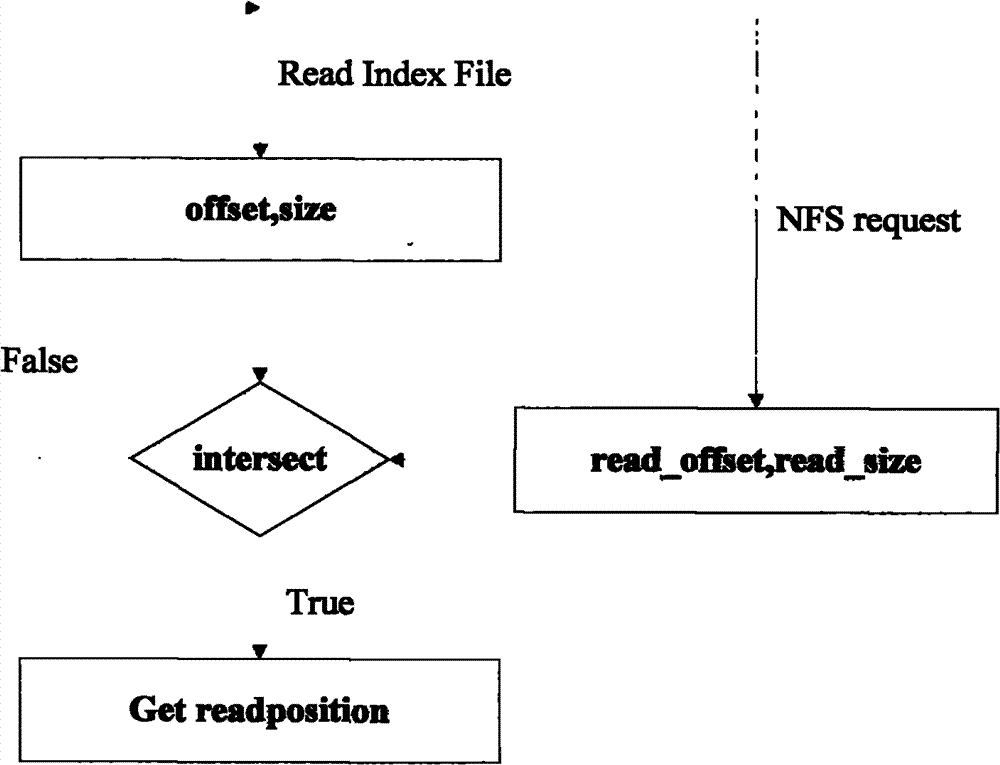
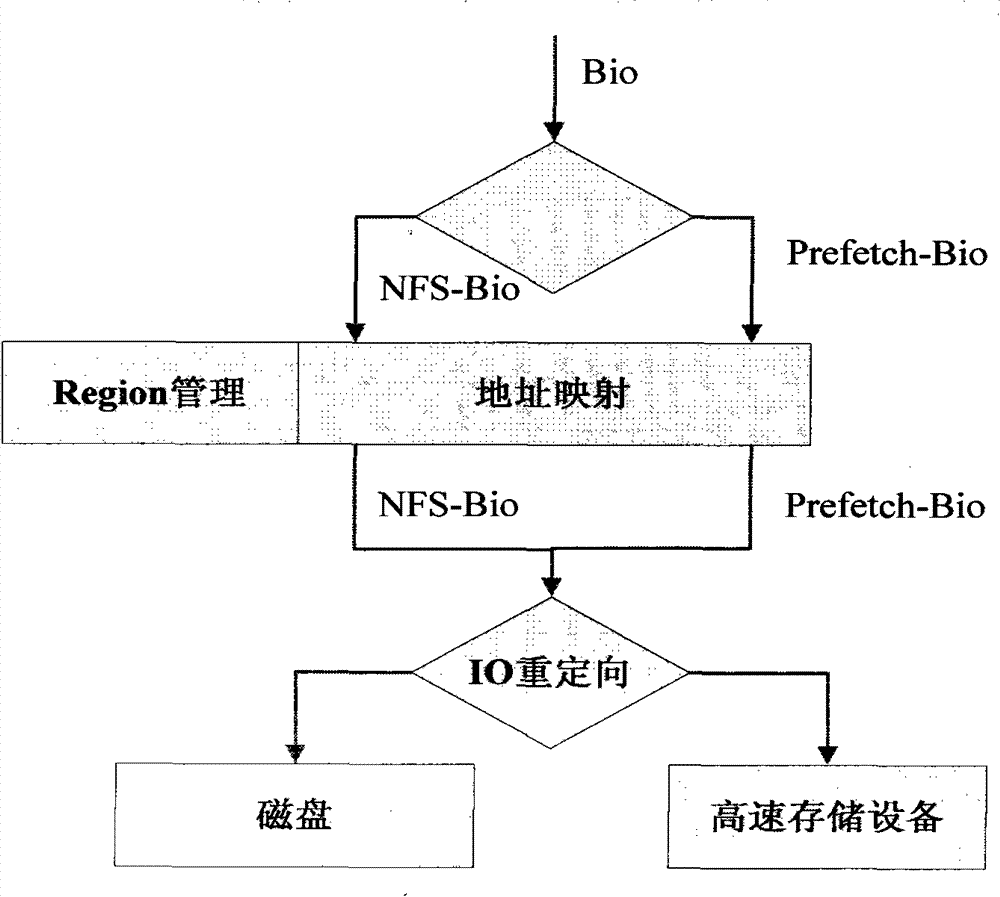
Pseudo-random type NFS application acceleration system
ActiveCN102147802ATransparency hasMinor changesSpecial data processing applicationsComputer moduleLinux kernel
The invention provides a pseudo-random type network file system (NFS) application acceleration system. The pseudo-random type NFS application acceleration system comprises two kernel modules, namely prefetch network file systemdaemon (pfnfsd) and device mapper cache (dmcache); pfnfsd is a rewrite of the kernel module nfsd, mainly comprises an NFS client request positioning module and a pre-acquiring module, and is used for capturing and positioning an NFS request of a client and executing pre-acquiring operation; and dmcache is a target driver realized on the basis of a linux kernel device mapper mechanism, mainly comprises a module for managing high-speed storage equipment, mapping an address and recycling resources, and is used for storing the pre-acquired data to the high-performance storage equipment. In the pseudo-random type NFS application acceleration system, the application is transparent, the kernel changes small and the extra high-speed storage equipment can be loaded.
Owner:DAWNING INFORMATION IND BEIJING +1
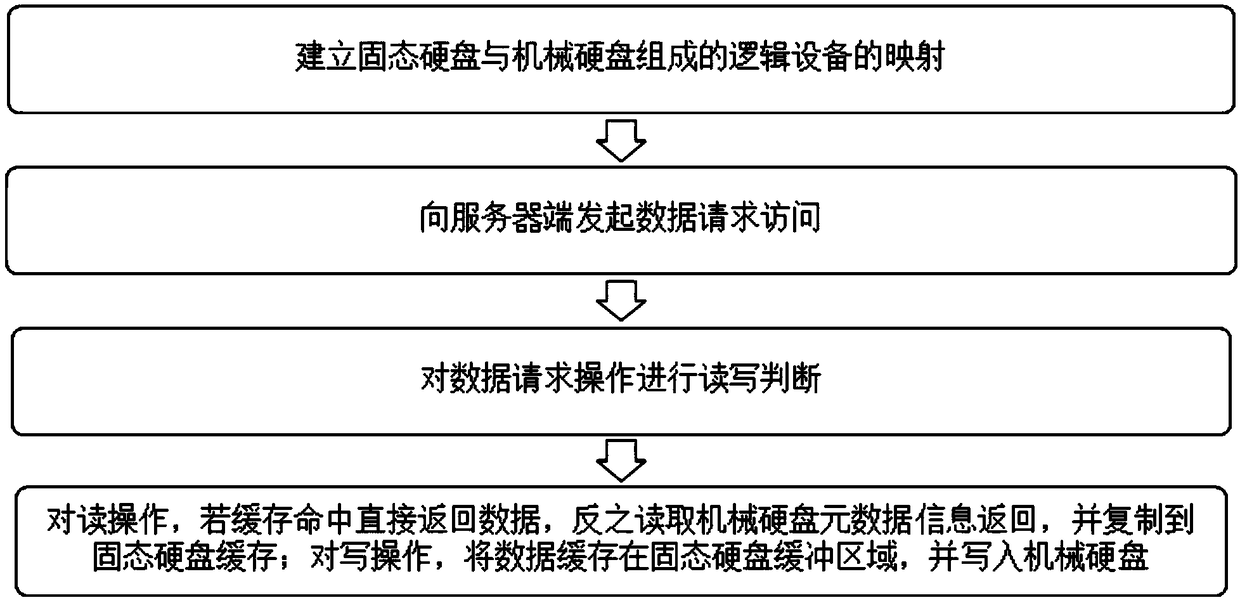
A system storage optimization method based on Device Mapper
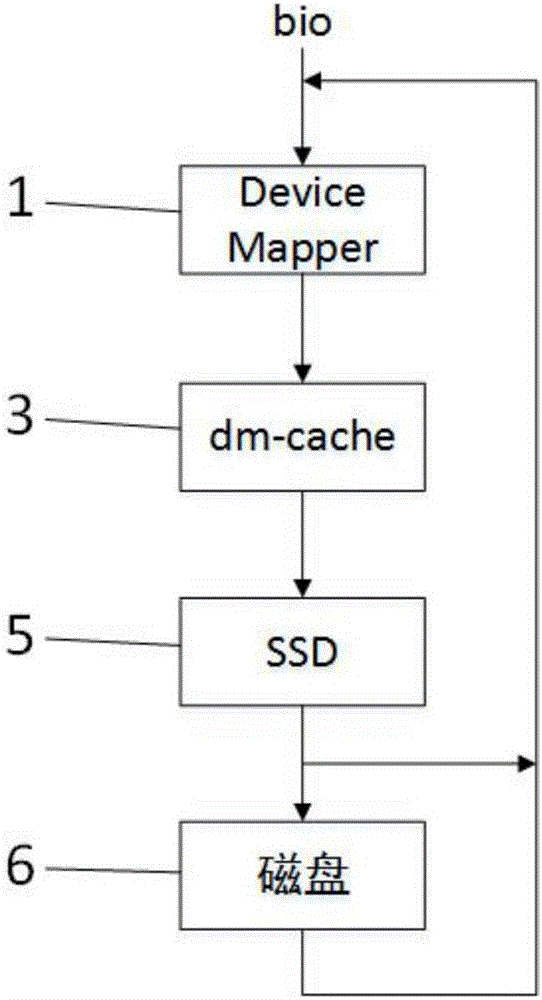
InactiveCN109388341AIncrease storage capacityReduce power consumptionInput/output to record carriersSolid-state storageDevice mapper
The invention relates to a system storage optimization method based on Device Mapper, When the client initiates the data request, the solid state storage is used as the cache of the mechanical hard disk by the Device Mapper technology. When the user space initiates the read operation, the data in the cache is searched first, if there is any, the data is returned to the user space, and if there isno data, the data is read by the mechanical hard disk. When the user space initiates a write operation, it writes to the cache first, and then to the mechanical hard disk when the system is idle. Theinvention fully utilizes the low power consumption characteristic of the solid-state hard disk, on the one hand, the power consumption of the mechanical hard disk can be reduced by reducing the use frequency of the mechanical hard disk, on the other hand, the energy consumed for completing the same workload is reduced by improving the work efficiency, the data storage efficiency is optimized, andthe hardware cost of the data storage device is saved.
Owner:ANHUI JIYUAN SOFTWARE CO LTD +1
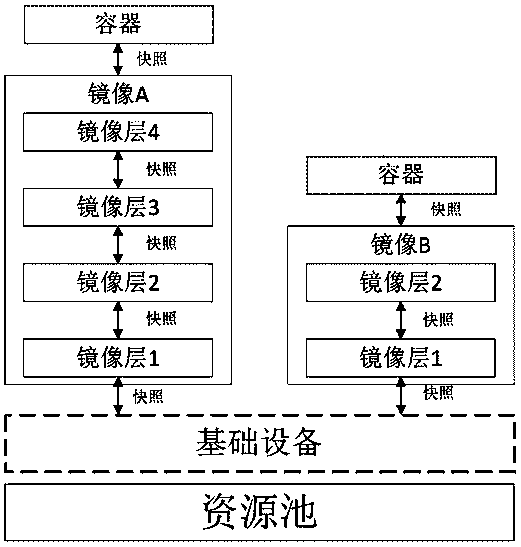
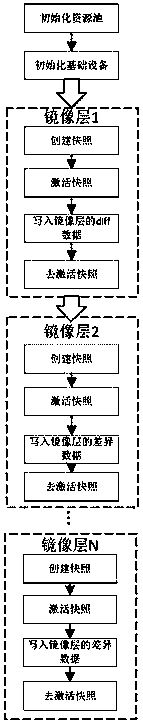
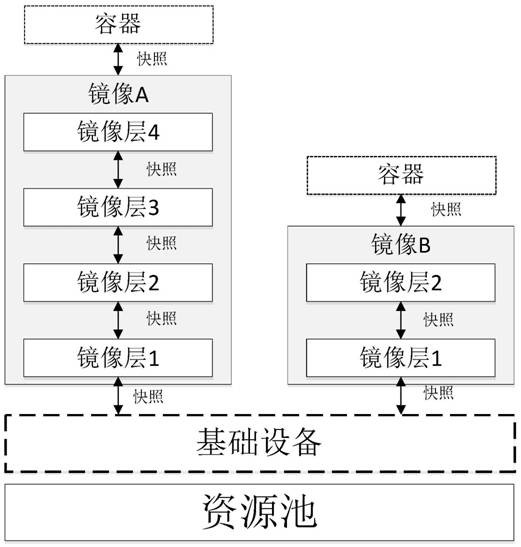
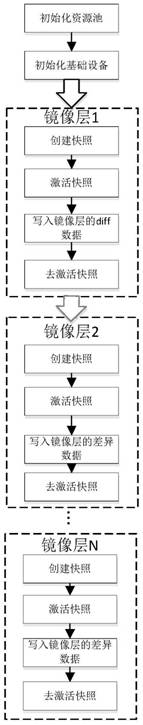
Container mirror hierarchical encryption storage method based on Device Mapper
ActiveCN109190386AAchieve safe storageImplement access controlDigital data protectionStorage securityFile system
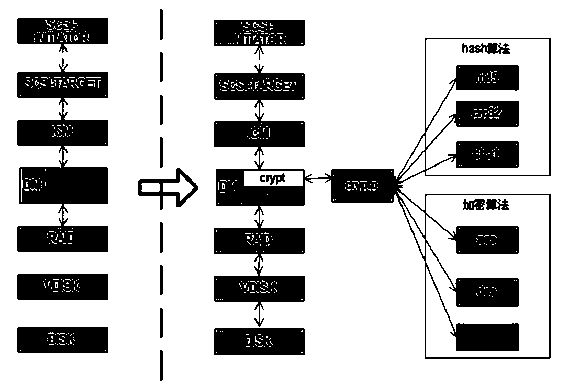
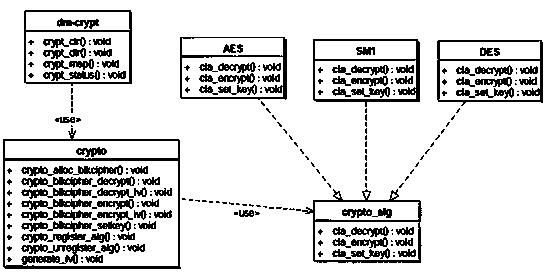
The invention relates to a container mirror image hierarchical encryption storage method based on Device Mapper, which mainly adopts dm-crypt to encrypt the specific snapshot device. A mirroring layercorresponds to a logical device under Device Mapper, and the current mirroring layer key is used to encrypt the logical device via dm-crypt module. When you need to use the mirroring layer, the mirroring layer key is used to decrypt the previously encrypted device via dm-crypt module, which is an accessible device that is provided to the user by binding to the file system. The invention improvesthe existing container mirror image storage mechanism, proposes a mirror image hierarchical encryption storage security mechanism, realizes the safe isolation of container mirror layer data, not onlyrealizes the storage security of the container, but also realizes the access control of the container through the hierarchical encryption. The method brings convenience for security administrators toprovide application services to users with different rights according to different needs, so that the application security of the container is significantly improved.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
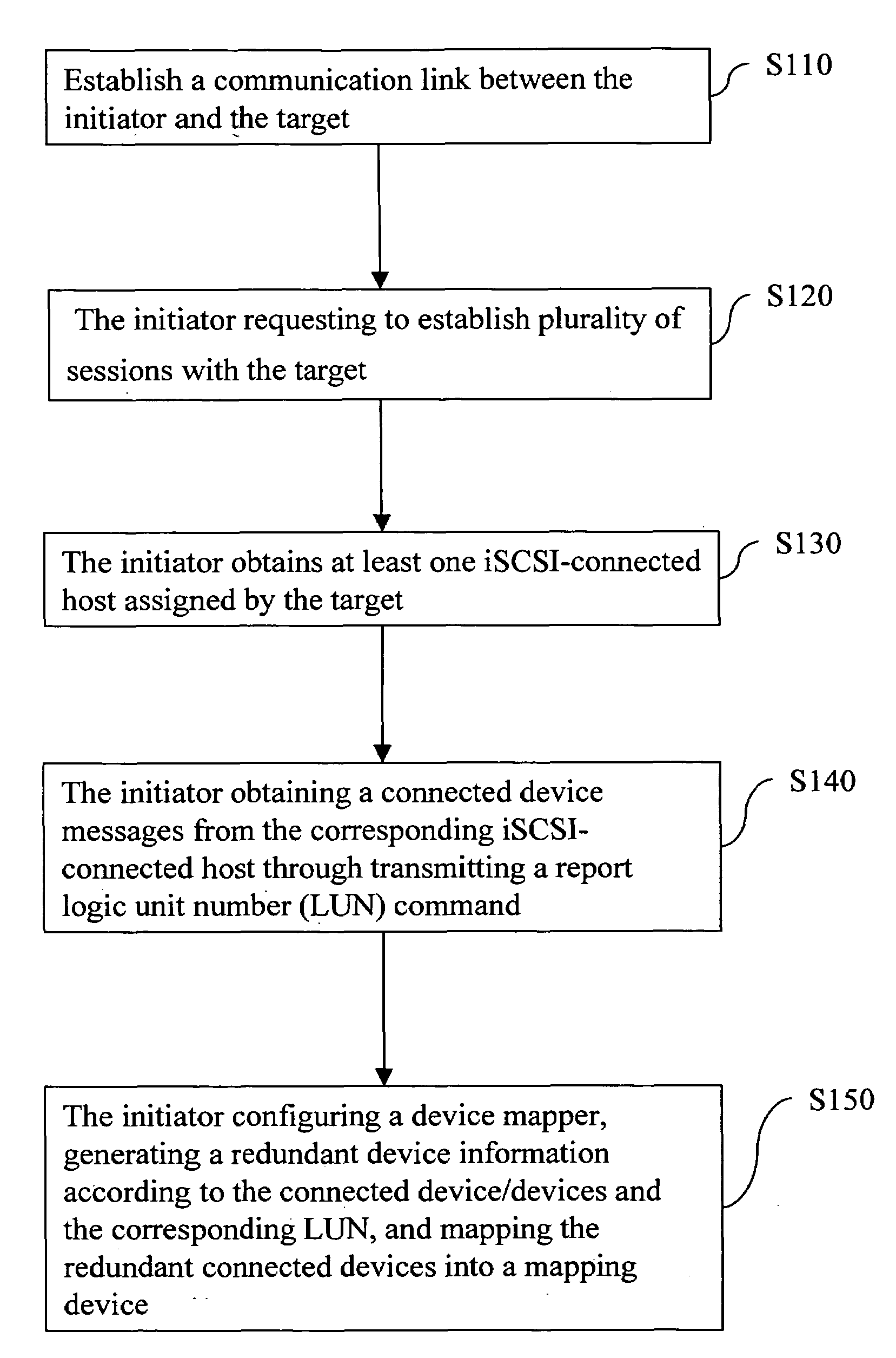
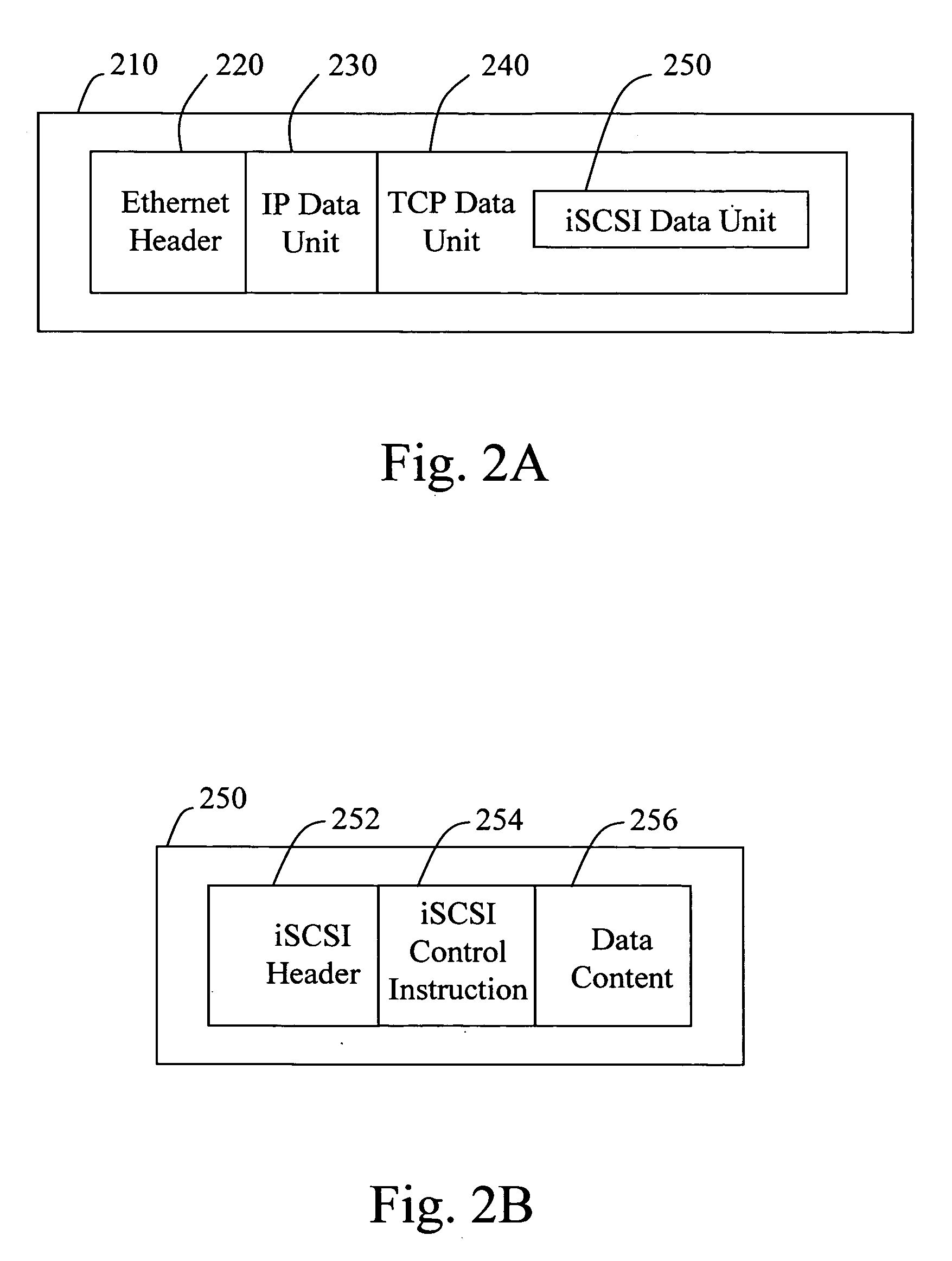
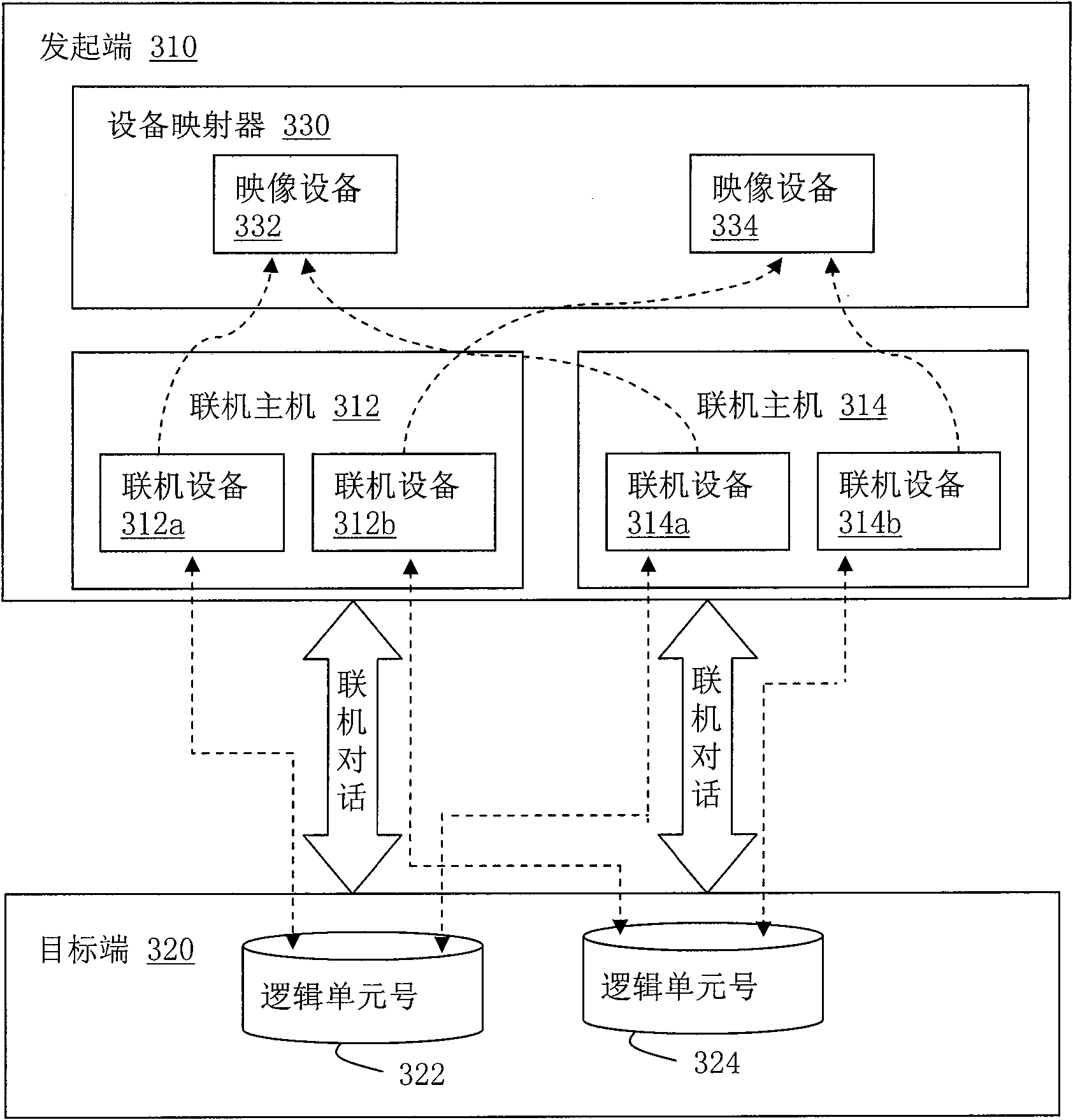
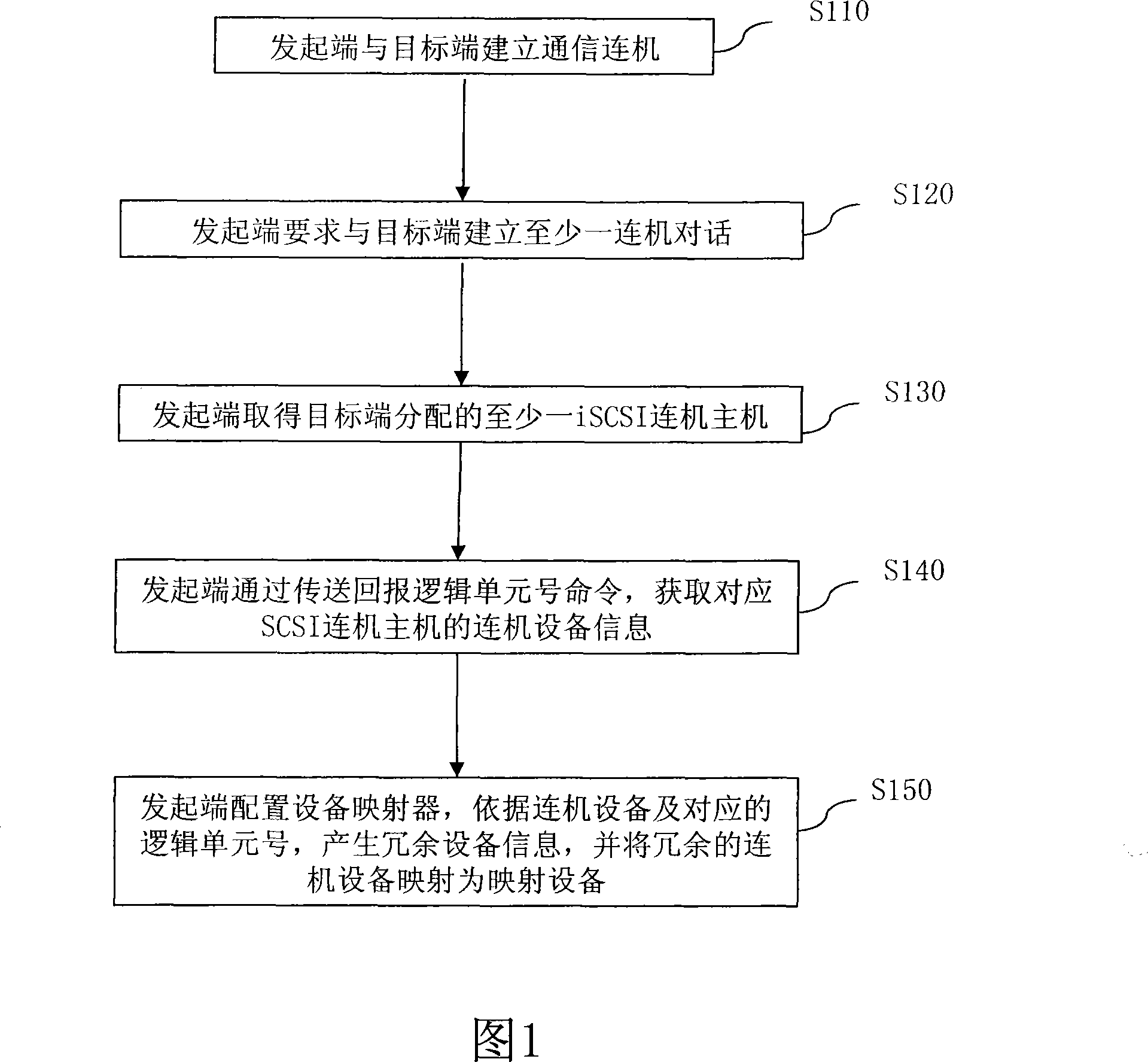
Method of multi-path accessing remote logic device under linux system
InactiveUS20090216886A1Multiple digital computer combinationsTransmissionStorage area networkGNU/Linux
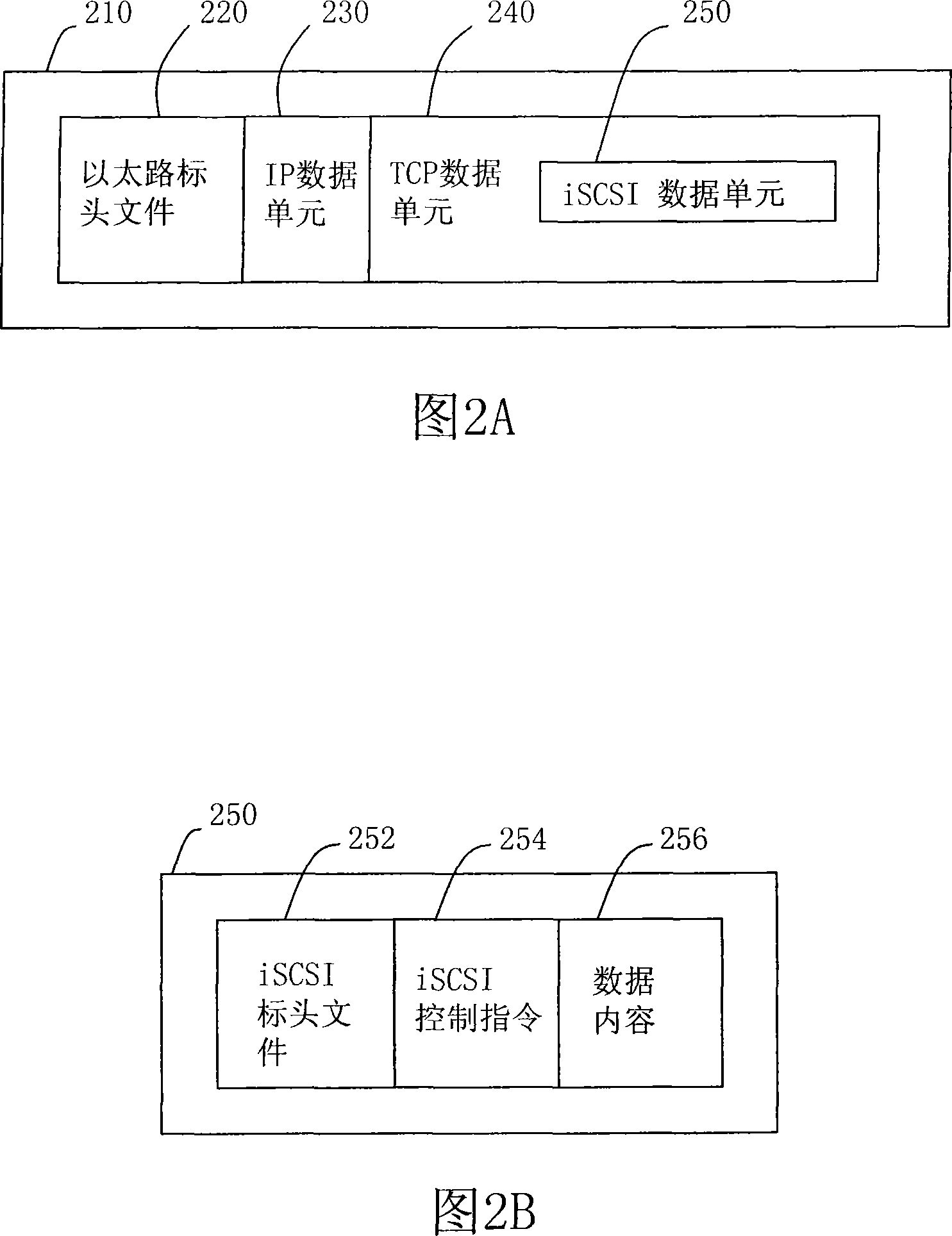
A method of multi-path accessing a remote logic device under a Linux system is used to realize a multi-path access between an initiator and a target in a storage area network (SAN). Firstly, a communication is established between the initiator and the target. Next, the initiator requests to establish at least one link session with the target. Then, the initiator obtains an iSCSI-connected host assigned by the target, and also obtains a message about connected devices corresponding to the iSCSI-connected host through transmitting a report logic unit number (LUN) command. Then, the initiator configures a device mapper, and the device mapper generates information about redundant devices according to the connected devices and the corresponding LUNs, and the redundant connected devices are mapped into a unique mapping device.
Owner:INVENTEC CORP
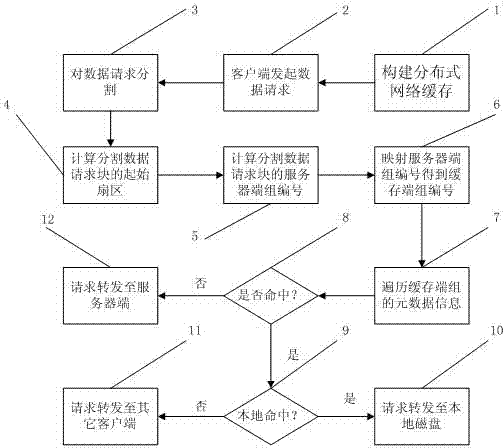
Distributed type network caching method based on Device Mapper
The invention relates to a distributed type network caching method based on a Device Mapper. The distributed type network caching method based on the Device Mapper is characterized in that when a plurality of client sides concurrently access a shared storage server, the client sides utilizes a local disk and disks of other client sides in a local area network (LAN) as caching of the storage server, when access requests of the client sides hit caching of the local disk, the access requests of the client sides are transmitted to the local disk to be processed; when the access requests of the client sides hit caching of the disks of other client sides, the access requests of the client sides are transmitted to the disks of other client sides; and when caching of all the client sides is not hit, the access requests of the client sides are transmitted to a disk of the server, therefore loads and network bandwidth consumption of the storage server are reduced, and the using rate and the request access speed of the disks of the client sides are enhanced. The distributed type network caching method based on the Device Mapper can be used for a high concurrency network storage system.
Owner:HANGZHOU DIANZI UNIV
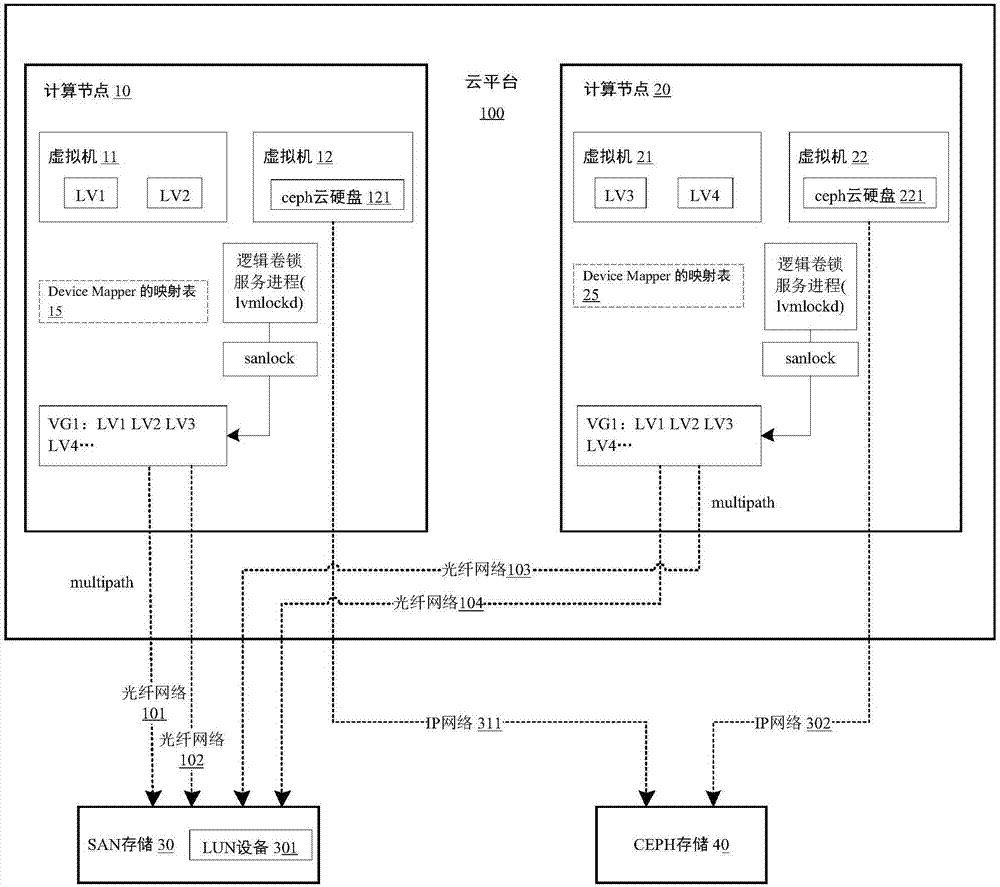
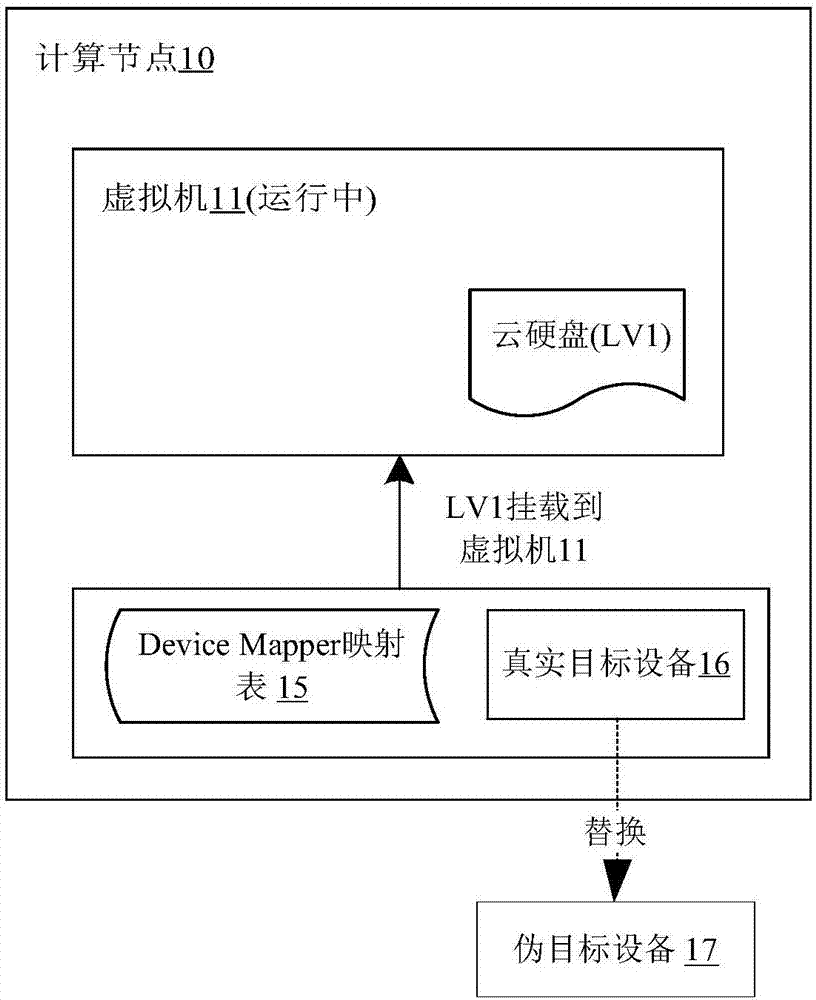
Locked resource configuration method based on shared storage
ActiveCN107888689AAvoid reset downtimeAvoid Forced Abort ResponsesData switching networksManagement toolHigh availability
The invention discloses a locked resource configuration method based on shared storage. The method comprises the steps that a logical volume locking service process calls a Device Mapper mapping tablemanagement tool to prohibit follow-up IO request operations between a volume group and real target equipment, and after IO request operations sent to logical volumes are completed, the real target equipment mapped by the logical volume corresponding to a failure generated by a multi-path data distribution link in a mapping table of the Device Mapper is replaced with pseudo target equipment. According to the method, the phenomenon that all computing nodes are reset and shut down due to the fact that a sanlock triggers a watchdog when the heartbeat of the watchdog is out of time can be avoided,therefore, other virtual machines mounted on the computing nodes are avoided, the phenomenon that the virtual machines mounted with ceph cloud hard disks are forced to suspend responding is avoided,and then the high availability and stability of a cloud platform are improved.
Owner:无锡地铁集团有限公司 +1
Method for recovering disk cache power down based on novel nonvolatile storage
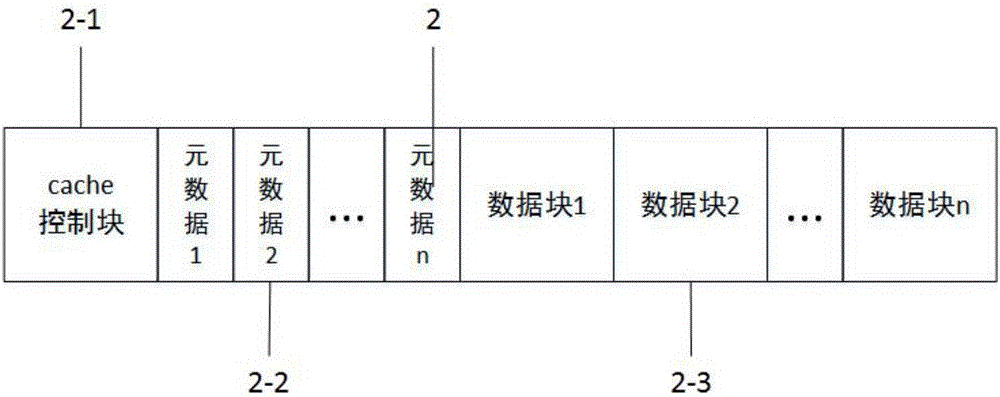
InactiveCN106775684ARealize the function of power failure recoveryIncrease flexibilityMemory loss protectionInternal/peripheral component protectionParallel computingBase function
Provided is a method for recovering disk power down based on a novel nonvolatile storage. According to the method, a Linux Kernel Device Mapper frame is adopted, an AEP is adopted in cache equipment in the bottom layer, open source software dm-cache is adopted as a chief source, on the basis of achieving disk cache basic functions, a power down recovering module is added, a byte writing method is adopted to timely write metadata of a cache equipment control structure and a cache block back to a cache control block and a metadata area of the AEP so as to retain in real time an operational scene of the cache module. When power down occurs in a system accidentally and the system is restarted, the operational scene of the cache module can be recovered through the method of reloading a total control data structure which is stored in the cache equipment in the cache control block of the AEP and the metadata information of the cache block in the metadata area of the AEP so as to make the system operate at a sate before the power down, and in this way, the purpose of recovering the data in the disk cache block is achieved.
Owner:BEIHANG UNIV
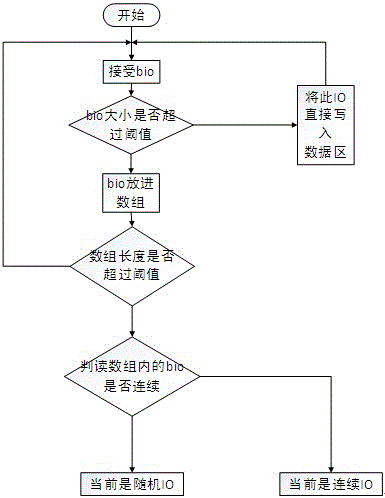
Method for accelerating random in-out (IO) read-write of disk
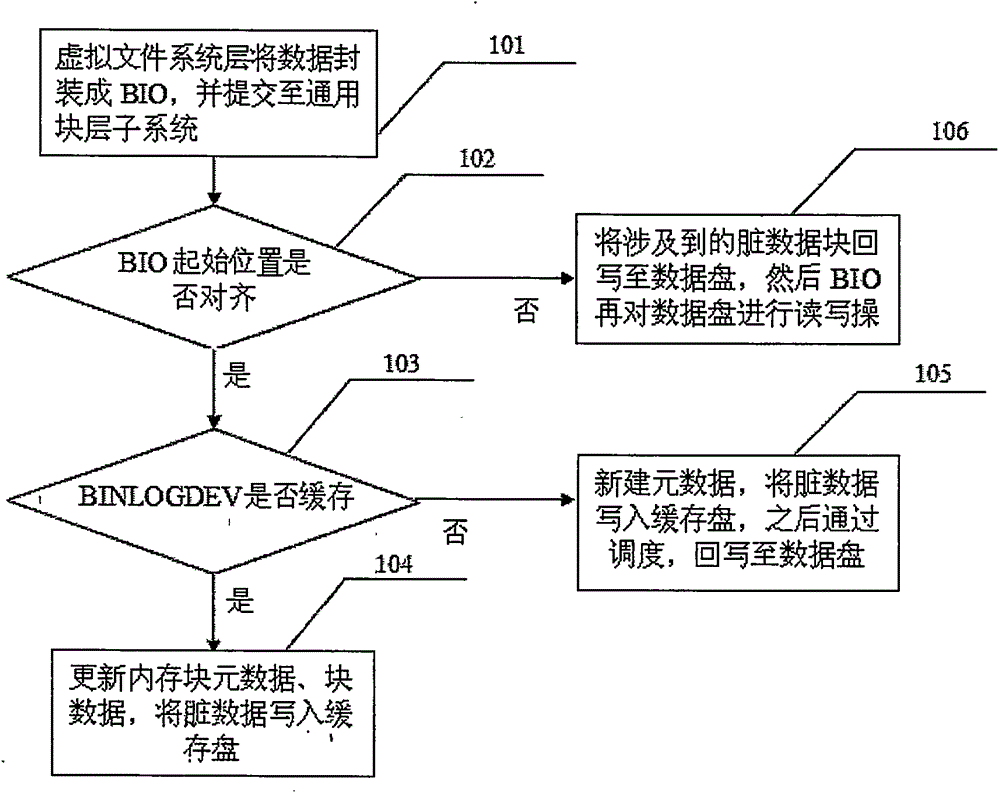
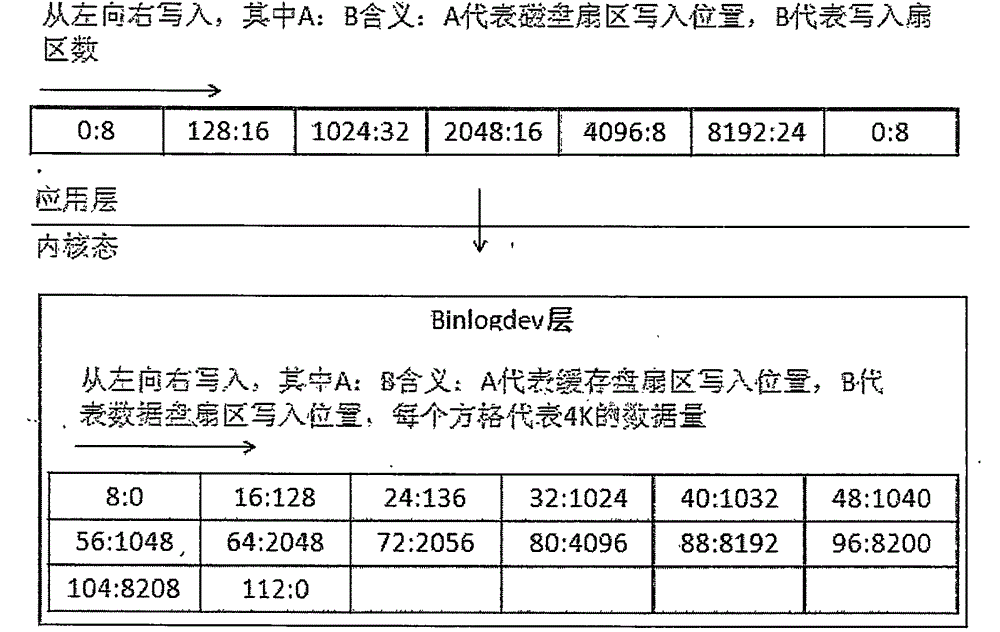
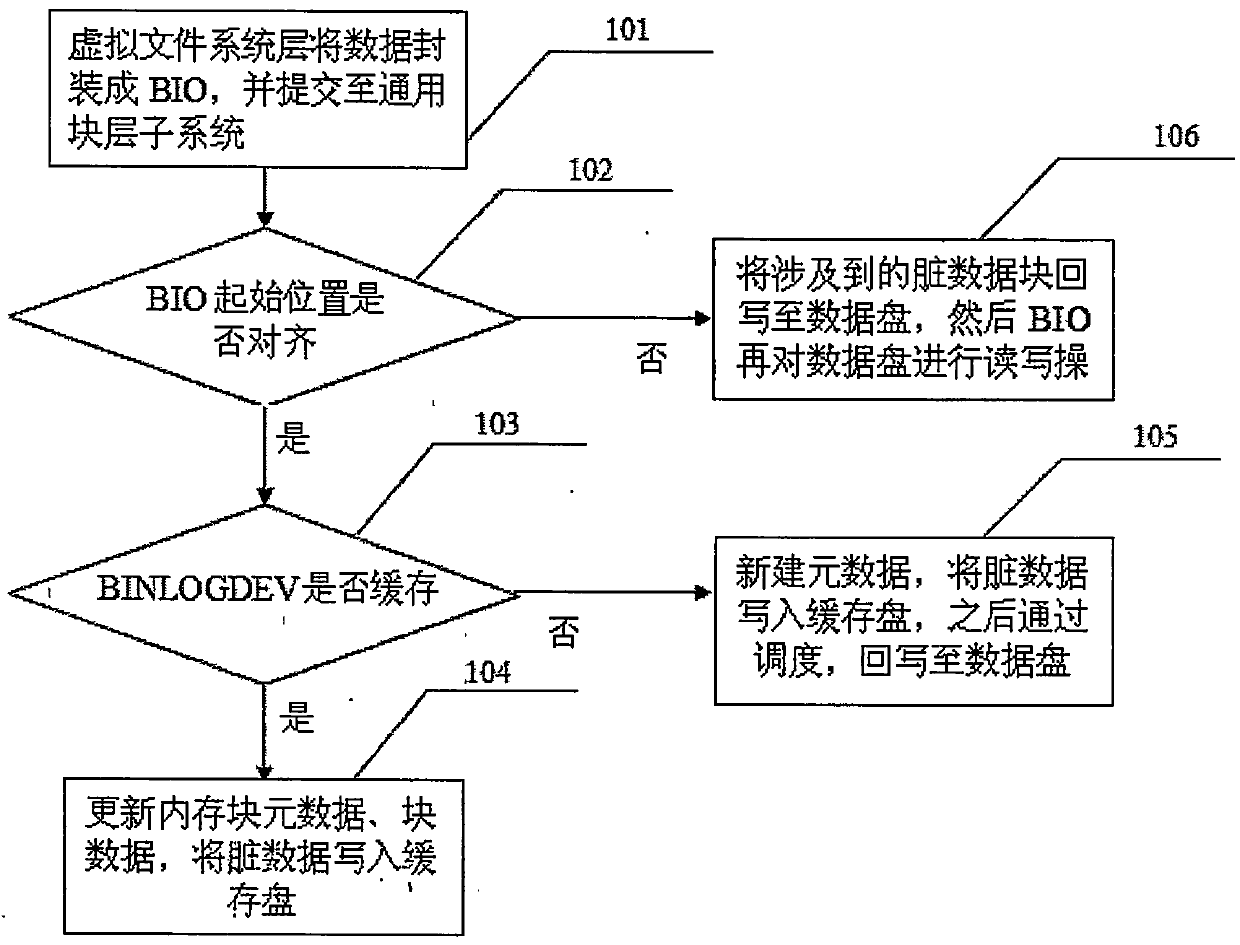
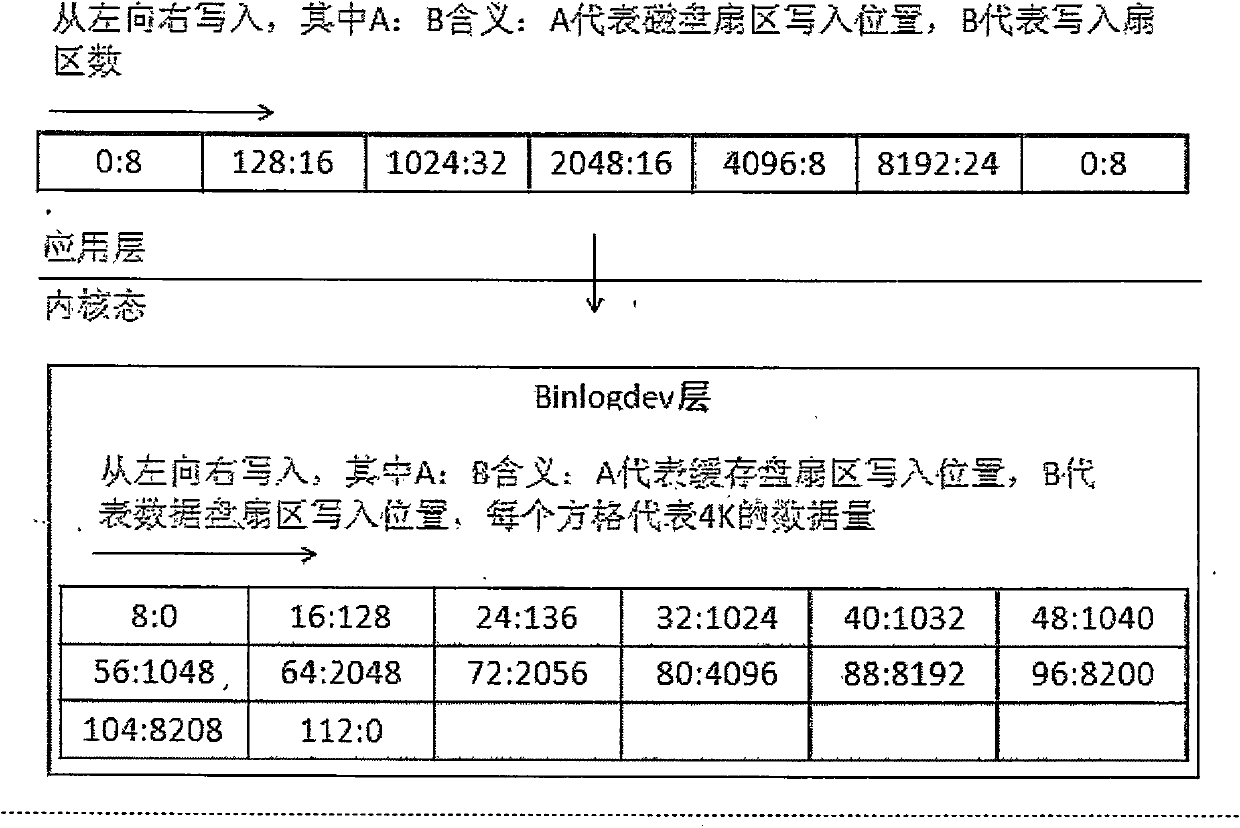
ActiveCN104793892AAccelerate the number of writesReduce the number of operationsInput/output to record carriersVirtual file systemDevice mapper
The invention discloses a method for accelerating random in-out (IO) read-write of a disk. The method is characterized by comprising the steps that a computer operating system application layer performs a data read-write operation and enters a kernel mode through invagination, a virtual file system layer encapsulates data into a BIO which is an interactive data structure between the virtual file system layer and a general block layer, and then the BIO is submitted to a general block layer subsystem; the BIO is cut into the fixed block size and transmitted to a BINLOGDEV module layer at a DEVICE-MAPPER driving layer of the general block layer subsystem, when the BIO enters the BINLOGDEV module layer, whether a caching condition is met or not is checked, that is, whether the initial position of the BIO is aligned or not, whether the length of the BIO is the block length or not, if the condition is met, a step 103 is conducted, and if the condition is not met, a step 106 is conducted. According to the method for accelerating the random in-out (IO) read-write of the disk, on the condition that the random IO is written, the random IO is converted into the sequence IO, the storing velocity is high, and the efficiency is high.
Owner:UCLOUD TECH CO LTD
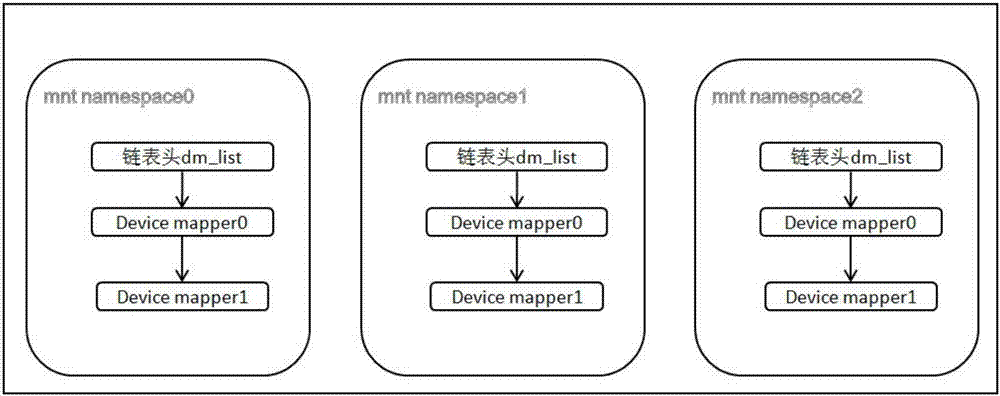
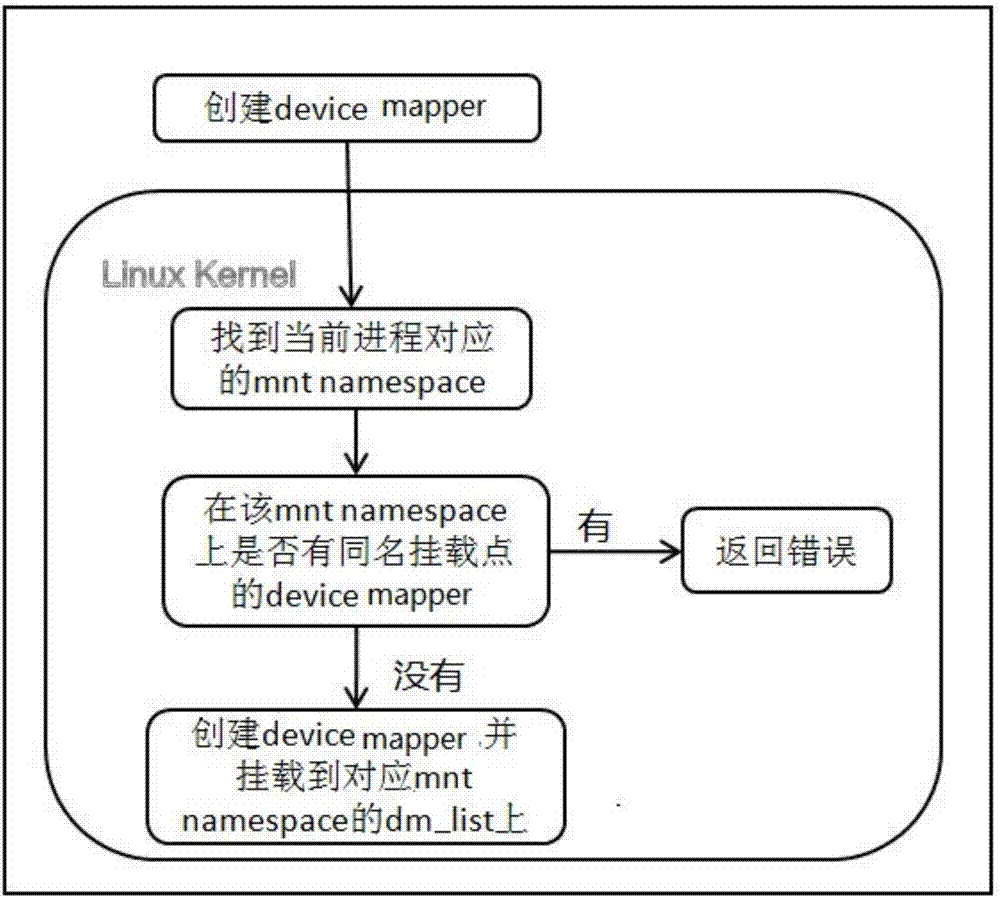
Device mapper isolation method based on android containers
InactiveCN107229467ANo incompatibility issuesImprove compatibilityProgramming languages/paradigmsProgram loading/initiatingOperational systemComputer compatibility
The invention provides a device mapper isolation method based on android containers. The method includes the following step: S1, adding a chain table head dm_list for a mnt namespace structure in an operating system kernel, using the mnt_namespace structure to create a device mapper, and mounting the newly created device mapper on a chain table which takes the chain table head dm_list of a mnt_namespace as a head, wherein each mnt namespace has a device mapper chain table. The method has the advantages that the Device Mapper is a virtual driver of the kernel, thus incompatibility problems of different android machines do not exist, and the compatibility is improved.
Owner:BEIJING HAIHANG COMM TECH CO LTD
Method for optimizing performance of encryption card based on DEVICE MAPPER
InactiveCN104268489ASave CPU timeReasonable designInternal/peripheral component protectionResource utilizationCPU time
The invention provides a method for optimizing the performance of an encryption card based on DEVICE MAPPER. The API of the encryption card is integrated into the universal block device kernel framework Device Mapper so that a dm-crypt encryption block device module suitable for the encryption card can be realized, and furthermore, an encrypted file system can be established for protecting confidential data at a disk storage level; the encryption block device module comprises two modes, namely synchronous block encryption and asynchronous block encryption of the domestic encryption algorithm sm1, and a method for registering the algorithm sm1 to a kernel password manager is provided. Compared with the prior art, the method for optimizing the performance of the encryption card based on DEVICE MAPPER is characterized in that the increase of the speed is realized by virtue of parallel operating of a plurality of cards, and in the aspect of system resource utilization rate, principally, the previous encryption card working pattern is changed from waiting mode into an asynchronous working mode, and therefore, the time of the cpu is greatly saved.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
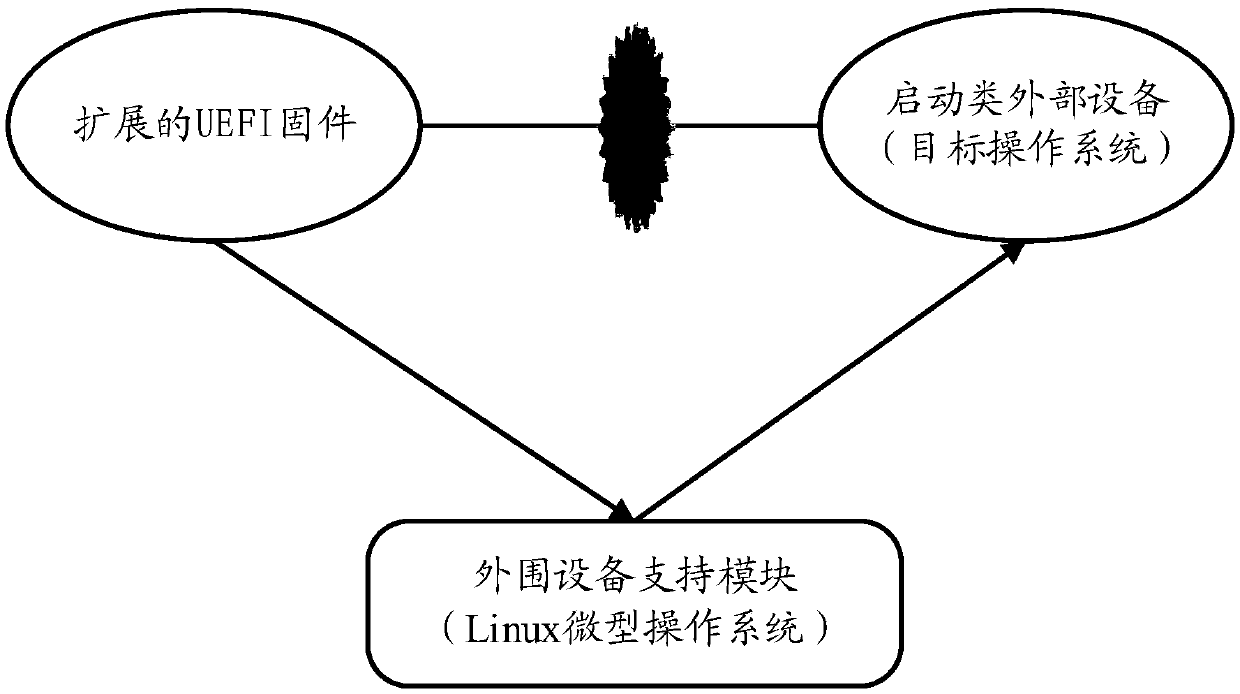
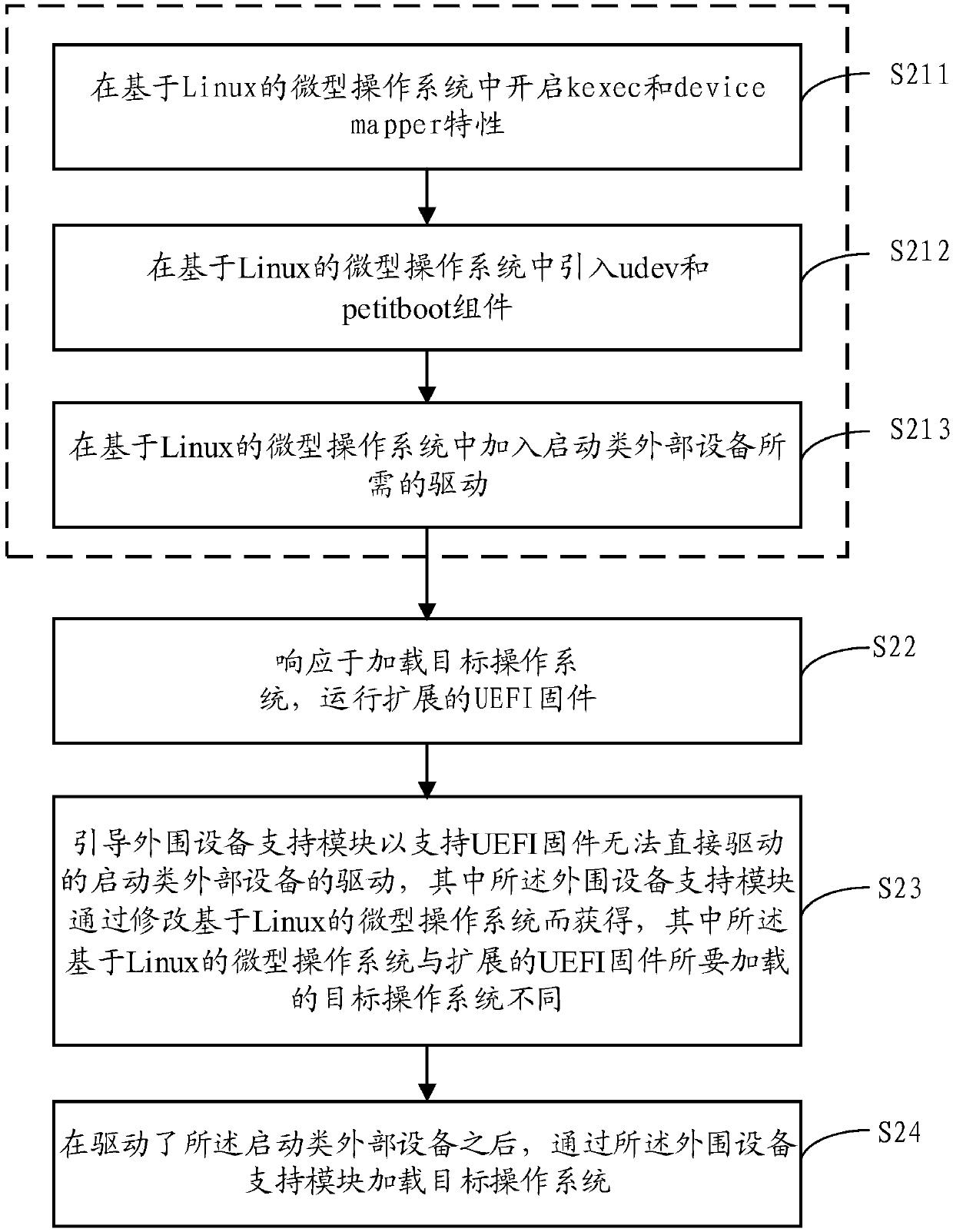
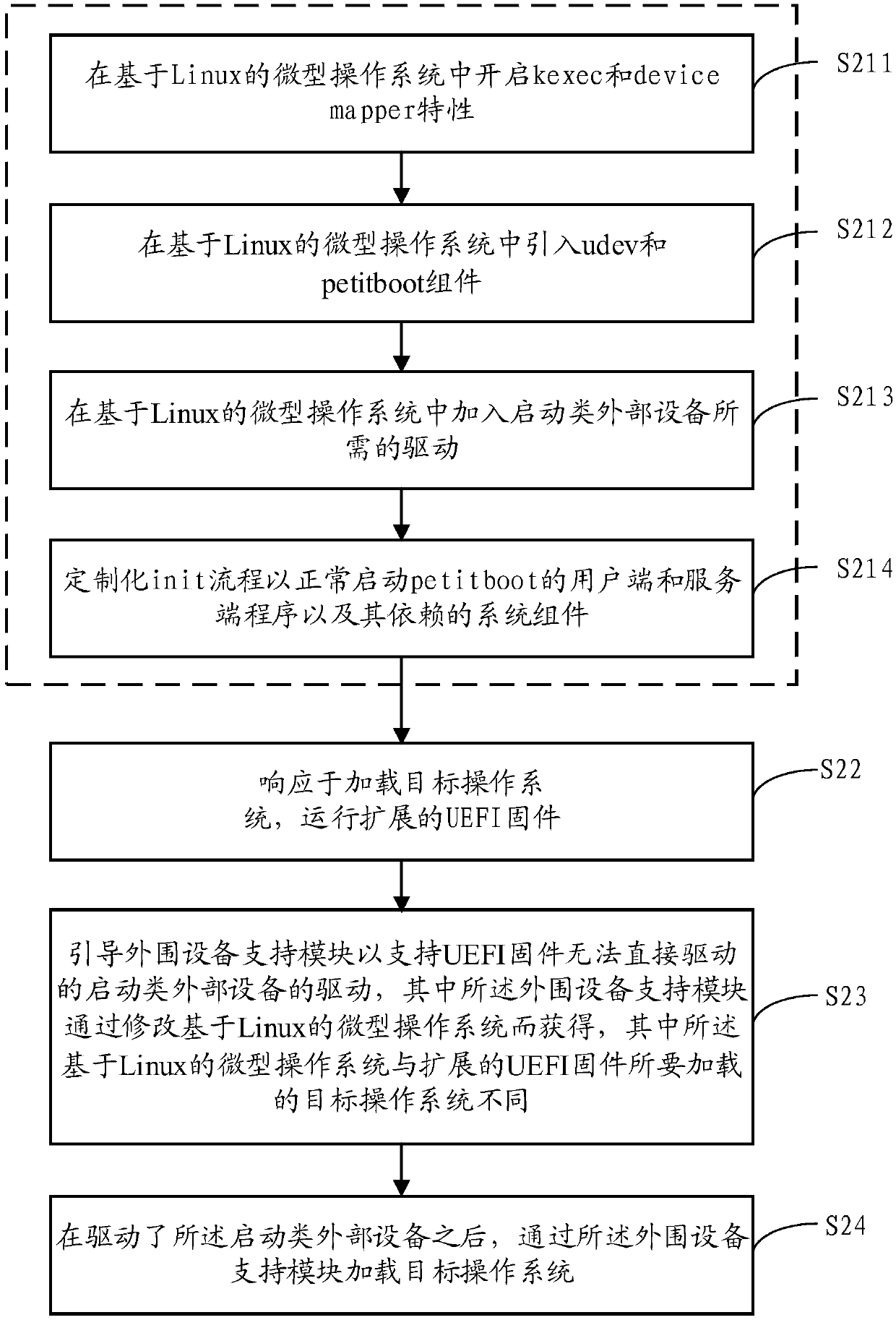
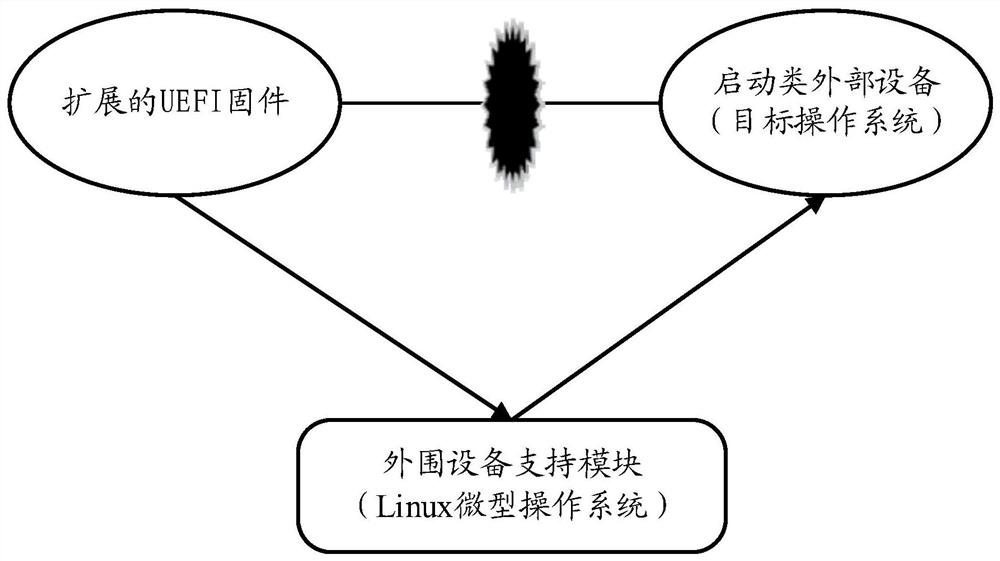
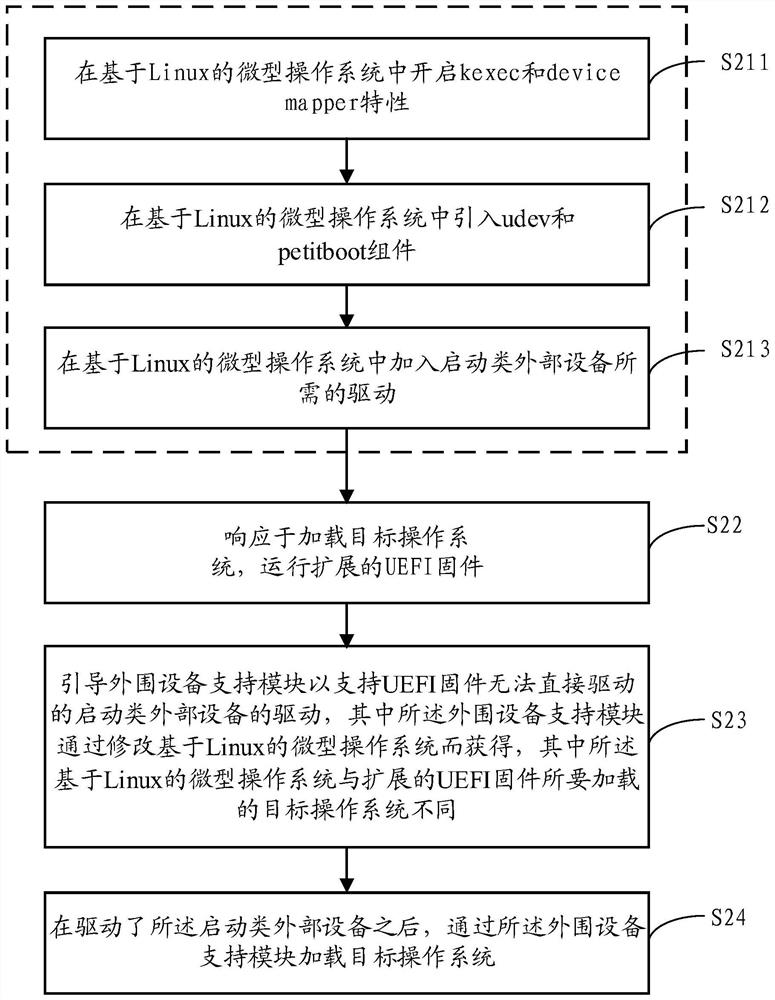
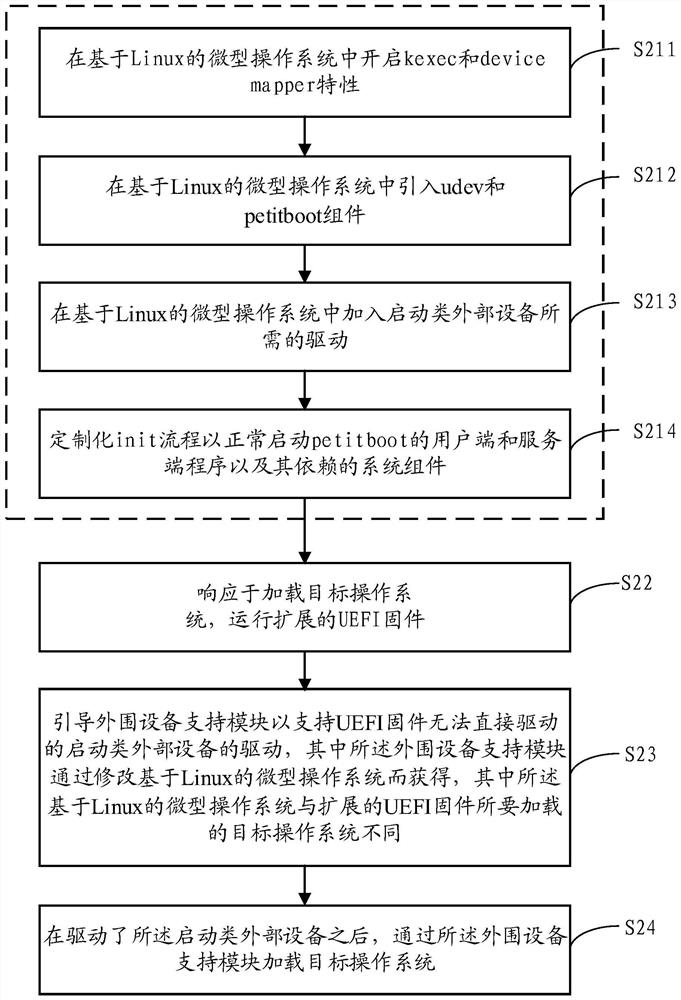
Method, device and system for supporting startup of a drivestarting of drive of external device
A method for extending UEFI firmware to support startup of a drive of an external device is provided. The method comprises the following steps: responding to loading of a target operating system, andoperating extended UEFI firmware; T; the peripheral equipment support module is guided to support the drive of the startup type external equipment, wherein the drive cannot be directly driven by the UEFI firmware; w; wherein the peripheral equipment support module is obtained by modifying a Linux-based micro operating system, and the Linux-based micro operating system is different from a target operating system to be loaded by extended UEFI firmware; A; and loading, by the peripheral device support module, a target operating system after the boot-up-type external device is driven, t, the peripheral device support module being obtained by: starting key ec and device mapper characteristics in a Linux-based micro operating system, and starting the boot-up-type external device by the peripheral device support module, T, the method comprises the following steps: introducing a udev component and a peer component into a Linux-based miniature operation system, t, the peer component being a starter using a Linux key mechanism; A; and adding a driver required for starting the class external equipment into the Linux-based micro operating system.
Owner:贵州华芯半导体技术有限公司
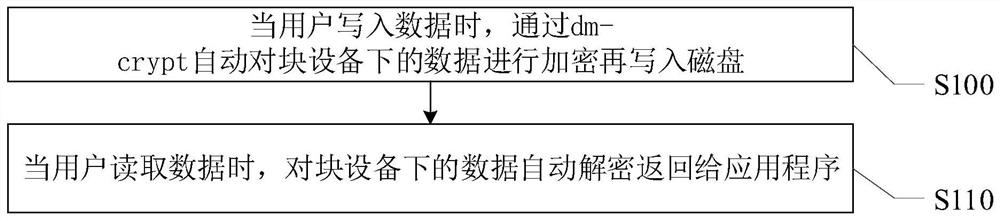
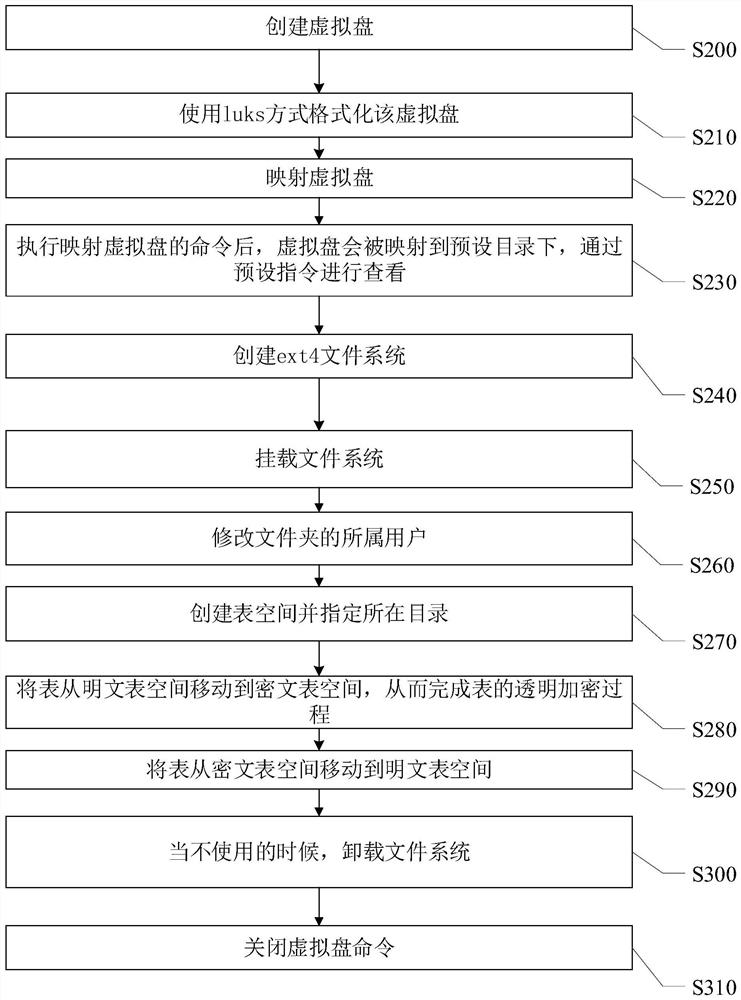
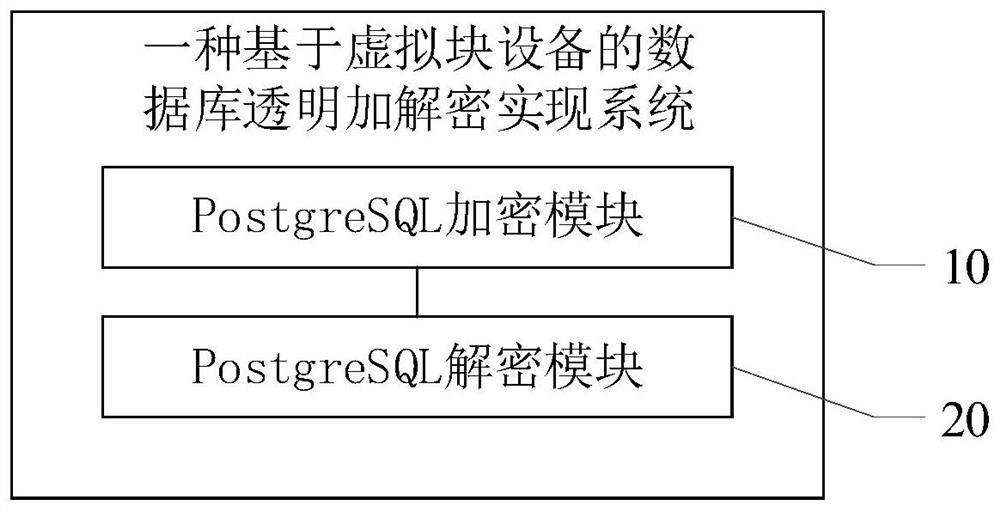
Database transparent encryption and decryption implementation method and system based on virtual block device
PendingCN114036538ARealize the TDE functionMeet transparent encryption requirementsInput/output to record carriersRelational databasesComputer hardwareCrypt
The invention provides a transparent database encryption and decryption implementation method and system based on virtual block equipment, and relates to the technical field of data safety. The transparent database encryption and decryption implementation method based on the virtual block device comprises the steps that when a user writes data, the data under the block device are automatically encrypted through dm-crypt and then written into a disk; and when a user reads the data, automatically decrypting the data under the block device and returning the decrypted data to the application program. According to the method, the TDE function of the POSTGRESQL database can be achieved by using a Device Mapper mechanism, encryption and decryption are operated at the block device level, any operation of the database is not affected, but data of a disk is stored in an encrypted mode, and therefore the transparent encryption requirement of a user is met. In addition, the invention further provides a database transparent encryption and decryption implementation system based on the virtual block device. The system comprises an encryption module and a decryption module.
Owner:北京中安星云软件技术有限公司
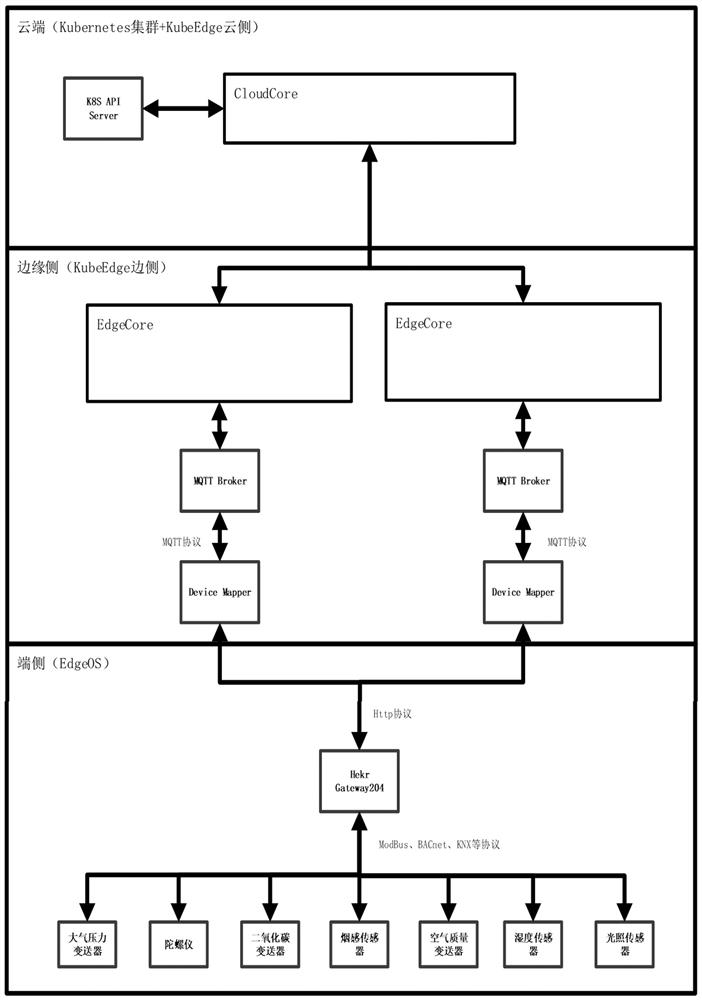
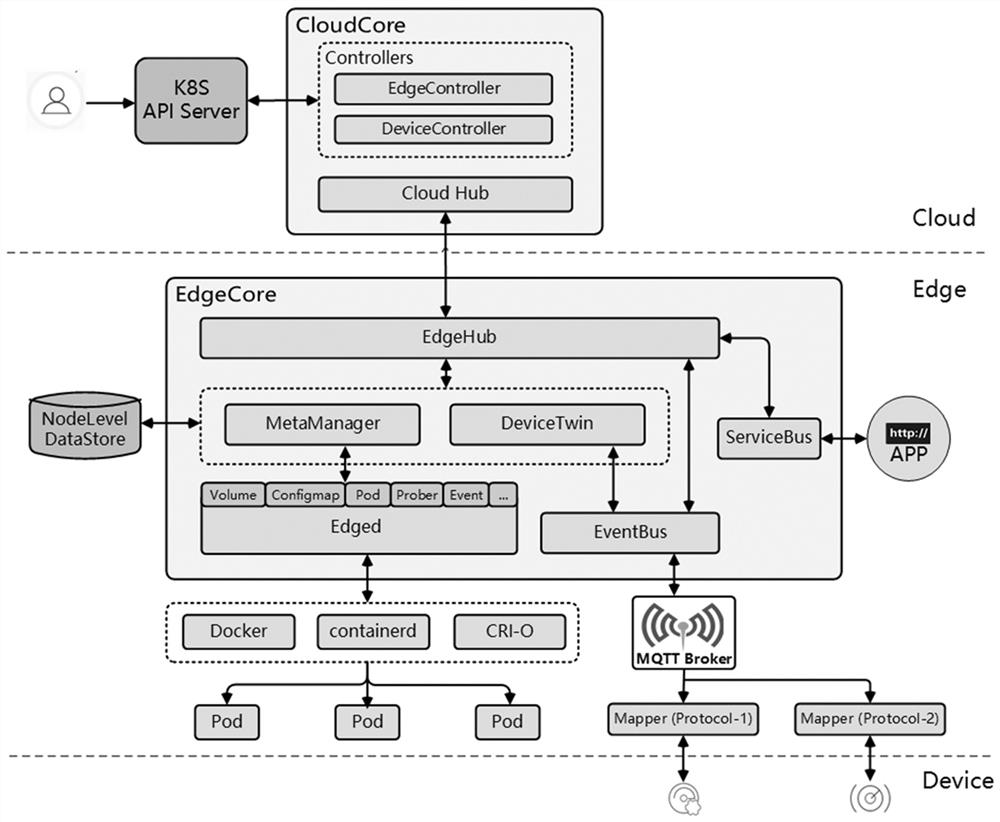
Internet of Things equipment control architecture and method based on KubeEdge and EdgeOS
PendingCN113691497ASolve efficient managementSolve intelligent analysisNetwork connectionsData synchronizationEdge node
The invention relates to an Internet of Things equipment control architecture and method based on KubeEdge and EdgeOS, and the architecture is specifically characterized in that the KubeEdge comprises a cloud side module and an edge side module, the cloud side module is provided with a cloud node, the edge side module is provided with an edge node, the cloud side module manages the edge node and issues an edge end application, the edge side module executes edge end application deployment and data synchronization to the cloud side module, the edge node deploys a Device Mapper and an MQTT Broker, the EdgeOS is configured with a Gateway gateway and performs data communication with an end side device through the Gateway gateway, and the Device Mapper interacts with the Gateway gateway in an HTTP message form, and publishes and subscribes an MQTT message to the MQTT Broker. According to the invention, the complexity of management and development of the KubeEdge side equipment is reduced.
Owner:ZHEJIANG LAB
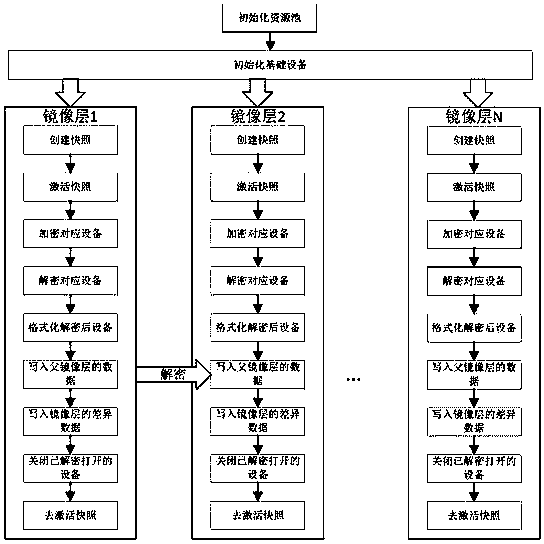
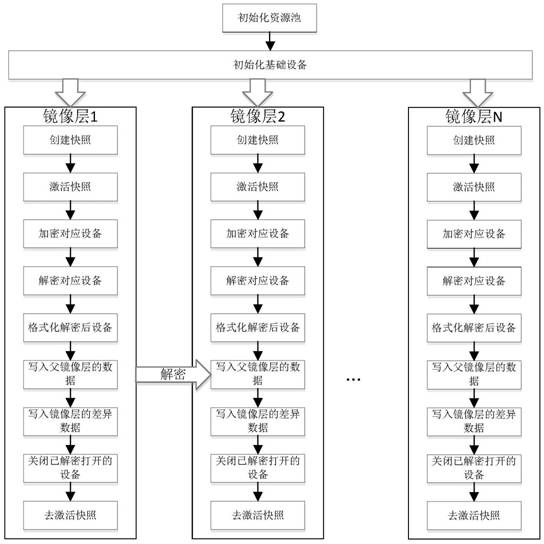
Layered encryption storage method of container image based on device Mapper
ActiveCN109190386BAchieve safe storageImplement access controlDigital data protectionComputer hardwareStorage security
The container image layered encrypted storage method based on Device Mapper of the present invention mainly adopts dm-crypt to encrypt specific snapshot devices. A mirror layer corresponds to a logical device under Device Mapper, and the logical device is encrypted by the dm-crypt module using the key of the current mirror layer. When you need to use the mirror layer, use the mirror layer key to decrypt and open the previously encrypted device through the dm-crypt module. The decrypted and opened device is an accessible device, which is provided to the user after being bound to the file system. The present invention improves the existing container image storage mechanism, proposes a security mechanism for image layered encryption storage, realizes the security isolation of container image layer data, not only realizes the storage security of the container, but also realizes the storage of the container through layered encryption Access control. It is convenient for security managers to provide application services to users with different permissions according to different needs, so that the application security of containers is significantly improved.
Owner:CHINA ELECTRONICS TECH CYBER SECURITY CO LTD
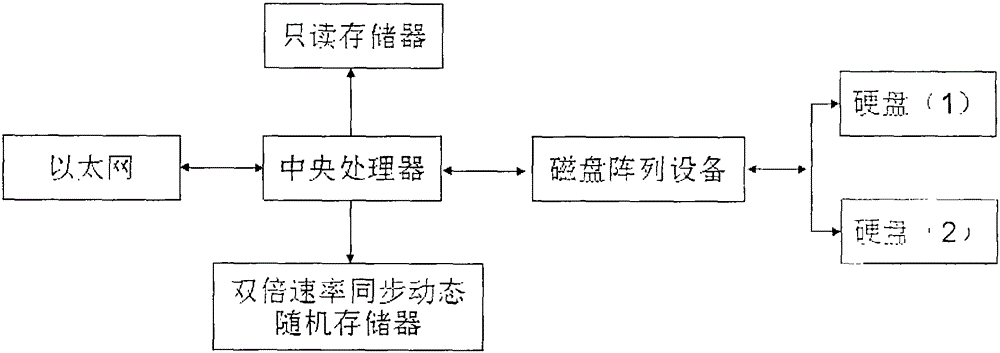
Method for preventing hard disk data from being modified and covered
InactiveCN105183671AEliminate the possibility of editingMemory loss protectionInternal/peripheral component protectionData informationSynchronous dynamic random-access memory
The invention discloses a method for preventing hard disk data from being modified and covered. The method is characterized by comprising the steps that a Device Mapper mechanism based on a linux system kernel transmits data information to a server side through Ethernet access, and the data information is encrypted, stored and processed through the server side, wherein the specific process comprises the steps that the data information is transmitted to a central processor through the Ethernet, then temporarily stored to a double-speed synchronous dynamic random access memory and a read-only memory through the central processor, processed through the central processor and then stored into two hard disks in an mirror image mode through a disk array device, meanwhile, the hard disks are encrypted through a Cryptsetup tool, and serial numbers of the hard disks are read. According to the method, in the process of writing data in through a computer, the hard disks are encrypted through the Cryptsetup tool, the read serial numbers of the hard disks are applied to encryption secret keys, so that after the hard disks leave the computer, the content in the hard disks cannot be read or modified on other computers, and the probability that the hard disks are compiled after leaving a system is eradicated.
Owner:深圳市图美电子技术有限公司
A cache system based on non-volatile memory and software raid
ActiveCN106528001BAvoid multiple visitsShorter read and write timesInput/output to record carriersDielectricRAID
The present invention proposes a cache system based on non-volatile memory and software RAID, which is characterized by a novel storage system architecture integrating non-volatile memory Apache Pass, software RAID and Device Mapper driver module Buaacache. The invention utilizes the Device Mapper mechanism of Linux to manage the software RAID, and uses the high-speed device Apache Pass as the Cache of the low-speed RAID, thereby constructing a two-level cache system. Persistent Memory has the characteristics of no loss of media data after power failure and excellent read and write performance. The present invention selects Persistent Memory as the high-speed cache of the software RAID, and realizes that the reading and writing performance of the software RAID is close to or even exceeds that of the hardware RAID under the condition that the cost is far lower than that of the hardware RAID.
Owner:BEIHANG UNIV
A non-volatile cache method for ssd
ActiveCN106201916BImprove random write performanceExtend your lifeMemory adressing/allocation/relocationInterference problemDevice mapper
The invention relates to a nonvolatile cache mechanism facing SSD. The method comprises following steps: a SSD is divided into a large buffer area; small random write requests are first written in small RAM buffer; after the RAM buffer is full, those write requests are written together in the form of log into a buffer area sequentially; then data in the buffer area is written back to a data area by a backstage; in this way, the random write-in performance of SSD is effectively increased; the cache mechanism can also optimize read interference problems; the cache mechanism comprises: sequential and large I / O are filtered by an I / O detection algorithm; cache write can also be sequentially written in a data area by a garbage recovery strategy facing data area, at the same time, remaining data in the buffer area can also be written again in the cache sequentially; a read cache strategy is provided for solving the problem of SSD read interference; A SSD cache SSD system of a log structure based on device mapper is fulfilled.
Owner:NAT UNIV OF DEFENSE TECH
GPU-based rs-draid system and storage device data control method
ActiveCN102520890BReduce resource utilizationIncrease profitInput/output to record carriersRedundant data error correctionData controlGraphics
The invention provides an RS (Reed-Solomon)-DRAID (D redundant array of independent array) system based on GPUs (graphic processing units) and a method for controlling data of memory devices. The RS-DRAID system comprises a plurality of device mappers, a plurality of servers and a plurality of memory devices. The servers are used for receiving writing IO (input and output) requests, each writing IO requests into a plurality of chunks which are synchronously transmitted, the servers are used for controlling writing into the memory devices and restoring failure memory devices, each server comprises an internal memory unit and a check code computing unit, the check code computing units are used for parallelly computing check codes according to the chunks from the device mappers, the check codes are recomputed when the memory devices are failure, the recomputed check codes are written into the internal memory units to recover the failure memory devices, the check code computing units are the graphic processing units GPU, and a central processing unit CPU is used for controlling data written into the memory devices. RS-DRAID algorithm is realized in a server cluster, the GPUs realize a check code parallel computing process, and service rate of the memory devices can be improved.
Owner:无锡天云数据中心科技有限公司
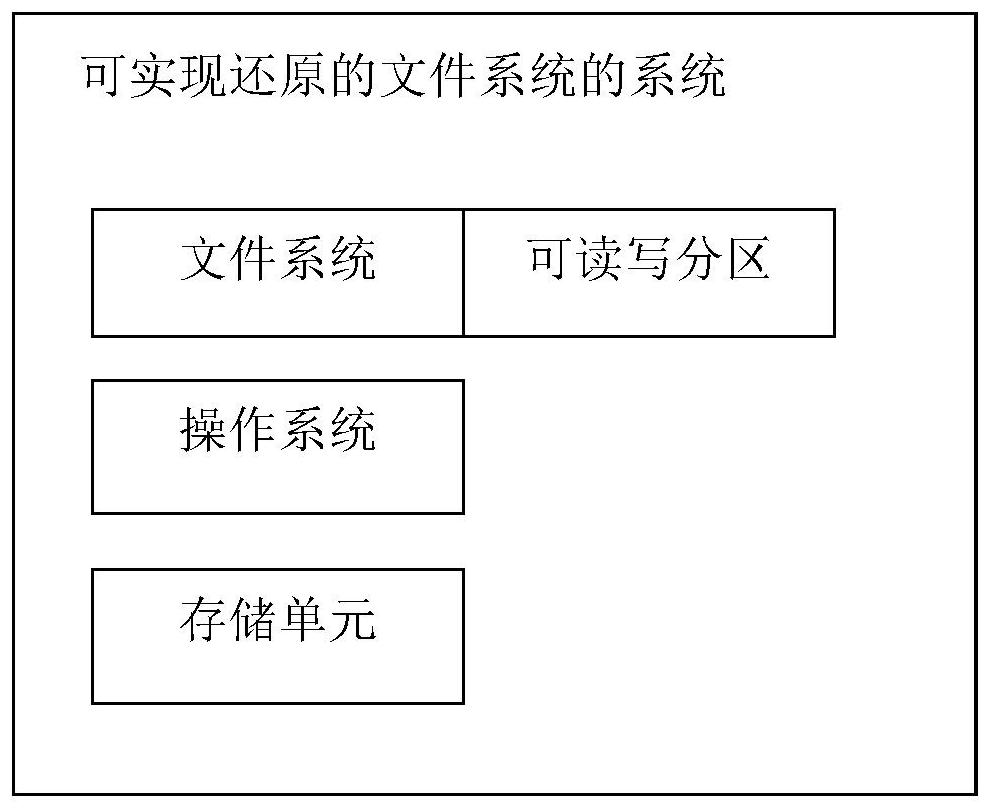
System capable of restoring file system
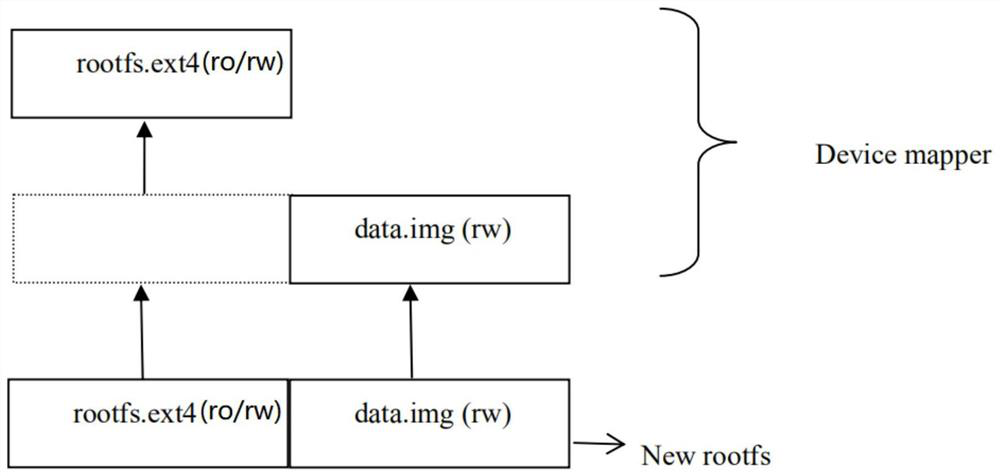
PendingCN112579347AShorten the timeSave spaceRedundant operation error correctionOperational systemFile system
The invention provides a system capable of restoring a file system. The system comprises a file system; a read-write partition which is used for copying the content of the file system and can be usedfor carrying out read-write operation according to the requirements of a user; a storage unit which is used for storing a device mapper software package, wherein the operating system calls a mountinginstruction in the device mapper software package to mount the file system and the readable-writable partition by utilizing a device mapping mechanism to form a file system with the readable-writablepartition, and after the original file system before mounting is damaged under the abnormal power failure or emergency situation, the mounted file system copied in the readable and writable partitionis started.
Owner:北京君正集成电路股份有限公司
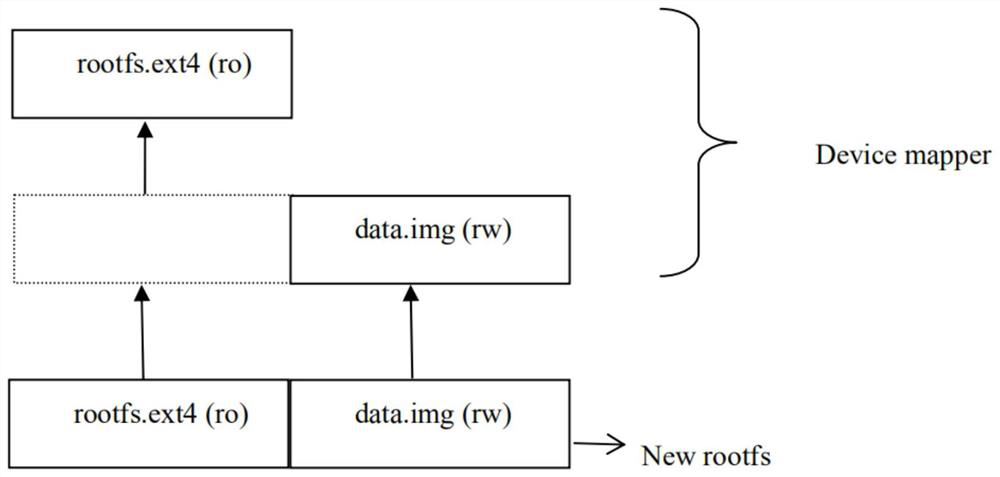
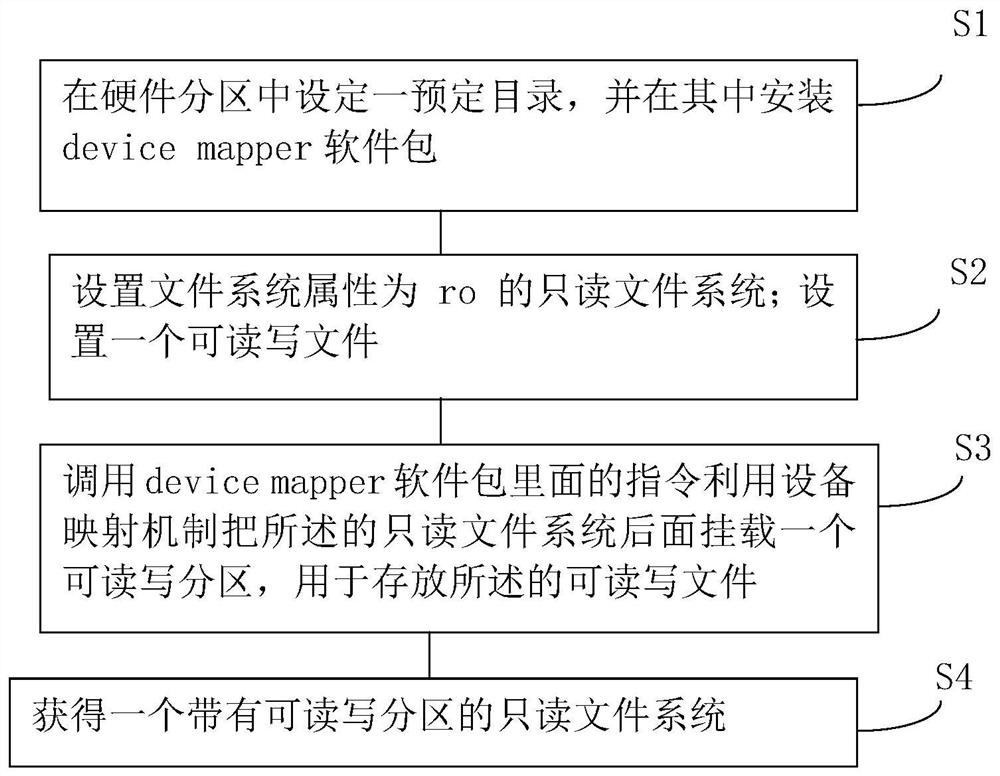
Implementation method of file system based on equipment mapping mechanism
PendingCN112579521AMeet literacy needsSave spaceFile system administrationFile access structuresFile systemSoftware engineering
The invention provides a method for realizing a file system based on an equipment mapping mechanism, which comprises the following steps of: S1, setting a predetermined directory in a hardware partition, and installing a device mapper software package in the predetermined directory; S2, setting a read-only file system of which the file system attribute is ro; setting a readable and writable file;S3, calling an instruction in an equipment mapper software package to mount a readable-writable partition behind the read-only file system by utilizing the equipment mapper, wherein the readable-writable partition is used for storing the readable-writable file; and S4, obtaining a read-only file system with a read-write partition.
Owner:北京君正集成电路股份有限公司
Method, device and system supporting drive of boot-type external device
Provides a method for extending UEFI firmware to support drivers for boot-type external devices. The method includes: in response to loading the target operating system, running extended UEFI firmware; booting the peripheral device support module to support the driver of the boot-type external device that the UEFI firmware cannot directly drive, wherein the peripheral device support module modifies the Linux-based micro operating system, wherein the Linux-based miniature operating system is different from the target operating system to be loaded by the extended UEFI firmware; and after driving the boot-type external device, load the target operating system through the peripheral device support module , wherein the peripheral device support module is obtained through the following steps: enabling kexec and device mapper features in a Linux-based micro-operating system; introducing udev and petitboot components into a Linux-based micro-operating system, wherein the petitboot component It is a launcher using the Linux kexec mechanism; it adds the driver required to start external devices in a Linux-based micro-operating system.
Owner:贵州华芯半导体技术有限公司
Pseudo-random type NFS application acceleration system
ActiveCN102147802BTransparency hasMinor changesSpecial data processing applicationsComputer moduleLinux kernel
Owner:DAWNING INFORMATION IND BEIJING +1
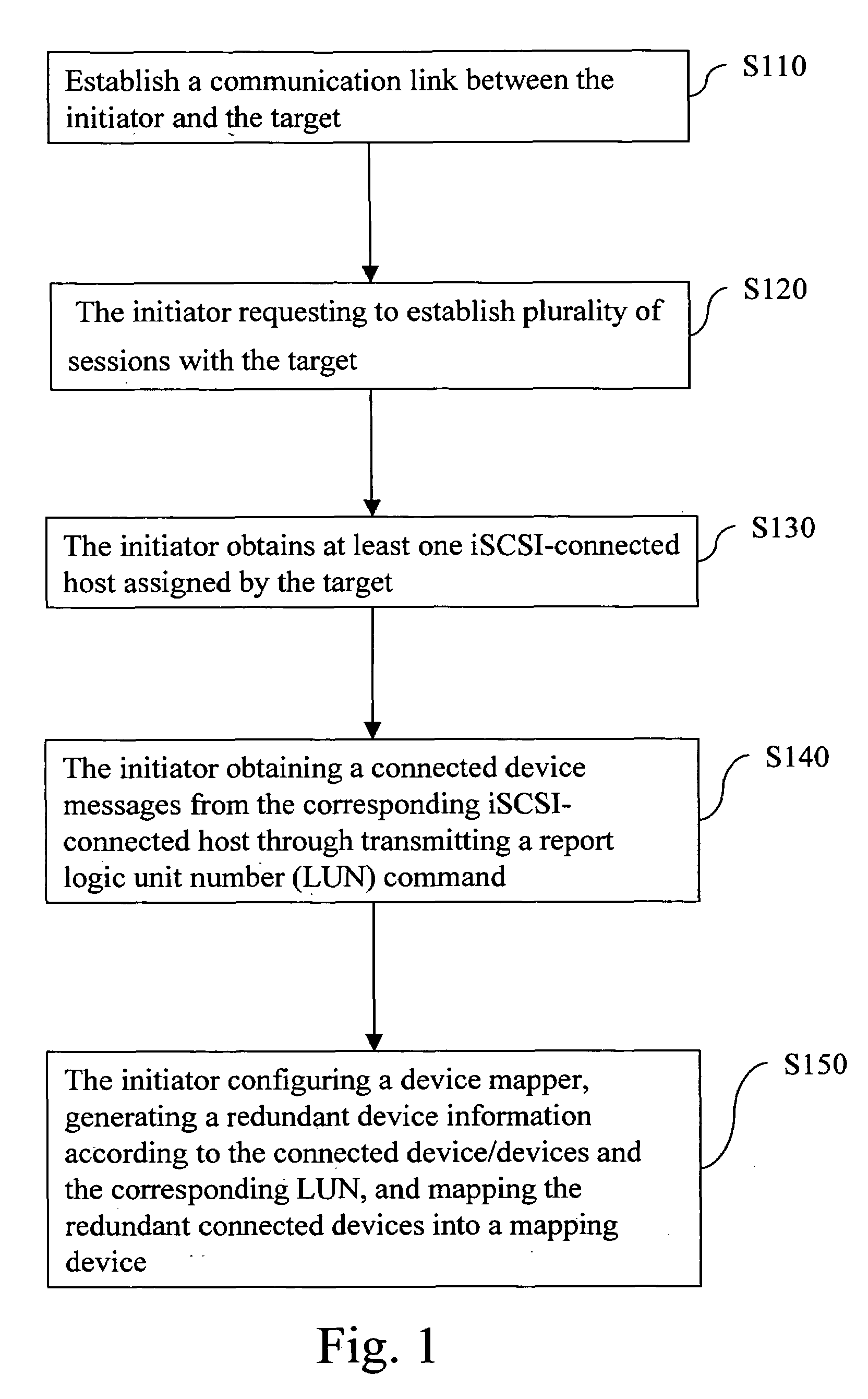
Method for accessing remote logic equipment through multiple routes in Linux system
The invention relates to a method for accessing a remote logical unit in a Linux system in a multipath manner. The method is used for realizing multipath access between an initiator and a target in a storage area network (SAN), and comprises the following steps: the initiator establishes on-line communication with the target and requests to establish at least one on-line session with the target; the initiator obtains internet small computer system interface (iSCSI) on-line host allocated by the target and acquires on-line equipment information corresponding to the iSCSI on-line host by returning a logical unit number (LUN) command; and the initiator which is equipped with an equipment mapping instrument generates redundant equipment information according to the on-line equipment and the corresponding LUN, and maps the redundant on-line equipment to be singular mapping equipment.
Owner:INVENTEC CORP
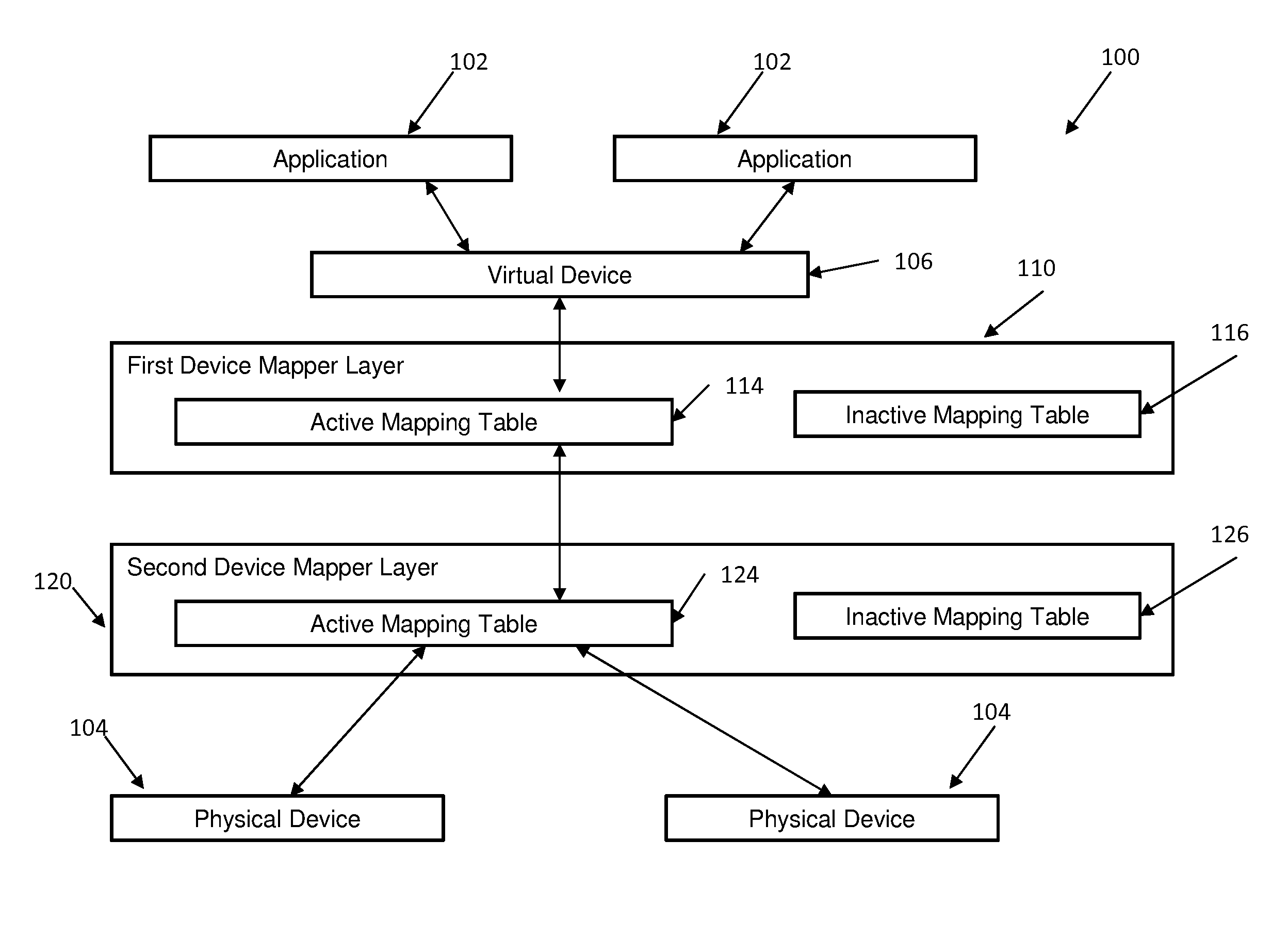
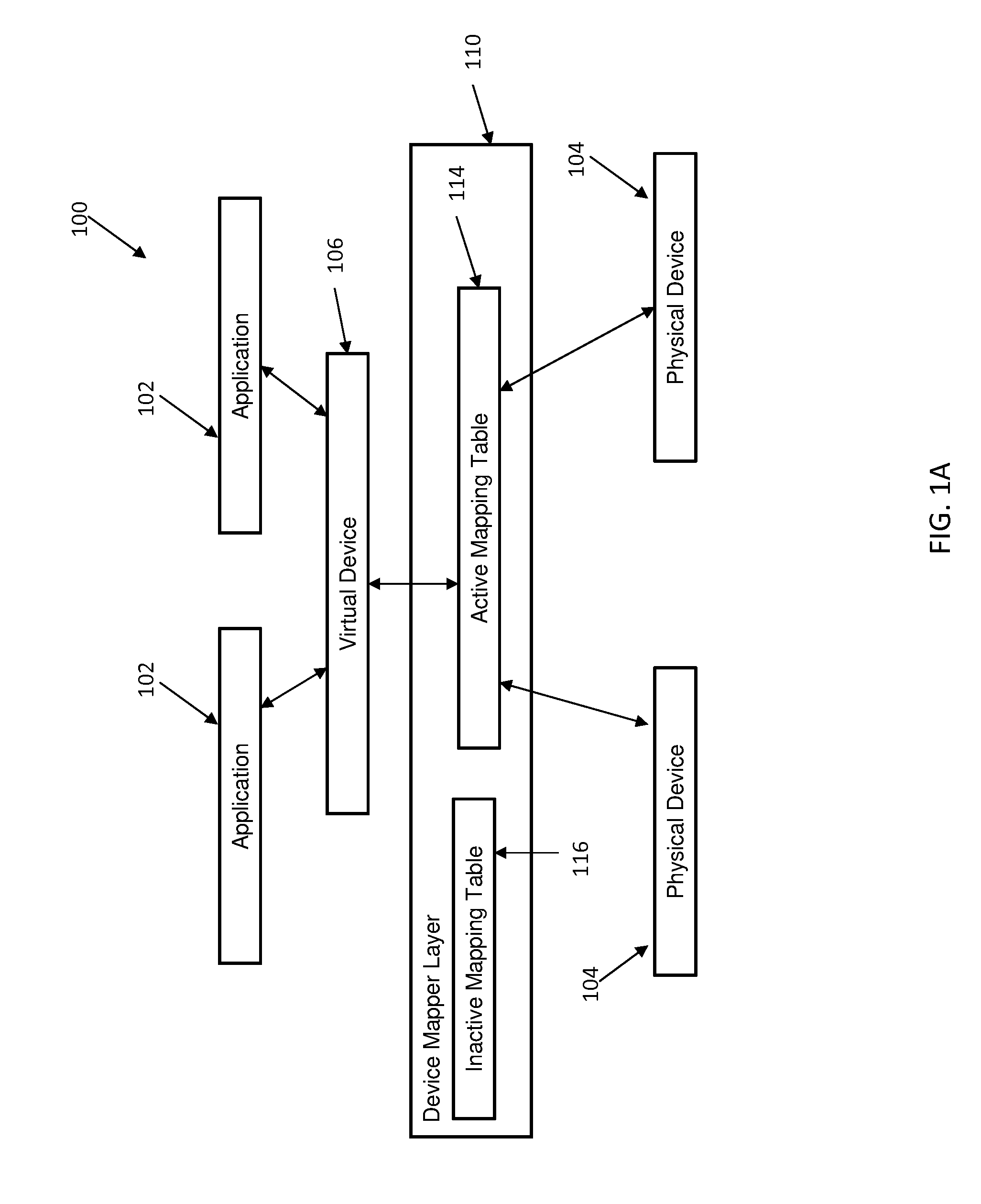
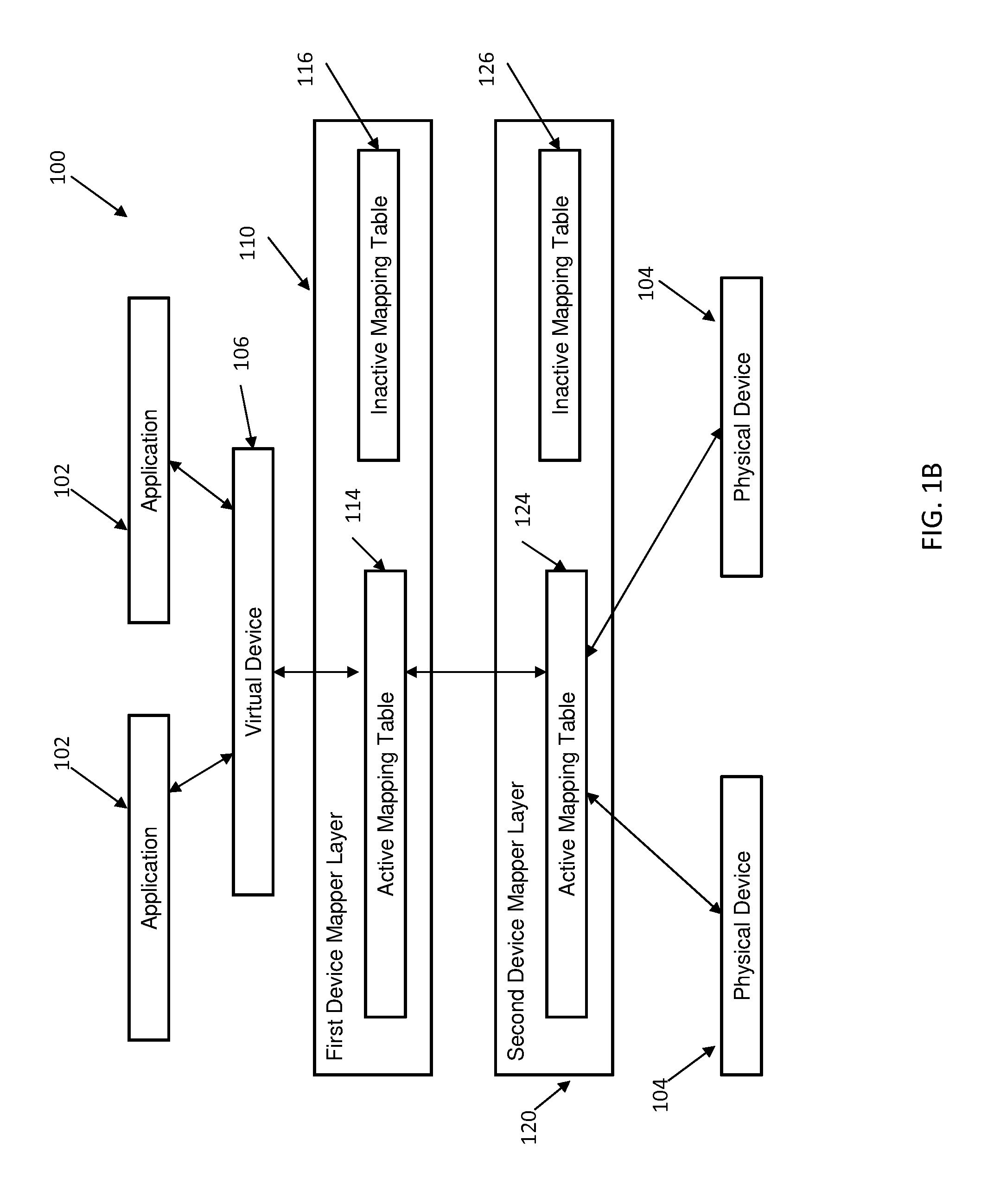
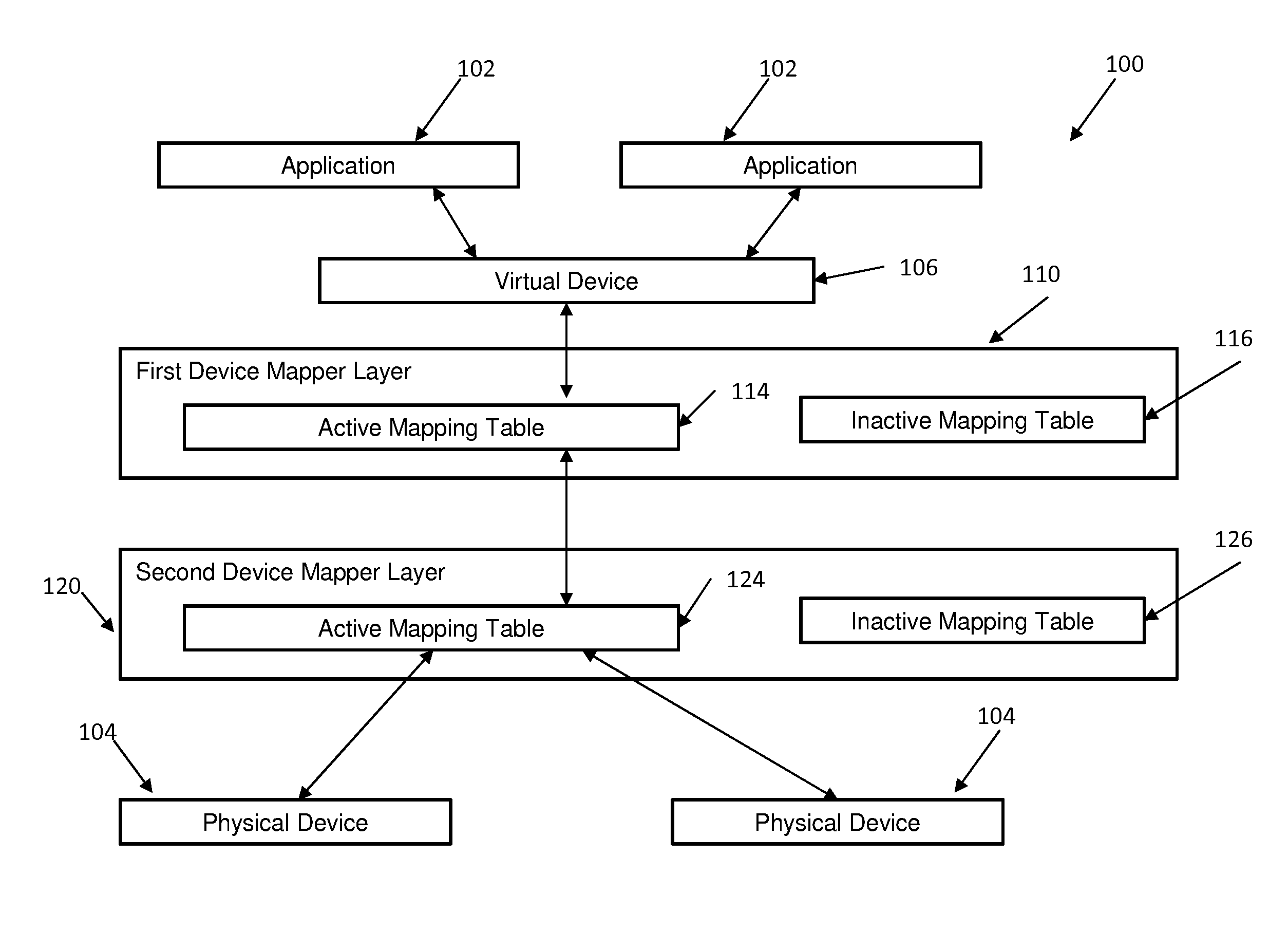
Non-disruptive modification of a device mapper stack
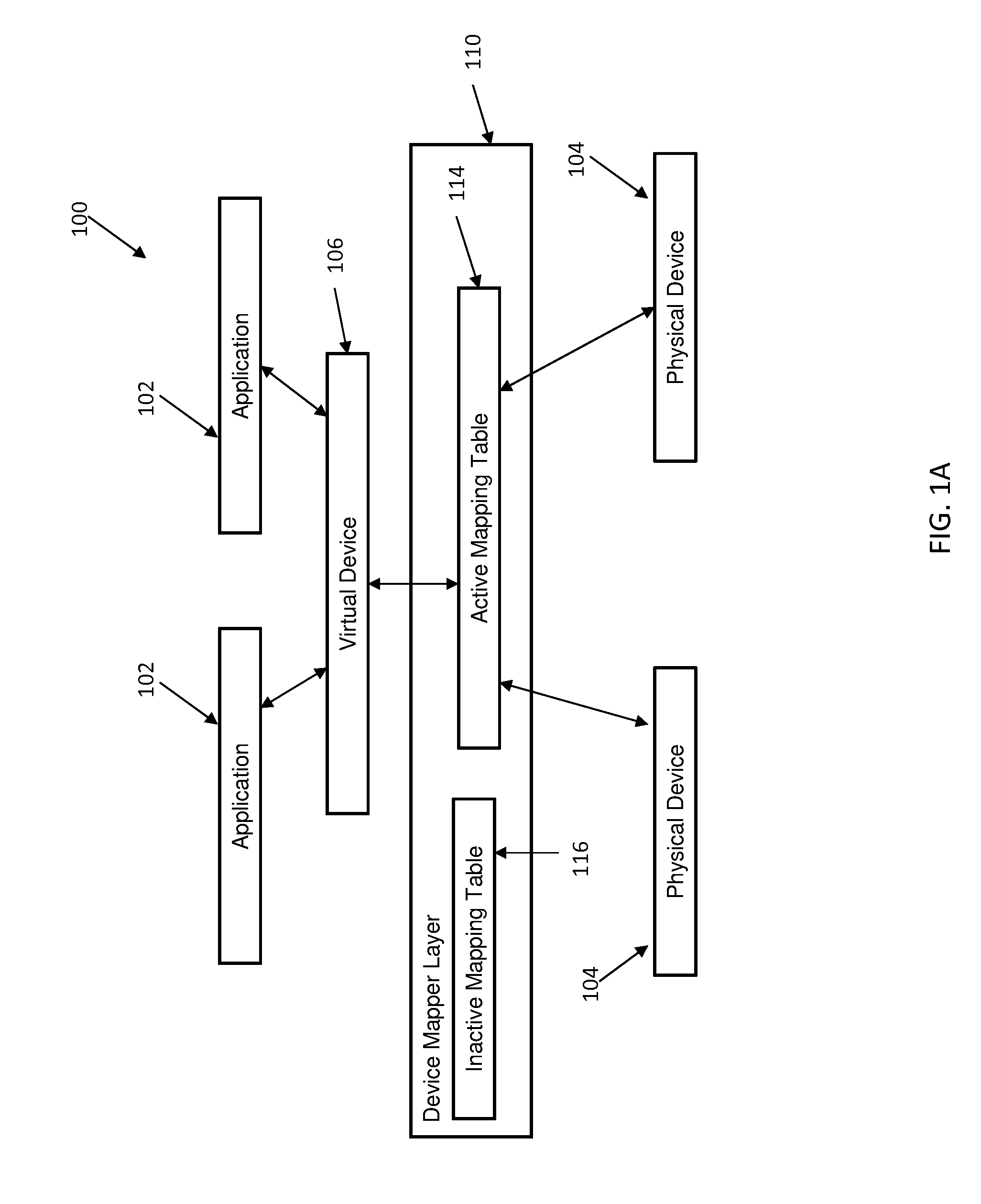
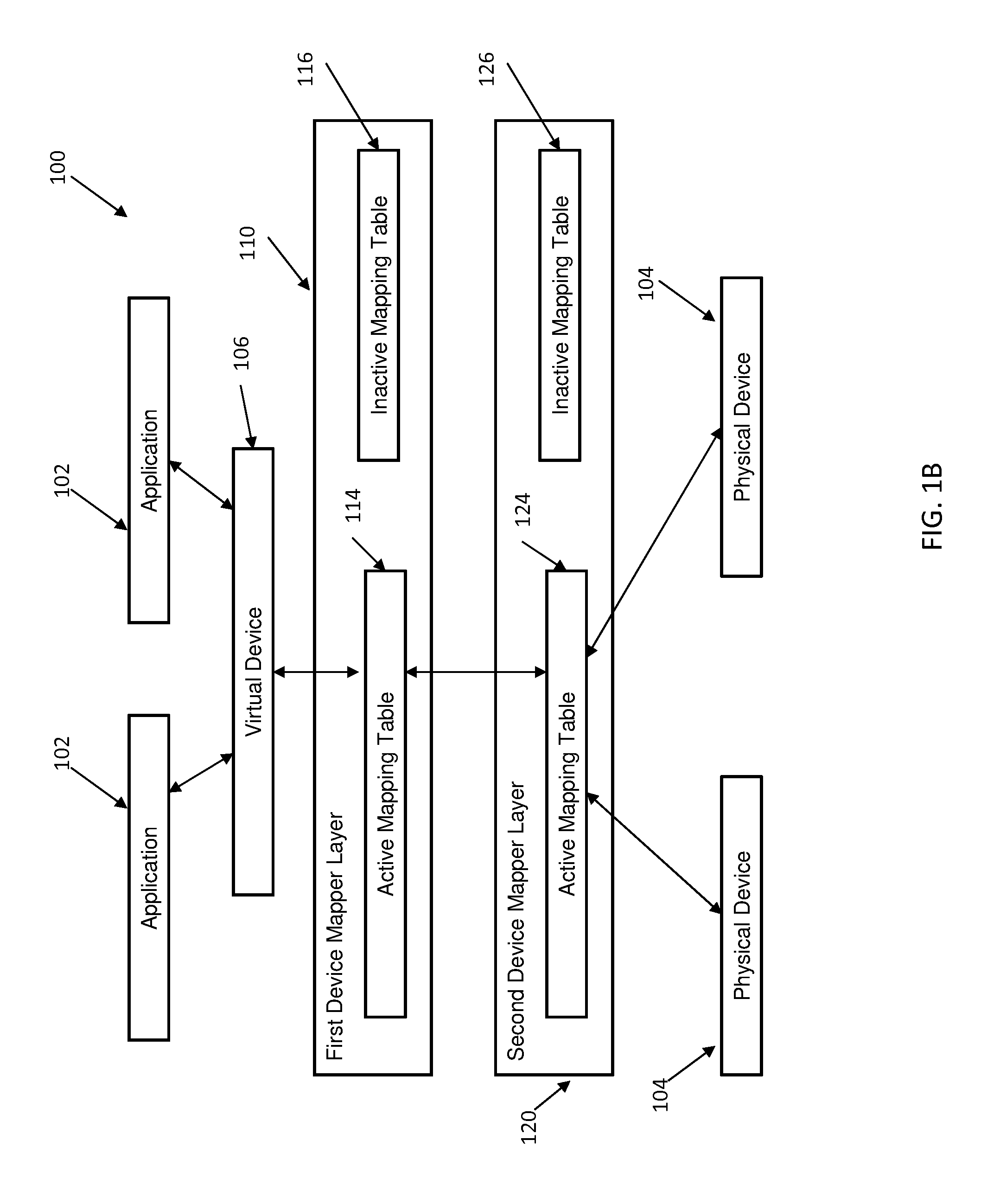
InactiveUS9176890B2Input/output to record carriersMemory adressing/allocation/relocationNon destructiveDevice mapper
Embodiments relate to non-disruptive modification of a device mapper stack. Aspects include receiving the device mapper stack comprising a first device mapper layer having an active mapping table and creating a second device mapper layer having a copy of the active mapping table from the first device mapper layer. Aspects further include creating an inactive mapping table having a desired mapping logic in the first device mapper layer and suspending and resuming an operation of the first device mapper layer. Suspending and resuming causes the active mapping table of the first device mapper layer to be replaced with the inactive mapping table of the first device mapper layer.
Owner:GLOBALFOUNDRIES INC
A method of accelerating disk random input and output (io) reading and writing
ActiveCN104793892BAccelerate the number of writesReduce the number of operationsInput/output to record carriersVirtual file systemDevice mapper
The invention discloses a method for accelerating random in-out (IO) read-write of a disk. The method is characterized by comprising the steps that a computer operating system application layer performs a data read-write operation and enters a kernel mode through invagination, a virtual file system layer encapsulates data into a BIO which is an interactive data structure between the virtual file system layer and a general block layer, and then the BIO is submitted to a general block layer subsystem; the BIO is cut into the fixed block size and transmitted to a BINLOGDEV module layer at a DEVICE-MAPPER driving layer of the general block layer subsystem, when the BIO enters the BINLOGDEV module layer, whether a caching condition is met or not is checked, that is, whether the initial position of the BIO is aligned or not, whether the length of the BIO is the block length or not, if the condition is met, a step 103 is conducted, and if the condition is not met, a step 106 is conducted. According to the method for accelerating the random in-out (IO) read-write of the disk, on the condition that the random IO is written, the random IO is converted into the sequence IO, the storing velocity is high, and the efficiency is high.
Owner:UCLOUD TECH CO LTD
Non-disruptive modification of a device mapper stack
InactiveUS20140365739A1Memory adressing/allocation/relocationInput/output processes for data processingNon destructiveDevice mapper
Embodiments relate to non-disruptive modification of a device mapper stack. Aspects include receiving the device mapper stack comprising a first device mapper layer having an active mapping table and creating a second device mapper layer having a copy of the active mapping table from the first device mapper layer. Aspects further include creating an inactive mapping table having a desired mapping logic in the first device mapper layer and suspending and resuming an operation of the first device mapper layer. Suspending and resuming causes the active mapping table of the first device mapper layer to be replaced with the inactive mapping table of the first device mapper layer.
Owner:GLOBALFOUNDRIES INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com